Security Week 42: collisions in SHA-1, practical hacking of routers, Android / Security / Sadness
 When you are at the epicenter of events, it is sometimes difficult to understand what really happened. Being in a traffic jam, you won’t know that it happened due to an accident until you get to two crippled pilots who occupied three lanes. Up to this point, you simply do not have enough information to draw conclusions. In the information security industry, this happens so often: the topic is complex, there are many nuances, and the result of some research can only be realistically evaluated after a few years.
When you are at the epicenter of events, it is sometimes difficult to understand what really happened. Being in a traffic jam, you won’t know that it happened due to an accident until you get to two crippled pilots who occupied three lanes. Up to this point, you simply do not have enough information to draw conclusions. In the information security industry, this happens so often: the topic is complex, there are many nuances, and the result of some research can only be realistically evaluated after a few years.This week, the three most interesting security news have nothing to do with each other, except for a thick layer of subtexts. If you do not deal with the topic constantly, the importance of some events can be estimated incorrectly, or you can’t see any important details. I’ll try, to the best of my ability, to explain with examples, although the subtexts are such a thing — everyone sees something different. Welcome to episode 11 of Security Week. Disruption of the Veil. Traditional rules: every week the editorial board of the Threatpost news site selects the three most significant news, to which I add an extended and merciless comment. All episodes of the series can be found here .
Collision search for the SHA-1 algorithm has seriously depreciated
News . FastBruce Schneier three years ago. A new study that has changed the concept of algorithm security.
Those who have advanced Linux a little further than installing Ubuntu automatically know that this system motivates them to read instructions. I mean, first of course I try to google a dock, where the sequence of commands is simply indicated, but in some cases nothing will work for me at first, and then everything will break. This news is from the same series: without at least minimal immersion in the materiel it is difficult to understand. Despite the fact that this is perhaps the most difficult topic for the entire existence of the series, I will try to tell what the point is, in simple words.

Well, I’ll try it somehow.
SHA-1 - cryptographic hashing algorithm. Such an algorithm can be given at the input a sequence of data of almost unlimited length, and at the output, 160 bits of information can be obtained that allow you to identify the original data array. Unless, of course, you have it: it will not work to recover information from the hash, it is impossible to turn the stuffing back.
More precisely, it should not work, even if, for example, there is a password for an unlucky user like 123456. There are two requirements to any such algorithm: the inability to get the source data with only a hash on hand and the inability to pick up such a pair of data sets so that their hash matches . More precisely, the ability to do both is almost always available. It just has to be connected with such a large amount of computation that there’s nothing to even try. Well, that is, you buy the most powerful supercomputer, give it the task to break the cipher. After 240 years, he says that the answer is 42, but by that time you already do not care.
But there is a nuance. Firstly, computer performance is constantly growing. Secondly, researchers are looking for workarounds to break into cryptographic systems. For a hashing algorithm, finding a collision is much easier than decrypting the original data. Meanwhile, the same SHA-1 is used in various encryption and authorization systems, where its main task is to make sure that the data from two different subscribers is the same. If you can find two or more data arrays that have the same hash, and do it cheaply and quickly , then the algorithm is no longer reliable.
Perhaps I will dwell on this, because then a very severe matan begins, which does not change the essence of the matter. Researchers' work looks something like this: we come up with a collision search algorithm that allows you to find one in a little less number of operations than a simple exhaustive search. More precisely, it makes sense to talk about the attack of " Birthdays ." Birthdays, Karl!
Some kind of wrong simple words.
Researchers then improve this algorithm, further reducing the number of operations. As a result, the very attack that required 240 years becomes possible to complete in 120 years. Or for 12. Or for 2. That's when, instead of two and a half centuries, it takes only two months, you can start to worry. So, three years ago, cryptography specialist Jesse Walker from Intel suggested that by 2015 it would take two to the eleventh degree server years to find collisions of the SHA-1 algorithm (well, based on such a spherical typical server in a vacuum). Fortunately, thanks to cloud services, specifically Amazon EC2, you can calculate a more specific monetary equivalent: about 700 thousand dollars and you will get a theoretical way, for example, to fake a digital signature in a relatively short time.
But it was a 2012 assessment. It turned out that even then the SHA-1 algorithm was not as reliable as we would like, only very wealthy organizations, for example, intelligence of some non-poor country , could exploit this unreliability . Naturally, such offices are in no hurry to issue press releases about their successes in the field of the fight against cryptography. So it’s more important to understand when access to such an “instrument” will be obtained, even if by the wealthy, but by cybercriminals.

Recently, a team of researchers from universities in the Netherlands, Singapore and France published a report in which they shared new ideas for optimizing the collision search algorithm. Thanks to them, in short, a real attack can cost "at Amazon prices" only 75 thousand dollars and take about 49 days. Well, or more expensive and faster, to whom it is convenient. Well-known cryptography expert Bruce Schneier commented on this in this way: the 2012 assessment took into account Moore's law, but did not take into account the improvement of the attack algorithm and attack method (for example, the use of graphic processors for calculations that perform the task faster and cheaper). Reliably predict the effect of such optimization is really impossible.
And then we ask the traditional question: in practice, is this a new study and a new assessment threatening someone? Not so much. But how can such “vulnerabilities” be exploited? There is an example for the much less robust MD5 algorithm: we take two different files (in this case, rock star photographs were used) and, sequentially modifying the data in one of them, we get the same hash for two completely different images.
And more specifically? The Flame cyber-espionage campaign used this technique to sign a malicious file with a valid (at that time) Microsoft certificate. More precisely, the signature was fake, but the hashes of the fake signature and the real one coincided. According to an independent assessment, such a trick, even with a weaker algorithm, could cost in the amount of 200 thousand to 2 million dollars. A little expensive!
What about SHA-1? The algorithm has been used since 1995, and, in general, already in 2005, 10 years ago, it was clear that this is not the most reliable technology in the world. But even with the new input, it’s still far from practical use, while SHA-1 is being phased out and replaced by more reliable hashing algorithms. Until 2017, developers of major browsers plan to abandon the use of SHA-1. Perhaps it’s worth hurrying, because if in three years the estimated price of the attack fell from $ 2.77 million to $ 100 thousand, then what could happen in another year? On the other hand, all SHA-1 vulnerability studies so far have purely scientific value. Trying to understand in practice what this is threatening with is the same as concluding from the message “April 12, 250 tons of rocket fuel burned over Kazakhstan” that man first flew into space, not knowing this in advance. Wait and see.
Fun fact: a hash is actually properly called digest or message digest. It turns out you just listened to the digest about the digest. Recursion, uiiii!
Vulnerability in Netgear routers exploited in practice
News . Description of the vulnerability.
Netgear N300 routers have discovered a vulnerability. Well, yes, another hole in the routers, and somehow it turns out that they are all different, but at the same time on one face. In one of the previous series already discusseda bunch of holes in Belkin devices. Netgear and everything is somehow completely offensive. Open the web interface of the router. We enter the password, incorrect, since the router is alien and we do not know the password. We are sent to the page where they write Access Denied. But if you try to open a page with the name BRS_netgear_success.html, then ... we will not be allowed anywhere either. But if you try to do this several times in a row, then they will let me go.

Naturally, it is desirable to be already inside the local network, which somewhat complicates the task. Although if a router, for example, distributes WiFi in a cafe, then getting inside is not a problem. And if for some reason the owner has enabled access to the web interface from the Internet, then everything is simple. By the way, can anyone say why, in principle, access to the web interface from the outside is needed? It is to the web interface of the router, and not to some things on the local network. It seems to me that there are no reasons to do this at all, and there are plenty of reasons to DO NOT, as you see.
In general, everything went pretty well here: the vendor was notified, after two months he made a beta version of the firmware. It would have cost a little, but no, it turned out that the vulnerability is being exploited, as they say, “in the fields”. The Swiss company Compass Security discovered such a router with changed settings: it was not the provider address that was registered as the DNS server, as it usually happens, but don’t understand what. Accordingly, all DNS queries passed through it unobtrusively. A study of the attacking server showed that it “serves” more than 10 thousand hacked routers.
Fun fact: Compass Security for quite some time could not get any response from NetGear. Then the dialogue did happen, and they were even sent a beta version of the firmware for verification. But then (out of nowhere) Shellshock Labs appeared and published its research on the same vulnerability without agreeing with anyone at all (which is not very good). Of course, to name a company after a bug in bash is cool, but nobody canceled the principle of “do no harm”. But from the study of “shell shockers” it becomes clear where the vulnerability in the web interface came from. The firmware code provides the ability to enter the web interface without a password once, at the first start . To prevent this from working further, a flag was provided that was simply forgotten about. Yes, the firmware was eventually updated .
85% of Android devices are unsafe
News . Researchers site with security ratings by vendors.

What are you! This has never happened before, and here again! Meanwhile, we are talking about another scientific study, although of course it is not as intricate as in the SHA-1 story. Researchers at the University of Cambridge did an interesting thing. We collected data on 32 serious vulnerabilities in Android, so we selected 13 of them the most serious, and immediately checked many phones from different manufacturers for this vulnerability. We checked it this way: we made the Device Analyzer application , through which we openly collected various anonymous telemetry from the participants in the experiment, including such parameters as the OS version and build number. In total, we managed to collect information from more than 20 thousand smartphones.
Further, by comparing the Android version number with vulnerability information, we were able to approximatelyassess the scale of the disaster. The result is this picture:
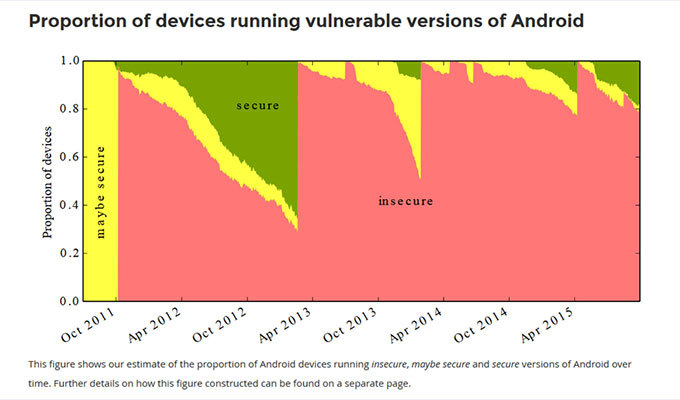
Averaging the indicators for the entire time of the study gave the same figure of 85% - on average at any given time, it is this proportion of Android devices that is subject to one of the known and potentially dangerous vulnerabilities. Or not one. As usual, emphasis should be placed on “potentially” - using the example of Stagefright, it is clear that even the most dangerous vulnerability is subject to severe restrictions on practical implementation.
But the researchers did not stop there and made a rating of the “danger” of devices by manufacturers, calling it the FUM Score. It also takes into account the reaction time of the vendor to information about a new vulnerability - how quickly the patch appears in the devices of a particular manufacturer. The winner was, predictably, the Nexus series of smartphones: it fixes bugs as quickly as possible. In second place is LG, in third is Motorola. However, there are really no “winners” here, only losers. The calculation takes into account precisely the share of updated devices, that is, not only the vendor should release the patch, but the owner should not be too lazy to update. The older the device, the worse: in a separate rating on smartphone models, not the oldest devices of two or three years ago have very dull indicators. Why? Do not update. But enjoy.
In general, the research methodology has many voluntary assumptions, and it proves what everyone already knows. According to the researchers, one of the goals of their work is an additional motivation for manufacturers to repair the system of patching holes in their devices. But what is really important: in the picture above we see an example of an ecosystem that, in principle, cannot be one hundred percent safe. Although Android, with its fragmentation, is the most telling example, there are many such ecosystems. We can say that iOS is safer, but as the first history of the digest pro shows, um, digest, there are no absolutely reliable systems, there are budget restrictions. And this is such a very important point when choosing a protection strategy.
What else happened:
Apple removedfrom the App Store, applications that installed root certificates, which allowed them to intercept, monitor or modify data transmitted over a secure connection. For example, to block ads, or worse. I understand that new applications with such functionality can no longer be downloaded. Why was it possible before?
The European Aviation Safety Agency spoke about the vulnerability in the ACARS system , which is used to transfer data between an aircraft and a ground station. In general, it was initially clear that it was not difficult to send a fake message in the system without any packet verification. You cannot steer a plane, but you can send a message that will mislead the pilots. About ACARS Vulnerability Researchersthey said (in PDF docs) back in 2013, but they were information security specialists, and here the supervisor is directly responsible for security. This is good news.
 Antiquities:
Antiquities:"Indicator-734"
Dangerous resident virus. Infects .COM files when they are loaded into memory. The old beginning of the file is encrypted, and uses 10h bytes of BIOS as a key. Those. files will be correctly decrypted and executed normally only on a computer with the same BIOS version on which they were infected. If it was not possible to decrypt the old beginning of the file, then the virus blocks the operation of the file (executes int 20h), having previously launched its counters. Depending on their condition (approximately 1 time per hour), the virus draws a red cross on the screen, in the center of which there is an inscription: “VINDICATOR”. It hooks int 1Ch, 21h.
Quote from the book "Computer viruses in MS-DOS" by Eugene Kaspersky. 1992 year. Page 70.
Disclaimer: This column reflects only the private opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Here it’s how lucky.
