How to catch what is not. Part Two: Shell and Armor
Part one was devoted to choosing a definition for the term “malicious program” and, quite logically, the article attracted little attention - well, really, who cares what color the rat is - the main thing is for the cat to strangle them properly.
In the second part, we will try to determine what the antivirus should do on the local network. If someone else thinks that the antivirus should catch viruses - we ask for a cat.
At the end of the first part, Khabrozhitel was proposed to answer three simple, children's questions:
Contrary to expectation, an answer close to the truth was immediately given to the first question. Unfortunately, in reality, customers and conference participants are not so knowledgeable. Personal statistics show that customers, participants in conferences where I was able to conduct a survey, and even partners who, in theory, should know a lot, answer the question: “How many malicious programs are created on average per day” - they call the figure 100. After the offer to increase - 500 or a thousand. And fall into a slight thoughtfulness when the real figure is voiced. Take a
look at live.drweb.com , the Infected tab:
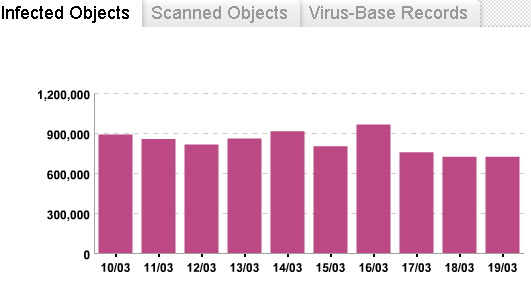
This is the receipt of samples for analysis. The numbers on the chart, by the way, are not at all record. If I’m not mistaken, then at the beginning of December 2013 there was a peak of up to 6 million on one of the days. Naturally, not everything that came is malware (this will be a separate topic when we talk about the level of knowledge of a typical user). And of course, there are repetitions, but, nevertheless, all this is being transformed into an increase in the virus base.
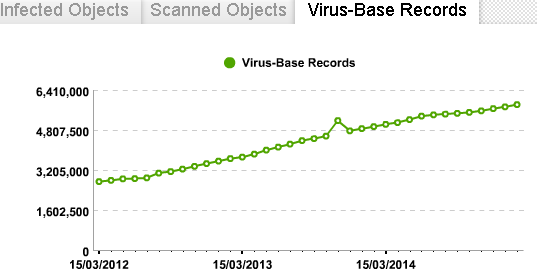
At the same time, the incoming stream is constantly growing. Unfortunately, I did not find any fresh figures for other companies, but in 2011 Evgeny Kaspersky wrote : “70 thousand. Daily. Yeah. "
A small digression. A common misconception is that antiviruses catch malware by signature. This opinion is usually actively exploited by programs that implement “fashionable” types of protection. Not so long ago, behavioral analyzers came out of this position, then it was the turn of cloud antiviruses. “Conventional signature antiviruses that consume resources will die out, they will come in their place ...” So, for those in the tank. Purely signature antiviruses became extinct in the 90s of the last century, when polymorphic viruses appeared that changed at each start and, accordingly, were not caught by signatures (by the way, this was the reason for the emergence of one of two domestic antiviruses - Dr.Web). Therefore, it is correct to measure virus databases in records.
Let's go back to the number of malicious files created per day. Why am I telling all this? The fact is that almost every second conference is asked - is it true that you write viruses? Moreover, the hired employees are quietly hinting - well, now I'm mine - show me where? The myth is so ingrained that clients constantly turn to antivirus companies to issue something else unknown for testing. Anti-virus companies do not send any samples, Western companies do not even hire former hackers because of their moral instability. Employees of companies are not shot during dismissal, and if someone ever finds out that company xxx created a sample ...
The myth is extremely dangerous. Based on it, the number of malicious files released per day is extremely small - well, how many vendors will create to get into the news? From the myth, it turns out that antivirus programs should know all malware - or almost all. But with such a stream of malicious files (and according to various estimates, no more than 70–80 (and I’m not too surprised that this estimate is overestimated) percent of malicious programs released into the “wild nature” on this day are processed and analyzed by antivirus laboratories promptly You can’t release an update instantly.
Let us announce the first two reasons for viruses to be skipped by the antivirus engine (we will talk about behavioral analyzers later):
But these two problems are solvable. The number of analysts is increasing, before analysts receive the stream, it is analyzed by a special robot that automatically generates entries in the databases, etc. Some of the malware that have not been analyzed are caught by heuristics.
Once we mentioned heuristics, then another digression in technology. Unfortunately, the first reaction to the story about the number of malicious programs released is the words: "This is understandable, such viruses should be detected by the heuristic." Unfortunately, many, relying on the myth of tests, consider heuristics a panacea. So here. Heuristics detect only new modifications of malware that have previously been analyzed, malware with known antivirus behavior. Suppose, some time ago, attackers developed a malicious program. After a while, it began to be detected. What should cybercriminals do? To start all over again? You can do it easier - pack in an archive with an unknown format for the antivirus / encrypt the malicious program. No heuristic will take such a hidden program. What to do antivirus? You can add each such sample to the virus database (and they do!), Or you can catch it using FLY-CODE and structural entropy analysis technology, as Dr.Web does (each company has its own technologies, therefore experts on other products are invited to fill up the list) . The first provides verification of packed executable objects, unpacks non-standard packers by the method of virtualizing file execution, the second detects unknown threats by the peculiarities of the location of code fragments in the tested objects protected by crypto packers.
Let us return to the reasons for non-detection. The worst problem is the third. Non-lone hackers have long been making the most dangerous malware. This is a well-organized criminal business, built in the image of companies developing ordinary programs. The composition of such "firms" includes:
And testers play a key role. Non-detection testing (why release a malicious program that will be detected?) Of the developed malware with up-to-date anti-virus solutions has enabled the release of only malicious programs that are not detected (until updates are received) by any anti-virus solutions - including using heuristic mechanisms. How many malware can one group produce? Characteristic in this respect was the group that released Carberp (http://updates.drweb.com - ONLY added to the virus database on 03/02/2012):
TrojanCarberp.14 (2) Trojan.Carberp.15 (7) Trojan.Carberp.194 Trojan.Carberp.195 Trojan.Carberp.196 Trojan.Carberp.197 Trojan.Carberp.198 Trojan.Carberp.199 Trojan.Carberp.200 Trojan .Carberp.201 Trojan.Carberp.202 Trojan.Carberp.203 Trojan.Carberp.204 Trojan.Carberp.205 Trojan.Carberp.206 Trojan.Carberp.207 Trojan.Carberp.208 (14) Trojan.Carberp.209 Trojan.Carberp .210 Trojan.Carberp.211 Trojan.Carberp.213 Trojan.Carberp.214 Trojan.Carberp.215 Trojan.Carberp.216 Trojan.Carberp.217 Trojan.Carberp.218 Trojan.Carberp.219 Trojan.Carberp.220 Trojan.Carberp .221 Trojan.Carberp.222 Trojan.Carberp.224 Trojan.Carberp.225 Trojan.Carberp.226 Trojan.Carberp.227 Trojan.Carberp.228 Trojan.Carberp.229 Trojan.Carberp.230 Trojan.Carberp.231 Trojan.Carberp .232 Trojan.Carberp.233 Trojan.Carberp.234 Trojan.Carberp.235 Trojan.Carberp.236 Trojan.Carberp.237 Trojan.Carberp.238 Trojan.Carberp.239 Trojan.Carberp.240 Trojan.Carberp.241 Trojan.Carberp.242 Trojan.Carberp.243 Trojan.Carberp.244 Trojan.Carberp.245 Trojan.Carberp.246 Trojan.Carberp.247 Trojan.Carberp. 248 Trojan.Carberp.249 Trojan.Carberp.250 Trojan.Carberp.251 Trojan.Carberp.252 Trojan.Carberp.253 Trojan.Carberp.254 Trojan.Carberp.255 Trojan.Carberp.256 Trojan.Carberp.257 Trojan.Carberp. 258 Trojan.Carberp.259 Trojan.Carberp.260 Trojan.Carberp.261 Trojan.Carberp.262 Trojan.Carberp.263 Trojan.Carberp.264 Trojan.Carberp.265 Trojan.Carberp.266 Trojan.Carberp.267 Trojan.Carberp. 29 (14) Trojan.Carberp.33 (10) Trojan.Carberp.45 (4) Trojan.Carberp.5 (3) Trojan.Carberp.60 (6) Trojan.Carberp.61 Trojan.Carberp.80Carberp.247 Trojan.Carberp.248 Trojan.Carberp.249 Trojan.Carberp.250 Trojan.Carberp.251 Trojan.Carberp.252 Trojan.Carberp.253 Trojan.Carberp.254 Trojan.Carberp.255 Trojan.Carberp.256 Trojan. Carberp.257 Trojan.Carberp.258 Trojan.Carberp.259 Trojan.Carberp.260 Trojan.Carberp.261 Trojan.Carberp.262 Trojan.Carberp.263 Trojan.Carberp.264 Trojan.Carberp.265 Trojan.Carberp.266 Trojan. Carberp.267 Trojan.Carberp.29 (14) Trojan.Carberp.33 (10) Trojan.Carberp.45 (4) Trojan.Carberp.5 (3) Trojan.Carberp.60 (6) Trojan.Carberp.61 Trojan. Carberp.80Carberp.247 Trojan.Carberp.248 Trojan.Carberp.249 Trojan.Carberp.250 Trojan.Carberp.251 Trojan.Carberp.252 Trojan.Carberp.253 Trojan.Carberp.254 Trojan.Carberp.255 Trojan.Carberp.256 Trojan. Carberp.257 Trojan.Carberp.258 Trojan.Carberp.259 Trojan.Carberp.260 Trojan.Carberp.261 Trojan.Carberp.262 Trojan.Carberp.263 Trojan.Carberp.264 Trojan.Carberp.265 Trojan.Carberp.266 Trojan. Carberp.267 Trojan.Carberp.29 (14) Trojan.Carberp.33 (10) Trojan.Carberp.45 (4) Trojan.Carberp.5 (3) Trojan.Carberp.60 (6) Trojan.Carberp.61 Trojan. Carberp.80Carberp.264 Trojan.Carberp.265 Trojan.Carberp.266 Trojan.Carberp.267 Trojan.Carberp.29 (14) Trojan.Carberp.33 (10) Trojan.Carberp.45 (4) Trojan.Carberp.5 (3) Trojan.Carberp.60 (6) Trojan.Carberp.61 Trojan.Carberp.80Carberp.264 Trojan.Carberp.265 Trojan.Carberp.266 Trojan.Carberp.267 Trojan.Carberp.29 (14) Trojan.Carberp.33 (10) Trojan.Carberp.45 (4) Trojan.Carberp.5 (3) Trojan.Carberp.60 (6) Trojan.Carberp.61 Trojan.Carberp.80
Impressive? One day. One grouping.
The number of programs produced by one group can reach hundreds of samples per day - and not one of them will be detected by the antivirus software used by the target group of victims.
TOTAL:
At any given moment in time, no anti-virus program - without the use of additional protection tools - can provide protection against the penetration of yet unknown malware - not received for analysis in the anti-virus laboratory.
If a company / user / administrator relies solely on an anti-virus program for malware detection, they are completely defenseless. This is what determines the success of cryptographers (and, in the recent past, WinLock).
A typical opinion is that the antivirus should catch everything at the input. This, unfortunately, is not the case. Anti-virus can detect known malicious programs (including using heuristic mechanisms) at the time of their penetration, and after receiving updates, detect and destroy (but not roll back actions!) Already running and actively counteract the detection of malicious programs.
Conclusion 1. Alas and ah. Choosing an antivirus based on test victories does not make sense. There will be a separate article about the tests, but one way or another, all tests are performed on already known malicious programs.
Conclusion 2. The function of the antivirus is the destruction of already active, previously missed by all malware protection tools. And no one except the antivirus can perform this task. But the function of counteracting the penetration of unknown malicious programs should be taken over by access control systems, launch restriction systems, behavioral analyzers (plus an antivirus as a traffic analyzer).
Again. At the moment, only anti-virus cannot be used to protect against malicious programs. It is necessary to implement an anti-virus protection system as part of the antivirus itself, firewall, behavioral analyzer, office / parental controls, and backup systems. This is a minimum of a minimum.
User access should be limited only by the really necessary resources of the local network and the Internet. The ability to use removable media should be limited. The user should not be allowed to install any programs, which will prevent the virus that bypassed the protection of security tools from being installed on the computer. The composition of the installed and used software should correspond to the known list.
A centralized update installation system should be used. The situation should be excluded when the decision on whether to install the update is made by the user. Using a centralized update system allows real-time monitoring of the absence of known vulnerabilities on protected workstations and servers.
The user should only work under an account with limited rights.
(Adapted from the CyberArk presentation at the recent interbank forum in Magnitogorsk)
I apologize for listing the elementary truths. But many are so sure that server protection is absolutely unnecessary ...
Where is America's discovery here?
Conclusion 3. The antivirus solution used to protect workstations and file servers should:
And finally, the question:
The analysis of IT mythology will continue in the next article.
In the second part, we will try to determine what the antivirus should do on the local network. If someone else thinks that the antivirus should catch viruses - we ask for a cat.
At the end of the first part, Khabrozhitel was proposed to answer three simple, children's questions:
- How many malicious programs are created by cybercriminals on average per day?
- what percentage of malware can an antivirus skip to be considered a good security measure, and why can an antivirus skip it?
- Why do you need an antivirus - what tasks does it perform in the protection system?
Contrary to expectation, an answer close to the truth was immediately given to the first question. Unfortunately, in reality, customers and conference participants are not so knowledgeable. Personal statistics show that customers, participants in conferences where I was able to conduct a survey, and even partners who, in theory, should know a lot, answer the question: “How many malicious programs are created on average per day” - they call the figure 100. After the offer to increase - 500 or a thousand. And fall into a slight thoughtfulness when the real figure is voiced. Take a
look at live.drweb.com , the Infected tab:

This is the receipt of samples for analysis. The numbers on the chart, by the way, are not at all record. If I’m not mistaken, then at the beginning of December 2013 there was a peak of up to 6 million on one of the days. Naturally, not everything that came is malware (this will be a separate topic when we talk about the level of knowledge of a typical user). And of course, there are repetitions, but, nevertheless, all this is being transformed into an increase in the virus base.

At the same time, the incoming stream is constantly growing. Unfortunately, I did not find any fresh figures for other companies, but in 2011 Evgeny Kaspersky wrote : “70 thousand. Daily. Yeah. "
A small digression. A common misconception is that antiviruses catch malware by signature. This opinion is usually actively exploited by programs that implement “fashionable” types of protection. Not so long ago, behavioral analyzers came out of this position, then it was the turn of cloud antiviruses. “Conventional signature antiviruses that consume resources will die out, they will come in their place ...” So, for those in the tank. Purely signature antiviruses became extinct in the 90s of the last century, when polymorphic viruses appeared that changed at each start and, accordingly, were not caught by signatures (by the way, this was the reason for the emergence of one of two domestic antiviruses - Dr.Web). Therefore, it is correct to measure virus databases in records.
Let's go back to the number of malicious files created per day. Why am I telling all this? The fact is that almost every second conference is asked - is it true that you write viruses? Moreover, the hired employees are quietly hinting - well, now I'm mine - show me where? The myth is so ingrained that clients constantly turn to antivirus companies to issue something else unknown for testing. Anti-virus companies do not send any samples, Western companies do not even hire former hackers because of their moral instability. Employees of companies are not shot during dismissal, and if someone ever finds out that company xxx created a sample ...
The myth is extremely dangerous. Based on it, the number of malicious files released per day is extremely small - well, how many vendors will create to get into the news? From the myth, it turns out that antivirus programs should know all malware - or almost all. But with such a stream of malicious files (and according to various estimates, no more than 70–80 (and I’m not too surprised that this estimate is overestimated) percent of malicious programs released into the “wild nature” on this day are processed and analyzed by antivirus laboratories promptly You can’t release an update instantly.
Let us announce the first two reasons for viruses to be skipped by the antivirus engine (we will talk about behavioral analyzers later):
- The delay in detecting a new malware is the delta between its getting to the victim and the analysis.
- Delay in processing due to the large number of programs received for analysis / incorrect assessment of the danger of the program at the time of detection. By the way, the myth about the greater effectiveness of Dr.Web CureIt is connected with this reason! Compared to conventional antivirus, often between malware infection and downloading the utility, the malware manages to get into the databases.
But these two problems are solvable. The number of analysts is increasing, before analysts receive the stream, it is analyzed by a special robot that automatically generates entries in the databases, etc. Some of the malware that have not been analyzed are caught by heuristics.
Once we mentioned heuristics, then another digression in technology. Unfortunately, the first reaction to the story about the number of malicious programs released is the words: "This is understandable, such viruses should be detected by the heuristic." Unfortunately, many, relying on the myth of tests, consider heuristics a panacea. So here. Heuristics detect only new modifications of malware that have previously been analyzed, malware with known antivirus behavior. Suppose, some time ago, attackers developed a malicious program. After a while, it began to be detected. What should cybercriminals do? To start all over again? You can do it easier - pack in an archive with an unknown format for the antivirus / encrypt the malicious program. No heuristic will take such a hidden program. What to do antivirus? You can add each such sample to the virus database (and they do!), Or you can catch it using FLY-CODE and structural entropy analysis technology, as Dr.Web does (each company has its own technologies, therefore experts on other products are invited to fill up the list) . The first provides verification of packed executable objects, unpacks non-standard packers by the method of virtualizing file execution, the second detects unknown threats by the peculiarities of the location of code fragments in the tested objects protected by crypto packers.
Let us return to the reasons for non-detection. The worst problem is the third. Non-lone hackers have long been making the most dangerous malware. This is a well-organized criminal business, built in the image of companies developing ordinary programs. The composition of such "firms" includes:
- Malware developers
- Created Software Testers
- Criminal Investigators of Vulnerabilities in Operating Systems and Application Software
- "Specialists" in the use of viral packers and encryption
- Malware distributors, social engineering specialists
- System administrators providing distributed secure work within the criminal community and botnet management
- droppers
- ...
And testers play a key role. Non-detection testing (why release a malicious program that will be detected?) Of the developed malware with up-to-date anti-virus solutions has enabled the release of only malicious programs that are not detected (until updates are received) by any anti-virus solutions - including using heuristic mechanisms. How many malware can one group produce? Characteristic in this respect was the group that released Carberp (http://updates.drweb.com - ONLY added to the virus database on 03/02/2012):
TrojanCarberp.14 (2) Trojan.Carberp.15 (7) Trojan.Carberp.194 Trojan.Carberp.195 Trojan.Carberp.196 Trojan.Carberp.197 Trojan.Carberp.198 Trojan.Carberp.199 Trojan.Carberp.200 Trojan .Carberp.201 Trojan.Carberp.202 Trojan.Carberp.203 Trojan.Carberp.204 Trojan.Carberp.205 Trojan.Carberp.206 Trojan.Carberp.207 Trojan.Carberp.208 (14) Trojan.Carberp.209 Trojan.Carberp .210 Trojan.Carberp.211 Trojan.Carberp.213 Trojan.Carberp.214 Trojan.Carberp.215 Trojan.Carberp.216 Trojan.Carberp.217 Trojan.Carberp.218 Trojan.Carberp.219 Trojan.Carberp.220 Trojan.Carberp .221 Trojan.Carberp.222 Trojan.Carberp.224 Trojan.Carberp.225 Trojan.Carberp.226 Trojan.Carberp.227 Trojan.Carberp.228 Trojan.Carberp.229 Trojan.Carberp.230 Trojan.Carberp.231 Trojan.Carberp .232 Trojan.Carberp.233 Trojan.Carberp.234 Trojan.Carberp.235 Trojan.Carberp.236 Trojan.Carberp.237 Trojan.Carberp.238 Trojan.Carberp.239 Trojan.Carberp.240 Trojan.Carberp.241 Trojan.Carberp.242 Trojan.Carberp.243 Trojan.Carberp.244 Trojan.Carberp.245 Trojan.Carberp.246 Trojan.Carberp.247 Trojan.Carberp. 248 Trojan.Carberp.249 Trojan.Carberp.250 Trojan.Carberp.251 Trojan.Carberp.252 Trojan.Carberp.253 Trojan.Carberp.254 Trojan.Carberp.255 Trojan.Carberp.256 Trojan.Carberp.257 Trojan.Carberp. 258 Trojan.Carberp.259 Trojan.Carberp.260 Trojan.Carberp.261 Trojan.Carberp.262 Trojan.Carberp.263 Trojan.Carberp.264 Trojan.Carberp.265 Trojan.Carberp.266 Trojan.Carberp.267 Trojan.Carberp. 29 (14) Trojan.Carberp.33 (10) Trojan.Carberp.45 (4) Trojan.Carberp.5 (3) Trojan.Carberp.60 (6) Trojan.Carberp.61 Trojan.Carberp.80Carberp.247 Trojan.Carberp.248 Trojan.Carberp.249 Trojan.Carberp.250 Trojan.Carberp.251 Trojan.Carberp.252 Trojan.Carberp.253 Trojan.Carberp.254 Trojan.Carberp.255 Trojan.Carberp.256 Trojan. Carberp.257 Trojan.Carberp.258 Trojan.Carberp.259 Trojan.Carberp.260 Trojan.Carberp.261 Trojan.Carberp.262 Trojan.Carberp.263 Trojan.Carberp.264 Trojan.Carberp.265 Trojan.Carberp.266 Trojan. Carberp.267 Trojan.Carberp.29 (14) Trojan.Carberp.33 (10) Trojan.Carberp.45 (4) Trojan.Carberp.5 (3) Trojan.Carberp.60 (6) Trojan.Carberp.61 Trojan. Carberp.80Carberp.247 Trojan.Carberp.248 Trojan.Carberp.249 Trojan.Carberp.250 Trojan.Carberp.251 Trojan.Carberp.252 Trojan.Carberp.253 Trojan.Carberp.254 Trojan.Carberp.255 Trojan.Carberp.256 Trojan. Carberp.257 Trojan.Carberp.258 Trojan.Carberp.259 Trojan.Carberp.260 Trojan.Carberp.261 Trojan.Carberp.262 Trojan.Carberp.263 Trojan.Carberp.264 Trojan.Carberp.265 Trojan.Carberp.266 Trojan. Carberp.267 Trojan.Carberp.29 (14) Trojan.Carberp.33 (10) Trojan.Carberp.45 (4) Trojan.Carberp.5 (3) Trojan.Carberp.60 (6) Trojan.Carberp.61 Trojan. Carberp.80Carberp.264 Trojan.Carberp.265 Trojan.Carberp.266 Trojan.Carberp.267 Trojan.Carberp.29 (14) Trojan.Carberp.33 (10) Trojan.Carberp.45 (4) Trojan.Carberp.5 (3) Trojan.Carberp.60 (6) Trojan.Carberp.61 Trojan.Carberp.80Carberp.264 Trojan.Carberp.265 Trojan.Carberp.266 Trojan.Carberp.267 Trojan.Carberp.29 (14) Trojan.Carberp.33 (10) Trojan.Carberp.45 (4) Trojan.Carberp.5 (3) Trojan.Carberp.60 (6) Trojan.Carberp.61 Trojan.Carberp.80
Impressive? One day. One grouping.
The number of programs produced by one group can reach hundreds of samples per day - and not one of them will be detected by the antivirus software used by the target group of victims.
TOTAL:
At any given moment in time, no anti-virus program - without the use of additional protection tools - can provide protection against the penetration of yet unknown malware - not received for analysis in the anti-virus laboratory.
If a company / user / administrator relies solely on an anti-virus program for malware detection, they are completely defenseless. This is what determines the success of cryptographers (and, in the recent past, WinLock).
A typical opinion is that the antivirus should catch everything at the input. This, unfortunately, is not the case. Anti-virus can detect known malicious programs (including using heuristic mechanisms) at the time of their penetration, and after receiving updates, detect and destroy (but not roll back actions!) Already running and actively counteract the detection of malicious programs.
Conclusion 1. Alas and ah. Choosing an antivirus based on test victories does not make sense. There will be a separate article about the tests, but one way or another, all tests are performed on already known malicious programs.
Conclusion 2. The function of the antivirus is the destruction of already active, previously missed by all malware protection tools. And no one except the antivirus can perform this task. But the function of counteracting the penetration of unknown malicious programs should be taken over by access control systems, launch restriction systems, behavioral analyzers (plus an antivirus as a traffic analyzer).
Again. At the moment, only anti-virus cannot be used to protect against malicious programs. It is necessary to implement an anti-virus protection system as part of the antivirus itself, firewall, behavioral analyzer, office / parental controls, and backup systems. This is a minimum of a minimum.
User access should be limited only by the really necessary resources of the local network and the Internet. The ability to use removable media should be limited. The user should not be allowed to install any programs, which will prevent the virus that bypassed the protection of security tools from being installed on the computer. The composition of the installed and used software should correspond to the known list.
A centralized update installation system should be used. The situation should be excluded when the decision on whether to install the update is made by the user. Using a centralized update system allows real-time monitoring of the absence of known vulnerabilities on protected workstations and servers.
The user should only work under an account with limited rights.
(Adapted from the CyberArk presentation at the recent interbank forum in Magnitogorsk)
I apologize for listing the elementary truths. But many are so sure that server protection is absolutely unnecessary ...

Where is America's discovery here?
Conclusion 3. The antivirus solution used to protect workstations and file servers should:
- have a self-defense system that does not allow an unknown malicious program to disrupt the normal operation of the antivirus — the antivirus solution should function normally until an update is received that allows the infection to be treated;
- both the control system and the anti-virus solution update system should be independent of the corresponding mechanisms used in the operating systems (no WSUS and Windows Update) and should be included in the anti-virus self-defense system, which eliminates the possibility of the malware intercepting the update system. In general, the number of components of the operating system, independent libraries, etc., used by the antivirus, but naturally not placed under the protection of the self-defense system, should be minimal;
- the anti-virus protection management system should ensure the fastest possible receipt of updates by protected workstations and servers;
- the anti-virus system should rely primarily on the technology of the anti-virus kernel - difficult to circumvent by malicious programs, and not on external components that may be compromised in one way or another due to misuse and / or use of vulnerabilities in external programs or libraries used in conjunction with them ( we will analyze this situation when we talk about the advantages and disadvantages of various technologies and the impact of the media on the level of security).
And finally, the question:
- In your opinion, are there currently any tests to adequately assess the quality of protection systems?
The analysis of IT mythology will continue in the next article.
