Easy management of 1C database lists
“It is better to lose a day, and then fly in five minutes” (c) m / f Wings, legs and tails.
On "Habré" there are three excellent posts about management of lists of bases in 8.x:
1. "Management of lists of bases 1C 8.2" ;
2. "How to cook hundreds of 1C bases and not go crazy" ;
3. "Managing the list of databases 1C 8.2 using Active Directory . "
Each of them contains its own piece of the puzzle from the full picture: Easy management of the lists of 1C databases.
The given construction ideology makes it easy to scale the settings, both for simple offices with one domain and for a multi-domain structure in the forest. Everyone chooses the specific implementation of the solution for themselves, but here the foundation is laid in order to get the necessary flexibility without unnecessary efforts. The decision is easily inherited. There are no scripts. Not at all. At all.
So, what are we fighting: There
are a lot of users! - bypassing 40+ users with the sole purpose of registering a new database or changing the connection settings from the old one will take a decent time. Well, those who have tech support fighters.
There are a lot of bases!- Zoo bases, test bases with easy submission 1Snikov appearing in production while still on the servers for testing. We multiply by the number of users and are horrified.
Indistinct database names! - in this place, every time I imagine how I can do the soul of the next 1Snik with my own hands for the base with the name " new2_baza2_copy " to which a bunch of processings, reports and COM connections are tied. Because it seemed logical to him SO to name a new base. The organization is one and it does not suddenly grow. And he alone and remembers everything. And never quit. And the documentation is kept by wimps. Yes, it’s always possible to quickly redo it!
Frequent user rotation!- each new user does not know what bases he needs (It often sounds: “I need EVERYTHING”), employees often change their positions, departments, organizations and, as a result, their responsibilities.
Load! Scripts! - sweet scripts scanning the entire AD forest in search of specific group names to connect a single database. And who wrote it? On what? When? Where are the comments?
Where are my bases ?! - oops. Many solutions do not allow you to save an individual list of 1C user databases and at the same time use a predefined set of databases.
Clusters 1C? DB server? - is there a difference? There may be more than one. Different versions of 1C, different databases. Technical support is trying to find the ends in order to understand exactly what exactly to register with the user on the PC.
I described the main pain.
Let's start
Six steps to happiness:
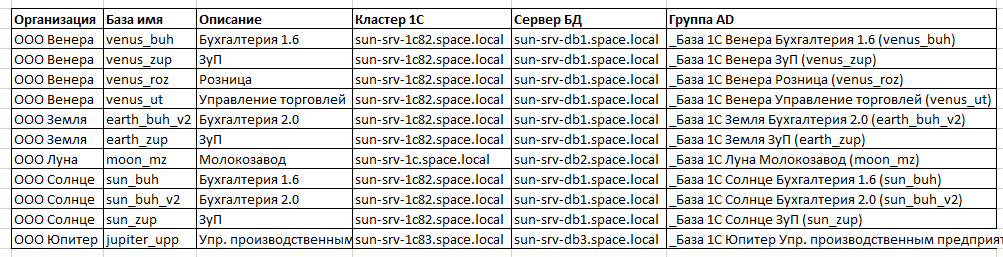
We take the table editor and 1Snikov. And we take a detailed inventory, perhaps even with our hands:
A table like this is born:
Our task is to understand what is where. Structure. Details to paint.
Creating groups for databases in Active Directory, we immediately write in the description the cluster and database server used:
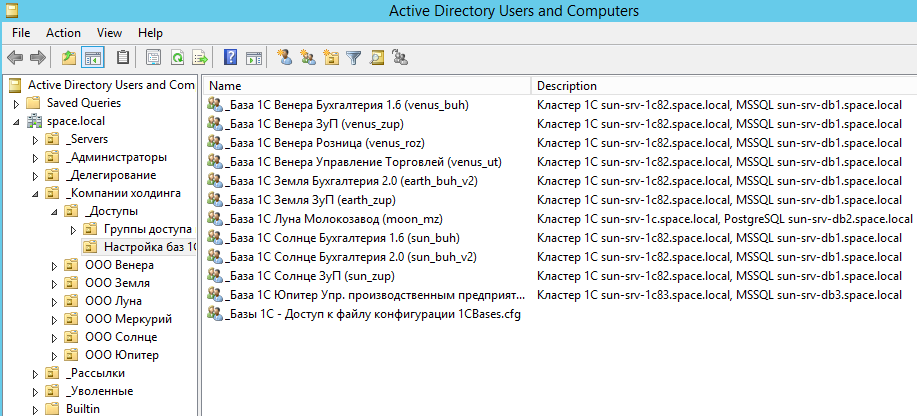
At the output, we get detailed information about each database in the Active Directory structure. Specifying the database name in the AD group name greatly facilitates the search for a group for a specific database in large infrastructures. Selected users, chose to add to the group and specified the desired database name. Op and all there. At the same time, your colleagues (or heirs) will immediately see which AD group is responsible for which base and where the base is located.
Important:
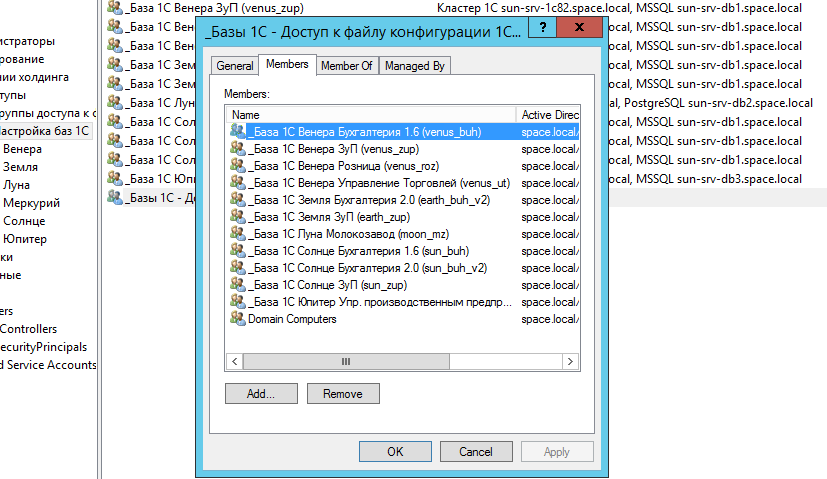
In addition to creating AD groups for each database, you must create an additional AD group “ _Bases 1C - Access to the configuration file 1CBases.cfg"- it will help us provide access to the file resource where the v8i configurations of all the bases we need are stored. We include in this group all AD groups for 1C databases. We do not forget to add new AD groups for 1C databases. We also need the Domain Computers group in its composition to enable PC accounts to access the file resource. About the nuances below.
The inventory was done, the AD groups for the databases were created, now the v8i configuration files. They store the settings for connecting to the databases: 1C cluster and the name of the database in this cluster.
We start 1C. If there is a formed list of bases, we name them beautifully and clearly.
Organization - Configuration - Configuration version. We
save them with the right button into files, we name the files by the name of the database. Carefully accumulate these wonderful v8i files in one directory. If there is no initial list, you can create one entry in the list, it will be the standard. From it, we produce new v8i configuration files by hammering the necessary information directly into the file text.
At the output, we have a file with the following contents: We
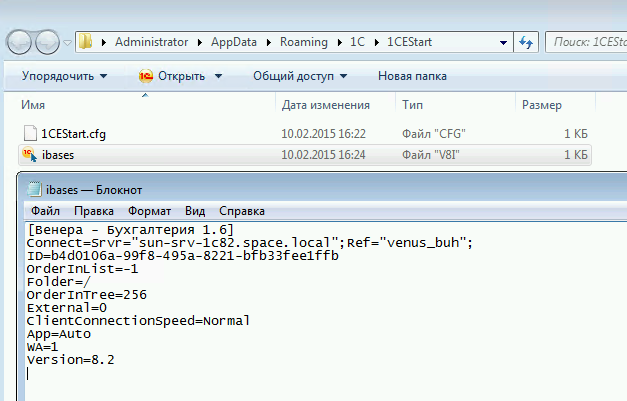
remove each file from extra lines:
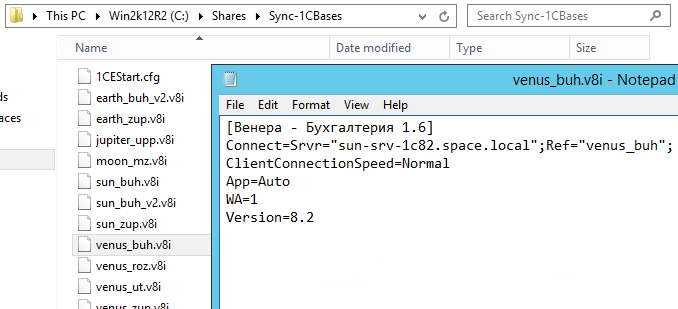
As a result, we get a certain number of v8i configuration files, as many as databases.
The next step is to edit the general database configuration file for 1C.
By default, it does not contain a list of databases at all:
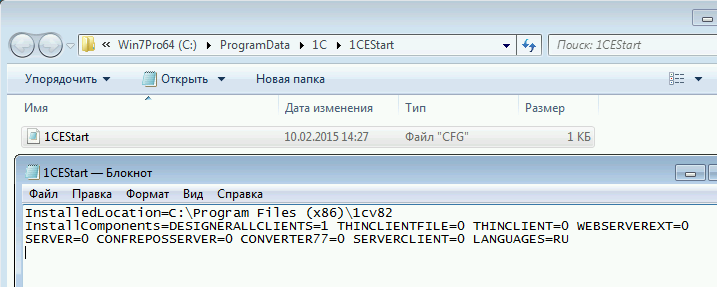
We will carry out small manipulations, and it now indicates the paths to all configuration files for v8i 1C databases.

Accessing v8i files works both with a simple network folder on a file server and with a DFS resource. Load balancing, fault tolerance? Yes! We know. We are flying.
As a result, we have a directory full of v8i configuration files for each database separately, plus a common configuration file that contains all the paths to all v8i configuration files.
Create a directory that will lie v8i configuration files for each connection to a particular database, as well as a general list of bases - file 1CEStart.cfg:
call the directory Sync-1CBases .
The ideological approach to access, to shared resources, is different for everyone. Many people prefer to put Everyone - Full control access on the shared resource itself , and then steer access at the file system level. It's easier. I prefer to cut off access right away at the level of the most shared resource, without creating additional load on the file server with unnecessary double-checks of accessibility.
We give access to the group " _Bases 1C - Access to the configuration file 1CBases.cfg " read permissions to the new network resource .
Divine manuals in one picture. Instead of a thousand words.
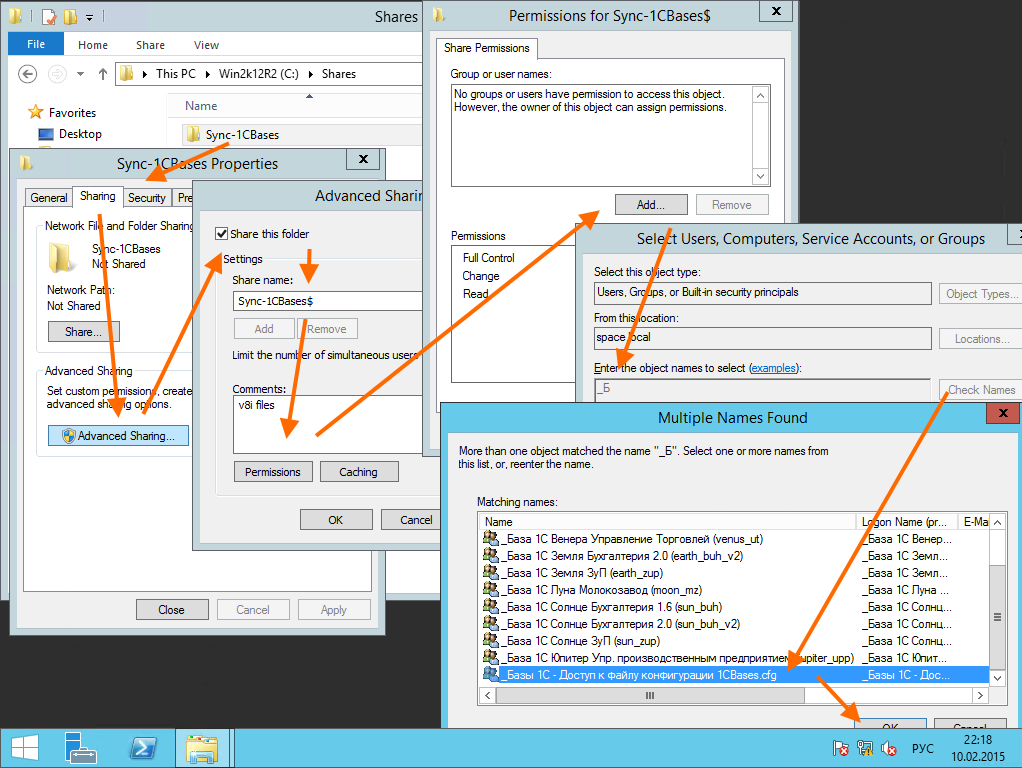
Important:
Next, we configure security at the file system level.
The very first step is to reset the default settings to the Sync-1CBases directory objects . Disable permission inheritance. We leave " SYSTEM ", local Administrators , Domain Admins . Where there is a forest, you can add enterprise administrators and / or delegated administrators. The resulting result is applied with inheritance. Immediately, not far from the checkout , add the AD group “ _Bases 1C - Access to the configuration file 1CBases.cfg ” with the right Readand only to this directory without inheritance. At this step, we get the opportunity to get to the root of the folder and get a list of files in the directory.
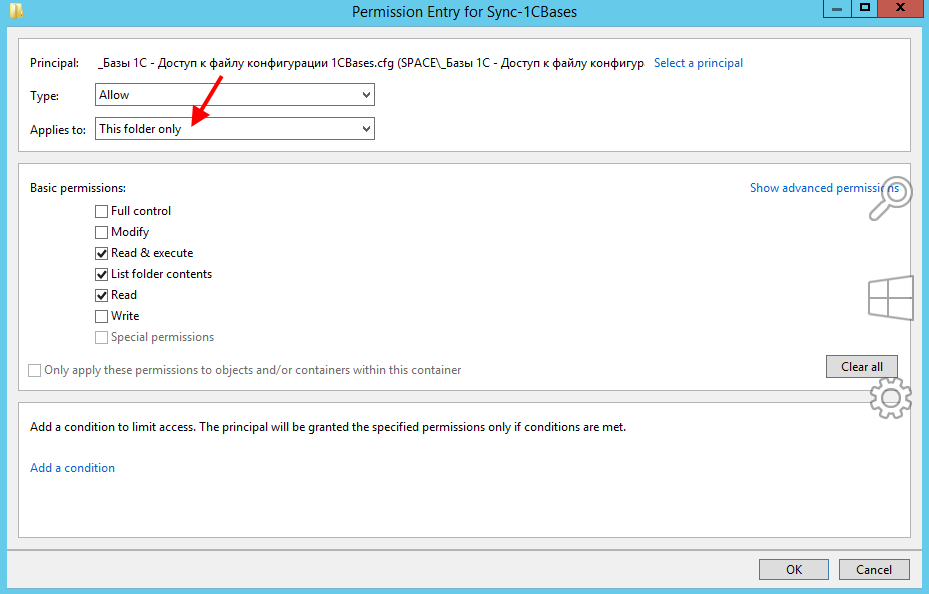
Until now, I’m not used to such an interface for setting access rights.
Next is the salt:
For the 1CEStart.cfg file , we give the right to read only to the AD group “ _Bases 1C - Access to the configuration file 1CBases.cfg ”

Then, access is granted for each v8i database configuration file your Active Directory access group:
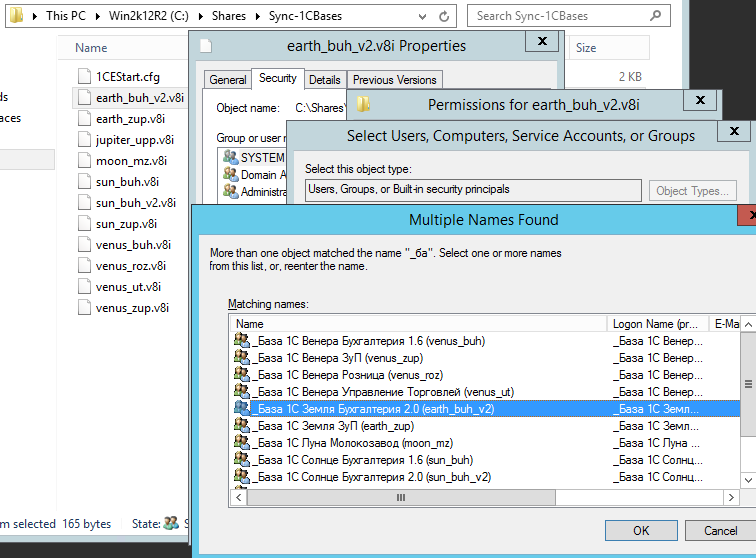
Repeat the last step until the v8i database configuration files run out.
Too many do not use group policies. Many use them neglectfully. In vain, in vain, in vain. This is a very powerful tool that makes life easier at work, even in small offices.
Create a new group policy, link it to the root of the domain. We indicate that it works only with Domain Computers :

The main revelation (or nuance) here is that the list of databases is connected not to the user, but to the PC. Unfortunately, the user cannot, with his rights, replace the configuration file located in C: \ ProgramData \ 1C \ 1CEStart \ and the PC will do it for him.
Editing the policy:
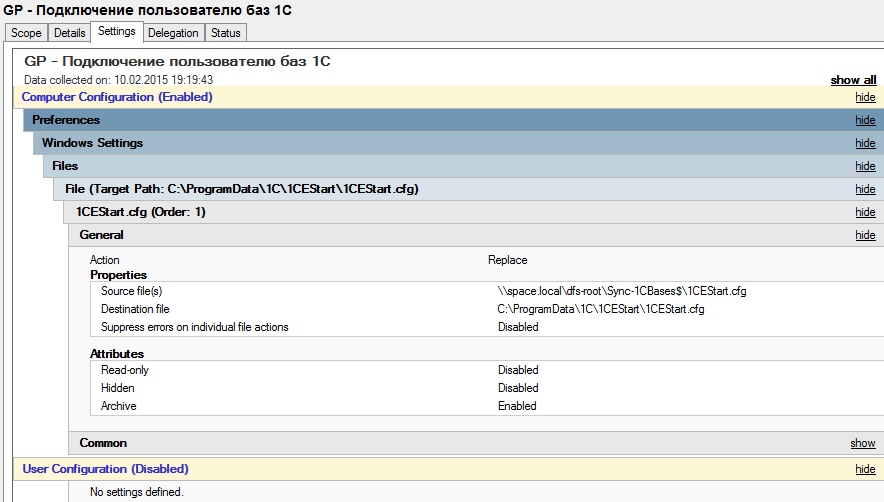
Here the task is to take the file from the shared resource and replace the local file.
What would this be done only by a PC with installed 1C, we set the conditions for the execution of group policy through Item Level Targeting .
We check the presence of installed 1C:
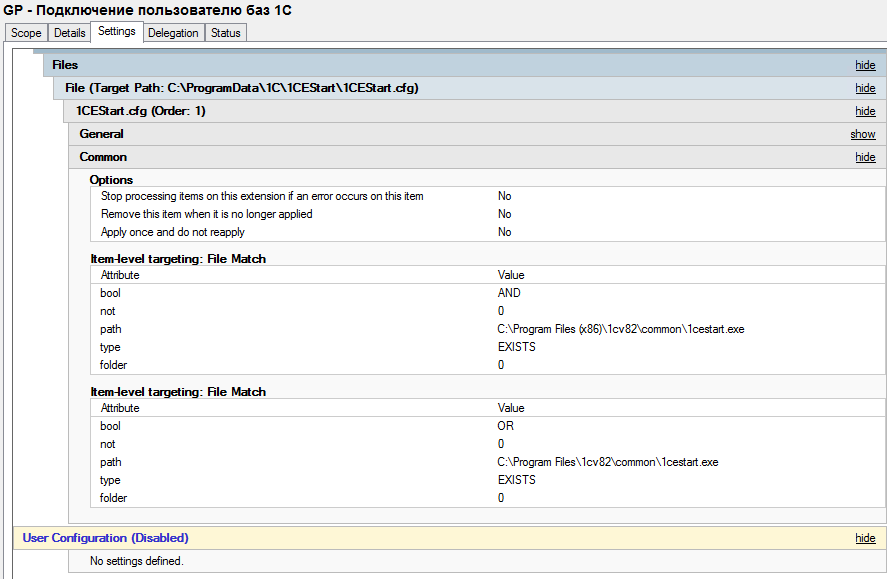
This is the most elementary check. Checks for both x86 and x64 editions of operating systems. Does not distinguish between server and client OS.
But the test conditions themselves can vary widely, applying these settings to certain organizational units, depending on the conditions for the availability of network resources and many other parameters, which makes it possible to narrow down the conditions for triggering this group policy.
The file is aligned when loading the PC, or once every 90 + - minutes.
We take the user. And we add it to the AD groups:
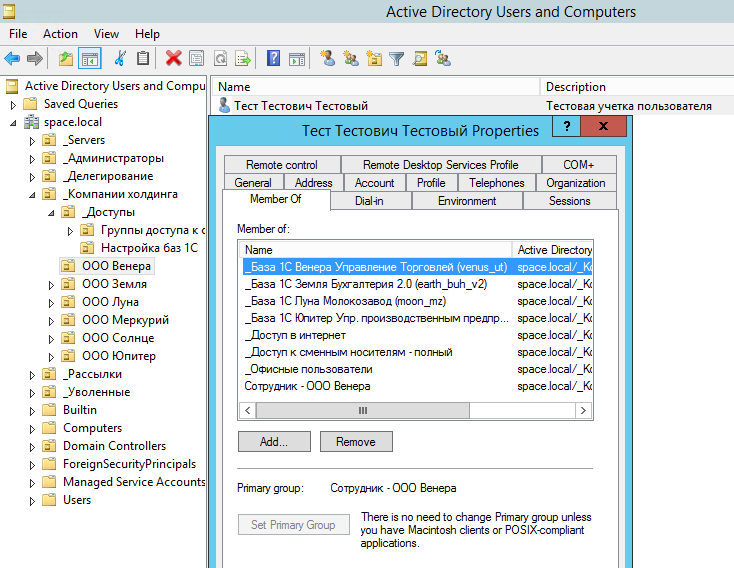
After that, we log in the user, run 1C, which reads the configuration file and connects all the v8i files to which the user has access. Result:
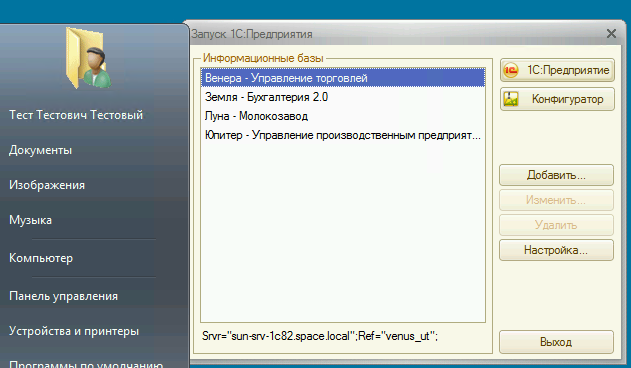
What actually achieved.
However, this solution does not affect the file C: \ Users \% username% \ AppData \ Roaming \ 1C \ 1CEStart \ ibases.v8i which stores the databases that the user himself registered. However, it can always be reset to clean the user’s database list. Group politicians in your hands!
Formally, I passed one of the many implementation options. Passed on the ideology. Additional solutions to this article can be very broad:
Automatically create a v8i file, add it to cfg, create an AD group for 1C database.
Editing access for 1C specialists for the same files.
Checking the relevance of the cfg configuration file before replacing it with a PC.
For paranoids, you can create cfg files with predefined lists, and in v8i register more than one database. In general, make the names of v8i files without indicating the name of the database.
You can change the method of delivering a cfg file to a PC, where the access rights to this file are changed in the PC configuration, and the user overwrites it with his rights.
And much more. Anything you want. Everyone is free to decide for himself.
Total: There
are a lot of users! - it does not matter.
There are a lot of bases! - entered the 1Sniki database into the registry, users received it. They didn’t make it - even the self-connected database will disappear at the next login, if the list of local databases is zeroed.
Indistinct database names! - what's the difference? You always have up-to-date information. There is no complete database information - users do not have a database.
Frequent user rotation! - Was there an application to connect the base? There is a base! Changed the place or unit, lost the base along with the dumping of rights.
Load! Scripts!- where? What for? Balancing, accurate targeting, only relevant information, ease of maintenance and support.
Where are my bases ?! - not allowed! Well, or use please. Everyone is happy.
Clusters 1C? DB server? - no confusion. Everything is already set by the settings. Techies are busy with useful things, and not figuring out to whom, where and what to prescribe, how to call names and how not to leave users in the morning without an account system due to an update.
I spent a day. That you flew in five minutes. Thanks!
Update:
Harazhitel - sisaenkov rightly noted that instead of copying cfg files to the folder C: \ ProgramData \ 1C \ 1CEStart \ , for client systems based on Windows XP you should use the variable "% ALLUSERSPROFILE% \ Application Data \ 1C \ 1CEStart \" , in while for systems based on Vista and older, you can use the option specified in the article, or the % ProgramData% \ 1C \ 1CEStart \

On "Habré" there are three excellent posts about management of lists of bases in 8.x:
1. "Management of lists of bases 1C 8.2" ;
2. "How to cook hundreds of 1C bases and not go crazy" ;
3. "Managing the list of databases 1C 8.2 using Active Directory . "
Each of them contains its own piece of the puzzle from the full picture: Easy management of the lists of 1C databases.
Prologue
The given construction ideology makes it easy to scale the settings, both for simple offices with one domain and for a multi-domain structure in the forest. Everyone chooses the specific implementation of the solution for themselves, but here the foundation is laid in order to get the necessary flexibility without unnecessary efforts. The decision is easily inherited. There are no scripts. Not at all. At all.
So, what are we fighting: There
are a lot of users! - bypassing 40+ users with the sole purpose of registering a new database or changing the connection settings from the old one will take a decent time. Well, those who have tech support fighters.
There are a lot of bases!- Zoo bases, test bases with easy submission 1Snikov appearing in production while still on the servers for testing. We multiply by the number of users and are horrified.
Indistinct database names! - in this place, every time I imagine how I can do the soul of the next 1Snik with my own hands for the base with the name " new2_baza2_copy " to which a bunch of processings, reports and COM connections are tied. Because it seemed logical to him SO to name a new base. The organization is one and it does not suddenly grow. And he alone and remembers everything. And never quit. And the documentation is kept by wimps. Yes, it’s always possible to quickly redo it!
Frequent user rotation!- each new user does not know what bases he needs (It often sounds: “I need EVERYTHING”), employees often change their positions, departments, organizations and, as a result, their responsibilities.
Load! Scripts! - sweet scripts scanning the entire AD forest in search of specific group names to connect a single database. And who wrote it? On what? When? Where are the comments?
Where are my bases ?! - oops. Many solutions do not allow you to save an individual list of 1C user databases and at the same time use a predefined set of databases.
Clusters 1C? DB server? - is there a difference? There may be more than one. Different versions of 1C, different databases. Technical support is trying to find the ends in order to understand exactly what exactly to register with the user on the PC.
I described the main pain.
Let's start
Spoiler?
1. All presented infrastructure is test and virtual. Any matches to the names of legal entities are random.
2. Forgive me for the English interface in the screenshots from the servers. I could not do otherwise.
3. Believe me, I am the leader of the group of system administrators, I know what I'm doing! (from)
2. Forgive me for the English interface in the screenshots from the servers. I could not do otherwise.
3. Believe me, I am the leader of the group of system administrators, I know what I'm doing! (from)
Six steps to happiness:
Stage 1 - Inventory
We take the table editor and 1Snikov. And we take a detailed inventory, perhaps even with our hands:
A table like this is born:

Our task is to understand what is where. Structure. Details to paint.
Stage 2 - AD groups for 1C databases
Creating groups for databases in Active Directory, we immediately write in the description the cluster and database server used:

At the output, we get detailed information about each database in the Active Directory structure. Specifying the database name in the AD group name greatly facilitates the search for a group for a specific database in large infrastructures. Selected users, chose to add to the group and specified the desired database name. Op and all there. At the same time, your colleagues (or heirs) will immediately see which AD group is responsible for which base and where the base is located.
Important:
In addition to creating AD groups for each database, you must create an additional AD group “ _Bases 1C - Access to the configuration file 1CBases.cfg"- it will help us provide access to the file resource where the v8i configurations of all the bases we need are stored. We include in this group all AD groups for 1C databases. We do not forget to add new AD groups for 1C databases. We also need the Domain Computers group in its composition to enable PC accounts to access the file resource. About the nuances below.

Stage 3 - 1C configuration files
The inventory was done, the AD groups for the databases were created, now the v8i configuration files. They store the settings for connecting to the databases: 1C cluster and the name of the database in this cluster.
We start 1C. If there is a formed list of bases, we name them beautifully and clearly.
Organization - Configuration - Configuration version. We
save them with the right button into files, we name the files by the name of the database. Carefully accumulate these wonderful v8i files in one directory. If there is no initial list, you can create one entry in the list, it will be the standard. From it, we produce new v8i configuration files by hammering the necessary information directly into the file text.
At the output, we have a file with the following contents: We

remove each file from extra lines:

As a result, we get a certain number of v8i configuration files, as many as databases.
The next step is to edit the general database configuration file for 1C.
By default, it does not contain a list of databases at all:

We will carry out small manipulations, and it now indicates the paths to all configuration files for v8i 1C databases.

Accessing v8i files works both with a simple network folder on a file server and with a DFS resource. Load balancing, fault tolerance? Yes! We know. We are flying.
As a result, we have a directory full of v8i configuration files for each database separately, plus a common configuration file that contains all the paths to all v8i configuration files.
Stage 4 - File or DFS Resource
Create a directory that will lie v8i configuration files for each connection to a particular database, as well as a general list of bases - file 1CEStart.cfg:
call the directory Sync-1CBases .
The ideological approach to access, to shared resources, is different for everyone. Many people prefer to put Everyone - Full control access on the shared resource itself , and then steer access at the file system level. It's easier. I prefer to cut off access right away at the level of the most shared resource, without creating additional load on the file server with unnecessary double-checks of accessibility.
We give access to the group " _Bases 1C - Access to the configuration file 1CBases.cfg " read permissions to the new network resource .
Divine manuals in one picture. Instead of a thousand words.

Important:
Next, we configure security at the file system level.
The very first step is to reset the default settings to the Sync-1CBases directory objects . Disable permission inheritance. We leave " SYSTEM ", local Administrators , Domain Admins . Where there is a forest, you can add enterprise administrators and / or delegated administrators. The resulting result is applied with inheritance. Immediately, not far from the checkout , add the AD group “ _Bases 1C - Access to the configuration file 1CBases.cfg ” with the right Readand only to this directory without inheritance. At this step, we get the opportunity to get to the root of the folder and get a list of files in the directory.

Next is the salt:
For the 1CEStart.cfg file , we give the right to read only to the AD group “ _Bases 1C - Access to the configuration file 1CBases.cfg ”

Then, access is granted for each v8i database configuration file your Active Directory access group:

Repeat the last step until the v8i database configuration files run out.
Stage 5 - Group Policies
Too many do not use group policies. Many use them neglectfully. In vain, in vain, in vain. This is a very powerful tool that makes life easier at work, even in small offices.
Create a new group policy, link it to the root of the domain. We indicate that it works only with Domain Computers :

The main revelation (or nuance) here is that the list of databases is connected not to the user, but to the PC. Unfortunately, the user cannot, with his rights, replace the configuration file located in C: \ ProgramData \ 1C \ 1CEStart \ and the PC will do it for him.
Editing the policy:

Here the task is to take the file from the shared resource and replace the local file.
What would this be done only by a PC with installed 1C, we set the conditions for the execution of group policy through Item Level Targeting .
We check the presence of installed 1C:

This is the most elementary check. Checks for both x86 and x64 editions of operating systems. Does not distinguish between server and client OS.
But the test conditions themselves can vary widely, applying these settings to certain organizational units, depending on the conditions for the availability of network resources and many other parameters, which makes it possible to narrow down the conditions for triggering this group policy.
The file is aligned when loading the PC, or once every 90 + - minutes.
Stage 6 - User
We take the user. And we add it to the AD groups:

After that, we log in the user, run 1C, which reads the configuration file and connects all the v8i files to which the user has access. Result:

What actually achieved.
However, this solution does not affect the file C: \ Users \% username% \ AppData \ Roaming \ 1C \ 1CEStart \ ibases.v8i which stores the databases that the user himself registered. However, it can always be reset to clean the user’s database list. Group politicians in your hands!
Epilogue
Formally, I passed one of the many implementation options. Passed on the ideology. Additional solutions to this article can be very broad:
Automatically create a v8i file, add it to cfg, create an AD group for 1C database.
Editing access for 1C specialists for the same files.
Checking the relevance of the cfg configuration file before replacing it with a PC.
For paranoids, you can create cfg files with predefined lists, and in v8i register more than one database. In general, make the names of v8i files without indicating the name of the database.
You can change the method of delivering a cfg file to a PC, where the access rights to this file are changed in the PC configuration, and the user overwrites it with his rights.
And much more. Anything you want. Everyone is free to decide for himself.
Total: There
are a lot of users! - it does not matter.
There are a lot of bases! - entered the 1Sniki database into the registry, users received it. They didn’t make it - even the self-connected database will disappear at the next login, if the list of local databases is zeroed.
Indistinct database names! - what's the difference? You always have up-to-date information. There is no complete database information - users do not have a database.
Frequent user rotation! - Was there an application to connect the base? There is a base! Changed the place or unit, lost the base along with the dumping of rights.
Load! Scripts!- where? What for? Balancing, accurate targeting, only relevant information, ease of maintenance and support.
Where are my bases ?! - not allowed! Well, or use please. Everyone is happy.
Clusters 1C? DB server? - no confusion. Everything is already set by the settings. Techies are busy with useful things, and not figuring out to whom, where and what to prescribe, how to call names and how not to leave users in the morning without an account system due to an update.
P.S
I spent a day. That you flew in five minutes. Thanks!
Update:
Harazhitel - sisaenkov rightly noted that instead of copying cfg files to the folder C: \ ProgramData \ 1C \ 1CEStart \ , for client systems based on Windows XP you should use the variable "% ALLUSERSPROFILE% \ Application Data \ 1C \ 1CEStart \" , in while for systems based on Vista and older, you can use the option specified in the article, or the % ProgramData% \ 1C \ 1CEStart \
