Banking Trojan Zeus Gameover returns in a new modification
A few days ago, researchers at Malcovery Security announced the discovery of a new modification of the most famous banking Trojan Zeus. This is a new modification of the so-called. Zeus Gameover (latest version of this banking malware). In addition to the new Zeus executable files with a modified botnet algorithm, spam mailing was recorded in e-mail, the attachment to the letters of which contains Zeus dropper. A new modification is detected by ESET as Win32 / Spy.ZBot.AAU .

The domains for communication with the management server, which are generated by the DGA algorithm of the Trojan program, confirm that it is a new version. We wrote earlierabout the operation of disabling the Zeus Gameover botnet, which was carried out by FBI and Europol in cooperation with security companies. As part of that operation, intelligence agencies also seized control of the domains Zeus used, gaining ownership of them and making it impossible for bots to receive new instructions from attackers.
A distinctive feature of the new version is the use of the Fast flux algorithmto work with a command server, instead of the previously used P2P. In the P2P scheme, there is no centralization in receiving commands from one server; instead, there are many so-called peers (other infected computers) in the botnet that can send instructions to the bot for execution. Fast flux offers a different scheme of work. In it, a domain for communicating with C&C can constantly change its purpose in the form of a computer IP address (domain association with IP), while the computer IP address over which attackers have control can be used as a system for registering a DNS record. Typically, this is a set of computers whose intruders use the IP addresses to quickly reassign the required C&C domain for them. The bot receives a list of such C&C domains through the updated DGA algorithm .
The story with Zeus has been going on for quite some time. The first versions of the bot were born in 2007 or even earlier. What distinguished Zeus from other malware was that it became the first crimeware toolkit or a full-featured tool to steal online banking data from various banks and transfer this information to an attacker’s server. To carry out such operations, it included a configuration file, which allowed attackers to quickly redirect it to the goals they needed (banking sites). Since then, several generations or versions of Zeus have appeared, the total financial damage from which is estimated at more than half a billion dollars. The number of different families or modifications of this malware and botnets based on it is already several dozen.
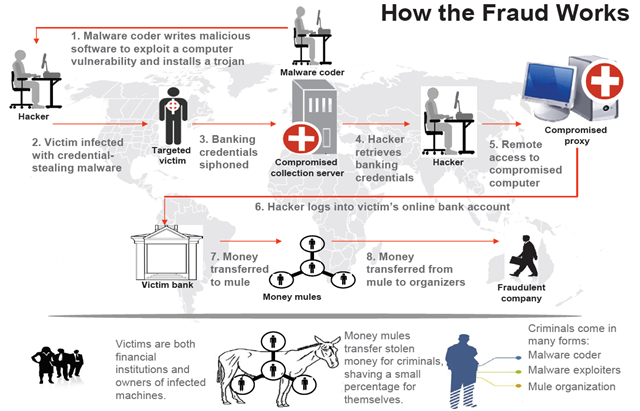
Fig. The scheme of work of cybercriminals who use the crimeware toolkit to steal funds from bank accounts.


Fig. FBI press release issued as part of the case of the arrest of "money mules", the so-called United States v. “Zeus money mules” in 2010 More than two dozen students from the former USSR were arrested, many of whom came to the United States using forged documents and carried out cashing of “dirty money” that was stolen from bank customers using Zeus. According to the investigation, in the framework of this case, more than $ 70 million was stolen.

The domains for communication with the management server, which are generated by the DGA algorithm of the Trojan program, confirm that it is a new version. We wrote earlierabout the operation of disabling the Zeus Gameover botnet, which was carried out by FBI and Europol in cooperation with security companies. As part of that operation, intelligence agencies also seized control of the domains Zeus used, gaining ownership of them and making it impossible for bots to receive new instructions from attackers.
A distinctive feature of the new version is the use of the Fast flux algorithmto work with a command server, instead of the previously used P2P. In the P2P scheme, there is no centralization in receiving commands from one server; instead, there are many so-called peers (other infected computers) in the botnet that can send instructions to the bot for execution. Fast flux offers a different scheme of work. In it, a domain for communicating with C&C can constantly change its purpose in the form of a computer IP address (domain association with IP), while the computer IP address over which attackers have control can be used as a system for registering a DNS record. Typically, this is a set of computers whose intruders use the IP addresses to quickly reassign the required C&C domain for them. The bot receives a list of such C&C domains through the updated DGA algorithm .
The story with Zeus has been going on for quite some time. The first versions of the bot were born in 2007 or even earlier. What distinguished Zeus from other malware was that it became the first crimeware toolkit or a full-featured tool to steal online banking data from various banks and transfer this information to an attacker’s server. To carry out such operations, it included a configuration file, which allowed attackers to quickly redirect it to the goals they needed (banking sites). Since then, several generations or versions of Zeus have appeared, the total financial damage from which is estimated at more than half a billion dollars. The number of different families or modifications of this malware and botnets based on it is already several dozen.

Fig. The scheme of work of cybercriminals who use the crimeware toolkit to steal funds from bank accounts.
- The author of the trojan is developing the necessary functionality of the bot.
- The operator (hacker) is responsible for distributing the compiled executable files of the Trojan. He can turn to the services of spammers to organize spam mailings, to “iframers” to redirect legitimate users of hacked sites to a trojan or other methods known in the cybercriminal world.
- The user becomes infected with a banking trojan, after which it uses a browser (in the process of which a malicious code is located) to work with online banking. The confidential data specified when working with the online banking system is sent to the attacker server.
- The operator (hacker) receives data sent by the bot in the previous step.
- The operator can use another compromised computer (proxy) to carry out fraudulent operations with the victim’s account, thus hiding the source of the attack.
- Using the proxy specified in the previous paragraph, the operator logs into the user’s online banking account using the login / password pairs stolen at step 4.
- Funds from the victim's account are transferred to several fraudulent bank accounts in small portions, and then cashed out at ATMs by various persons participating in the criminal scheme (mules).
- The organizer (coordinator) of the entire criminal scheme receives funds from the "mules", while each of them "mules" gets its share.


Fig. FBI press release issued as part of the case of the arrest of "money mules", the so-called United States v. “Zeus money mules” in 2010 More than two dozen students from the former USSR were arrested, many of whom came to the United States using forged documents and carried out cashing of “dirty money” that was stolen from bank customers using Zeus. According to the investigation, in the framework of this case, more than $ 70 million was stolen.
