DEFCON 17. Hacking 400,000 passwords, or how to explain to a roommate why the electricity bill has increased. Part 1
- Transfer
Greetings to all and thank you for making my presentation the final DEFCON conference this year. I really appreciate it and will try not to disappoint you. My name is Matt Weir, I am a graduate student at the University of Florida. Before we start talking directly about password cracking, I want to say that I work with a very good team and call its members right now. This is my supervisor, Professor, Dr. Sidir Eggrvol, who put his hand to my presentation and Professor Brenot de Medeiros. I would also like to thank the National Institute of Justice and the National Center for Criminal Research "White Collars" for funding my research.
I really appreciate it, because this help gave my research a bit of legitimacy. Because when I went to the scientific council to approve the topic of my research, I began the conversation with the fact that it was dedicated to cracking passwords. These words provoked an indignant reaction, so I had to explain that it was necessary in order, for example, to catch and bring to justice the molesters of minors and other such criminals.
Thus, the main purpose of my research is to help jurisprudence.
The law enforcement agencies are strong enough in encryption, so I was not going to help them with this, I simply wouldn’t have enough brains for that. I decided to investigate the problems associated with attacks on users, because it is much easier than hacking complex ciphers. I wanted to develop a more advanced model of how people create their passwords in real life, and then use it in an attack-resistant password strategy.
The first thing we need is to have an idea of how people create their passwords. We spent a little time just to go online and find open password lists. They appear there for various reasons, for example, some hacker hacks the site and puts a list of user passwords to say to everyone: “see how cool I am”! We collected these passwords and analyzed.
There are many hackers forums, electronic bulletin boards and the like, where we also collected passwords. Now you rarely see simple text passwords, but this is a great thing, because all we have to do is just to find them and read them. However, most passwords are hashed, so in order to understand how people create them, we first need to crack them.
In fact, this is good for us, as it forces us to focus on practical goals. I mean, we just can’t just sit back and write research papers while drinking wine. We actually have to go ahead and try to apply what we got in our password lists, and check how it works. I was really interested in how to create an effective protection against hacking and to make passwords better, using more effective password creation strategies based on the knowledge gained from hacking.
I think it's much easier to hack something instead of fixing it. In this presentation I will try to avoid a detailed description of the tools and trifles I used. I'm not going to spend the next 50 minutes parsing each command line of the J program.ohn the Ripper , which serves to recover passwords by their hashes, or analyze page by page, how often people use sports team names as passwords. I do not want to waste your time.
If you are interested in the details, you can visit my password-breaking blog www.reusablesec.blogspot.com or the site with my tools and documentation, which are freely available on the Internet at www.reusablesec.sites.google.com . Please leave your comments and feel free to say if you think we are doing something stupid. I really appreciate such comments, because it is the best way to evaluate the effectiveness of our work.
You also do not need to feverishly record anything or be afraid to skip some of the slides that flash on the screen, since this presentation is available on the conference CD, besides, you can download these slides from the Internet. I also recorded several additional tools on the disc. I’ll talk briefly about the tools used: this is our dictionary, created on the basis of the online version of RainbowCrack Tables , a few password cracking scripts, parsing scripts that we used to analyze password lists and several user password lists we compiled.
It is noteworthy that we probably have the largest collection of single-line ASCII code encodings of passwords on the Internet. So you can say that my parents can be proud of me. I note that people create passwords even in this way, so you can use it and hack them.
You can say, “Oh my God, passwords suck! Users are idiots because they create stupid passwords, and in general, we are all doomed! ” Yes, I could spend time making fun of users, because it is fun, but not at all productive. I mean, we have known for many years that the fire is hot, the water is wet, that the user will simply choose a 1-2-3 password. This is not new. But we, as a security community, have to figure out what to do about it.
Not to say that I am an optimist, but I’m not too pessimistic about the future of passwords. I mean, we are “stuck” on these stars, which need to be filled in, and we will always use them, because they are really good.
There are many different factors that allow you to get rid of any "water", leaving only safety. Password cracking becomes difficult, because people are beginning to use strong encryption, stronger password hashes, and passwords are more responsive to passwords. I think that is why there is such an interest in cracking passwords. I hope that Windows 7 will finally stick an aspen stake in the heart of XP , and we are starting to see fewer and fewer cases of using the WEP security algorithm.for Wi-Fi networks, despite the fact that it is still quite widespread around. I mean, we should work on the problem of protecting passwords from hacking instead of destroying the existing system.
This approach will actually improve the situation, so I want to focus on what constitutes a password hacking session, what techniques are used and what steps need to be taken to crack password lists.
I want to focus on two different case studies. First of all, we created a password database for hacking using CISSP data - an independent information security certification. We collected a lot of passwords everywhere, but these two sources, phpbb.com and webhostingtalk.com, were the best, because there were very large lists of passwords in the public domain.
Therefore, we first talk about hacking passwords from the phpbb.com list , and then about the results of hacking webhostingtalk.com . I will not arrange an introductory course in CISSP , because you know the language and terminology. After that, I will take a short break, and you can ask questions related to research using the TrueCrypt program , as well as talk about some passwords and non-standard passwords. So, let's talk about the basics of password cracking.

There are two different types of passwords and, accordingly, two ways to crack them, and they are very different from each other. The first is online passwords. You know from the movies that you may not have access to the site at all if you do not know the password. Therefore, you are trying to get there by picking up various usernames and passwords. The main thing is that site creators try to protect themselves from hackers with the help of additional functions, for example, limiting the number of attempts to enter authorization data.
The second way is to hack offline passwords when you download a password hash and hack it on your computer. These are big problems in computer forensics, so you need to try to crack passwords before the police break in with an arrest warrant, kicking the door open with your feet. At the same time, they will remove the hard disk on which your program will be installed for hacking TrueCrypt along with the cracked passwords. In addition, for password cracking offline requires a very powerful computer and a lot of time.
In fact, after the attacker hacked the site and downloaded all the passwords and usernames, he is only limited by the time after which he can be caught.
The question is why a hacker should crack passwords if he can simply get full access to the site through a router. The answer is that people use the same password everywhere, so it’s easier for you to access both email and bank account and PayPal account .
We did not do that. Having cracked passwords, we never used them for verification, for entrance on any site or in someone's account. I say this not because I believe that there are many federal agents in the audience here, but because this is really not good.
So, there are three different steps committed when a password is cracked. I want to differentiate them, because I will refer to them later. I had problems at each of these three stages.
The first stage concerns autonomous password cracking. Computer forensics assumes that you already have a password hash, in our case the entire hard disk of the computer was filled with this data. So, the first step you need to take is to try to guess what the user came up with for the password. To do this, you use the first attempt, suppose password123 . Then you hash it and get a set of letters and numbers 52F8A73082B1290 . In most cases, a simple and fast MD5 hashing algorithm is used . After that, you compare this set with your real user password hash, for example, 82503CA693453D1 . If it matched, you hacked the password. But since 52F8A73082B1290 ≠ 82503CA693453D1, you try again and use the monkey123 guess . You repeat it again and again, until you get bored and you do not give up this thing.

Left: as encryption experts imagine.
“His laptop is encrypted.” Let's create a million dollar decryptor and hack it! ”
“It won't go, it's a 4096-bit cipher!”
- "Heck! Our criminal plan failed ”!
Right: as it usually happens.
“His laptop is encrypted.” We’ll give him a drink and beat him with this five-dollar wrench until he tells us the password!
”-“ I agree ”!
Let's talk about the "highlights" in passwords. This information is added to the password to complicate its hacking. It happens that two different people decided to use the same password. In this case, for example, you can add different usernames to the “defcon” password , in which case the hashes will be very different from each other.

This is especially important for passwords that are stored on the network. Often, as a "highlight" to the password "microsoft"people add their own username, but in reality this is a bad idea. Because the "raisins" also protect against attacks using the hash search. Usually, a hacker simply copies all password hashes at once, and if he needs to crack a password, he simply scans the stolen hash, and this happens very quickly. But if you are using the "highlights", the hacker will not be able to do this until he hashes the hash of each particular user for the presence of "highlights" there.
Assuming that people have a “zest” for each microsoft password , then a hacker may not want to create a whole table with user names. However, he knows that among them there can be a very popular name "administrator", people are used to trusting him, so in this case a hacker can succeed.
Therefore, when creating "highlights" you need to consider such important things:
However, this method does not protect the user from attacks of a different kind, and you still have to think about how to make a password hash hack relatively expensive for a criminal.
And now let's go directly to the issue of password cracking.
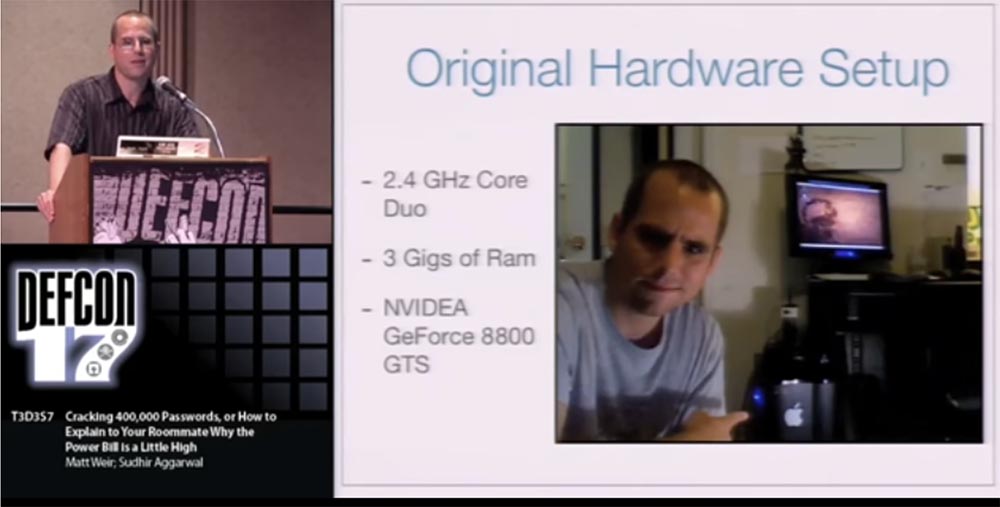
People usually ask me what kind of hardware I use when cracking passwords. I have a desktop computer with a 2.4 GHz dual-core processor, 3 GB of RAM and an NVidia GeForce 8800GTS video card , which is already 2 years old. This is not a special password cracking machine. I also use this MacBook a little bit . So all I have is 2 computers.
Unfortunately, after a couple of weeks of research, the electricity bill increased by 75%.
It is difficult to explain to your roommate when the coolers of your computers literally roar non-stop during the last 2 weeks. However, after I finished the work, the power consumption returned to normal.
Now, almost all password cracking operations I spend on a computer in the institute laboratory. I used to use the generation of the RainbowCrack Table dictionary . When you hear people say about you, if you have whole racks of something like Play Station 3 and a whole botnet for cracking passwords, you want to say: “you know, dude, I only have a laboratory Dell.” Therefore, when you consider threat modeling, it should be borne in mind that an attacker can definitely throw a lot more resources at that. For example, on hacking a site likephpBB.com . This is the phpbb software site . It was hacked on January 14, 2009, and this list was published on the Internet in early February. The attacker posted a lot of information about password hashes, site user names, e-mail accounts, and a very detailed description of the attack itself.
It was a pretty good “reading matter”, and the list itself contained about 259 thousand MD5 hashes of passwords without “highlights” and 83 thousand hashed passwords with “highlights”, which were created using the phpbb3 hashing algorithm . However, this is a new and rather rare algorithm, so in our research we only cracked passwords with traditional MD5 hashes. We excluded from consideration passwords with "highlight", because their hacking is too time consuming task, and we didn’t really figure it out. Therefore, we focused on the MD5 password list . So passwords with "highlights" are protected much better, and any hacker would prefer to deal with something easier.
But I want to emphasize once again that if you are attacked and your password list is revealed, you still need to “cure” it and take the attack as a serious event, because the attacker could later use the result of his theft.
Next, we looked at the list of passwords for a hacked webhostingtalk site.. For one or two weeks, the hacker used online password cracking, trying to hack about 117 thousand accounts. As a result, he managed to get 28,635 passwords, which accounted for 24% of the total. So, after analyzing the result, it can be said that even as a result of a powerful online attack, the hacker succeeds in cracking no more than a quarter of all available passwords.
Next, I will compare the effectiveness of online password hacking. The results are taken from the site http://www.hashkiller.com/ , most of them relate to Germany. But Babel Fishdoing much better - they not only have their own online password cracker forums, but they also track the performance of most other cracker communities. According to statistics, the success of online hacking is from 20 to 40% of all passwords that hackers have. There are MD5 hacker tools that collect hashes for online passwords from many sites. They can be downloaded from this link: http://sourceforge.net/projects/md5-utils/ . Currently there are 33 sites where these utilities can be used.
I want to warn you that there are serious privacy issues here, because if you think that those to whom you send password hashes will simply keep them for the collection, then you are a very trusting person.
Today there are several popular tools for hacking passwords.

The most popular is John the Ripper , which is free software, and I recommend it first. But the main reason for its popularity, in which it is ahead of even paid programs, is the availability of open source code. If you want to crack passwords, this program will cope with everything you want. My favorite option in JtR is STDIN . If you remember the introductory slides, then in this case I don’t need to perform stage 1 and 2, I can write my own “guesswork” program, and then transfer the results to JtR. And he will decrypt the hashes and try to crack passwords. So if you are thinking about the method of generating “riddles”, that is, variants of user passwords, you can compile the code and use this program, it is extremely powerful.
In the beginning I acted like an idiot, although it is hard to believe in it. I used the old version of this program without checking for updates, and I didn’t know that it had difficulty coping with a large list of passwords; it took forever. In January, the creators released a patch, but I found out about it too late.
Therefore, I tried to switch from JtR to the Cain & Able program (Cain and Abel), for which I am still a bit ashamed. Because JtRconstantly updated, and you can subscribe to the newsletter updates, and if it were not for my stupidity, then everything would be just perfect.
That's how much time I spent on hacking passwords, despite the problems with JtR :
The numbers are different because many people use the same passwords. In fact, this is very bad. But I'm not the only one who has achieved this success. I used DefCon contacts to talk about this topic with different people. For example, Brandon Enright hacked 95% of passwords with an MD5 hash , and he cracked 2525 passwords with which I failed, and I cracked 2677 passwords that he could not crack. For confidentiality reasons, we exchanged not simple text lists of passwords with him, but the digital form of data.
I received a letter from another person who reports that his result has reached 97%, and I believe him. Because we are still learning how to crack passwords, and I'm not the coolest hacker, but just a student who is learning this business. Probably, there are better ways to hack.
We managed to crack enough passwords with a twist, not because I had a lot of money or I was an elite hacker, but because they really were weak, and the average length of these passwords was only 7.2 characters. Only 6% of these passwords contained capital letters and only 1% contained special characters, and 51% contained only lowercase letters. This is without taking into account 5% of passwords that we could not crack.
I want to note that we were limited in resources. We could not use a brute-force attack everywherebecause they were limited in time. Therefore, we had to choose between different attack strategies, because we simply could not try them all. We had to first form an idea in our head about how the user created his password, and depending on this, choose the method of attack. Therefore, we tried to crack not all passwords, but only the most typical ones.
I want to say that a person simply needs to create a truly strong password, you just need to give it a bit of uniqueness. Do what others do, and then it will be difficult for a hacker to crack your password. Usually, all you have to do is create a password so long that it is difficult to crack it using brute-force. But it’s hard to get everyone to be unique, this trait is not “embedded” in a person by default. It is thanks to this that you manage to crack passwords.
I want to tell you about this type of attack on user passwords, like a Dictionary Attack , or a dictionary attack. When I speak of “dictionary attack”, I not only mean entering words in a dictionary, but also using word formation rules, such as adding 2 numbers at the end of words or writing a word with a capital letter.
There are two main reasons why Dictionary Attack can fail. The first is “illiteracy” when you simply do not write the word as it appears in the dictionary. For example, you write zibra123 , while a word like zibra, in the dictionary no. The second is when you do not use word formation rules when writing complex words, that is, you do not just add the numbers 123 to the end of the password. So if you want to create a truly strong password, you should not use the words in the dictionary.
If you want to use many word forms, you should reduce the size of the input dictionary, and vice versa, the fewer word formation rules you use, the larger the dictionary can be.
People tend to create a redundant collection of input dictionaries. This causes them to become vulnerable to brute-force attacks.. I call it the “crazy cat-girl” syndrome, which causes 50-60 cats in the house, and they foul everything around. Therefore, using input dictionaries when creating passwords, think about how voluminous they should be, and do not over-inflate the vocabulary. Think about what is best to use for security - 1 dictionary or 40.
25:15 min.
Continuation:
DEFCON conference 17. Hacking 400,000 passwords, or how to explain to a roommate why the electricity bill has increased. Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?

I really appreciate it, because this help gave my research a bit of legitimacy. Because when I went to the scientific council to approve the topic of my research, I began the conversation with the fact that it was dedicated to cracking passwords. These words provoked an indignant reaction, so I had to explain that it was necessary in order, for example, to catch and bring to justice the molesters of minors and other such criminals.
Thus, the main purpose of my research is to help jurisprudence.
The law enforcement agencies are strong enough in encryption, so I was not going to help them with this, I simply wouldn’t have enough brains for that. I decided to investigate the problems associated with attacks on users, because it is much easier than hacking complex ciphers. I wanted to develop a more advanced model of how people create their passwords in real life, and then use it in an attack-resistant password strategy.
The first thing we need is to have an idea of how people create their passwords. We spent a little time just to go online and find open password lists. They appear there for various reasons, for example, some hacker hacks the site and puts a list of user passwords to say to everyone: “see how cool I am”! We collected these passwords and analyzed.
There are many hackers forums, electronic bulletin boards and the like, where we also collected passwords. Now you rarely see simple text passwords, but this is a great thing, because all we have to do is just to find them and read them. However, most passwords are hashed, so in order to understand how people create them, we first need to crack them.
In fact, this is good for us, as it forces us to focus on practical goals. I mean, we just can’t just sit back and write research papers while drinking wine. We actually have to go ahead and try to apply what we got in our password lists, and check how it works. I was really interested in how to create an effective protection against hacking and to make passwords better, using more effective password creation strategies based on the knowledge gained from hacking.
I think it's much easier to hack something instead of fixing it. In this presentation I will try to avoid a detailed description of the tools and trifles I used. I'm not going to spend the next 50 minutes parsing each command line of the J program.ohn the Ripper , which serves to recover passwords by their hashes, or analyze page by page, how often people use sports team names as passwords. I do not want to waste your time.
If you are interested in the details, you can visit my password-breaking blog www.reusablesec.blogspot.com or the site with my tools and documentation, which are freely available on the Internet at www.reusablesec.sites.google.com . Please leave your comments and feel free to say if you think we are doing something stupid. I really appreciate such comments, because it is the best way to evaluate the effectiveness of our work.
You also do not need to feverishly record anything or be afraid to skip some of the slides that flash on the screen, since this presentation is available on the conference CD, besides, you can download these slides from the Internet. I also recorded several additional tools on the disc. I’ll talk briefly about the tools used: this is our dictionary, created on the basis of the online version of RainbowCrack Tables , a few password cracking scripts, parsing scripts that we used to analyze password lists and several user password lists we compiled.
It is noteworthy that we probably have the largest collection of single-line ASCII code encodings of passwords on the Internet. So you can say that my parents can be proud of me. I note that people create passwords even in this way, so you can use it and hack them.

You can say, “Oh my God, passwords suck! Users are idiots because they create stupid passwords, and in general, we are all doomed! ” Yes, I could spend time making fun of users, because it is fun, but not at all productive. I mean, we have known for many years that the fire is hot, the water is wet, that the user will simply choose a 1-2-3 password. This is not new. But we, as a security community, have to figure out what to do about it.
Not to say that I am an optimist, but I’m not too pessimistic about the future of passwords. I mean, we are “stuck” on these stars, which need to be filled in, and we will always use them, because they are really good.
There are many different factors that allow you to get rid of any "water", leaving only safety. Password cracking becomes difficult, because people are beginning to use strong encryption, stronger password hashes, and passwords are more responsive to passwords. I think that is why there is such an interest in cracking passwords. I hope that Windows 7 will finally stick an aspen stake in the heart of XP , and we are starting to see fewer and fewer cases of using the WEP security algorithm.for Wi-Fi networks, despite the fact that it is still quite widespread around. I mean, we should work on the problem of protecting passwords from hacking instead of destroying the existing system.
This approach will actually improve the situation, so I want to focus on what constitutes a password hacking session, what techniques are used and what steps need to be taken to crack password lists.
I want to focus on two different case studies. First of all, we created a password database for hacking using CISSP data - an independent information security certification. We collected a lot of passwords everywhere, but these two sources, phpbb.com and webhostingtalk.com, were the best, because there were very large lists of passwords in the public domain.
Therefore, we first talk about hacking passwords from the phpbb.com list , and then about the results of hacking webhostingtalk.com . I will not arrange an introductory course in CISSP , because you know the language and terminology. After that, I will take a short break, and you can ask questions related to research using the TrueCrypt program , as well as talk about some passwords and non-standard passwords. So, let's talk about the basics of password cracking.

There are two different types of passwords and, accordingly, two ways to crack them, and they are very different from each other. The first is online passwords. You know from the movies that you may not have access to the site at all if you do not know the password. Therefore, you are trying to get there by picking up various usernames and passwords. The main thing is that site creators try to protect themselves from hackers with the help of additional functions, for example, limiting the number of attempts to enter authorization data.
The second way is to hack offline passwords when you download a password hash and hack it on your computer. These are big problems in computer forensics, so you need to try to crack passwords before the police break in with an arrest warrant, kicking the door open with your feet. At the same time, they will remove the hard disk on which your program will be installed for hacking TrueCrypt along with the cracked passwords. In addition, for password cracking offline requires a very powerful computer and a lot of time.
In fact, after the attacker hacked the site and downloaded all the passwords and usernames, he is only limited by the time after which he can be caught.
The question is why a hacker should crack passwords if he can simply get full access to the site through a router. The answer is that people use the same password everywhere, so it’s easier for you to access both email and bank account and PayPal account .
We did not do that. Having cracked passwords, we never used them for verification, for entrance on any site or in someone's account. I say this not because I believe that there are many federal agents in the audience here, but because this is really not good.
So, there are three different steps committed when a password is cracked. I want to differentiate them, because I will refer to them later. I had problems at each of these three stages.
The first stage concerns autonomous password cracking. Computer forensics assumes that you already have a password hash, in our case the entire hard disk of the computer was filled with this data. So, the first step you need to take is to try to guess what the user came up with for the password. To do this, you use the first attempt, suppose password123 . Then you hash it and get a set of letters and numbers 52F8A73082B1290 . In most cases, a simple and fast MD5 hashing algorithm is used . After that, you compare this set with your real user password hash, for example, 82503CA693453D1 . If it matched, you hacked the password. But since 52F8A73082B1290 ≠ 82503CA693453D1, you try again and use the monkey123 guess . You repeat it again and again, until you get bored and you do not give up this thing.

Left: as encryption experts imagine.
“His laptop is encrypted.” Let's create a million dollar decryptor and hack it! ”
“It won't go, it's a 4096-bit cipher!”
- "Heck! Our criminal plan failed ”!
Right: as it usually happens.
“His laptop is encrypted.” We’ll give him a drink and beat him with this five-dollar wrench until he tells us the password!
”-“ I agree ”!
Let's talk about the "highlights" in passwords. This information is added to the password to complicate its hacking. It happens that two different people decided to use the same password. In this case, for example, you can add different usernames to the “defcon” password , in which case the hashes will be very different from each other.

This is especially important for passwords that are stored on the network. Often, as a "highlight" to the password "microsoft"people add their own username, but in reality this is a bad idea. Because the "raisins" also protect against attacks using the hash search. Usually, a hacker simply copies all password hashes at once, and if he needs to crack a password, he simply scans the stolen hash, and this happens very quickly. But if you are using the "highlights", the hacker will not be able to do this until he hashes the hash of each particular user for the presence of "highlights" there.
Assuming that people have a “zest” for each microsoft password , then a hacker may not want to create a whole table with user names. However, he knows that among them there can be a very popular name "administrator", people are used to trusting him, so in this case a hacker can succeed.
Therefore, when creating "highlights" you need to consider such important things:
- this is not a secret. Well, if you keep the principle of creating "highlights" for passwords in secret, but first of all you need to ensure the security of the password itself;
- users do not need to know this. I do not mean that the user should not know that passwords are stored on the server, I mean that the "highlight" must be unique for each user;
- “Highlight” will protect if an attacker targets only one user, and not a whole bunch of passwords. In this case, it prevents hash search attacks.
However, this method does not protect the user from attacks of a different kind, and you still have to think about how to make a password hash hack relatively expensive for a criminal.
And now let's go directly to the issue of password cracking.

People usually ask me what kind of hardware I use when cracking passwords. I have a desktop computer with a 2.4 GHz dual-core processor, 3 GB of RAM and an NVidia GeForce 8800GTS video card , which is already 2 years old. This is not a special password cracking machine. I also use this MacBook a little bit . So all I have is 2 computers.
Unfortunately, after a couple of weeks of research, the electricity bill increased by 75%.
It is difficult to explain to your roommate when the coolers of your computers literally roar non-stop during the last 2 weeks. However, after I finished the work, the power consumption returned to normal.
Now, almost all password cracking operations I spend on a computer in the institute laboratory. I used to use the generation of the RainbowCrack Table dictionary . When you hear people say about you, if you have whole racks of something like Play Station 3 and a whole botnet for cracking passwords, you want to say: “you know, dude, I only have a laboratory Dell.” Therefore, when you consider threat modeling, it should be borne in mind that an attacker can definitely throw a lot more resources at that. For example, on hacking a site likephpBB.com . This is the phpbb software site . It was hacked on January 14, 2009, and this list was published on the Internet in early February. The attacker posted a lot of information about password hashes, site user names, e-mail accounts, and a very detailed description of the attack itself.

It was a pretty good “reading matter”, and the list itself contained about 259 thousand MD5 hashes of passwords without “highlights” and 83 thousand hashed passwords with “highlights”, which were created using the phpbb3 hashing algorithm . However, this is a new and rather rare algorithm, so in our research we only cracked passwords with traditional MD5 hashes. We excluded from consideration passwords with "highlight", because their hacking is too time consuming task, and we didn’t really figure it out. Therefore, we focused on the MD5 password list . So passwords with "highlights" are protected much better, and any hacker would prefer to deal with something easier.
But I want to emphasize once again that if you are attacked and your password list is revealed, you still need to “cure” it and take the attack as a serious event, because the attacker could later use the result of his theft.
Next, we looked at the list of passwords for a hacked webhostingtalk site.. For one or two weeks, the hacker used online password cracking, trying to hack about 117 thousand accounts. As a result, he managed to get 28,635 passwords, which accounted for 24% of the total. So, after analyzing the result, it can be said that even as a result of a powerful online attack, the hacker succeeds in cracking no more than a quarter of all available passwords.
Next, I will compare the effectiveness of online password hacking. The results are taken from the site http://www.hashkiller.com/ , most of them relate to Germany. But Babel Fishdoing much better - they not only have their own online password cracker forums, but they also track the performance of most other cracker communities. According to statistics, the success of online hacking is from 20 to 40% of all passwords that hackers have. There are MD5 hacker tools that collect hashes for online passwords from many sites. They can be downloaded from this link: http://sourceforge.net/projects/md5-utils/ . Currently there are 33 sites where these utilities can be used.
I want to warn you that there are serious privacy issues here, because if you think that those to whom you send password hashes will simply keep them for the collection, then you are a very trusting person.
Today there are several popular tools for hacking passwords.

The most popular is John the Ripper , which is free software, and I recommend it first. But the main reason for its popularity, in which it is ahead of even paid programs, is the availability of open source code. If you want to crack passwords, this program will cope with everything you want. My favorite option in JtR is STDIN . If you remember the introductory slides, then in this case I don’t need to perform stage 1 and 2, I can write my own “guesswork” program, and then transfer the results to JtR. And he will decrypt the hashes and try to crack passwords. So if you are thinking about the method of generating “riddles”, that is, variants of user passwords, you can compile the code and use this program, it is extremely powerful.
In the beginning I acted like an idiot, although it is hard to believe in it. I used the old version of this program without checking for updates, and I didn’t know that it had difficulty coping with a large list of passwords; it took forever. In January, the creators released a patch, but I found out about it too late.
Therefore, I tried to switch from JtR to the Cain & Able program (Cain and Abel), for which I am still a bit ashamed. Because JtRconstantly updated, and you can subscribe to the newsletter updates, and if it were not for my stupidity, then everything would be just perfect.
That's how much time I spent on hacking passwords, despite the problems with JtR :
- 4 hours - 38% of passwords cracked;
- 1 week - 62% of passwords cracked;
- 1 month and 1 week - 89%;
- in total, 98% of passwords have been cracked, 95% of them with a unique MD5 hash .
The numbers are different because many people use the same passwords. In fact, this is very bad. But I'm not the only one who has achieved this success. I used DefCon contacts to talk about this topic with different people. For example, Brandon Enright hacked 95% of passwords with an MD5 hash , and he cracked 2525 passwords with which I failed, and I cracked 2677 passwords that he could not crack. For confidentiality reasons, we exchanged not simple text lists of passwords with him, but the digital form of data.
I received a letter from another person who reports that his result has reached 97%, and I believe him. Because we are still learning how to crack passwords, and I'm not the coolest hacker, but just a student who is learning this business. Probably, there are better ways to hack.
We managed to crack enough passwords with a twist, not because I had a lot of money or I was an elite hacker, but because they really were weak, and the average length of these passwords was only 7.2 characters. Only 6% of these passwords contained capital letters and only 1% contained special characters, and 51% contained only lowercase letters. This is without taking into account 5% of passwords that we could not crack.
I want to note that we were limited in resources. We could not use a brute-force attack everywherebecause they were limited in time. Therefore, we had to choose between different attack strategies, because we simply could not try them all. We had to first form an idea in our head about how the user created his password, and depending on this, choose the method of attack. Therefore, we tried to crack not all passwords, but only the most typical ones.
I want to say that a person simply needs to create a truly strong password, you just need to give it a bit of uniqueness. Do what others do, and then it will be difficult for a hacker to crack your password. Usually, all you have to do is create a password so long that it is difficult to crack it using brute-force. But it’s hard to get everyone to be unique, this trait is not “embedded” in a person by default. It is thanks to this that you manage to crack passwords.
I want to tell you about this type of attack on user passwords, like a Dictionary Attack , or a dictionary attack. When I speak of “dictionary attack”, I not only mean entering words in a dictionary, but also using word formation rules, such as adding 2 numbers at the end of words or writing a word with a capital letter.
There are two main reasons why Dictionary Attack can fail. The first is “illiteracy” when you simply do not write the word as it appears in the dictionary. For example, you write zibra123 , while a word like zibra, in the dictionary no. The second is when you do not use word formation rules when writing complex words, that is, you do not just add the numbers 123 to the end of the password. So if you want to create a truly strong password, you should not use the words in the dictionary.
If you want to use many word forms, you should reduce the size of the input dictionary, and vice versa, the fewer word formation rules you use, the larger the dictionary can be.

People tend to create a redundant collection of input dictionaries. This causes them to become vulnerable to brute-force attacks.. I call it the “crazy cat-girl” syndrome, which causes 50-60 cats in the house, and they foul everything around. Therefore, using input dictionaries when creating passwords, think about how voluminous they should be, and do not over-inflate the vocabulary. Think about what is best to use for security - 1 dictionary or 40.
25:15 min.
Continuation:
DEFCON conference 17. Hacking 400,000 passwords, or how to explain to a roommate why the electricity bill has increased. Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
