Classification of user authentication mechanisms and their overview
While writing my dissertation on the protection of information on the development of a new user authentication algorithm, I faced the task of classifying existing authentication mechanisms so that I could determine which class my development belongs to.
I was faced with the fact that there is no generally accepted classification, and each author has her own, if any. Therefore, I offer you my classification, synthesized from those that I met during the work. And I would like to hear the opinion of experts how rational, adequate and useful it is. And most importantly, have you heard her somewhere before?
After analyzing the existing user authentication mechanisms, I identified 3 main characteristics that each of them has: The
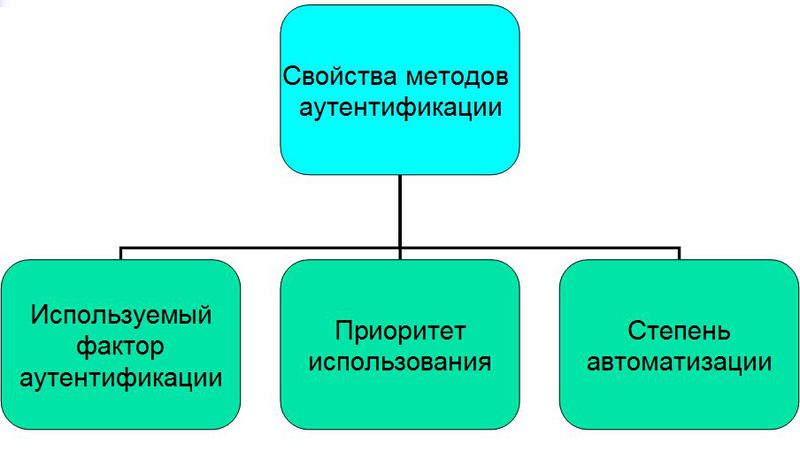
degree of automationmay be complete or incomplete . This refers to the automation of authentication by the system, not the user. Those. the authentication system on the hub is fully automated, and the authentication system using the intercom is not fully automated, because guest authentication requires host intervention.
The priority of use is the order in which the user uses this authentication method.
Basic authentication methodAs the name implies, this method is used for regular login. The most common of them is password entry, which is used in the vast majority of computer systems. A less common way is to use hardware identifiers, which are used to write access keys or user passwords.
Two-factor authentication is also popular in the corporate sector. As a rule, this is understood as a combination of an e-token and a PIN code entered by the user, but there are also more exotic combinations consisting of a biometric scanner and a hardware identifier or user password.
Fallback Authentication MethodIn case of loss of password or e-token, or hacking of an account, backup authentication methods come into effect. However, these are not so much authentication methods as password reset mechanisms.
Two methods are most common: the answer to the "secret question" and sending the password to the trusted mailbox specified during registration. These methods are included in the gentleman's set of any self-respecting information service.
There are many interesting modifications to this authentication method. For example, one of the first was the proposal to use their own "secret questions" [1]. What was almost immediately implemented by leading providers [2].
You can also give an example of an advanced backup authentication system based on questions from the online dating database. There are many such questions, they are simple in themselves, but in the aggregate of them one can quite clearly imagine the character of a person. When contacting, the system asks part of the questions, of which the user answered during registration, if he is able to correctly answer most of them, then authentication is considered successful [3].
A very similar idea was described in recent works [4, 5]. Both of them tried to integrate authentication based on many simple “security questions” into the PKI architecture. And if in the first work Randy Baden, Neil Spring and Bobi Bhatachardzhi tried to generate a common encryption key for two friends based on answers to such “secret questions” compiled by users [4], then in the second work the authorization server with the base acted as the second user personal data [5].
There are no less original ideas about using user information, for example, everyone knows captcha (and how annoying it can be): hard-to-read combinations of letters and numbers that have to be entered in order to, say, complete registration. And although its task is to protect information services from the ubiquitous bots, Facebook engineers decided to cross it with “secret questions” and use it as a backup authentication system. Not long ago, Social Authentication [6] was introduced on Facebook, which is fundamentally the wrong name. The user is shown several photos of his friends, and he must correctly enter the names of friends.
As mentioned at the beginning, the second way is to send a password to a trusted mailbox. In general, the concept of shifting responsibility for authenticating a person from one side to the other is not new. Authenticating users through an alternate email address shifts the responsibility of authentication to the provider, that alternate address. It should be added that since the box is not the main one, it is used less often, and therefore the probability of forgetting the password or the answer to the "secret question" becomes much higher. True, since the number of cell phones sold in Russia exceeded its total population, many providers have the opportunity to send new passwords using sms messages. For the first time, this system was used by banks for additional authentication of transactions [7, 8], after which, having proved its effectiveness, it was adopted by other Internet services. But such a system also has its drawbacks inherent in all hardware identifiers. Phones are very often lost, stolen or broken. For example, in a 2008 article, it is reported that in New York taxis alone more than 60,000 mobile devices are forgotten annually [9].
last-resort mechanism ("last resort")Despite all the minuses and weaknesses of such mechanisms for backing up access to accounts, leading Internet companies are forced to use them, because an alternative to this is the use of “last-resort” authentication [10], which can be translated as “last resort” authentication, that is, a mechanism , which resorted to in the most extreme cases, when all other methods were powerless. At the moment, this means contacting information system administrators or special customer support departments, which is prohibitively expensive considering that only two of the largest mail providers have more than a billion active users per year [11, 12]. But even such departments are almost defenseless against social engineering, as the legendary hacker Kevin Mitnik wrote in his book in 2002 [13].
The authentication factor used - authentication is the process of comparing the information provided by the user with the reference. Depending on the type of information, it can be attributed to one of the four main factors, or to a combination thereof.
The Knowledge Factor (Password Authentication) is "what you know."
The first and most common authentication mechanism at the moment is to enter something that is known only to the user, for example, a password or an answer to a secret question. Theoretically, this is the easiest and safest authentication method, since it has sufficient cryptographic strength, it is simple and cheap to implement, and all that is needed from the user is to remember an 8-12-character combination of letters, numbers and various characters. However, in practice, everything is completely different.
First, users, as a rule, set weak passwords, which is connected with the physiology of a person, more precisely, his brain. Our thinking is associative and directly related to speech, we think in images, each of which has a name, so as a password we choose the name of one of them. Thus, we can find most of the passwords set by users in a regular dictionary, and therefore they are easily selected by dictionary search. A lot of articles have been written about the weak cryptographic strength of user-selected passwords. One of the oldest dates back to 1990. In it, Daniel Klein describes how, having armed himself with a dictionary of 62,727 words, in a couple of weeks he was able to pick up passwords for 3,340 accounts, which amounted to 24.2% of the total [14]. It is worth noting two factors:
1. People have not set more complex passwords since.
2. According to the "Moore's Law", the computing power of computers has since grown more than 16 thousand times.
Of course, since then a lot of research has been carried out and on their basis many systems for constructing complex passwords based on mnemonic phrases have been proposed. But in percentage terms, few people use them.
In addition, in spite of any miracle systems, with the increasing complexity of the password, it is becoming increasingly difficult to remember. A 2004 SafeNet study found that 47% of respondents forgot their passwords during the year [15]. And with the increase in the number of accounts from various computer systems, which are becoming more and more every year, the situation is even worse. The ability to remember passwords was studied at the Wu laboratory in 2007. After the first week, 12.5% of participants forgot their six-character alphanumeric passwords. Of the participants who were supposed to remember passwords for five accounts, 25% forgot at least one [16].
In addition, with an increase in password complexity, the number of errors when entering it also increases. For example, Brostoff and Saiss noticed that permission to enter up to ten incorrect passwords in a row reduces the number of requests to reset them [17]. Actually, after this study, many companies adjusted their password policies.
But even this is not the worst. A study conducted by John Leydon in 2003 revealed an appalling tendency for office workers to give their passwords to strangers for a nominal fee. The study involved 152 people. He was asked a series of questions, one of which asked for the user's password, and 75% of respondents immediately called him. They revealed their password in exchange for a trinket worth less than one pound [18].
The next most common authentication mechanism is usually used if the password is still lost. Then the user is asked to answer the so-called "secret question", the answer to which he indicated when registering an account. It is this system that is used by 4 leading mail providers AOL, Google (Gmail), Microsoft (Hotmail), and Yahoo! [19].
However, the cryptographic strength of such “question and answer”, chosen by users, is even less than that of passwords chosen by them. In 2009, a study report was published at the IEEE Security and Privacy conference, which was attended by 130 people. The results showed that slightly less than a third of the subjects — 28 percent — were able to “guess” the answer to the secret password, if they knew their opponent closely. If the opponent was completely unfamiliar, 17 percent of the subjects guessed the answer to the question. However, the final result largely depends on the complexity of the question posed. For example, a question about a user's favorite team or his favorite city will not be a big problem in 30 and 57 percent of cases, respectively. But even for questions of a personal nature - the city of birth, or pet name - the cracker gives the correct answer in 45 and 40 percent of cases, respectively. In addition, after 3 to 6 months, 49 participants were asked to recall their answers, 16% forgot them [20]. Earlier in 2008, Ariel Rabkin conducted a similar study, stating that many of the “secret questions” were either not applicable to more than 15% of the general public, unforgettable, ambiguous, easily guessed even if there was no information about the victim, or easily guessed with minimal knowledge of the victim [21]. Similar work took place earlier in 1996 [22] and in 1990 [23]. They also explored the ability to remember and guess answers to “secret questions”. And they showed similar results, namely: spouses and close friends could guess 33% -39% of the answers, and 20% -22% forgot their answers within 3 months.
An interesting work was published the year before last. Her goal was to find out the cryptographic strength of the answers to the "secret questions" by themselves. To this end, the authors have compiled a huge database (about 269 million) of names, surnames, pet names, dates and birthdays of users. When analyzing these data, it turned out, however, it did not surprise me that they obey the Zipf distribution, a special case of which is the “Pareto law”, i.e. 20% of names and dates accounted for 80% of users. As a result, it turned out that the cryptographic strength of the answers to these “secret questions” corresponds to the cryptographic strength of the encryption key from 8 to 23 bits long, depending on the prevalence of a particular name or surname [24].
In 2005, V. Griffin and M. Jacobson conducted a study that revealed that the answers to the most popular “secret questions” can be found in open sources. This was brilliantly confirmed in practice during the 2008 presidential election in the United States, when, using a "secret question", the account of Sarah Palin, a candidate from the Republicans, was hacked [25].
Real Factor (Hardware Authentication)“What you own.” The second most popular authentication factor. First of all, this refers to hardware-software systems for identification and authentication (SIA) or input devices for identification features [26]. The SIA includes hardware identifiers, input-output devices (readers, contact devices, adapters, system board connectors, etc.) and the corresponding software. Identifiers are designed to store unique identification features. In addition, they can store and process sensitive data. I / O devices and software exchange data between the identifier and the protected system.
In electronic SIA identification signs are represented in the form of a digital code stored in the identifier memory. According to the method of data exchange between the identifier and the input-output device, electronic SIA are divided into:
• contact:
o iButton - information button - information "tablet";
o smart cards - smart cards;
o USB keys or USB tokens (token - identification sign, marker);
• contactless:
o RFID identifiers - radio-frequency identification - radio frequency identifiers;
o smart cards.
Contact reading implies direct contact of the identifier with the input-output device. The non-contact (remote) exchange method does not require a clear positioning of the identifier and the input-output device. Reading or writing data occurs when the identifier is brought to a certain distance to the input-output device.
SIA based on smart cards and radio frequency identifiers can be assigned to the older one by the time of their creation, iButton to the middle one, and USB keys to the younger generation.
When discussing the reliability of SIA, they usually consider the most important and at the same time the weakest link in the system - the identifier. In turn, the reliability of identifiers is associated with the degree of their protection from mechanical influences, the influence of temperature, external electromagnetic fields, aggressive media, dust, moisture, as well as from attacks aimed at opening chips that store sensitive data.
The developers of iButton identifiers ensure the safety of the characteristics of their products with a mechanical shock of 500g, falling from a height of 1.5 m onto a concrete floor, an operating temperature range of -40 to 70 ° C, exposure to electromagnetic fields and the atmosphere. This is facilitated by the sealed steel case of the identifier, which maintains strength with a million contacts with the input-output device. The memory of some identifiers (DS1991, DS1963S) is protected from access. The life of the iButton ID is 10 years.
The disadvantages of SIA based on iButton include the lack of cryptographic tools built into the identifiers that implement data encryption during storage and transfer to a computer. Therefore, iButton is usually used in conjunction with other systems entrusted with encryption functions.
Of course, in terms of mechanical reliability, radio frequency identifiers, smart cards and USB keys are inferior to iButton. Plastic is difficult to compete with steel. Failure of the card due to mechanical damage is not such a rare event. The ten-year studies carried out during the implementation of the French GIE Carte Bancaire project over 22 million cards showed that the probability of their failure for a number of reasons (which also includes mechanical damage) is 0.022.
The bottleneck of USB keys is the resource of their USB connectors. The developers of these identifiers even include this indicator in the technical specifications of products. For example, for eToken family identifiers, the guaranteed number of connections is at least 5,000 times.
The advantage of radio frequency identifiers, smart cards and USB keys is that they include a secure non-volatile memory and a cryptographic processor to increase the level of protection of devices. However, the attacking side is not asleep, coming up with a variety of ways to reveal secret information.
Many papers have been published that describe a variety of attacks on identifier chips. These studies are both theoretical and practical. Theoretical autopsy methods include, but are not limited to, Bellcore attacks, differential distortion analysis DFA (Differential Fault Analysis) and DPA (Differential Power Analysis). Practical methods include glitching and physical attacks aimed at unpacking the chip and extracting the necessary information.
As far as possible, developers of cryptographic processors adequately respond to attacks using various mechanisms of external and internal protection. External protection mechanisms include the installation of sensors (capacitive or optical sensor), coating the chip with a metal layer, special adhesives, etc., internal ones include bus encryption, random clocking, repeated calculations, noise generation.
In general, due to the cost of hardware identifiers, they are mainly used in business where convenience, reliability and high cryptographic strength are required. There are only two main disadvantages: they can be taken away or lost and they can break.
Biofactor (Biometric Authentication)“That which is part of you.” Biometric data, the removal of which, as a rule, requires special software and hardware - the so-called biometric scanners, which differ in the nature of the data being read.
Static methods based biometric scanners:
• Fingerprint recognition. This is the most common static method of biometric identification, which is based on the uniqueness for each person of the pattern of papillary patterns on the fingers. The fingerprint image obtained using a special scanner is converted into a digital code (convolution) and compared with the previously entered template (reference) or a set of templates;
• Hand geometry recognition. This static method is based on recognition of the geometry of the hand, which is also a unique biometric characteristic of a person. Using a special device that allows you to get a three-dimensional image of the hand (some manufacturers scan the shape of several fingers), the measurements necessary to obtain a unique digital convolution identifying a person are obtained;
• Iris recognition. This recognition method is based on the uniqueness of the iris pattern. To implement the method, you need a camera that allows you to get an image of the human eye with sufficient resolution, and specialized software that allows you to select from the received image a picture of the iris of the eye, which is used to construct a digital code for identifying a person.
Dynamic based biometric scanners:
• Handwriting recognition. As a rule, for this dynamic method of identification of a person, his signature is used (sometimes writing a code word). The digital identification code is generated by the dynamic characteristics of the spelling, that is, a convolution is built for identification, which includes information on the graphic parameters of the signature, the temporal characteristics of the signature and the dynamics of pressure on the surface, depending on the capabilities of the equipment (graphics tablet, PDA screen, etc. .);
• Recognition by keyboard handwriting. The method is generally similar to the above, but instead of signing it uses a certain code word, and only a standard keyboard is required from the equipment. The main characteristic by which the convolution for identification is built is the dynamics of the set of a code word;
• Voice recognition. Currently, the development of this one of the oldest technologies has accelerated, as it is expected to be widely used in the construction of intelligent buildings. There are many ways to build a voice identification code: as a rule, these are various combinations of frequency and statistical characteristics of the latter.
In general, for many of the above methods, quite expensive equipment and no less expensive software are required. There are quite good developments in this area, but they will not soon become the same standard as the above methods. Moreover, with the development of technology, the role of biometrics as a means of authentication will decrease, since getting an attacker access to such data is becoming easier. You can record a voice, photograph your face and eyes, and scan your fingerprints. Then create a computer model, and print the mask on a 3D printer. As a result, biometrics will become more a means of identification.
Social Factor (Social Authentication)“Those who know you.” As the last factor, you can use someone who knows you, well, of course not you, but a legal user. Such a system can be called based on trusted authentication. For example, in organizations, the responsibility for authenticating a user who has forgotten or lost a password is often transferred to the system administrator, security service, or other technical personnel. Microsoft has long used a trust-based account recovery form for its own employees: if an employee forgot his credentials, his manager or colleagues could request a temporary password on his behalf [27]. Such a mechanism, by definition, requires the intervention of another person, and is often applicable in small systems of small and medium-sized companies, where the system administrator can make time to generate a new password. In large companies and corporations, there are entire departments dealing with similar problems. Therefore, this authentication method is currently one of the most expensive. However, Facebook is a pioneer in this area. They were the first to introduce an automated system of social authentication called “trusted friends”, which probably saved a lot of money on those support.
I hope someone finds this article useful.
REFERENCES
1. M. Just. Designing authentication systems with challenge questions. In LF Cranor and S. Garfield, editors, Security and Usability: Designing Secure Systems that People Can Use, pages 143–155, Sebastopol, CA, 2005. O'Reilly Media, Inc.
2. B. Sullivan. 'forgot your password?' may be weakest link. MSNBC Red Tape Chronicles, Aug. 26, 2008. URL: redtape.msnbc.com/2008/08/almost-everyone.html
3. M. Jakobsson, E. Stolterman, S. Wetzel, and L. Yang. Love and authentication. In CHI '08: Proceeding of the Twenty-Sixth Annual SIGCHI Conference on Human Factors in Computing Systems, pages 197–200, New York, NY, USA, 2008. ACM.
4. Identifying Close Friends on the Internet - Randy Baden, Neil Spring, Bobby Bhattacharjee
5. FaceTrust: Assessing the Credibility of Online Personas via Social Networks - Michael Sirivianos, Kyungbaek Kim, Xiaowei Yang
6. Social Authentication. Alex Rice URL: blog.facebook.com/blog.php?post=486790652130 (accessed January 2011).
7. T. Pullar-Strecker. NZ bank adds security online. Sidney Morning Herald, 8 November 2004. Referenced 2006 AT www.smh.com.au THE .
8. CommonwealthBank. NetBank NetCode SMS, 2008. URL: www.commbank.com.au/netbank/netcodesms .
9. CREDANT Technologies. Mountains of mobiles left in the back of New York cabs, 16, 2008. URL:www.credant.com/mountains-of-mobiles-left-in-the-back-of-new-york-cabs.html .
10. S. Schechter, S. Egelman, and RW Reeder. It's not what you know, but who you know: A social approach to last-resort authentication. In CHI '09: Proceedings of the ACM SIGCHI Conference on Human Factors in Computing Systems, Boston, MA, 2009. ACM.
11. J. Kremer. Happy 10th birthday, Yahoo! Mail, Oct. 2007. URL: ycorpblog.com/2007/10/08/happy-10th-birthday-yahoo-mail .
12. Microsoft Corporation. Windows live hotmail fact sheet, May 2007. URL: www.microsoft.com/presspass/newsroom/msn/factsheet/hotmail.mspx .
13. KD Mitnick and WL Simon. The Art of Deception: Controlling the Human Element of Security. Wiley, 2002.
14. DV Klein. Foiling the cracker: A survey of and improvements to, password security. In UNIX Security II: USENIX Workshop Proceedings, pages 5-14, Berkeley, CA, 1990.
15. SafeNet, Inc. 2004 annual password survey results, 2005. URL: www.safenet-inc.com/news/view.asp?news ID = 239.
16. K.-PL Vu, RW Proctor, A. Bhargav-Spantzel, B.-LB Tai, J. Cook, and EE Schultz. Improving password security and memorability to protect persona and organizational information. Int. J. Hum. Comput. Stud., 65 (8): 744–757, 2007.
17. S. Brostoff and AM Sasse. Ten strikes and you're out: Increasing the number of login attempts can improve password usability. In Proceedings of CHI 2003 Workshop on HCI and Security Systems, 2003.
18. J. Leyden. Office workers give away passwords for a cheap pen. The Register, April 18, 2003. Referenced 2006 at www.theregister.co.uk .
19. HP Ltd. Top 20 websites, 2008. URL: www.hitwise.com/datacenter/rankings.php .
20. S. Schechter, AJB Brush, and S. Egelman. It's no secret: Measuring the security and reliability of authentication via `secret 'questions. In IEEE Security and Privacy. IEEE,
2009.21. Rabkin. Personal knowledge questions for fallback authentication: security questions in the era of facebook. In SOUPS '08: Proceedings of the 4th Symposium on Usable Privacy and Security, pages 13-23, New York, NY, USA, 2008. ACM.
22. J. Podd, J. Bunnell, and R. Henderson. Cost-effective computer security: Cognitive and associative passwords. In OZCHI '96: Proceedings of the 6th Australian Conference on Computer-Human Interaction (OZCHI '96), page 304, Washington, DC, USA, 1996. IEEE Computer Society.
23. M. Zviran and WJ Haga. User authentication by cognitive passwords: an empirical assessment. In JCIT: Proceedings of the Fifth Jerusalem Conference on Information technology, pages 137–144, Los Alamitos, CA, USA, 1990. IEEE Computer Society Press.
24. Joseph Bonneau, University of Cambridge, Mike Just, Greg Matthews, What's in a Name? Evaluating Statistical Attacks on Personal Knowledge Questions. In Financial Cryptography and Data Security '10
25. T. Bridis. Hacker impersonated Palin, stole email password, Sept. 18, 2008. Associated Press.
26. GOST R 51241-98
27. S. Schechter, S. Egelman, and RW Reeder. It's not what you know, but who you know: A social approach to last-resort authentication. In CHI '09: Proceedings of the ACM SIGCHI Conference on Human Factors in Computing Systems, Boston, MA, 2009. ACM.
I was faced with the fact that there is no generally accepted classification, and each author has her own, if any. Therefore, I offer you my classification, synthesized from those that I met during the work. And I would like to hear the opinion of experts how rational, adequate and useful it is. And most importantly, have you heard her somewhere before?
After analyzing the existing user authentication mechanisms, I identified 3 main characteristics that each of them has: The

degree of automationmay be complete or incomplete . This refers to the automation of authentication by the system, not the user. Those. the authentication system on the hub is fully automated, and the authentication system using the intercom is not fully automated, because guest authentication requires host intervention.
The priority of use is the order in which the user uses this authentication method.
Basic authentication methodAs the name implies, this method is used for regular login. The most common of them is password entry, which is used in the vast majority of computer systems. A less common way is to use hardware identifiers, which are used to write access keys or user passwords.
Two-factor authentication is also popular in the corporate sector. As a rule, this is understood as a combination of an e-token and a PIN code entered by the user, but there are also more exotic combinations consisting of a biometric scanner and a hardware identifier or user password.
Fallback Authentication MethodIn case of loss of password or e-token, or hacking of an account, backup authentication methods come into effect. However, these are not so much authentication methods as password reset mechanisms.
Two methods are most common: the answer to the "secret question" and sending the password to the trusted mailbox specified during registration. These methods are included in the gentleman's set of any self-respecting information service.
There are many interesting modifications to this authentication method. For example, one of the first was the proposal to use their own "secret questions" [1]. What was almost immediately implemented by leading providers [2].
You can also give an example of an advanced backup authentication system based on questions from the online dating database. There are many such questions, they are simple in themselves, but in the aggregate of them one can quite clearly imagine the character of a person. When contacting, the system asks part of the questions, of which the user answered during registration, if he is able to correctly answer most of them, then authentication is considered successful [3].
A very similar idea was described in recent works [4, 5]. Both of them tried to integrate authentication based on many simple “security questions” into the PKI architecture. And if in the first work Randy Baden, Neil Spring and Bobi Bhatachardzhi tried to generate a common encryption key for two friends based on answers to such “secret questions” compiled by users [4], then in the second work the authorization server with the base acted as the second user personal data [5].
There are no less original ideas about using user information, for example, everyone knows captcha (and how annoying it can be): hard-to-read combinations of letters and numbers that have to be entered in order to, say, complete registration. And although its task is to protect information services from the ubiquitous bots, Facebook engineers decided to cross it with “secret questions” and use it as a backup authentication system. Not long ago, Social Authentication [6] was introduced on Facebook, which is fundamentally the wrong name. The user is shown several photos of his friends, and he must correctly enter the names of friends.
As mentioned at the beginning, the second way is to send a password to a trusted mailbox. In general, the concept of shifting responsibility for authenticating a person from one side to the other is not new. Authenticating users through an alternate email address shifts the responsibility of authentication to the provider, that alternate address. It should be added that since the box is not the main one, it is used less often, and therefore the probability of forgetting the password or the answer to the "secret question" becomes much higher. True, since the number of cell phones sold in Russia exceeded its total population, many providers have the opportunity to send new passwords using sms messages. For the first time, this system was used by banks for additional authentication of transactions [7, 8], after which, having proved its effectiveness, it was adopted by other Internet services. But such a system also has its drawbacks inherent in all hardware identifiers. Phones are very often lost, stolen or broken. For example, in a 2008 article, it is reported that in New York taxis alone more than 60,000 mobile devices are forgotten annually [9].
last-resort mechanism ("last resort")Despite all the minuses and weaknesses of such mechanisms for backing up access to accounts, leading Internet companies are forced to use them, because an alternative to this is the use of “last-resort” authentication [10], which can be translated as “last resort” authentication, that is, a mechanism , which resorted to in the most extreme cases, when all other methods were powerless. At the moment, this means contacting information system administrators or special customer support departments, which is prohibitively expensive considering that only two of the largest mail providers have more than a billion active users per year [11, 12]. But even such departments are almost defenseless against social engineering, as the legendary hacker Kevin Mitnik wrote in his book in 2002 [13].
The authentication factor used - authentication is the process of comparing the information provided by the user with the reference. Depending on the type of information, it can be attributed to one of the four main factors, or to a combination thereof.
The Knowledge Factor (Password Authentication) is "what you know."
The first and most common authentication mechanism at the moment is to enter something that is known only to the user, for example, a password or an answer to a secret question. Theoretically, this is the easiest and safest authentication method, since it has sufficient cryptographic strength, it is simple and cheap to implement, and all that is needed from the user is to remember an 8-12-character combination of letters, numbers and various characters. However, in practice, everything is completely different.
First, users, as a rule, set weak passwords, which is connected with the physiology of a person, more precisely, his brain. Our thinking is associative and directly related to speech, we think in images, each of which has a name, so as a password we choose the name of one of them. Thus, we can find most of the passwords set by users in a regular dictionary, and therefore they are easily selected by dictionary search. A lot of articles have been written about the weak cryptographic strength of user-selected passwords. One of the oldest dates back to 1990. In it, Daniel Klein describes how, having armed himself with a dictionary of 62,727 words, in a couple of weeks he was able to pick up passwords for 3,340 accounts, which amounted to 24.2% of the total [14]. It is worth noting two factors:
1. People have not set more complex passwords since.
2. According to the "Moore's Law", the computing power of computers has since grown more than 16 thousand times.
Of course, since then a lot of research has been carried out and on their basis many systems for constructing complex passwords based on mnemonic phrases have been proposed. But in percentage terms, few people use them.
In addition, in spite of any miracle systems, with the increasing complexity of the password, it is becoming increasingly difficult to remember. A 2004 SafeNet study found that 47% of respondents forgot their passwords during the year [15]. And with the increase in the number of accounts from various computer systems, which are becoming more and more every year, the situation is even worse. The ability to remember passwords was studied at the Wu laboratory in 2007. After the first week, 12.5% of participants forgot their six-character alphanumeric passwords. Of the participants who were supposed to remember passwords for five accounts, 25% forgot at least one [16].
In addition, with an increase in password complexity, the number of errors when entering it also increases. For example, Brostoff and Saiss noticed that permission to enter up to ten incorrect passwords in a row reduces the number of requests to reset them [17]. Actually, after this study, many companies adjusted their password policies.
But even this is not the worst. A study conducted by John Leydon in 2003 revealed an appalling tendency for office workers to give their passwords to strangers for a nominal fee. The study involved 152 people. He was asked a series of questions, one of which asked for the user's password, and 75% of respondents immediately called him. They revealed their password in exchange for a trinket worth less than one pound [18].
The next most common authentication mechanism is usually used if the password is still lost. Then the user is asked to answer the so-called "secret question", the answer to which he indicated when registering an account. It is this system that is used by 4 leading mail providers AOL, Google (Gmail), Microsoft (Hotmail), and Yahoo! [19].
However, the cryptographic strength of such “question and answer”, chosen by users, is even less than that of passwords chosen by them. In 2009, a study report was published at the IEEE Security and Privacy conference, which was attended by 130 people. The results showed that slightly less than a third of the subjects — 28 percent — were able to “guess” the answer to the secret password, if they knew their opponent closely. If the opponent was completely unfamiliar, 17 percent of the subjects guessed the answer to the question. However, the final result largely depends on the complexity of the question posed. For example, a question about a user's favorite team or his favorite city will not be a big problem in 30 and 57 percent of cases, respectively. But even for questions of a personal nature - the city of birth, or pet name - the cracker gives the correct answer in 45 and 40 percent of cases, respectively. In addition, after 3 to 6 months, 49 participants were asked to recall their answers, 16% forgot them [20]. Earlier in 2008, Ariel Rabkin conducted a similar study, stating that many of the “secret questions” were either not applicable to more than 15% of the general public, unforgettable, ambiguous, easily guessed even if there was no information about the victim, or easily guessed with minimal knowledge of the victim [21]. Similar work took place earlier in 1996 [22] and in 1990 [23]. They also explored the ability to remember and guess answers to “secret questions”. And they showed similar results, namely: spouses and close friends could guess 33% -39% of the answers, and 20% -22% forgot their answers within 3 months.
An interesting work was published the year before last. Her goal was to find out the cryptographic strength of the answers to the "secret questions" by themselves. To this end, the authors have compiled a huge database (about 269 million) of names, surnames, pet names, dates and birthdays of users. When analyzing these data, it turned out, however, it did not surprise me that they obey the Zipf distribution, a special case of which is the “Pareto law”, i.e. 20% of names and dates accounted for 80% of users. As a result, it turned out that the cryptographic strength of the answers to these “secret questions” corresponds to the cryptographic strength of the encryption key from 8 to 23 bits long, depending on the prevalence of a particular name or surname [24].
In 2005, V. Griffin and M. Jacobson conducted a study that revealed that the answers to the most popular “secret questions” can be found in open sources. This was brilliantly confirmed in practice during the 2008 presidential election in the United States, when, using a "secret question", the account of Sarah Palin, a candidate from the Republicans, was hacked [25].
Real Factor (Hardware Authentication)“What you own.” The second most popular authentication factor. First of all, this refers to hardware-software systems for identification and authentication (SIA) or input devices for identification features [26]. The SIA includes hardware identifiers, input-output devices (readers, contact devices, adapters, system board connectors, etc.) and the corresponding software. Identifiers are designed to store unique identification features. In addition, they can store and process sensitive data. I / O devices and software exchange data between the identifier and the protected system.
In electronic SIA identification signs are represented in the form of a digital code stored in the identifier memory. According to the method of data exchange between the identifier and the input-output device, electronic SIA are divided into:
• contact:
o iButton - information button - information "tablet";
o smart cards - smart cards;
o USB keys or USB tokens (token - identification sign, marker);
• contactless:
o RFID identifiers - radio-frequency identification - radio frequency identifiers;
o smart cards.
Contact reading implies direct contact of the identifier with the input-output device. The non-contact (remote) exchange method does not require a clear positioning of the identifier and the input-output device. Reading or writing data occurs when the identifier is brought to a certain distance to the input-output device.
SIA based on smart cards and radio frequency identifiers can be assigned to the older one by the time of their creation, iButton to the middle one, and USB keys to the younger generation.
When discussing the reliability of SIA, they usually consider the most important and at the same time the weakest link in the system - the identifier. In turn, the reliability of identifiers is associated with the degree of their protection from mechanical influences, the influence of temperature, external electromagnetic fields, aggressive media, dust, moisture, as well as from attacks aimed at opening chips that store sensitive data.
The developers of iButton identifiers ensure the safety of the characteristics of their products with a mechanical shock of 500g, falling from a height of 1.5 m onto a concrete floor, an operating temperature range of -40 to 70 ° C, exposure to electromagnetic fields and the atmosphere. This is facilitated by the sealed steel case of the identifier, which maintains strength with a million contacts with the input-output device. The memory of some identifiers (DS1991, DS1963S) is protected from access. The life of the iButton ID is 10 years.
The disadvantages of SIA based on iButton include the lack of cryptographic tools built into the identifiers that implement data encryption during storage and transfer to a computer. Therefore, iButton is usually used in conjunction with other systems entrusted with encryption functions.
Of course, in terms of mechanical reliability, radio frequency identifiers, smart cards and USB keys are inferior to iButton. Plastic is difficult to compete with steel. Failure of the card due to mechanical damage is not such a rare event. The ten-year studies carried out during the implementation of the French GIE Carte Bancaire project over 22 million cards showed that the probability of their failure for a number of reasons (which also includes mechanical damage) is 0.022.
The bottleneck of USB keys is the resource of their USB connectors. The developers of these identifiers even include this indicator in the technical specifications of products. For example, for eToken family identifiers, the guaranteed number of connections is at least 5,000 times.
The advantage of radio frequency identifiers, smart cards and USB keys is that they include a secure non-volatile memory and a cryptographic processor to increase the level of protection of devices. However, the attacking side is not asleep, coming up with a variety of ways to reveal secret information.
Many papers have been published that describe a variety of attacks on identifier chips. These studies are both theoretical and practical. Theoretical autopsy methods include, but are not limited to, Bellcore attacks, differential distortion analysis DFA (Differential Fault Analysis) and DPA (Differential Power Analysis). Practical methods include glitching and physical attacks aimed at unpacking the chip and extracting the necessary information.
As far as possible, developers of cryptographic processors adequately respond to attacks using various mechanisms of external and internal protection. External protection mechanisms include the installation of sensors (capacitive or optical sensor), coating the chip with a metal layer, special adhesives, etc., internal ones include bus encryption, random clocking, repeated calculations, noise generation.
In general, due to the cost of hardware identifiers, they are mainly used in business where convenience, reliability and high cryptographic strength are required. There are only two main disadvantages: they can be taken away or lost and they can break.
Biofactor (Biometric Authentication)“That which is part of you.” Biometric data, the removal of which, as a rule, requires special software and hardware - the so-called biometric scanners, which differ in the nature of the data being read.
Static methods based biometric scanners:
• Fingerprint recognition. This is the most common static method of biometric identification, which is based on the uniqueness for each person of the pattern of papillary patterns on the fingers. The fingerprint image obtained using a special scanner is converted into a digital code (convolution) and compared with the previously entered template (reference) or a set of templates;
• Hand geometry recognition. This static method is based on recognition of the geometry of the hand, which is also a unique biometric characteristic of a person. Using a special device that allows you to get a three-dimensional image of the hand (some manufacturers scan the shape of several fingers), the measurements necessary to obtain a unique digital convolution identifying a person are obtained;
• Iris recognition. This recognition method is based on the uniqueness of the iris pattern. To implement the method, you need a camera that allows you to get an image of the human eye with sufficient resolution, and specialized software that allows you to select from the received image a picture of the iris of the eye, which is used to construct a digital code for identifying a person.
Dynamic based biometric scanners:
• Handwriting recognition. As a rule, for this dynamic method of identification of a person, his signature is used (sometimes writing a code word). The digital identification code is generated by the dynamic characteristics of the spelling, that is, a convolution is built for identification, which includes information on the graphic parameters of the signature, the temporal characteristics of the signature and the dynamics of pressure on the surface, depending on the capabilities of the equipment (graphics tablet, PDA screen, etc. .);
• Recognition by keyboard handwriting. The method is generally similar to the above, but instead of signing it uses a certain code word, and only a standard keyboard is required from the equipment. The main characteristic by which the convolution for identification is built is the dynamics of the set of a code word;
• Voice recognition. Currently, the development of this one of the oldest technologies has accelerated, as it is expected to be widely used in the construction of intelligent buildings. There are many ways to build a voice identification code: as a rule, these are various combinations of frequency and statistical characteristics of the latter.
In general, for many of the above methods, quite expensive equipment and no less expensive software are required. There are quite good developments in this area, but they will not soon become the same standard as the above methods. Moreover, with the development of technology, the role of biometrics as a means of authentication will decrease, since getting an attacker access to such data is becoming easier. You can record a voice, photograph your face and eyes, and scan your fingerprints. Then create a computer model, and print the mask on a 3D printer. As a result, biometrics will become more a means of identification.
Social Factor (Social Authentication)“Those who know you.” As the last factor, you can use someone who knows you, well, of course not you, but a legal user. Such a system can be called based on trusted authentication. For example, in organizations, the responsibility for authenticating a user who has forgotten or lost a password is often transferred to the system administrator, security service, or other technical personnel. Microsoft has long used a trust-based account recovery form for its own employees: if an employee forgot his credentials, his manager or colleagues could request a temporary password on his behalf [27]. Such a mechanism, by definition, requires the intervention of another person, and is often applicable in small systems of small and medium-sized companies, where the system administrator can make time to generate a new password. In large companies and corporations, there are entire departments dealing with similar problems. Therefore, this authentication method is currently one of the most expensive. However, Facebook is a pioneer in this area. They were the first to introduce an automated system of social authentication called “trusted friends”, which probably saved a lot of money on those support.
I hope someone finds this article useful.
REFERENCES
1. M. Just. Designing authentication systems with challenge questions. In LF Cranor and S. Garfield, editors, Security and Usability: Designing Secure Systems that People Can Use, pages 143–155, Sebastopol, CA, 2005. O'Reilly Media, Inc.
2. B. Sullivan. 'forgot your password?' may be weakest link. MSNBC Red Tape Chronicles, Aug. 26, 2008. URL: redtape.msnbc.com/2008/08/almost-everyone.html
3. M. Jakobsson, E. Stolterman, S. Wetzel, and L. Yang. Love and authentication. In CHI '08: Proceeding of the Twenty-Sixth Annual SIGCHI Conference on Human Factors in Computing Systems, pages 197–200, New York, NY, USA, 2008. ACM.
4. Identifying Close Friends on the Internet - Randy Baden, Neil Spring, Bobby Bhattacharjee
5. FaceTrust: Assessing the Credibility of Online Personas via Social Networks - Michael Sirivianos, Kyungbaek Kim, Xiaowei Yang
6. Social Authentication. Alex Rice URL: blog.facebook.com/blog.php?post=486790652130 (accessed January 2011).
7. T. Pullar-Strecker. NZ bank adds security online. Sidney Morning Herald, 8 November 2004. Referenced 2006 AT www.smh.com.au THE .
8. CommonwealthBank. NetBank NetCode SMS, 2008. URL: www.commbank.com.au/netbank/netcodesms .
9. CREDANT Technologies. Mountains of mobiles left in the back of New York cabs, 16, 2008. URL:www.credant.com/mountains-of-mobiles-left-in-the-back-of-new-york-cabs.html .
10. S. Schechter, S. Egelman, and RW Reeder. It's not what you know, but who you know: A social approach to last-resort authentication. In CHI '09: Proceedings of the ACM SIGCHI Conference on Human Factors in Computing Systems, Boston, MA, 2009. ACM.
11. J. Kremer. Happy 10th birthday, Yahoo! Mail, Oct. 2007. URL: ycorpblog.com/2007/10/08/happy-10th-birthday-yahoo-mail .
12. Microsoft Corporation. Windows live hotmail fact sheet, May 2007. URL: www.microsoft.com/presspass/newsroom/msn/factsheet/hotmail.mspx .
13. KD Mitnick and WL Simon. The Art of Deception: Controlling the Human Element of Security. Wiley, 2002.
14. DV Klein. Foiling the cracker: A survey of and improvements to, password security. In UNIX Security II: USENIX Workshop Proceedings, pages 5-14, Berkeley, CA, 1990.
15. SafeNet, Inc. 2004 annual password survey results, 2005. URL: www.safenet-inc.com/news/view.asp?news ID = 239.
16. K.-PL Vu, RW Proctor, A. Bhargav-Spantzel, B.-LB Tai, J. Cook, and EE Schultz. Improving password security and memorability to protect persona and organizational information. Int. J. Hum. Comput. Stud., 65 (8): 744–757, 2007.
17. S. Brostoff and AM Sasse. Ten strikes and you're out: Increasing the number of login attempts can improve password usability. In Proceedings of CHI 2003 Workshop on HCI and Security Systems, 2003.
18. J. Leyden. Office workers give away passwords for a cheap pen. The Register, April 18, 2003. Referenced 2006 at www.theregister.co.uk .
19. HP Ltd. Top 20 websites, 2008. URL: www.hitwise.com/datacenter/rankings.php .
20. S. Schechter, AJB Brush, and S. Egelman. It's no secret: Measuring the security and reliability of authentication via `secret 'questions. In IEEE Security and Privacy. IEEE,
2009.21. Rabkin. Personal knowledge questions for fallback authentication: security questions in the era of facebook. In SOUPS '08: Proceedings of the 4th Symposium on Usable Privacy and Security, pages 13-23, New York, NY, USA, 2008. ACM.
22. J. Podd, J. Bunnell, and R. Henderson. Cost-effective computer security: Cognitive and associative passwords. In OZCHI '96: Proceedings of the 6th Australian Conference on Computer-Human Interaction (OZCHI '96), page 304, Washington, DC, USA, 1996. IEEE Computer Society.
23. M. Zviran and WJ Haga. User authentication by cognitive passwords: an empirical assessment. In JCIT: Proceedings of the Fifth Jerusalem Conference on Information technology, pages 137–144, Los Alamitos, CA, USA, 1990. IEEE Computer Society Press.
24. Joseph Bonneau, University of Cambridge, Mike Just, Greg Matthews, What's in a Name? Evaluating Statistical Attacks on Personal Knowledge Questions. In Financial Cryptography and Data Security '10
25. T. Bridis. Hacker impersonated Palin, stole email password, Sept. 18, 2008. Associated Press.
26. GOST R 51241-98
27. S. Schechter, S. Egelman, and RW Reeder. It's not what you know, but who you know: A social approach to last-resort authentication. In CHI '09: Proceedings of the ACM SIGCHI Conference on Human Factors in Computing Systems, Boston, MA, 2009. ACM.
