Bug Bounty Kyivstar: reward for admin access to Jira, AWS, Apple, Google Developer, Bitbucket services - $ 50
The story of coincidence, luck and reward.
Two years ago, a dinikin user wrote a post about how he found a vulnerability in the personal account of Ukraine’s largest mobile operator, Kyivstar. The vulnerability allowed to add to your account without verification any Kyivstar phone number and fully manage it:
The vulnerability was closed, and the author, in gratitude, waspaid a huge premium by connecting 4,000 megabytes of Internet for 3 months.

Later, habraprzovatel rewiaca in his post " Why in Ukraine there are no white hackers or the history of hacking Kyivstar " described the situation with such a generous reward more emotionally.
Vitaly Sultan, Soultan , Chief Digital Officer of Kyivstar was noted in the comments then , promising to launch in the Bug Bounty company soon.
And now, after almost two years, Kyivstar announces the launch of its own Bug Bounty program. One of the first phrases in the announcement was as follows:
And in the evening I found in my Spam folder a letter from the Kyivstar domain with an HTML attachment.
And here begins the most interesting.
Despite the fact that the sender's name coincided with the name of the employee who answered my previous request on the Bugcrowd platform, the e-mail came to the wrong box that was used for registration.
After checking the attachment for viruses, opening it with a notepad and googling the sender, I still could not believe such a coincidence: these were bookmarks from the browser of the working computer of the Kyivstar employee.
Ukraine’s largest mobile operator was lucky that a letter with an attachment of the form “Bookmarks_July.2018.html” didn’t get anywhere (sorry for tautology), but to someone who understands the value of such data and the consequences of their loss.
There were 113 bookmarks in the file. And among the various links, both for work (which did not open from the external network), and not very much, there was one, which opened my eyes to five kopecks.
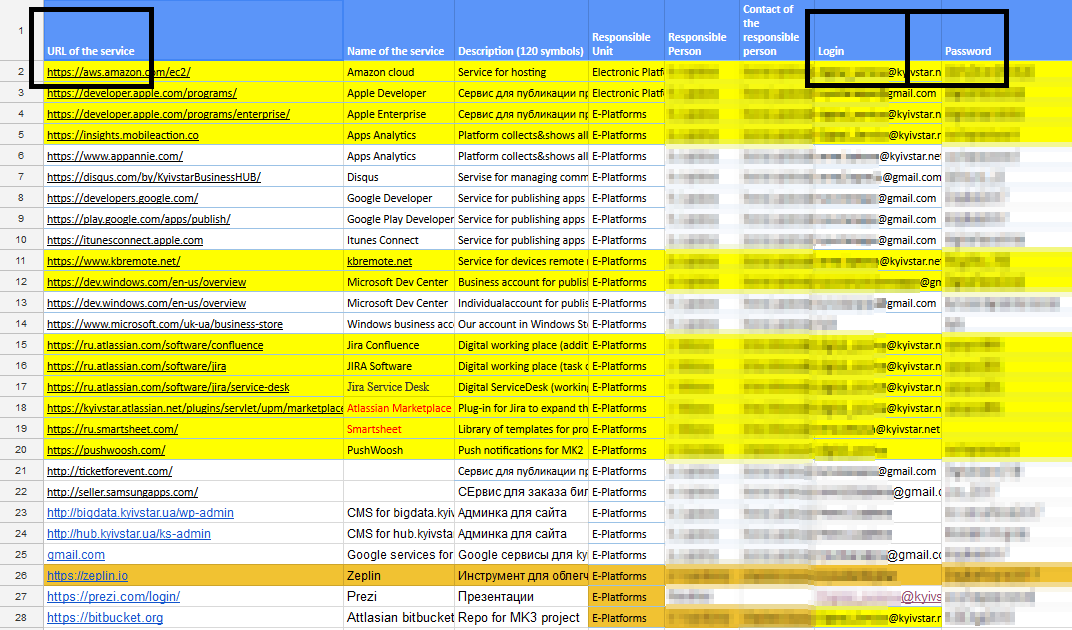
The link led to an unprotected file, in which, among other things, there were the following columns: “URL of the service”, “Login” and “Password”: (to enlarge the image, open it in a new tab) After another thought, is this not a fake? , whether honeypot , I tried to enter into several of the services, waiting for a barrier in the form of two-factor authentication. But she was not there, and I entered. Logged in as admin:

Understanding that administrator access is critical, the next day I quickly created and sent a request to Kievstar on the same Bugcrowd. Later I received a thank you, reputation points and $ 50 in response.
$ 50 for access to the accounts, the total cost of which is officially more than $ 5 800.
I wrote that the access to the services from the list as an administrator:
Amazon's the Web Services
Apple's Developer,
Mobile the Action
the App of Annie
Disqus
the Google Developers
the Windows the Dev Center
KBRemote
JIRA
Smartsheet
PushWoosh
TicketForEvent
the Samsung Developers
CMS for bigdata.kyivstar.ua and hub.kyivstar.ua
Gmail
Zeplin
Prezi
Bitbucket
is a critical issue; it is access to almost the entire structure of the company and the services it uses.
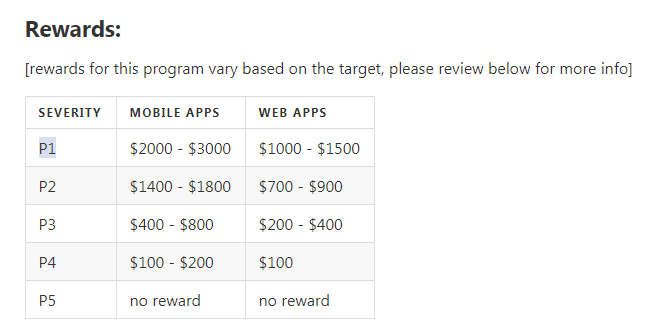
Relying on potential damage to business, reputation and customers, and simply looking at the Kyivstar rewards table, where my signal was given P1 priority (Sensitive Data Exposure: Critically Sensitive Data - Password Disclosure), I expected more:
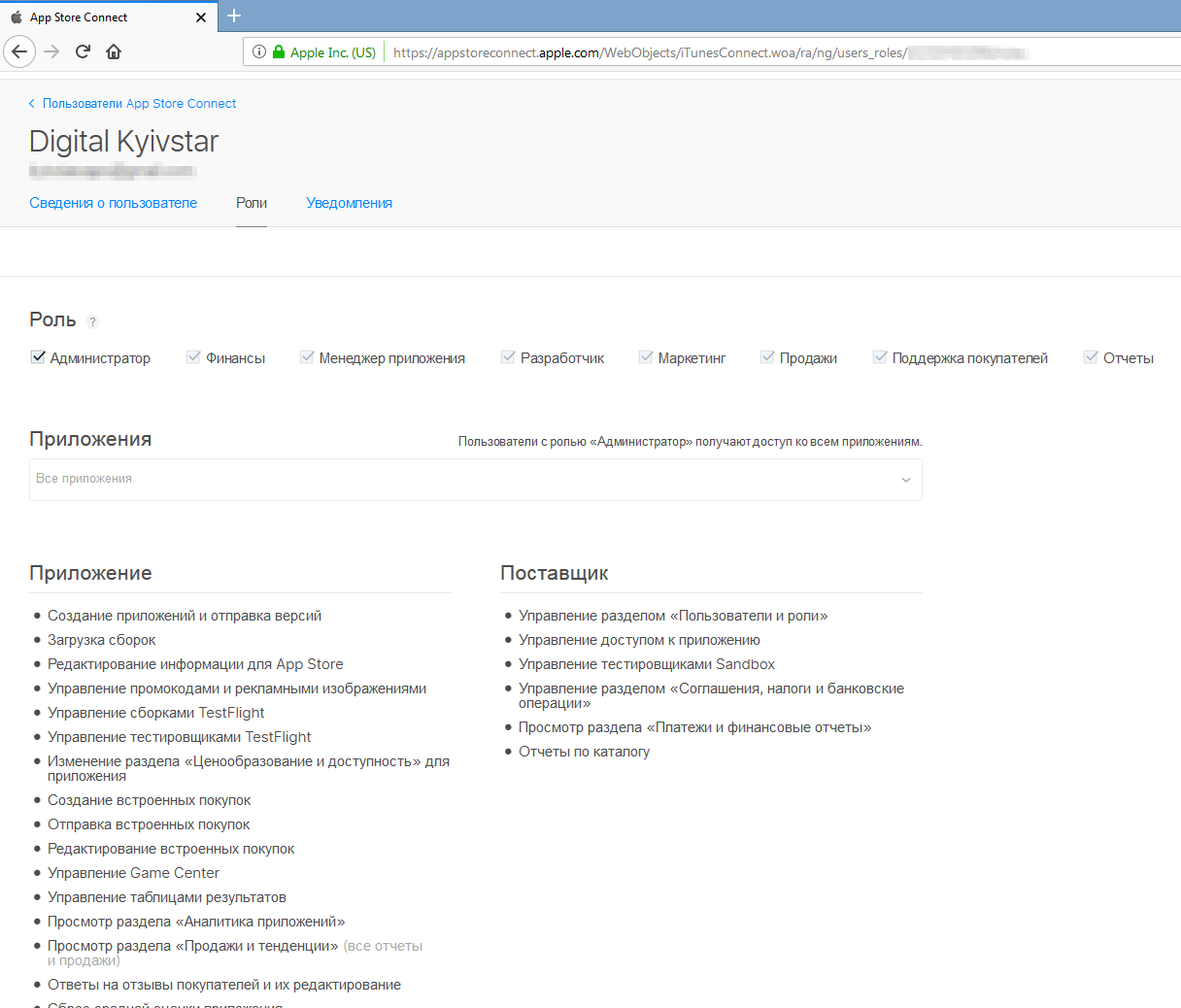
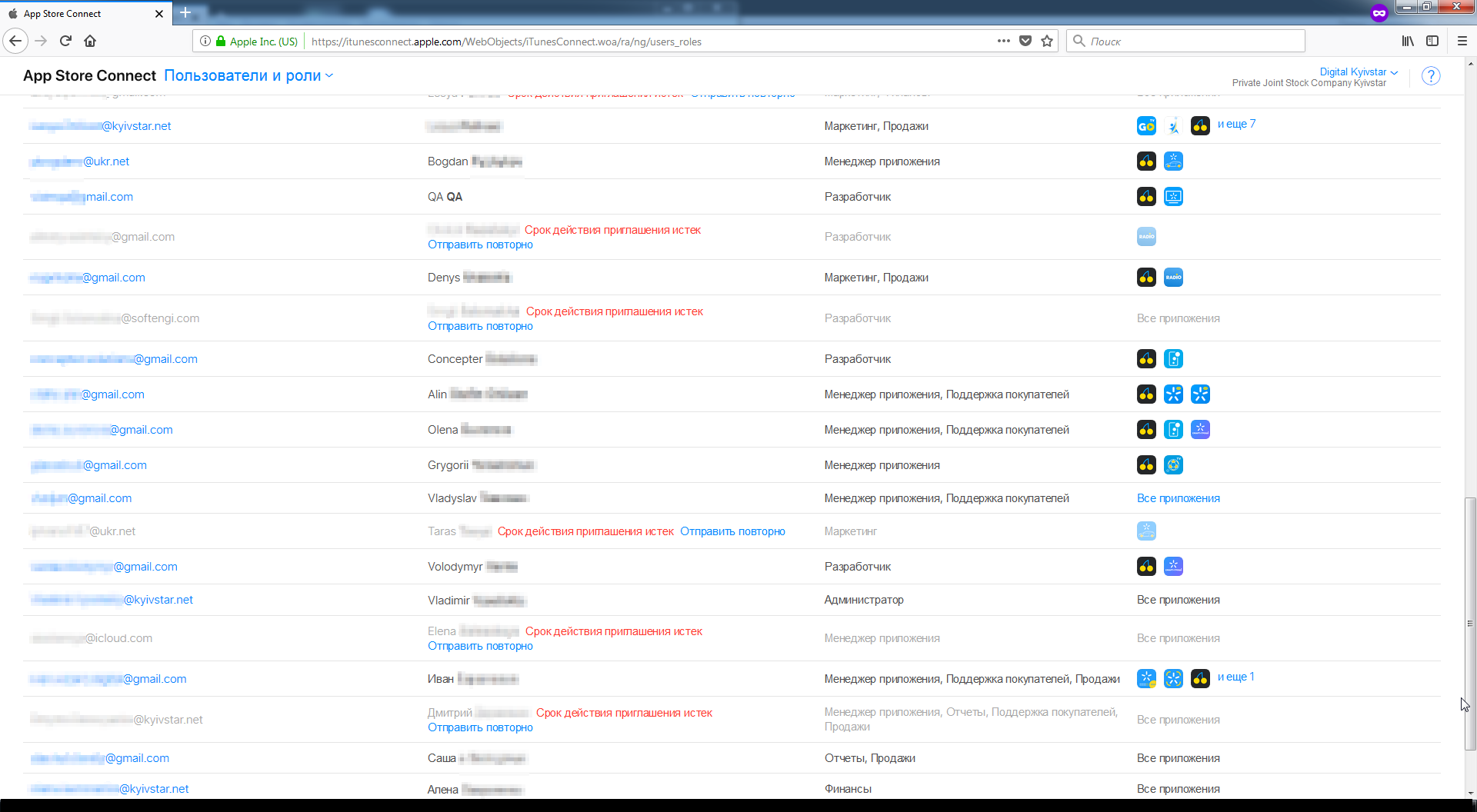
Loss of access to such services any A digital company is a significant blow to business and reputation. This is much worse than just some kind of vulnerability, this is full access. This is Klondike useful information for any criminal.
Using only one account, for example, in Apple Developer, an attacker can change the username and password and upload their application builds or simply add themselves to the administrators, leaving the backdoor.
However, Kyivstar was adamant: “Thank you, here is $ 50 for you, this finding is beyond the scope of the program”.
It is a pity that because of such corporate decisions, honest people will think about where to report this: official channels, like me, or better to find someone who offers more information for this information. Companies themselves are pushing people to bad thoughts and actions.
And it's not about the money, but about the company’s disrespect towards me. While in one of the banks I found opportunities to receive receipts from other customers and I was paid a little more than $ 300 for each opportunity found, there are also payment services that paid less than $ 20 for the same vulnerability - and nothing, I am not angry at the second 500 UAH also money. But here ...
Perhaps I was mistaken in that I expected a greater reward. Please select in the survey options below the correct in your opinion remuneration in this situation. You can voice your opinion right here in the comments.
PS: every rule has an exception.
UPD from 01/09/2019: posted answers to questions arising from reading this post + new Kyivstar problem - https://habr.com/post/435074/
Two years ago, a dinikin user wrote a post about how he found a vulnerability in the personal account of Ukraine’s largest mobile operator, Kyivstar. The vulnerability allowed to add to your account without verification any Kyivstar phone number and fully manage it:
- view the balance and call details;
- view the PUK-code and the serial number of the SIM-card, which allows you to replace the SIM-card;
- add new services and change the tariff plan;
- and most importantly - transfer money from phone to phone.
The vulnerability was closed, and the author, in gratitude, was

Later, habraprzovatel rewiaca in his post " Why in Ukraine there are no white hackers or the history of hacking Kyivstar " described the situation with such a generous reward more emotionally.
Vitaly Sultan, Soultan , Chief Digital Officer of Kyivstar was noted in the comments then , promising to launch in the Bug Bounty company soon.
And now, after almost two years, Kyivstar announces the launch of its own Bug Bounty program. One of the first phrases in the announcement was as follows:
Kyivstar noted that they decided to launch the program after they found a vulnerability during beta testing of the updated My Kyivstar system.As you can see, the company is cunning, because it is the user of Habrahabr.ru dinikin who found a vulnerability in the “My Kyivstar” system.
Some lyrics
Ещё до запуска Bug Bounty мной на сайте Киевстара была найдена возможность получать информацию о платёжеспособности клиентов компании по номеру телефона, а также о том, активен ли тот или иной номер.
И зная то, сколько тратит абонент, недобропорядочные люди могут использовать такие номера для обзвона, или просто собрать и продать базу номеров для рассылки.
Вот только программа выплаты вознаграждения за уязвимости была запущена всего на 2 недели, после чего перешла в режим приватной, и я не успел сообщить им о проблеме (а что бывает, если отправить сигнал по каналам связи, непредназначенным для подачи подобных заявок, описано в конце того же поста про Киевстар).
Общаясь с w9w по другим вопросам, выяснилось, что у него есть возможность отправить отчёт в приватную программу Киевстара. Было принято решение попробовать передать проблему через коллегу. Но пока я составлял описание и подбирал скриншоты, мобильный оператор снова открыл доступ к Bug Bounty всем желающим.
Поэтому я самостоятельно оформил обнаруженный мной кейс. Получив ответ, что это часть логики работы и риски были приняты на этапе их реализации, я не спорил.
И зная то, сколько тратит абонент, недобропорядочные люди могут использовать такие номера для обзвона, или просто собрать и продать базу номеров для рассылки.
Вот только программа выплаты вознаграждения за уязвимости была запущена всего на 2 недели, после чего перешла в режим приватной, и я не успел сообщить им о проблеме (а что бывает, если отправить сигнал по каналам связи, непредназначенным для подачи подобных заявок, описано в конце того же поста про Киевстар).
Общаясь с w9w по другим вопросам, выяснилось, что у него есть возможность отправить отчёт в приватную программу Киевстара. Было принято решение попробовать передать проблему через коллегу. Но пока я составлял описание и подбирал скриншоты, мобильный оператор снова открыл доступ к Bug Bounty всем желающим.
Поэтому я самостоятельно оформил обнаруженный мной кейс. Получив ответ, что это часть логики работы и риски были приняты на этапе их реализации, я не спорил.
And in the evening I found in my Spam folder a letter from the Kyivstar domain with an HTML attachment.
And here begins the most interesting.
Despite the fact that the sender's name coincided with the name of the employee who answered my previous request on the Bugcrowd platform, the e-mail came to the wrong box that was used for registration.
After checking the attachment for viruses, opening it with a notepad and googling the sender, I still could not believe such a coincidence: these were bookmarks from the browser of the working computer of the Kyivstar employee.
Ukraine’s largest mobile operator was lucky that a letter with an attachment of the form “Bookmarks_July.2018.html” didn’t get anywhere (sorry for tautology), but to someone who understands the value of such data and the consequences of their loss.
There were 113 bookmarks in the file. And among the various links, both for work (which did not open from the external network), and not very much, there was one, which opened my eyes to five kopecks.
The link led to an unprotected file, in which, among other things, there were the following columns: “URL of the service”, “Login” and “Password”: (to enlarge the image, open it in a new tab) After another thought, is this not a fake? , whether honeypot , I tried to enter into several of the services, waiting for a barrier in the form of two-factor authentication. But she was not there, and I entered. Logged in as admin:




Understanding that administrator access is critical, the next day I quickly created and sent a request to Kievstar on the same Bugcrowd. Later I received a thank you, reputation points and $ 50 in response.
$ 50 for access to the accounts, the total cost of which is officially more than $ 5 800.
I wrote that the access to the services from the list as an administrator:
Amazon's the Web Services
Apple's Developer,
Mobile the Action
the App of Annie
Disqus
the Google Developers
the Windows the Dev Center
KBRemote
JIRA
Smartsheet
PushWoosh
TicketForEvent
the Samsung Developers
CMS for bigdata.kyivstar.ua and hub.kyivstar.ua
Gmail
Zeplin
Prezi
Bitbucket
is a critical issue; it is access to almost the entire structure of the company and the services it uses.
Relying on potential damage to business, reputation and customers, and simply looking at the Kyivstar rewards table, where my signal was given P1 priority (Sensitive Data Exposure: Critically Sensitive Data - Password Disclosure), I expected more:

Loss of access to such services any A digital company is a significant blow to business and reputation. This is much worse than just some kind of vulnerability, this is full access. This is Klondike useful information for any criminal.
Using only one account, for example, in Apple Developer, an attacker can change the username and password and upload their application builds or simply add themselves to the administrators, leaving the backdoor.
However, Kyivstar was adamant: “Thank you, here is $ 50 for you, this finding is beyond the scope of the program”.
It is a pity that because of such corporate decisions, honest people will think about where to report this: official channels, like me, or better to find someone who offers more information for this information. Companies themselves are pushing people to bad thoughts and actions.
And it's not about the money, but about the company’s disrespect towards me. While in one of the banks I found opportunities to receive receipts from other customers and I was paid a little more than $ 300 for each opportunity found, there are also payment services that paid less than $ 20 for the same vulnerability - and nothing, I am not angry at the second 500 UAH also money. But here ...
Perhaps I was mistaken in that I expected a greater reward. Please select in the survey options below the correct in your opinion remuneration in this situation. You can voice your opinion right here in the comments.
PS: every rule has an exception.
UPD from 01/09/2019: posted answers to questions arising from reading this post + new Kyivstar problem - https://habr.com/post/435074/
Only registered users can participate in the survey. Sign in , please.
What amount should the company pay in this case:
- 4.6% 0 dollars 42
- 2.8% 50 dollars 26
- 9.7% up to 1000 dollars inclusive 88
- 31.2% $ 1000 - $ 3000 283
- 50.4% $ 3,000 and up 457
- 0.9% of your version (I will write in the comments). 9
