Create Your Sniffer / FireWall / Parental control / SpyWare / Client for Computer Club. LSP Technology
Create Your Sniffer / FireWall / Parental control / SpyWare / Client for Computer Club. LSP Technology

Provider).
Recently, one acquaintance revealed a desire that for the Electronic Room (library) he needs a program that will control access to computers and automatically consider who and why.
Since there was no money in the budget for 2012, a friend stopped. But the idea of access control has already ignited. I began to think how to do it.
Most of all, one question bothered me. How to block HTTP traffic if the user pays only for renting a computer, and not for renting a computer with the Internet?
On the Internet, I found an interesting article about LSP and now I present its translation with some changes.
To whom it is interesting I ask under kat.
LSP-based HTTP sniffer (Layered Service Provider)
This article describes how to create a simple sniffer to monitor HTTP traffic on Windows. This program is based on open technology provided by Microsoft, its name is LSP (Layered Service Provider). This technology is used by various software. These are mainly Antiviruses, Firewalls and traffic filtering programs.
In order to create this software package I used an example from the Microsoft Platform SDK (Program Files \ Microsoft Platform SDK \ Samples \ NetDS \ WinSock \ LSP \) and added an additional ability to filter HTTP traffic and collect the results in a separate storage.
Concept
Basic Outline
We start
Findings and Tips
Useful Links.
Concept.
The main idea of LSP is to create a provider that will be included in the chain of existing providers. Something reminds the principle of hooks in Windows.
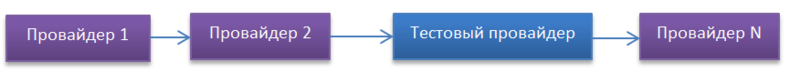
During the installation of the provider, you can specify a place in the chain of providers. And the chain will be rebuilt according to the new settings. In our case, the provider is installed on top of the [TCP / IP] provider. Be careful when installing on a real machine. If the installation fails, this will add a lot of problems - loss of network, Internet and the failure of some network applications.
In order to get around the debugging problems and creating the LSP provider, test it on the Virtual Machine.
In the LSP provider, you must replace all the winsock library methods. Actually, in the Platform SDK example, the replacement logic is already included, it remains only to add the logic of interception, blocking the URL or saving HTTP traffic.
LSPs use both legal programs and SpyWare / AdWare.
For example:
Legal programs:
- Sygate firewall
- Mcafee Personal Firewall
- E-safe
- Dr.Web Security Space 6 uses LSP as a Parental Control module.
Adware:
- Webhancer
- New.net
- Newdotnet

LSP in action.
Basic Scheme
This is the basic scheme of a software package.
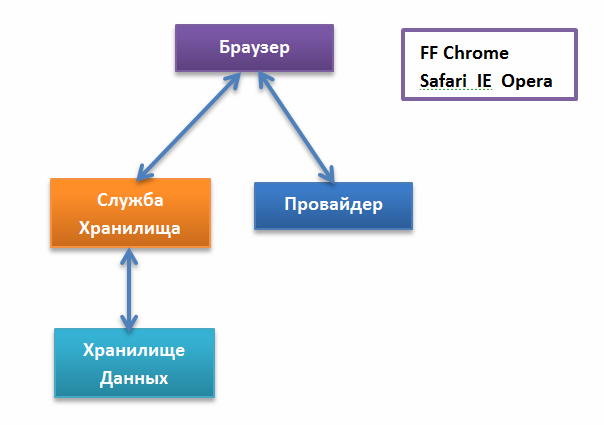
After installing the software package, many programs will use our provider (in general, our provider is a simple DLL file that is loaded into every application that uses the Winsock library). But we only need to determine HTTP traffic. Below is a line of code (our provider) with a hard-bound port that will be monitored (HTTP protocol uses port 80 by default).
if((namelen >= sizeof(sockaddr_in)) && (((sockaddr_in*)name)->sin_port == htons(HTTPPort)))
{
SocketContext->intercept = TRUE;
}
You can improve this tool, and make the program logic more elegant to save your settings, rather than hard-defined constants as in the example.
In addition, we must define HTTP requests. HTTP GET requests are determined by a simple comparison with the string “GET”. Defining POST requests can be done in the same way.
We also have a Service that collects all the information that is filtered - the service was created in order to prevent data corruption, it can happen if we monitor several applications, and not one. All intercepted information from the browser will be transmitted to this service. This service is a Socket server (listens on port 4004) so there should not be any problems with synchronizing data collection. In this case, the Data Warehouse is just a text file, but you can easily replace it with a more convenient and stable option (for example, use a DBMS).
We begin
The test package contains the following projects.
1. LSP
project (LSP folder) This project contains an overload of the basic Winsock methods. It is in this place that we must add our changes. In my case, this project contains an example from the Platform SDK, where I added the logic to determine the connection to the 80th port and marked it as being intercepted in the Connect method:
if((namelen >= sizeof(sockaddr_in)) && (((sockaddr_in*)name)->sin_port == htons(HTTPPort)))
{
SocketContext->intercept = TRUE;
}
Thus, in future calls to the Send method, we find that this socket is used by the HTTP protocol. We also established a connection to the Traffic Collection Service in the Connect method. In the SEND method, we implemented the logic of detecting HTTP requests and redirecting them to our Service:
if (IsHTTPRequest(lpBuffers->buf) && SocketContext->intercept)
{
SetBlockingProvider(SocketContext->Provider);
ret = SocketContext->Provider->NextProcTable.lpWSPSend(
serviceConnection.GetSocket(),
lpBuffers,
dwBufferCount,
lpNumberOfBytesSent,
dwFlags,
lpOverlapped,
lpCompletionRoutine,
lpThreadId,
lpErrno
);
SetBlockingProvider(NULL);
}
I created a specialized class that holds one persistent connection for each loaded DLL file.
class ServiceConnectionKeeper;
Its role is to keep Socket connected. Thus, only one connection is established with the storage service.
2. Common project (Common folder) - this project contains all the utilities provided in the Platform SDK examples. And some GUID manipulations from our LSP provider were also done.
The Installer project (Installer folder) is the LSP installer. We changed its main method - removed command line parsing and added a search for TCP provider. Now during installation we look for the TCP provider ID and rebuild the provider chain. We placed our provider on top of TCP.
if (IsHTTPRequest(lpBuffers->buf) && SocketContext->intercept)
{
SetBlockingProvider(SocketContext->Provider);
ret = SocketContext->Provider->NextProcTable.lpWSPSend(
serviceConnection.GetSocket(),
lpBuffers,
dwBufferCount,
lpNumberOfBytesSent,
dwFlags,
lpOverlapped,
lpCompletionRoutine,
lpThreadId,
lpErrno
);
SetBlockingProvider(NULL);
}
3. The Service project (the Service folder) is a traffic collector. It is a simple Windows service and methods for installing and uninstalling a service. The MAIN function of our service also implements a Socket server. All the logic of manipulating the service is kindly borrowed from MSDN. The server accepts all incoming connections and launches a separate thread for each application. The launched thread receives data sequentially separated by "\ r \ n \ r \ n" (essentially 2 empty lines) and saves them in the storage.
do
{
result = recv(clientSocket, buffer, PACKSIZE, 0);
if (result > 0)
{
response += std::string(buffer, result);
do
{
position = response.find(messageTerminator);
if (std::string::npos != position)
{
if (!CollectorServer::Instance()->SaveData(std::string(response.begin(), response.begin() + position)))
{
return -1;
}
response = response.substr(position + messageTerminator.size());
}
} while (std::string::npos != position);
}
else
{
break;
}
} while (SOCKET_ERROR != result);
In order to start working with this project you need to assemble the entire Visual studio project. After that, put the NSI script in the build result folder and compile the Nsi script. We get the installation setup.exe file.
During the installation of setup.exe, all the necessary files will be unpacked into their working folders. LSP.DLL will be placed in% SYSTEMROOT% \\ system32 \\ LSP.dll. The service and provider installer will be placed in the Program Files folder. Also, the uninstall shortcut will be placed on the desktop. The history file will be located in the root of C: //.
Conclusions and advice.
This article describes how to create your own provider and monitor all network traffic. But this is not the only example for using this technology. You can also easily implement logic for:
Blocking HTTP requests and responses;
Change and delete traffic;
Block connections (as Firewall does);
Intercept SLL encrypted data (it is even possible to intercept MITM) (Man in the midle)
There were many rakes in the LSP development, so as not to regret that the Internet connection was lost and there was a failure, it is better to use the Virtual Machine for tests. It is much more convenient to roll back the VM image to its previous state than to use the Windows recovery system each time.
Most anti-virus software also uses this technology, so you can find them in the chain of installed LSP providers in your OS. Also, antiviruses can become a problem for you when testing your LSP provider, because antiviruses also filter traffic.
You can add logic to ignore the applications you have selected. So that Our LSP provider does nothing except transfer data if the application is in the list of ignored.
This tool was developed only for 32-bit applications. But it can be easily ported to 64-bit applications. You just have to rebuild the project into 64-bit and set the LspCatalog64Only flag during the installation of the provider.
To see the changes in the Platform SDK example that were made to create this tool, you can compare the text with the original example.
I also noted all the code blocks that were added by the // ADDED comment.
Also note that you must generate a new GUID for your LSP provider in order to avoid conflicts with other LSP providers.
useful links
Unfortunately there are not many links, but they are still there.
0. Original article in English
1. MSDN and Platform SDK documentation.
2. There is also information on the LSP developers website .
The project itself has been laid out HERE.
Also the project has been laid out at GITHAB
