Introduction to Dynamic Access Control in Windows Server 2012: Innovations in File Server Auditing

We continue to translate and publish material related to Windows Server 2012 and updates to Microsoft’s native auditing systems. We invite interested readers to familiarize themselves with the story of a Windows Server team employee about the new Dynamic Access Control features.
Hello, my name is Nir Ben-Zvi, I work in the Windows Server team. I am pleased to present today a new set of functions for Dynamic Access Control, which is available in Windows Server 2012.
First, I will briefly talk about the planning process, then we will look at the new Central Access Policy model and describe what's new in File Server, the solution that we built in Windows Server 2012. I also have a gradual implementation issue, so that you don’t need to had to move the entire environment to Windows Server 2012, if you need to use this feature. In the end, we will consider issues related to what decisions of our partners will help expand the proposed functionality of our solutions.
Introduction
In modern (read: complex) IT infrastructures, data creation occurs at a staggering rate in dispersed systems; at the same time access to this data is carried out from numerous devices. Compliance with information security standards and the need to protect confidential information from leaks are some of the most important problems for business and IT. In order for these problems to be successfully resolved, it is necessary to control who gained access to certain information, and it is desirable that it is desirable that during the implementation of such control access information be presented as clearly as possible.
We were aware of these problems facing business and IT a couple of years ago when we planned what Windows Server 2012 would be like. Here are just a few common requests from our clients:
• Centralized access control to information based on business requests, as well and in order to comply with regulatory requirements
• Access to information should be audited for the purpose of analysis and compliance with information security requirements
• Confidential information should be protected
• Content owners should be responsible for information - administrators should not engage in non-work
• A key aspect is maintaining the productivity of information professionals
We took a look at the individual positions in the organization and their interaction in the process of fulfilling requests from the business and regulatory bodies in order to present a set of technologies and solutions adequate to the requirements.
Thus, the list of posts involved in resolving the identified problems begins with CSO / CIO, which defines needs from a business perspective and fulfills regulatory requirements. They are followed by IT administrators who manage the systems, and content owners who monitor the actual information. As for those who directly work with information, the influence of the applied decisions on them should be minimal (ideally, it should not be at all).
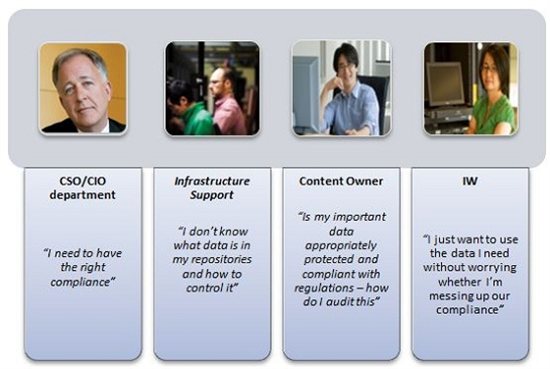
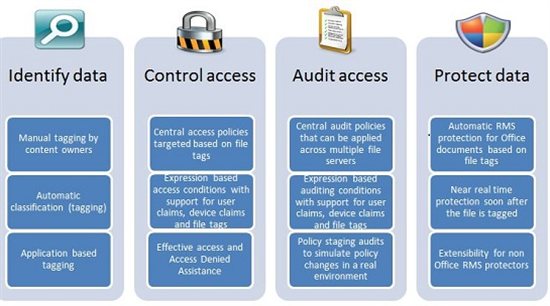
To help organizations meet regulatory requirements and solve their business tasks, we ultimately focused on the following areas:
• Defining information that should be managed to achieve goals
• Applying information access policies
• Auditing access to information
• Encryption Information
These tasks have been translated into a set of Windows functions that make it possible to protect data using Windows solutions and partner solutions.
• Added the ability to configure Central Access and audit policies in Active Directory. These policies are based on conditional requirements (see below); however, the number of security groups for access control can be significantly reduced:
o Who is the user
o What device is he using
o What data is accessed
• Claims are integrated into Windows authentication (Kerberos) so that users and devices can be described not only through the security groups that they are members of, but also on applications, for example: “User from the Finance Department”, and “User access category (security clearance) is high”.
• Improved File Classification Infrastructure, which allows content owners and users to identify (tag) their data so that IT administrators can create targeted policies based on these tags. This feature works along with the ability of the file classification infrastructure to automatically classify files based on their contents or other characteristics.
• Rights Management Services are integrated to automatically protect (encrypt) confidential information on servers, so that even when it leaves the server, it is protected.
Central Access Policies
Central access policies can be compared to the insurance that the organization uses on its servers. These policies improve (but do not replace) the local access policy (for example, discretionary ACLs) that apply to information. For example, if the local DACL of a file allows access to a specific user, but the Central Policy prohibits access to the same user, then he will not be able to access the file (and vice versa).
The initiative to implement and strengthen central access policies grows from various causes and from different levels of organization:
• Policy related to compliance with regulatory requirements: This policy is consistent with regulatory and business requirements and aims to protect the correct (adequately established) access to the information that is being managed. For example, to give access to information that falls under the regulatory documents of “US-EU Safe Harbor” only to a specific group of users.
• Permission policy at the department level: Each department in the organization has certain requirements for working with data that they would like to protect (strengthen). This situation is often found in organizations with an extensive organizational structure. For example, the finance department wants to restrict access to financial information only to financial employees.
• Need to know policy: This policy ensures that access is allowed only to those who need to know. For example:
o Vendors should access information and edit only files that are related to the projects they are working on.
o In financial institutions, the “walls” between information are important, for example, analysts should not have access to brokerage information, and brokers should not have access to analytical information.
Central Audit Policies
The Central Audit Policy is a powerful tool that allows you to maintain the security of your organization. One of the key objectives of a security audit is to comply with information security regulations. Industry standards such as SOX, HIPPA, PCI, and others require organizations to follow a well-established set of rules related to information security and data privacy. The work of auditors is to establish the presence (or absence) of such policies, thereby proving compliance (or non-compliance) with the requirements of these standards. In addition, security audits allow you to record abnormal behavior,
Windows Server 2012 allows administrators to design audit policies using expressions that take into account what information users access and who these users are, so that an organization can audit access to only certain information, regardless of where they are was not. This paves the way for more targeted and at the same time easy to use audit policies. Now you can implement scenarios that until now were difficult to implement. For example, you can easily develop audit policies that are listed below:
• Audit for everyone who does not have a high tolerance category and who, nevertheless, is trying to access “important” information
• An audit of all vendors who are trying to access project documents that they are not working on.
This helps to regulate the scope of audit events and limits them only to more important ones, so that you can track access to information on various servers without creating a huge number of records.
In addition, information tagging is recorded in audit events, so that using the event collection mechanism, contextual reports can be generated, for example: Who has gained access to Important information over the past three months.
File Server Solution
Based on this infrastructure, we have developed a comprehensive solution for Windows Server 2012 Active Directory, Windows Server 2012 File Server and Windows 8 client. This solution allows you to:
• Identify data using automatic and manual file classification.
• Control access to files across all servers by applying the safety net policy for central access policies. For example, you can control who receives network health information throughout the organization.
• Audit access to files on file servers; they use central audit policies to comply with information security standards and conduct investigations. For example, you can determine who has gained access to highly confidential information in the last three months.
• Data encryption through automatic encryption of Rights Management Services (RMS) for confidential documents. For example, you can configure RMS to encrypt all documents that contain information protected by HIPAA.
In order to support the implementation of multiple file servers in the organization, we also provide the Data Classification Toolkit, which allows you to configure and generate reports among multiple servers.
The beta version of the Data Classification Toolkit can be downloaded here.
Gradual implementation concept
One of the key principles for developing DAC is gradual implementation. You can start using this function as soon as you have a need to solve the tasks facing your company regarding audit of file servers and access to information.
You can use most of the Dynamic Access Control features in the Windows Server 2012 file server and the updated Active Directory domain schema. Adding a minimum number of Windows Server 2012 domain controllers allows you to enable custom requests, etc. Each part of the system that you upgrade will give you more options, however, to set the speed of implementation is up to you.
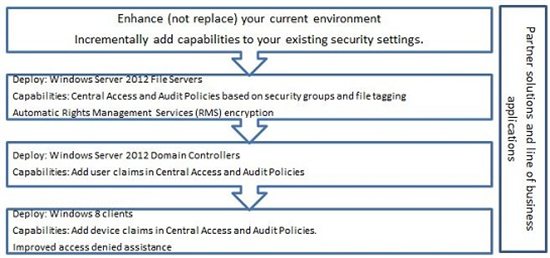
Partner solutions
Partner solutions and a range of business applications can increase your investment in Windows infrastructure for Dynamic Access Control, providing value for organizations using Active Directory. Here are just a few examples of partnership solutions presented at the conference last year:
• Integration of Data Leakage Prevention systems with automatic content classification system
• Centralized analysis of audit data
• Authorization of Rights Management Services using Central Access Policies
• Many More ...
via Technet
