Operating system vulnerabilities. Part III

Half way passed. We already know what holes are in the Android OS or macOS. Today we will talk about operating systems that are not as common as the same Android, but deserve no less attention. If you want to familiarize yourself with OS vulnerabilities from the previous parts - here are the references: Part I and Part II .
But for starters, I would like to remind you why these are the OS we are examining today, how vulnerabilities are selected and what data about them is contained in the tables, of which you will see quite a bit lower in the text.
In this part we will study the third five operating systems from the table below (in bold):
| OS name | Manufacturer | Total number of vulnerabilities for 2017 | Total number of vulnerabilities for 2016 | The total number of vulnerabilities for all time statistics |
|---|---|---|---|---|
| Android | 666 | 523 | 1357 | |
| Linux Kernel | Linux | 381 | 217 | 1921 |
| Iphone os | Apple | 293 | 161 | 1277 |
| Windows 10 | Microsoft | 226 | 172 | 451 |
| Windows Server 2016 | Microsoft | 212 | 39 | 251 |
| Windows Server 2008 | Microsoft | 212 | 133 | 981 |
| Mac os x | Apple | 210 | 215 | 1888 |
| Windows Server 2012 | Microsoft | 201 | 156 | 606 |
| Windows 7 | Microsoft | 197 | 134 | 838 |
| Windows 8.1 | Microsoft | 192 | 154 | 542 |
| Windows RT 8.1 | Microsoft | 124 | 139 | 438 |
| Debian linux | Debian | 95 | 327 | 1029 |
| Fedora | Fedora project | 84 | 120 | 441 |
| Ubuntu linux | Canonical | 66 | 279 | 867 |
| Watchos | Apple | 65 | 77 | 231 |
| Windows vista | Microsoft | 64 | 125 | 814 |
| Opensuse | Opensuse project | 58 | five | 119 |
| Leap | Opensuse project | 57 | 2 | 60 |
| Leap | Novell | 48 | 260 | 349 |
| XEN | XEN | 44 | 28 | 228 |
Regarding the choice of vulnerabilities for more detailed consideration (since it was already written in the previous part, we will hide everything under the spoiler so as not to lengthen the text):
Стоит рассмотреть более внимательно некоторые из уязвимостей, замеченные на той или иной ОС. Портал CVE Details выставляет баллы каждой из них. Число баллов зависит от уровня ущерба и массовости распространения. Максимальный показатель — 10 баллов. Именно о таких уязвимостях (если они есть и если они уникальны) и будет идти речь далее. Дабы эта статья не превратилась в пятитомник Ленина, будем уделять внимание только трем уязвимость из списка, который может содержать сотни.
Regarding the data structure in the tables (since it was already written in the previous part, we will hide everything under the spoiler so as not to lengthen the text):
Описание таблиц
В таблицах каждого из типов уязвимостей указываются определенные дополнительные параметры, касающиеся той или иной уязвимости. Подробнее о них.
Уровень воздействия на
1) конфиденциальность:
2) целостность:
3) доступность:
Сложность доступа
Аутентификация
В таблицах каждого из типов уязвимостей указываются определенные дополнительные параметры, касающиеся той или иной уязвимости. Подробнее о них.
Уровень воздействия на
1) конфиденциальность:
- Полный — уязвимость открывает злоумышленникам доступ ко всей информации на устройстве;
- Частичный — значительное раскрытие информации;
- Отсутствует — конфиденциальность не нарушается;
2) целостность:
- Полный — целостность системы полностью скомпрометирована, полная потеря защиты системы;
- Частичный — модификация некоторых системных файлов или информации возможна, но злоумышленник не имеет контроля над тем, что может быть изменено;
- Отсутствует — воздействия на целостность системы нет;
3) доступность:
- Полный — уязвимость позволяет злоумышленнику полностью закрыть доступ к ресурсу;
- Частичный — снижение производительности или непостоянная доступность ресурсов;
- Отсутствует — воздействия на доступность системы нет;
Сложность доступа
- Низкая — особых условий для получения доступа не требуется, как и не требуется специфический знаний или навыков;
- Средняя — необходимо удовлетворение некоторых условий для получения доступа;
- Высокая — специальные условия получения доступа, ограничивающие эксплойт;
Аутентификация
- Не требуется — аутентификация не требуется для эксплойта уязвимости;
- Single system — уязвимость требует, чтобы взломщик был залогинен в систему (например, через командную строку, режим рабочего стола или через веб-интерфейс).
1. Windows Rt 8.1

Windows Rt 8.1 is the operating system of the Windows NT family, released October 26, 2012.
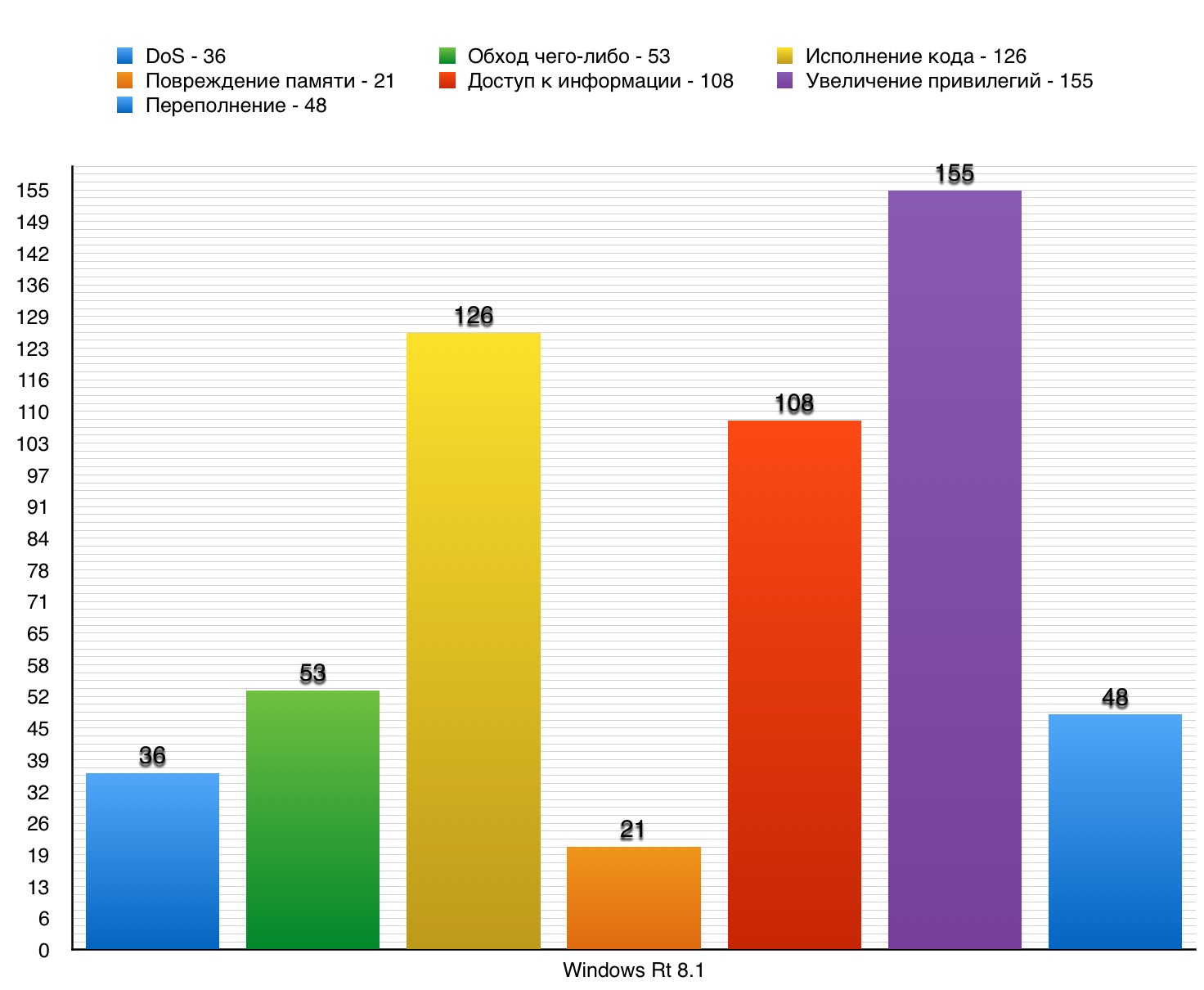
DoS
Total vulnerabilities - 36. 10 points scored - 0.
Vulnerability №1 (9.3)
usp10.dll in Uniscribe allowed adding an entry to the EMF + font file, which opened the possibility to execute the code or lead to DoS.
Vulnerability # 2 (9.3)
MSXML 3.0 allowed creating a DoS through the created XML content.
Vulnerability # 3 (9.3)
atmfd.dll in the Adobe Type Manager library allowed a remote attacker to arrange DoS through the font he created by OpenType.

The DoS vulnerability table in Windows Rt 8.1.
Bypassing anything
53 vulnerabilities in all. 0 scored 10 points.
Vulnerability # 1 (9.3)
The OS allowed attackers to bypass the application sandbox security protocols and perform actions in the registry through the application created.
Vulnerability # 2 (9.3)
OS allowed attackers to bypass the application sandbox security protocols and perform actions on the file system through the application created.
Vulnerability # 3 (7.6)
OS could not correctly restrict keyboard and mouse data exchange between programs at different integrity levels, which allowed an attacker to bypass access restrictions by gaining control over a low-level process for launching an on-screen keyboard, and then download the created application.
Table of vulnerabilities of the category “Bypassing something” in Windows OS Rt 8.1
Execution of code
126 vulnerabilities in total. 10 points - 5.
Vulnerability # 1
OS allowed the hacker to gain control over the system when Windows Search could not cope with the processing of memory objects.
Vulnerability # 2
OS allowed the hacker to gain control over the system when Windows Search could not cope with the processing of memory objects.
Vulnerability # 3
OS allowed to remotely execute arbitrary code, because it could not process DNS responses.
Code Execution Vulnerability Table in Windows Rt 8.1
Memory corruption
A total of 21 vulnerabilities. 10 points - 0.
Vulnerability # 1 (9.3)
The Imaging component allowed a remote attacker to execute code through the created document.
Vulnerability # 2 (9.3)
Animation Manager allowed a remote hacker to execute code through the created website.
Vulnerability # 3 (9.3)
Media Foundation allowed a remote hacker to execute code through the created website.

Table of vulnerabilities of the category "memory corruption" in the OS Windows Rt 8.1
Access to information
Total found 108 vulnerabilities. 10 points - 0.
Vulnerability # 1 (7.2)
Drivers in kernel mode could give an authenticated attacker the opportunity to execute the application created by him for information or even DoS.
Vulnerability # 2 (6.6)
win32k.sys in the kernel mode drivers made it possible for local users to acquire information from the kernel memory through the application created.
Vulnerability # 3 (5.8)
SChannel could not guarantee that the certificate of the X.509 server during the renewal was the same as before the renewal, which made it possible to obtain information or modify the TLS data through a “triple handshake attack”.

Vulnerability table of the “Access to information” category in Windows Rt 8.1
Increase of privileges
Total - 155. 10 points scored 2.
Vulnerability # 1 (10)
The OS kernel mode drivers allowed a local user to get privileges through the created application.
Vulnerability # 2 (10)
The Graphics component in the OS kernel allowed local users to get privileges through the application created.
Vulnerability # 3 (9.3)
Traversing the directory in the TSWbPrxy component of the OS made it possible to obtain privileges through the path created in the executable file.

Vulnerability table of the “Privilege escalation” category in Windows Rt 8.1 Total
overflow
- 48. 10 points - 0.
Vulnerability # 1 (9.3)
The Uniscribe component when an unsuccessful attempt to correctly process memory objects led to the possibility of code execution.
Vulnerability # 2 (9.3) The
JET Database Engine gave control over the system, since it processed memory objects.
Vulnerability # 3 (9.3) The
JET Database Engine gave control over the system, since it was processing memory objects.

Table of vulnerabilities category "Overflow" in OS Windows Rt 8.1
As in the previous version of Windows - the 8th, there is the same trend. A greater number of vulnerabilities relate to increasing privileges, which leads to the possibility of activating remotely malicious software, which, in turn, can exploit other vulnerabilities and lead to various kinds of consequences.
2. Debian Linux

Debian Linux is an operating system first released on August 16, 1993. One of the most popular incarnations of Linux, Debian is suitable for use on both workstations and servers.
Funny fact: all working versions of the OS are named after the characters of the animated film “Toy Story”. But the unstable version is called Sid (that was the name of the boy in the same cartoon that mocked the toys).
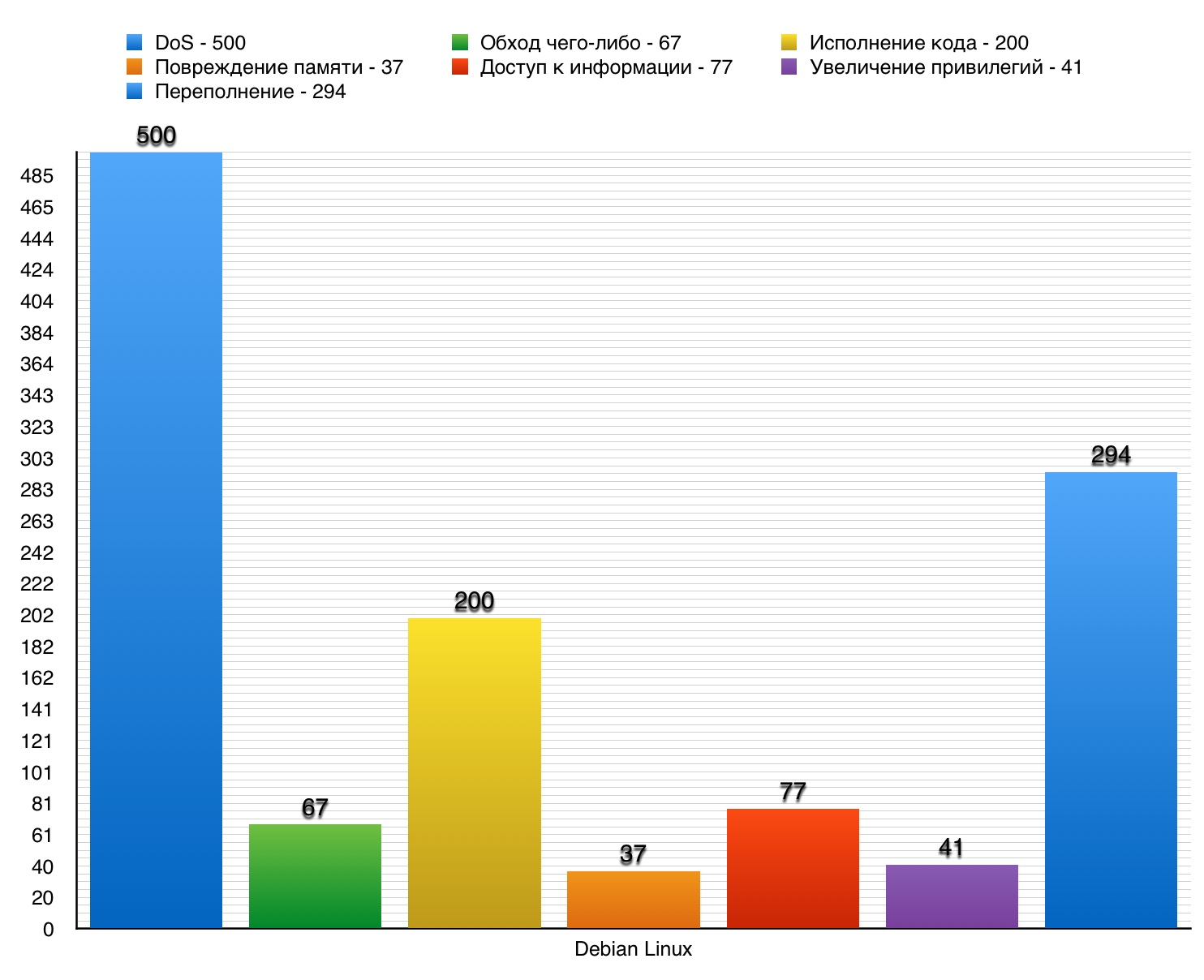
DoS
Total - 500 vulnerabilities. However, among such a large number, only 16 scored 10 points.
Vulnerability # 1
The xmlNextChar function in libxml2 allowed using a generated XML document to organize DoS by a remote hacker.
Vulnerability # 2
A buffer overflow in the heap of the encode_msg function in encode_msg.c in the SEAS Kamailio module allowed a remote attacker to arrange a DoS or execute code through a large SIP packet.
Vulnerability # 3
A number of unidentified vulnerabilities in Mozilla Firefox browser up to version 46.0 and Firefox ESR 45.x up to version 45.1 allowed a remote attacker to organize DoS through an unidentified vector.
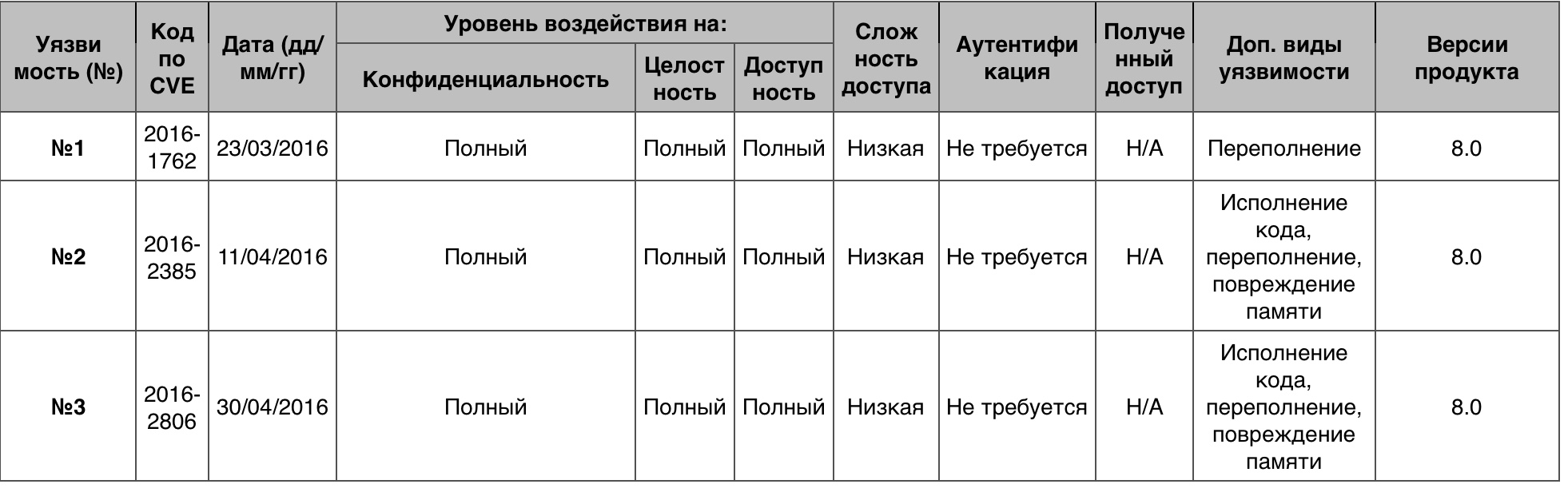
The DoS vulnerability table in Debian Linux OS.
Bypassing anything.
Of the 67 vulnerabilities, only 4 scored 10 points.
Vulnerability # 1
Gallery version 1.4.3 and later allowed to bypass authentication and get Gallery administrator rights.
Vulnerability # 2
Google Chrome, older than 48.0.2564.116, allowed you to bypass the rule of restriction of the Blink domain and bypass the sandbox security protocols through an unspecified vector.
Vulnerability # 3
The pam_sm_authenticate function in pam_sshauth.c in libpam-sshauth allowed context-dependent hackers to bypass authentication or obtain privileges through the user's system account.
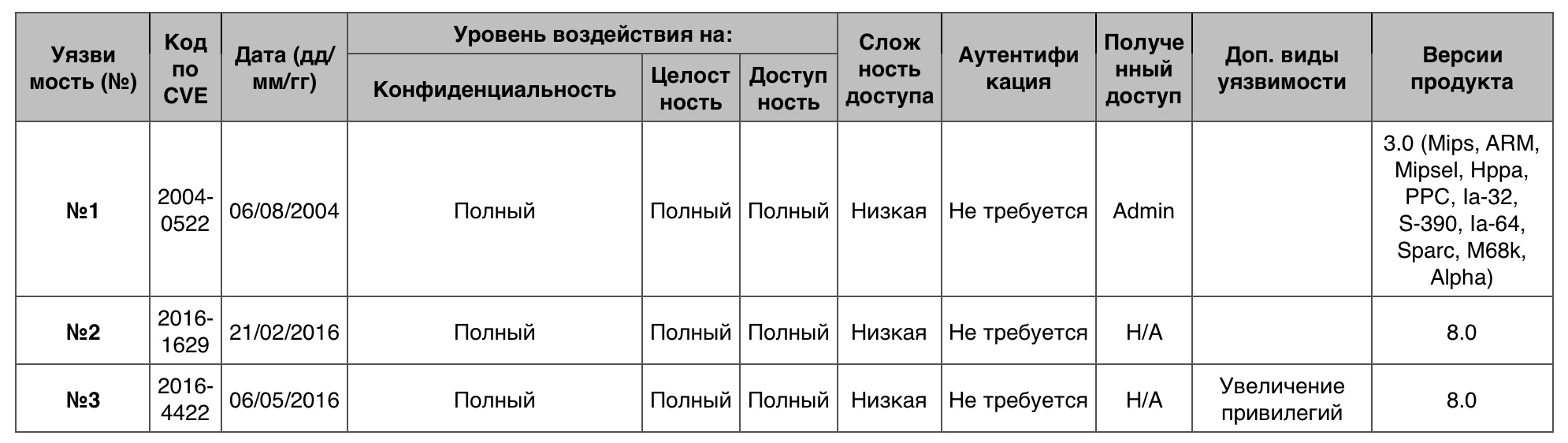
Table vulnerable categories in Debian Linux OS "Bypass something"
executing code
Total - 200 10 points - 25.
Vulnerability №1
Many unidentified vulnerabilities in Mozilla Firefox to version 46.0 and Firefox ESR 45.x to version 45.1 allows remote attackers to organize DoS via unspecified vector.
Vulnerability # 2
The OpenBlob function in blob.c in GraphicsMagick up to version 1.3.24 and ImageMagick allowed an attacker to execute arbitrary code by using the “|” symbol at the beginning of the file name.
Vulnerability # 3
The use-after-free vulnerability in the __sys_recvmmsg function in net / socket.c in the Linux kernel version 4.5.2 allowed a remote attacker to execute arbitrary code through vectors due to the use of an improper system call recvmmsg during error handling.

Code Execution Vulnerability Table in Debian Linux OS
Memory damage
Total - 37 vulnerabilities. Of these, 10 points scored 4.
Vulnerability number 1
A number of unknown vulnerabilities in Mozilla Firefox browser up to version 46.0 and Firefox ESR 45.x up to version 45.1 allowed a remote attacker to organize DoS via an undefined vector.
Vulnerability # 2
Buffer overflow in the heap of the encode_msg function in encode_msg.c in the SEAS Kamailio module allowed the remote attacker to arrange DoS or execute code through a large SIP packet.
Vulnerability # 3
A number of unidentified vulnerabilities in Mozilla Firefox browser up to version 46.0 and Firefox ESR 45.x up to version 45.1 allowed a remote attacker to organize DoS through an unidentified vector.
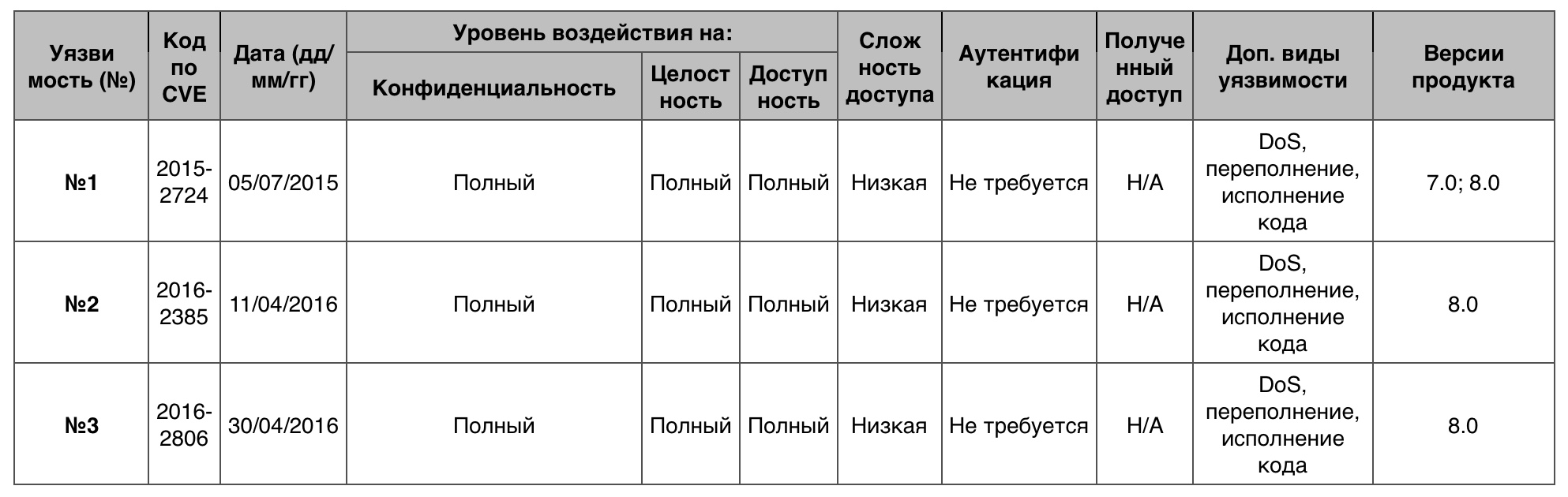
Table of vulnerabilities of the category “Memory damage” in the OS Debian Linux
Access to information
Total - 77. 10 points - 0 vulnerabilities.
Vulnerability # 1 (9.0)
The oarsh script in OAR up to version 2.5.7 allowed the remote authenticated cluster user to get valuable information and get privileges through vectors that include the OpenSSH options.
Vulnerability # 2 (7.5)
The htmlParseComment function in HTMLparser.c in libxml2 allowed access to information through an unclosed HTML comment.
Vulnerability # 3 (7.2)
x86 Xen emulation from 3.2.x to version 4.5.x incorrectly ignored redefinition of segments for instructions with register operands , which allowed the local guest user to get information through an unspecified vector.
The operand is the argument of the operation.

Access to Information Vulnerability Table on Debian Linux OS
Privilege Increase
Total detected 41 vulnerabilities. 10 points scored 2 of them.
Vulnerability # 1 (10)
rpc.statd in the nfs-utils package in various Linux distributions incorrectly strings with an unreliable format, which made it possible to obtain privileges remotely.
Vulnerability # 2 (10)
The pam_sm_authenticate function in pam_sshauth.c in libpam-sshauth allowed context-dependent hackers to bypass authentication or obtain privileges through the user's system account.
Vulnerability # 3 (9.0)
PostgreSQL incorrectly restricted access for unspecified user configuration settings for PL / Java, which allowed the attacker to obtain privileges through an unspecified vector.

Privilege Privilege Vulnerability Table on Debian Linux OS
Overflow
Total - 294. 10 points - 25.
Vulnerability # 1
Software overflow in the PointGFp constructor in Botan allowed a remote attacker to rewrite the memory and execute arbitrary code through the point created by ECC , which provoked a heap overflow.
ECC - error-correcting code.
Vulnerability # 2
Buffer overflow in the heap of the encode_msg function in encode_msg.c in the SEAS Kamailio module allowed the remote attacker to arrange DoS or execute code through a large SIP packet.
Vulnerability # 3
A number of unidentified vulnerabilities in Mozilla Firefox browser up to version 46.0 and Firefox ESR 45.x up to version 45.1 allowed a remote attacker to organize DoS through an unidentified vector.
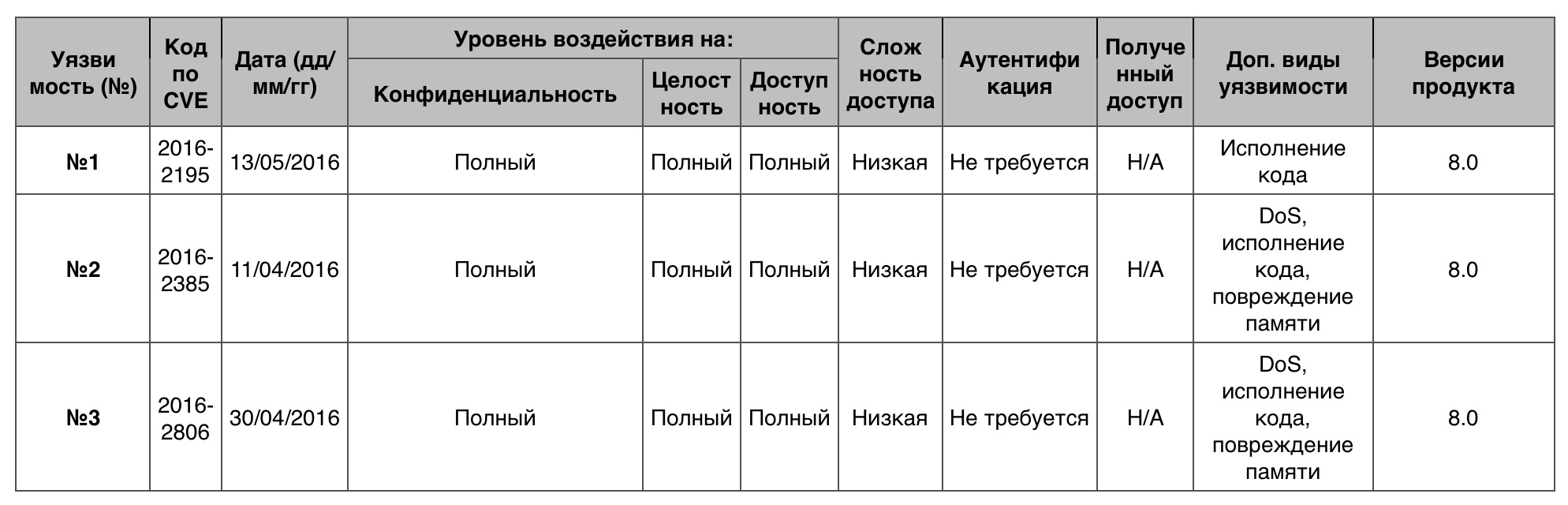
Table of vulnerabilities in the Overflow category in the Debian Linux OS
Despite the rather large number of vulnerabilities, especially in the DoS category, their exploit level and corresponding consequences are not so great. Due to its specific architecture, the Debian Linux OS can withstand most malicious attacks, which makes it extremely popular among companies that value their data. Even NASA uses this OS on astronaut workstations on the ISS.
3. Fedora

Fedora is the distribution of the GNU / Linux operating system, first released on November 6, 2003. This distribution is fully supported by the community, that is, those who use it and those who develop software for it. Fedora is a kind of sandbox for developers, as the software consists of free software, i.e. one that can be used indefinitely and even changed by the user.

DoS
Of the 205 vulnerabilities, 10 scored the maximum score.
Vulnerability # 1
Software overflow in the RTPReceiverVideo :: ParseRtpPacket function in Mozilla Firefox prior to version 43.0 and in Firefox ESR 38.x up to version 38.5 allowed the hacker to obtain information, organize DoS through the activation of the created WebRTC RTP package.
Vulnerability # 2
The buffer overflow in the XDRBuffer :: grow function in js / src / vm / Xdr.cpp in Mozilla Firefox prior to version 43.0 made it possible to arrange DoS through the generated JavaScript code.
Vulnerability # 3
Buffer overflow in nsDeque :: GrowCapacity function in xpcom / glue / nsDeque.cpp in Mozilla Firefox prior to version 43.0 made it possible to arrange DoS through changing the size of the deck .
December - deque is the abbreviated phrase “double-ended-queue”, which, in English, means two-way queue. Container Dec is very similar to container - Vector, as well as Vectors, Decks are dynamic arrays.
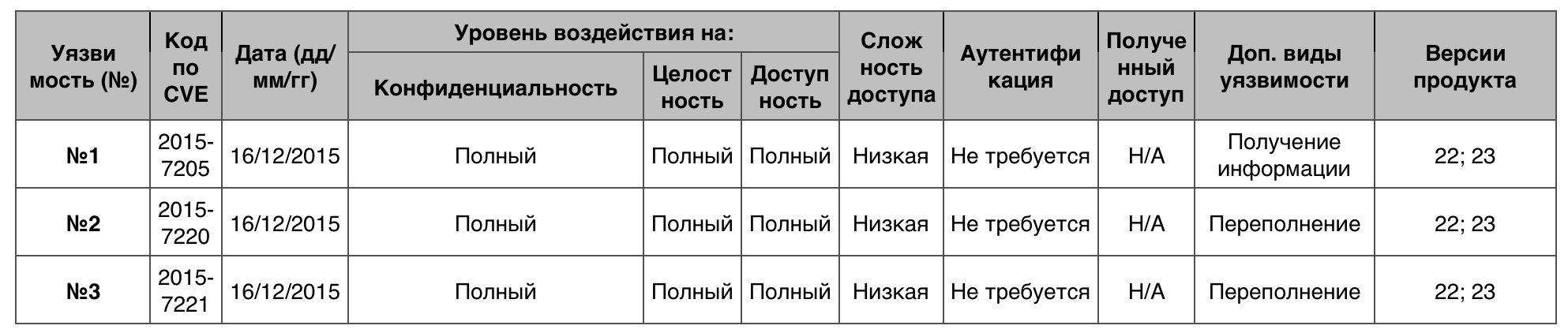
The DoS vulnerability table in Fedora.
Bypassing something.
Not one vulnerability out of 25 did not score 10 points.
Vulnerability # 1 (9.3)
OpenOffice.org (versions: 2.x, 3.0 to 3.2.1) allowed you to bypass the Python macro security restrictions and execute the Python code through the generated ODT file.
Vulnerability # 2 (9.3)
The scm plugin in mock allowed you to bypass the chroot protection mechanisms and get root privileges through the created spec file.
Vulnerability # 3 (7.5)
ganglia-web to version 3.7.1 allowed to bypass authentication.

Vulnerability table of the “Bypassing something” category in Fedora OS
Execution of the
Total code - 84. 10 points - 6.
Vulnerability # 1
The function get_rpm_nvr_by_file_path_temporary in util.py in setroubleshoot up to version 3.2.22 allowed to execute the command via the metacharacters in the file name.
Vulnerability # 2
Software overflow in the RTPReceiverVideo :: ParseRtpPacket function in Mozilla Firefox up to version 43.0 and in Firefox ESR 38.x up to version 38.5 allowed the hacker to get information, organize DoS through the activation of the created WebRTC RTP package.
Vulnerability # 3
A number of unidentified vulnerabilities in Mozilla Firefox browser up to version 43.0 allowed a remote attacker to execute arbitrary code via an undetected vector.

Code Execution Vulnerability Table in Fedora
Memory corruption
Total - 12. 10 points - 4.
Vulnerability # 1
The mozilla :: dom :: OscillatorNodeEngine :: ComputeCustom function in the Web Audio subsystem in Mozilla Firefox prior to version 29.0 and SeaMonkey up to version 2.26 allowed remote attackers to execute arbitrary code or arrange DoS through the created content.
Vulnerability # 2
A number of unidentified vulnerabilities in Mozilla Firefox browser up to version 43.0 and Firefox ESR 38.x up to version 38.5 allowed attackers to arrange DoS, damage memory, and execute arbitrary code.
Vulnerability # 3
A number of unidentified vulnerabilities in Mozilla Firefox browser up to version 43.0 allowed a remote hacker to execute arbitrary code via an unidentified vector.
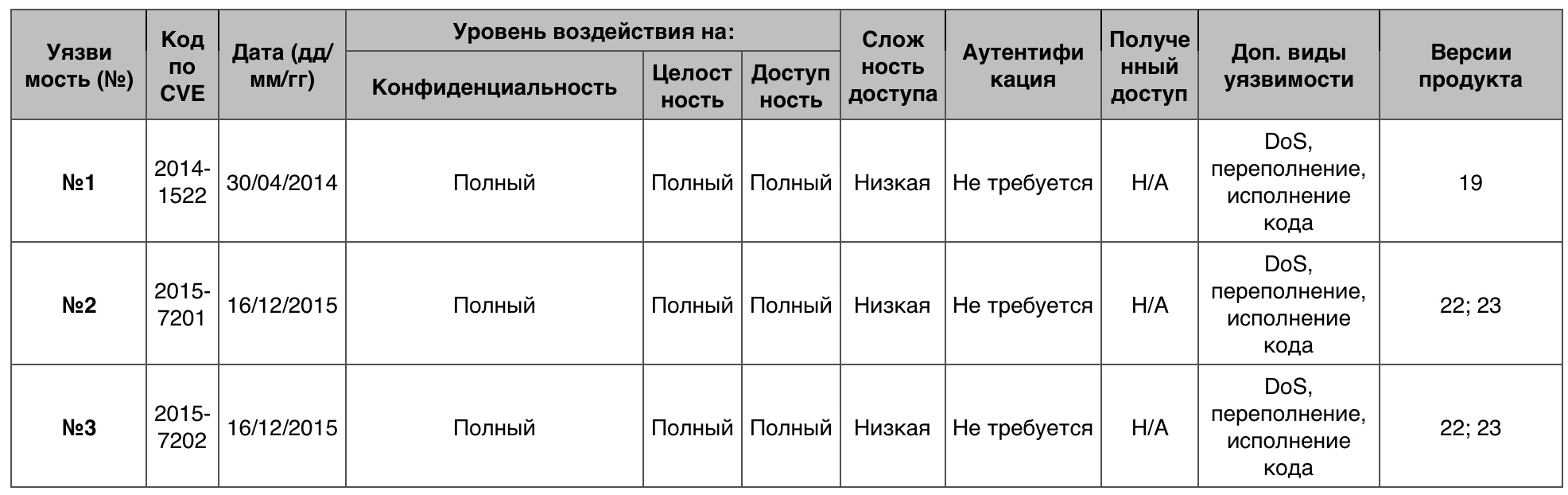
Memory Corruption Vulnerability Table on Fedora
Access to Information
Of the 53 vulnerabilities, only one scored 10 points.
Vulnerability # 1 (10)
Software overflow in the RTPReceiverVideo :: ParseRtpPacket function in Mozilla Firefox up to version 43.0 and Firefox ESR 38.x up to version 38.5 allowed remote attackers to obtain information, arrange DoS through the activation of the created WebRTC RTP package.
Vulnerability # 2 (7.2)
x86 Xen emulation from 3.2.x to version 4.5.x incorrectly ignored redefinition of segments for instructions with register operands, which allowed the local guest user to get information through an unspecified vector.
Vulnerability # 3 (6.9)
Multiple software overflows in Grub2 1.98-2.02 allowed to bypass authentication, get information, or arrange DoS through a space in the grub_username_get function in grub-core / normal / auth.c or the grub_password_get function in lib / crypto.c, which caused errors in the memory “Off” -by-two and out of bounds overwrite.

Vulnerability Table "Access to Information" in the Fedora OS
Increase of privileges
Of the 20 vulnerabilities, only one scored 10 points.
Vulnerability # 1 (10)
libuv prior to version 0.10.34 incorrectly handled group privileges, which allowed an attacker to obtain privileges through an unspecified vector.
Vulnerability # 2 (9.3)
The scm plugin in mock allowed you to bypass the chroot protection mechanisms and get root privileges through the created spec file.
Vulnerability # 3 (7.5)
The XGetImage function in X.org libX11 up to version 1.6.4 allowed remote X servers to obtain privileges through vectors including the image type and geometry, which caused an out-of-bounds read operation.

Vulnerability table of the “Privilege escalation” category in Fedora OS
Overflow of
8 vulnerabilities out of 123 scored 10 points.
Vulnerability # 1 A
buffer overflow in the DirectWriteFontInfo :: LoadFontFamilyData function in gfx / thebes / gfxDWriteFontList.cpp in Mozilla Firefox prior to version 43.0 allowed attackers to arrange DoS and have other types of implementations through the font name.
Vulnerability # 2
The buffer overflow in the XDRBuffer :: grow function in js / src / vm / Xdr.cpp in Mozilla Firefox prior to version 43.0 allowed the remote attacker to arrange DoS through the generated JavaScript code.
Vulnerability # 3
Buffer overflow in nsDeque :: GrowCapacity function in xpcom / glue / nsDeque.cpp in Mozilla Firefox browser prior to version 43.0 allowed a remote attacker to arrange DoS by activating the resize of the deck.

Overflow Vulnerability Table in Fedora
Despite the fact that Fedora has been around for almost 15 years, the total number of vulnerabilities recorded is relatively small. It can be argued that this is due to the use of open source software. Since the users themselves improve it. The more people working on the software, the more chances he has to avoid some bugs and holes. As they say, one head is good, but two is better.
4. Ubuntu Linux

Ubuntu Linux is a Debian GNU / Linux based operating system. The first appearance is October 20, 2004. The estimated number of users is about 20 million. Another OS with free software. Extremely popular. It is used both in the French government, and as the main OS on the workstations of Google employees, and as a database server for the Wikipedia project, etc.

DoS
Of the 441 vulnerabilities, only 12 scored 10 points.
Vulnerability # 1
A number of unidentified vulnerabilities in Google Chrome prior to version 50.0.2661.75 resulted in DoS via an unidentified vector.
Vulnerability # 2
The xmlNextChar function in libxml2 up to version 2.9.4 allowed the remote attacker to set up a DoS through the created XML document.
Vulnerability # 3
The usbip_recv_xbuff function in drivers / usb / usbip / usbip_common.c in the Linux kernel before version 4.5.3 allowed the remote attacker to arrange DoS through the created value in the USB / IP package.

Vulnerability table of the DoS category in Ubuntu Linux OS
Bypassing anything
Of the 70 vulnerabilities, no one was awarded 10 points.
Vulnerability # 1 (9.3)
OpenOffice.org (version: 2.x, 3.0 to 3.2.1) made it possible to bypass Python macro security restrictions and execute Python code through the generated ODT file.
Vulnerability # 2 (9.0)
The openvswitch-agent process in the OpenStack Neutron from 2013.1 to 2013.2.4 and from 2014.1 to 2014.1.1 allowed the remote authenticated user to bypass security protocols through invalid CIDR in the group security rule, which prevented the activation of other rules.
Vulnerability # 3 (7.5)
nbd-server in Network Block Device (nbd) to version 3.5 incorrectly checked IP addresses, which could allow a remote attacker to bypass established access restrictions via an IP address that partially coincides in the authfile configuration file.
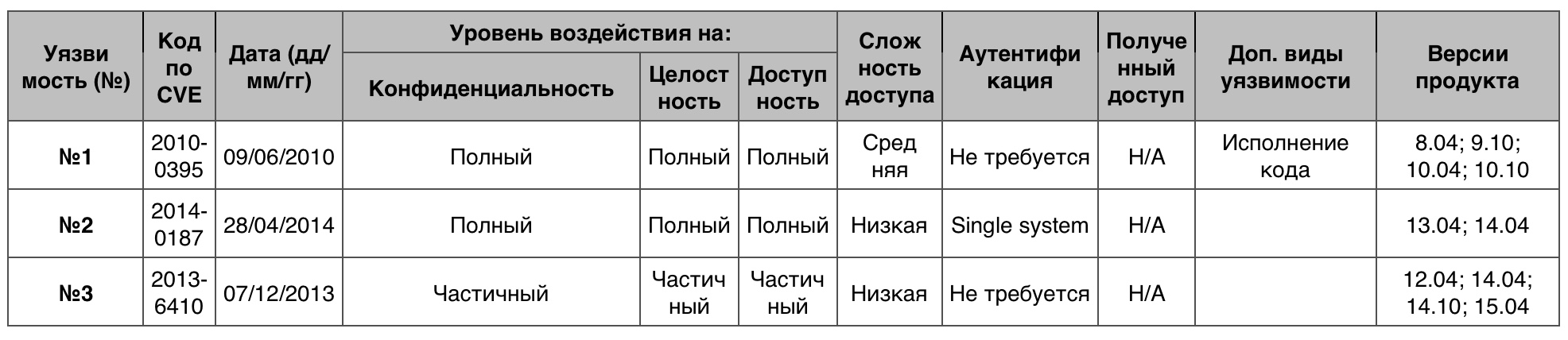
Vulnerability table “Bypassing something” category in Ubuntu Linux OS
Code execution
18 vulnerabilities out of 152 scored 10 points.
Vulnerability # 1
EPHEMERAL, HTTPS, MVG, MSL, TEXT, SHOW, WIN and PLT coders in ImageMagick up to version 6.9.3-10 and 7.x up to version 7.0.1-1 allowed the remote hacker to execute code through the metacharacters shell in the created image .
Vulnerability # 2
The OpenBlob function in blob.c in GraphicsMagick prior to version 1.3.24 and ImageMagick allowed a remote attacker to execute arbitrary code through the “|” symbol at the beginning of the file name.
Vulnerability # 3
The use-after-free vulnerability in the __sys_recvmmsg function in net / socket.c in the Linux kernel version 4.5.2 allowed a remote attacker to execute arbitrary code through vectors due to the use of an improper system call recvmmsg during error handling.

Code Execution Vulnerability Table in Ubuntu Linux OS
Memory corruption
10 points out of 41 vulnerabilities scored only 6.
Vulnerability # 1
Many unknown vulnerabilities in Mozilla Firefox browser up to version 39.0, Firefox ESR 31.x up to 31.8 and from 38.x up to 38.1, as well as Thunderbird up to version 38.1 allowed the remote hacker to damage the memory through an unspecified vector.
Vulnerability # 2
A number of unidentified vulnerabilities in Mozilla Firefox browser up to version 40.0 and Firefox ESR from 38.x to 38.2 allowed a remote attacker to cause memory damage and application crashes through an undefined vector.
Vulnerability # 3
A number of unidentified vulnerabilities in Mozilla Firefox browser prior to version 40.0 allowed a remote attacker to cause memory damage through an unidentified vector.

Table of vulnerabilities category "memory damage" in the OS Ubuntu Linux
Access to information
None of the 86 vulnerabilities scored 10 points.
Vulnerability # 1 (8.5)
The OZWPAN driver in the Linux kernel up to version 4.0.5 relied on the unchecked field length value during packet parsing, which allowed the remote attacker to obtain information from the kernel memory or to organize DoS through the created package.
Vulnerability # 2 (7.2)
The __switch_to function in arch / x86 / kernel / process_64.c in the Linux kernel incorrectly switched the context of IOPL 64-bit PV Xen guests, which allowed the local guest user to get privileges, arrange DoS or get information using port access I / o.
Vulnerability # 3 (7.2)
The get_rock_ridge_filename function in fs / isofs / rock.c in the Linux kernel before version 4.5.5 incorrectly processed NM input data containing “\ 0” characters, which allowed the local user to retrieve information from the kernel memory through the isofs file system created.
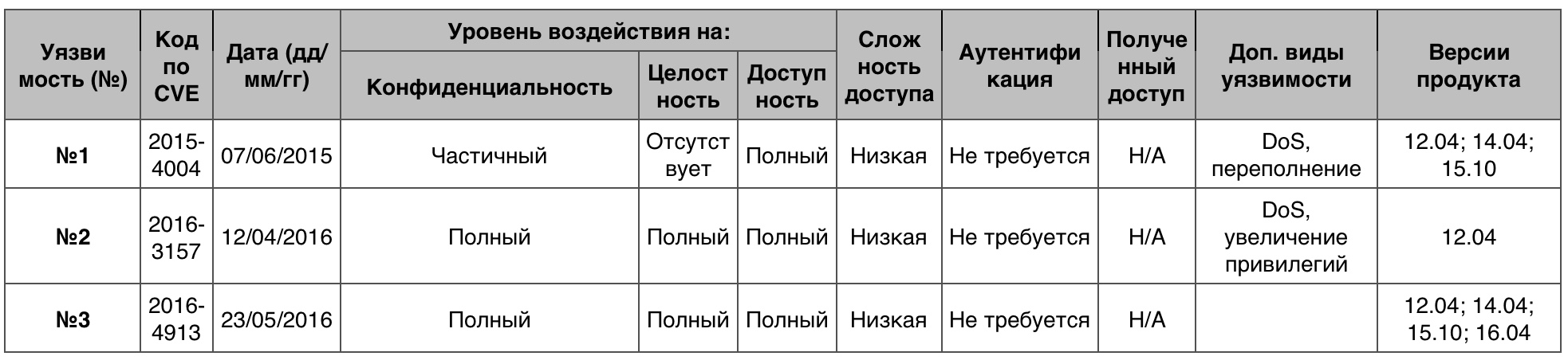
Table Vulnerability category "Access to information" in the Ubuntu Linux operating system
Increase privileges
Total fixed 44 vulnerabilities, of which none has scored 10 points.
Vulnerability # 1 (9.0)
PostgreSQL incorrectly restricted access for unspecified user configuration settings for PL / Java, which allowed a hacker to obtain privileges through an unspecified vector.
Vulnerability # 2 (7.6)
The default settings in the openstack-neutron package prior to version 2013.2.3-7 incorrectly processed the rootwrap configuration file, which allowed the remote attacker to obtain privileges through the created configuration file.
Vulnerability # 3 (7.5)
click / install.py in click did not require the tarballs package files in the file system to start with ./, which allowed the remote attacker to install and modify security protocols and obtain privileges through the created package.
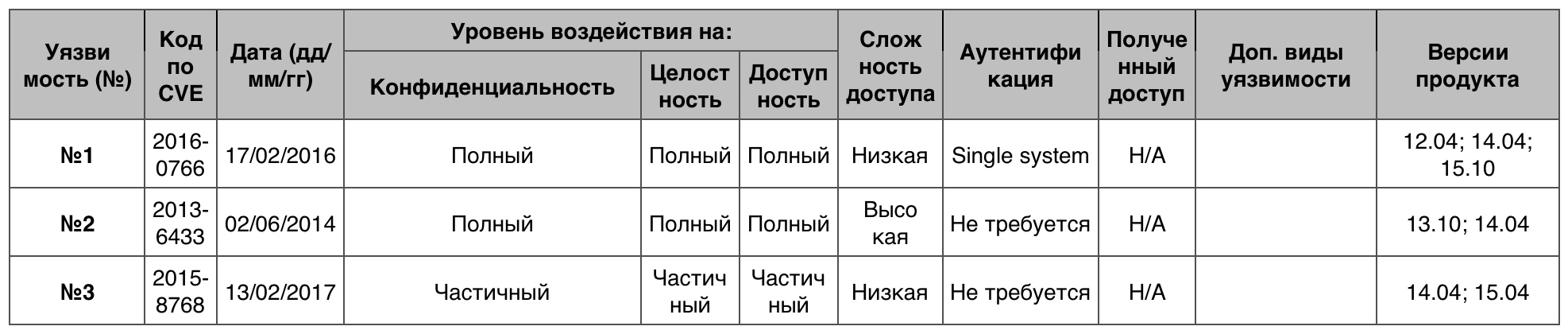
Vulnerability table of the “Privilege escalation” category in the Ubuntu Linux OS
Overflow
Total - 223 vulnerabilities. 10 points - 14 vulnerabilities.
Vulnerability # 1
Unknown vulnerability in Oracle Java SE (6u105, 7u91, 8u66); Java SE Embedded 8u65; JRockit R28.3.8 allowed a remote attacker to affect the privacy, integrity and availability of the system through a vector that includes the AWT. NOTE: Oracle did not confirm the words of third parties that it was a software buffer overflow in the readImage function, which allowed the remote attacker to execute code through the created image data.
Vulnerability # 2
The xmlNextChar function in libxml2 up to version 2.9.4 allowed a remote attacker to create a buffer overflow through the created XML document.
Vulnerability # 3
The usbip_recv_xbuff function in drivers / usb / usbip / usbip_common.c in the Linux kernel before version 4.5.3 allowed the remote attacker to cause a buffer overflow through the generated length value in the USB / IP package.
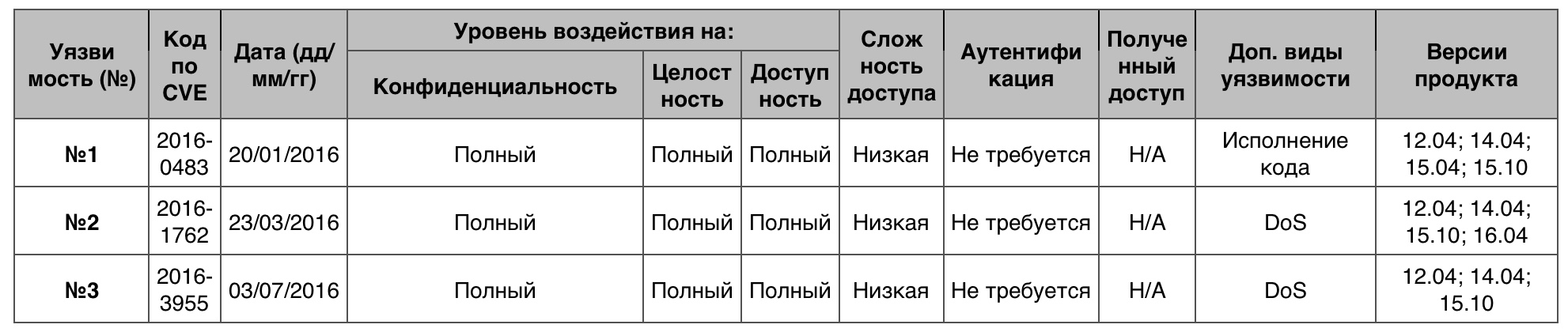
Table of vulnerabilities of the category "Overflow" in OS Ubuntu Linux
Most of all vulnerabilities are fixed in the category "DoS" (441), but there are very few critical ones. As for the other categories, among them the number of top-level vulnerabilities also does not cause concern. Resistance to external malicious system effects and the insignificance of the consequences of exploiting vulnerabilities are one of the decisive factors in choosing this OS.
5. WatchOS

WatchOS - a special operating system for Apple Watch, was released on April 24, 2015. OS is not for PC, not for server, but for wristwatches. But this is still an operating system, and it also, like others, has its drawbacks.
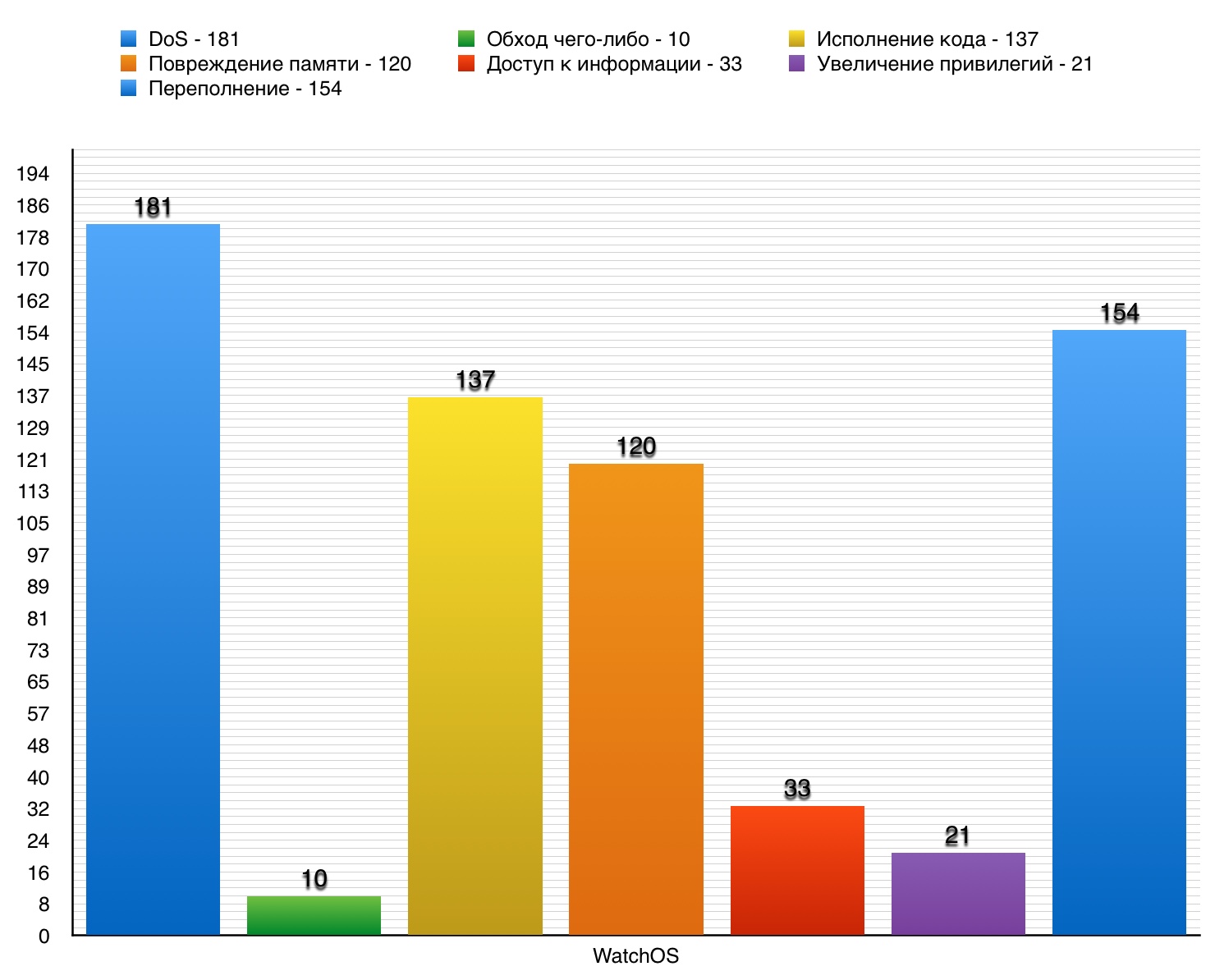
DoS
Of the 181 vulnerabilities, 9 pieces scored 10 points.
Vulnerability # 1
Vulnerability was detected in watchOS prior to version 4. The basis is the “Wi-Fi” component, which allowed a remote attacker to execute code in a privileged context or arrange DoS through the created Wi-Fi traffic.
Vulnerability # 2
The xmlNextChar function in libxml2 up to version 2.9.4 allowed the remote attacker to set up a DoS through the created XML document.
Vulnerability # 3
The LaunchServices component allowed an attacker to execute arbitrary code or organize DoS (memory corruption) through a modified plist.

Table of vulnerabilities in the DoS category in WatchOS OS.
Bypassing something
10 vulnerabilities, of which there are no those that scored 10 points.
Total - 16. 10 points - 0.
Vulnerability # 1 (9.3)
The kernel in watchOS prior to version 2.2 incorrectly restricted the execution permission, which allowed the hacker to bypass the code signature protection mechanism through the created application.
Vulnerability # 2 (7.2)
Implementing the processor_set_tasks API in the OS allowed a local user to bypass the rights protection mechanism and gain access to the ports of tasks of the executable process through the use of root privileges.
Vulnerability # 3 (6.8)
AppSandbox in watchOS prior to version 2.1 incorrectly processed hard links, which allowed a remote user to bypass the revocation of access to Contacts through the created application.

Table of vulnerabilities in the category “Bypassing something” in the WatchOS OS
Execution of code
7 of 137 vulnerabilities scored 10 points.
Vulnerability # 1 of
libxml2 in watchOS prior to version 3 allowed a remote attacker to execute code or set up a DoS through the generated XML document.
Vulnerability # 2
The LaunchServices component in watchOS prior to version 2.1 allowed an attacker to execute arbitrary code in a privileged context or to build DoS through a modified plist .
plist - files that store serialized objects.
Vulnerability # 3 (9.3)
IOKit in the OS kernel allowed the attacker to execute code in a privileged context or to arrange DoS through the application created.

Table “Code Execution” vulnerability table in WatchOS.
Memory corruption
8 vulnerabilities out of 120 scored 10 points.
Vulnerability # 1 (9.3)
IOHIDFamily allowed a cracker to execute code in a privileged context or to set up a DoS through the application created.
Vulnerability # 2 (9.3)
dyld in Dev Tools allowed a cracker to execute code in a privileged context or arrange DoS through the application created.
Vulnerability # 3 (9.3)
WebKit allowed a cracker to execute code or set up a DoS through the created website.
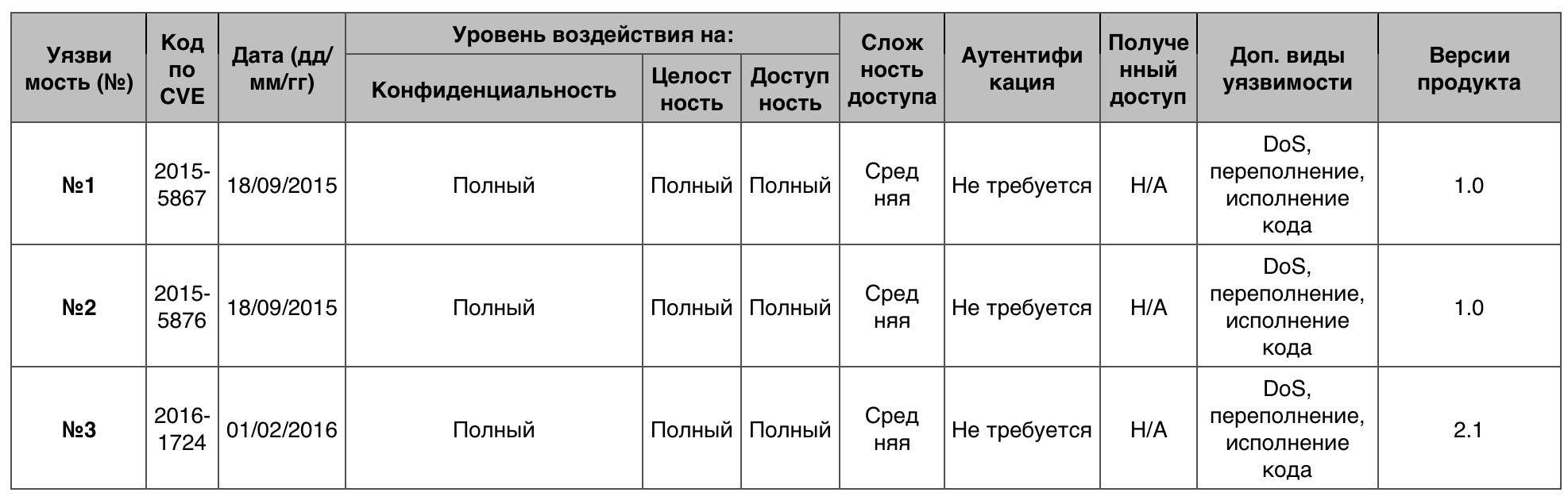
Table of vulnerabilities of the category "memory corruption" in OS WatchOS
Access to information
Among the 33 there are no vulnerabilities that scored 10 points.
Vulnerability # 1 (6.8)
The libxml2 component allowed a remote attacker to obtain information or set up a DoS through the generated XML file.
Vulnerability # 2 (5.8)
The xmlSAX2TextNode function in SAX2.c in the push interface in the HTML parser in libxml2 prior to version 2.9.3 allows an attacker to arrange DoS or get information through the generated XML data.
Vulnerability # 3 (5.8)
IOAcceleratorFamily in watchOS prior to version 3 allowed the remote attacker to obtain valuable information from the process memory or to set up a DoS through the created website.

Vulnerability table of the category “Access to Information” in WatchOS OS
Privilege Increase
Only 1 vulnerability out of 21 scored 10 points.
Vulnerability # 1 (10)
The kernel in the OS allowed a local user to obtain privileges or arrange DoS via an unspecified vector.
Vulnerability # 2 (7.2)
IOMobileFrameBuffer in the OS allowed a local user to obtain privileges or organize DOS through an unspecified vector.
Vulnerability # 3 (7.2)
The Disk Images component allowed a local user to get privileges or set up a DoS through an unspecified vector.
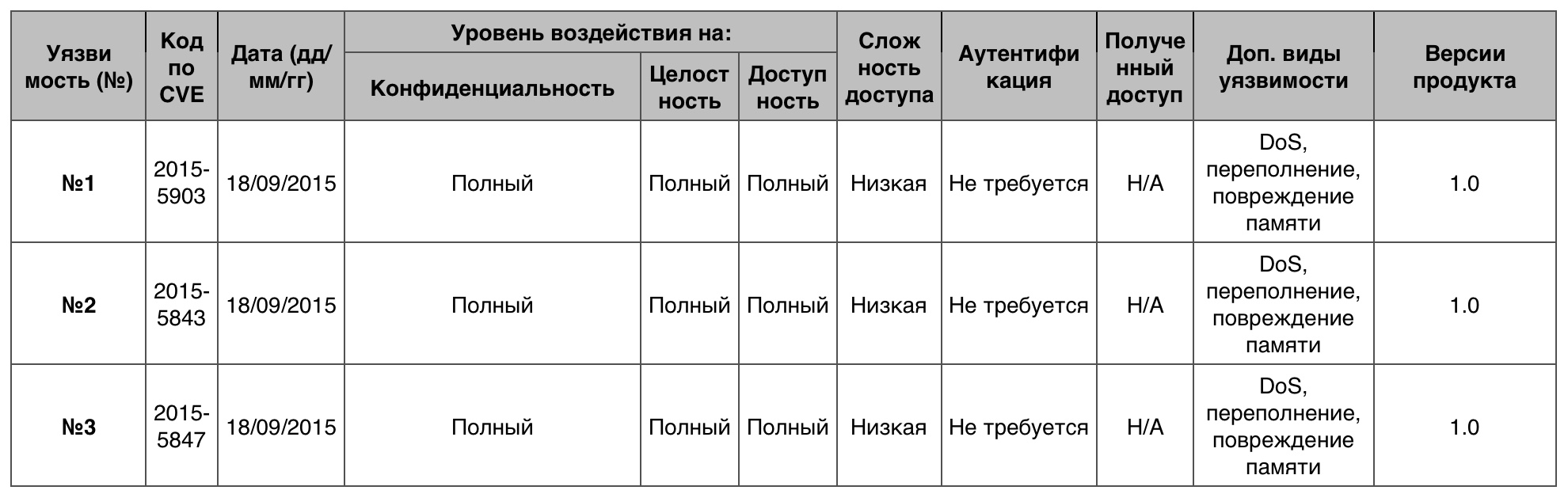
Vulnerability table of the “Privilege escalation” category in WatchOS OS
Overflow of
10 vulnerabilities out of 154 scored 10 points.
Vulnerability # 1 (9.3)
GasGauge in the OS allowed the hacker to execute arbitrary code in a privileged context or to arrange DoS through the created application.
Vulnerability # 2 (9.3)
FontParser in watchOS prior to version 2.2 allowed a remote attacker to execute arbitrary code or set up a DoS through the created PDF document.
Vulnerability # 3 (9.3)
TrueTypeScaler in watchOS prior to version 2.2 allowed a remote user to execute arbitrary code or set up a DoS through the created font file.

Vulnerability table of the category "Overflow" in the OS WatchOS The
closeness of the software from Apple, in that clean and their operating systems, does not prevent them from having some vulnerabilities. At the moment, the number of which is not so shocking, but do not forget that WatchOS is a young product. The future of this OS in terms of vulnerabilities is still unclear. To make any assumption will be bold and unjustified.
As we have already seen, after three parts of our research, none of the operating systems is not without its weaknesses, in this case vulnerabilities. However, this is not a reason to say that this or that OS is bad and cannot be used. In the next, final, part we will look at the scandalous Windows Vista and a couple of rather exotic systems that not everyone knows about. Have a good day and a minimum of bugs in the software.
As advertising. These are not just virtual servers! These are VPS (KVM) with dedicated drives, which can be no worse than dedicated servers, and in most cases - better! We made VPS (KVM) with dedicated drives in the Netherlands and the USA(configurations from VPS (KVM) - E5-2650v4 (6 Cores) / 10GB DDR4 / 240GB SSD or 4TB HDD / 1Gbps 10TB available at a uniquely low price - from $ 29 / month, options with RAID1 and RAID10 are available) , do not miss the chance to issue order for a new type of virtual server, where all resources belong to you, as allocated, and the price is much lower, with a much more productive hardware!
How to build the infrastructure of the building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny? Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA!
