Amateur-3 robbery or the same eggs, only in profile
Good evening Habr!
Again, I have something to tell. Perhaps you remember my previous topics ( 1 , 2 ) on the topic of storing / transferring passwords in clear text? The holes I found were quickly patched, but no one made the right conclusions (from the technical staff of the companies). Therefore, you are reading this topic.
As I promised, I decided to check some other popular mail server with a mail collector service. The choice fell mail.qip.ru. Why? Yes, because it is quite old and well-known to many Pochta.ru, but under a different sign.
1. Hmm. AJAX pop-up window will scare away almost any amateur. But not me =)

2. With almost no hope, I look in the source code and suddenly I find there a blank for the pop-up window on the layers, carefully marked by the authors of the code. I’m the type of password field, and the magic Opera browser helps me apply the result to the directly active page
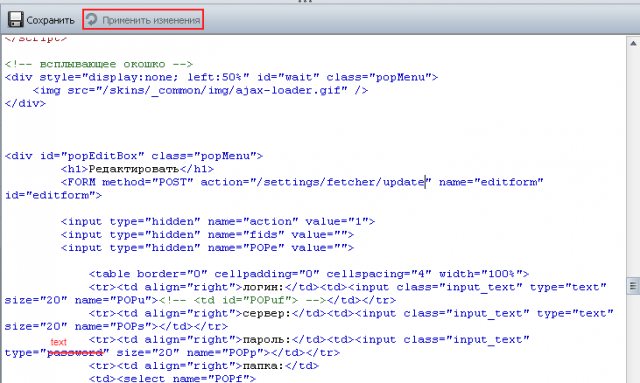
3. Voila, everything is in the palm of your hand
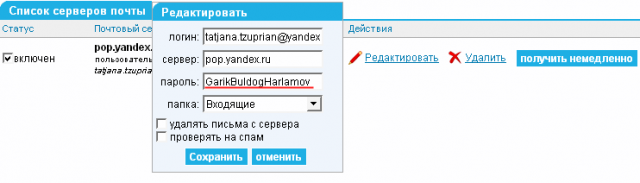
4. I remember Yandex.Mail and its new NEO interface.
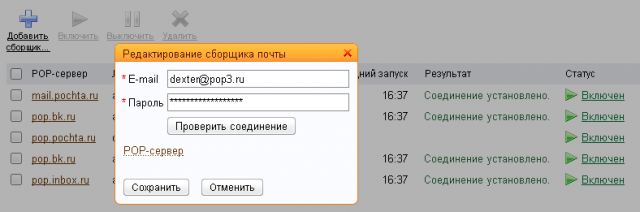
5. The page code is not so readable, but the principle of its work is similar. I find a blank, change the type of field, apply ...

6. “Fiasco, fiasco!” The drunk parrot shouted.

What did Comrade say there? kukutz :
And the remaining 99% use the NEO interface?
UPD Yandex fixed the problem .
Again, I have something to tell. Perhaps you remember my previous topics ( 1 , 2 ) on the topic of storing / transferring passwords in clear text? The holes I found were quickly patched, but no one made the right conclusions (from the technical staff of the companies). Therefore, you are reading this topic.
As I promised, I decided to check some other popular mail server with a mail collector service. The choice fell mail.qip.ru. Why? Yes, because it is quite old and well-known to many Pochta.ru, but under a different sign.
1. Hmm. AJAX pop-up window will scare away almost any amateur. But not me =)

2. With almost no hope, I look in the source code and suddenly I find there a blank for the pop-up window on the layers, carefully marked by the authors of the code. I’m the type of password field, and the magic Opera browser helps me apply the result to the directly active page

3. Voila, everything is in the palm of your hand

4. I remember Yandex.Mail and its new NEO interface.

5. The page code is not so readable, but the principle of its work is similar. I find a blank, change the type of field, apply ...

6. “Fiasco, fiasco!” The drunk parrot shouted.

What did Comrade say there? kukutz :
How? Less than one percent of Yandex.Mail users use the classic interface. To exploit the vulnerability, you must simultaneously:
And the remaining 99% use the NEO interface?
UPD Yandex fixed the problem .
