StealthWatch: basic concepts and minimum requirements. Part 1
- Tutorial

1. Introduction
This article is about the Cisco StealthWatch Network Monitoring Product.
Cisco Systems is actively promoting it as a product to improve network security, so let's get it right.
There has already been an article on this topic in the TS Solution blog , in this series of articles I will focus on configuring and deploying the product. Nevertheless, for those who have heard about StealthWatch for the first time, we define basic concepts.
“The Stealthwatch system provides industry- leading network monitoring and security analysis capabilities to accelerate and more accurately detect threats, respond to incidents and conduct investigations,” says Cisco, and lists about 50 success stories you can reviewhere .
Based on the telemetry data of your infrastructure, StealthWatch allows you to:
· detect a variety of cyber attacks (APTs, DDoS, 0-day, data leakage, botnet)
· monitor compliance with security policies
· detect anomalies in the behavior of users and equipment
· conduct crypto audit of traffic (ETA technology)
At the heart of StealthWatch is the collection of NetFlow and IPFIX from routers, switches, and other network devices. As a result, the network becomes a sensitive sensor and allows the administrator to look where traditional methods of protecting the network, such as NGFW, cannot reach. The following protocols can collect StealthWatch: NetFlow (starting with version 5), sFlow, jFlow, cFlow, Netstream, nvzFlow, IPFIX, Packeteer-2 and other custom improvements.
2. What tools does this software use for analytics?
Firstly, behavioral modeling and behavioral signatures, in other words, constant monitoring of each device in the network and the ability to determine the basic indicators of normal and abnormal behavior. For each host, whether a user, server or router, its own baseline is built (an ideal behavior model), deviating from which we see all the anomalies in relation to this host.
As an example: a user suddenly started downloading large amounts of data, although he never did - StealthWatch almost instantly detects this.
Secondly, global threat analytics. This refers to integration with the well-known Cisco Talos - a huge database of signatures of known attacks, updated worldwide in real time.
Third, the good old machine learning, in the case of Cisco, based on Cognitive Intelligence technology.
The technology also underlies the ETA solution - Encrypted Traffic Analytics, which allows you to determine if an encrypted connection is bad without decrypting it (attack, unwanted traffic and C&C communications).
3. A brief introduction to the interface
So that you understand how it looks and do not come up with beautiful pictures, I want to show a couple of screenshots from Cisco lab work that can be done by everyone in dcloud .
Quite convenient charts and graphs in the dashboard show general network statistics: alarms, from whom and when they were, traffic of network protocols, applications, and security incidents.
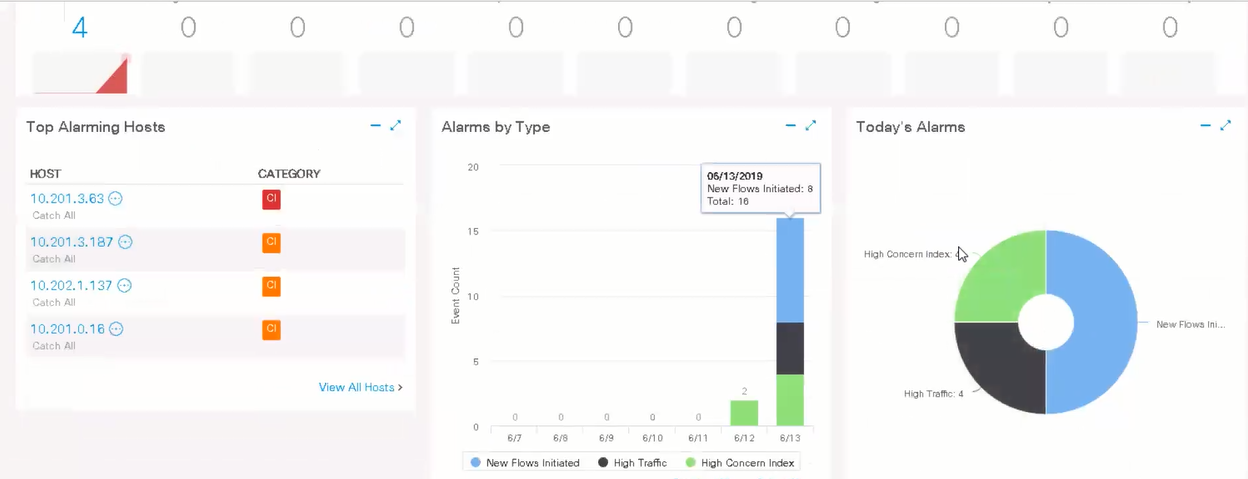
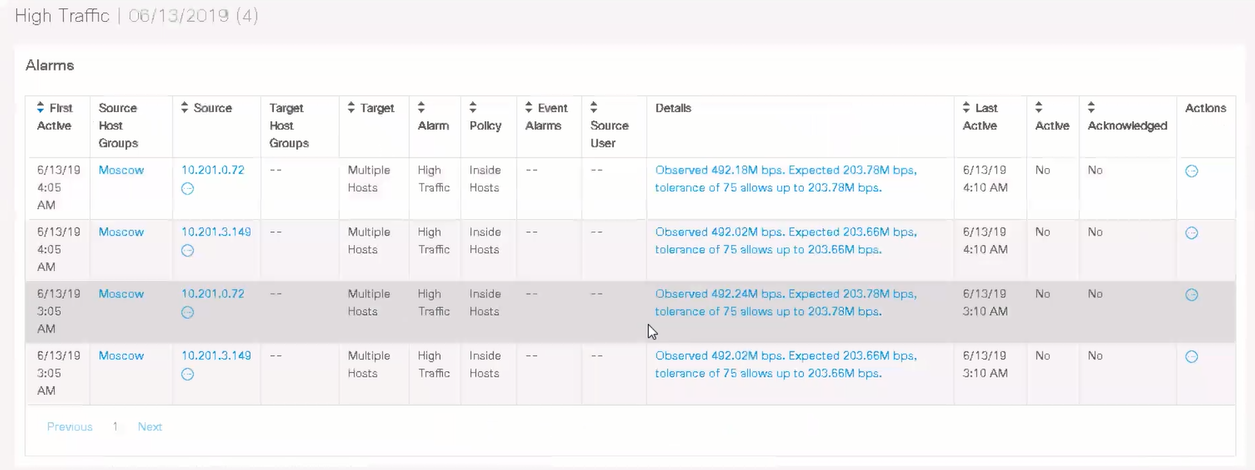
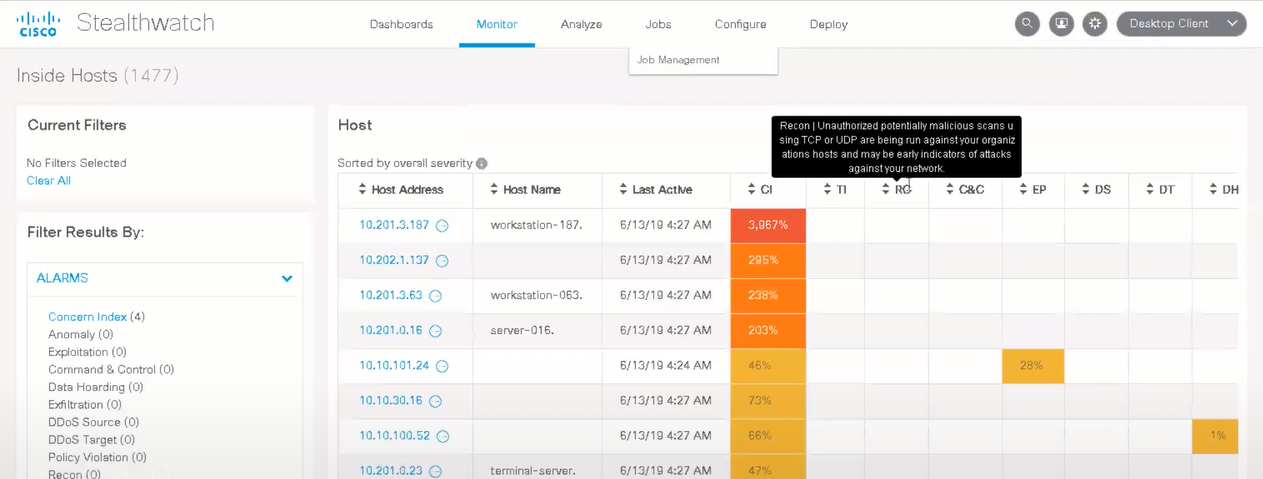
In the monitor tab, a more detailed listing of suspicious hosts occurs and a table whose values are responsible for suspicious behavior and attacks on a particular host.
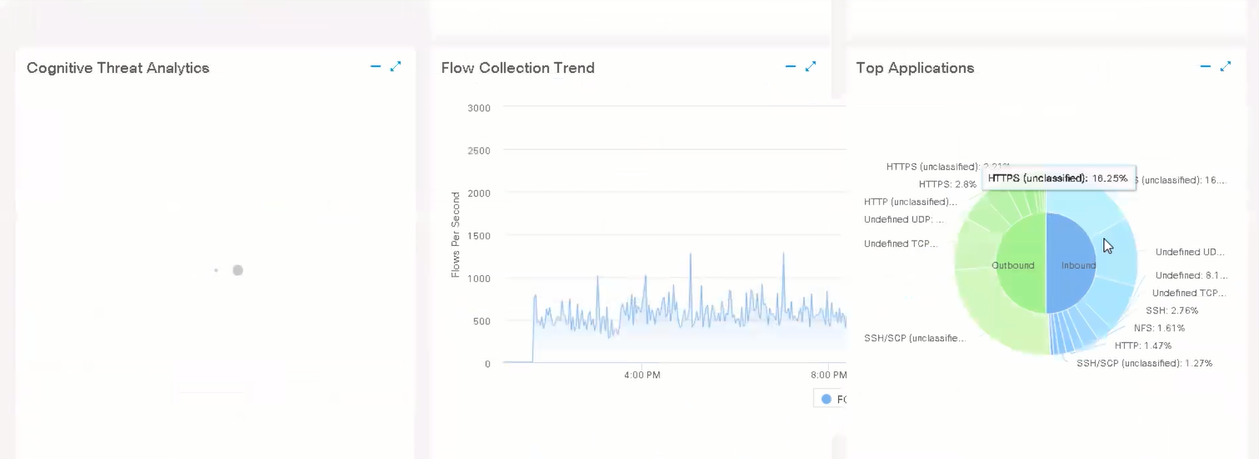
Next, you can observe the application traffic, broken down by protocols. Of course, the time period changes, you can fall through inward, highlighting the necessary section (in Flow in the dashboard you can also “fall through”).
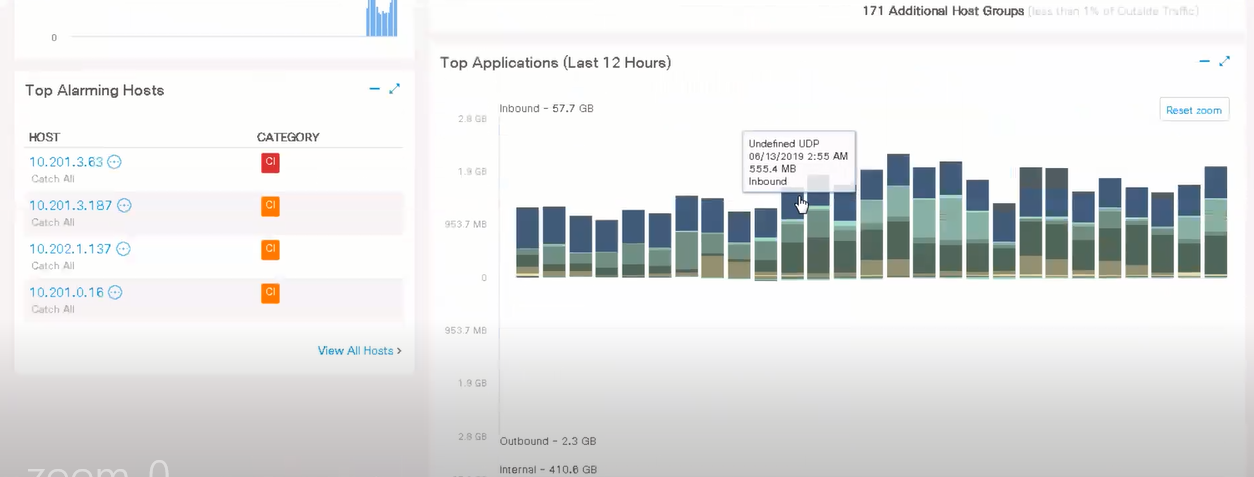
All settings and complete immersion in the interface, you will see in the following articles.
4. Architecture
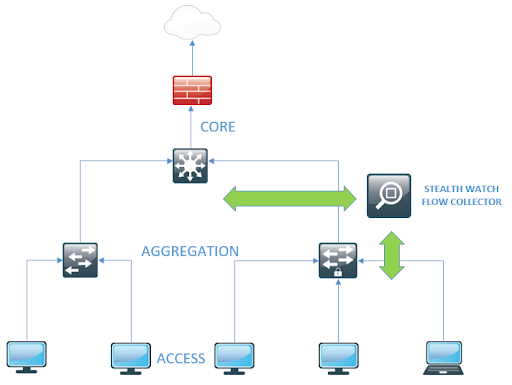
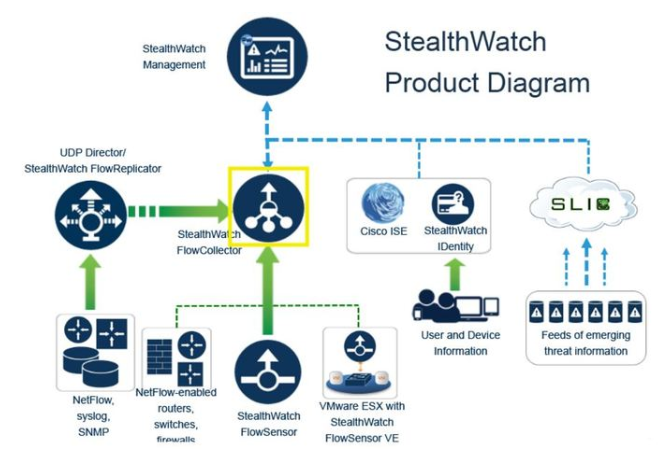
The architecture of StealthWatch is on the one hand a little more complicated than that of its competitors, but on the other hand it is more granular and allows for more customization. The required components are Flow Collector (FC) and StealthWatch Management Console (SMC).
FlowCollector is a physical or virtual device that collects NetFlow data and NBAR application data from switches, routers, and firewalls.
SMC is a physical or virtual device that combines, organizes, and graphically represents data collected from FCs. Integration with AD and Cisco ISE is possible.
As optional, but no less interesting devices, I highlight FlowSensor (FS) and UDP-Director (UDP-D).
The first can be either a physical or virtual device, and is a solution for generating NetFlow from legacy devices or when you use cheap access level switches. FlowSensor can provide the formation of NetFlow records for all traffic arriving using the SPAN, RSPAN protocols.
Moreover, FlowSensor in most cases is required to use ETA technology (detection of malicious software in encrypted traffic), however, starting with ISR and ASR series, routers can work with ETA without Flow Sensor.
UDP-D is a physical device that collects NetFlow data and sends it as a single and compressed stream to a FlowCollector. As an example, it can export a stream at the same time to StealthWatch, SolarWinds, and something else. It also reduces the load on the Flow Collector and optimizes network performance. In truth, it is only necessary to export a stream to different platforms. As a result, the most expensive component of the StealthWatch architecture is not so necessary.
The architecture looks something like this in a simplified version:
And in a more complete (complex and incomprehensible) version:
5. Minimum system requirements
Now you can switch to “you” with StealthWatch, so let's look at the minimum resources for deploying it on the network.
For StealthWatch Management Console:
RAM 16 GB (24GB recommended), 3 CPUs, 125 GB disks
For FlowCollector:
RAM 16GB, 2 CPUs, 200 GB disks
* Supports <250 exporters, <125000 hosts, <4500 fps
And if we want a complete architecture , which we will consider later, we should also allocate resources for FlowSensor and UDP-Director.
For FlowSensor:
the RAM 4 GB, 1 CPU, 60 GB disk
for the UDP-Director:
the RAM 4GB, 1 CPU, 60 GB disc
* Preferably SSD for all the VM, but NetFlow «flies" precisely on FlowCollector, so for FC resources to allocate stands First of all, an
important nuance is that images for these virtual machines are available only for VMware (ESXi) and KVM. Requirements for them.
VMware (ESXi):
Version 6.0 or 6.5.
Live migration and snapshots are not supported.
KVM:
Using any compatible Linux distribution.
KVM host versions are libvirt 3.0.0, qemu-KVM 2.8.0, Open vSwitch 2.6.1, and Linux Kernel 4.4.38. They may be others, but Cisco engineers performed tests on these and confirm their operability.
If you are interested in looking at the security of your network from a different angle, you can contact us at sales@tssolution.ru and we will conduct a demonstration or pilot StealthWatch on your network for free.
That's all for now. In the next article, we will proceed directly to the deployment of StealthWatch and talk more about the nuances of this process.
