What is what and who is who in the DDoS protection market
I have been in the digital market since 2008, and during this time I have seen the transition from websites on Joomla (remember this?) To today's Internet with its mobile-first applications and hundreds of millions of IoT devices connected to the network.
Attacks on the Internet have also developed quite well during this time :)
But the DDoS protection market and the anti-attack technology used by operators are still quite closed.
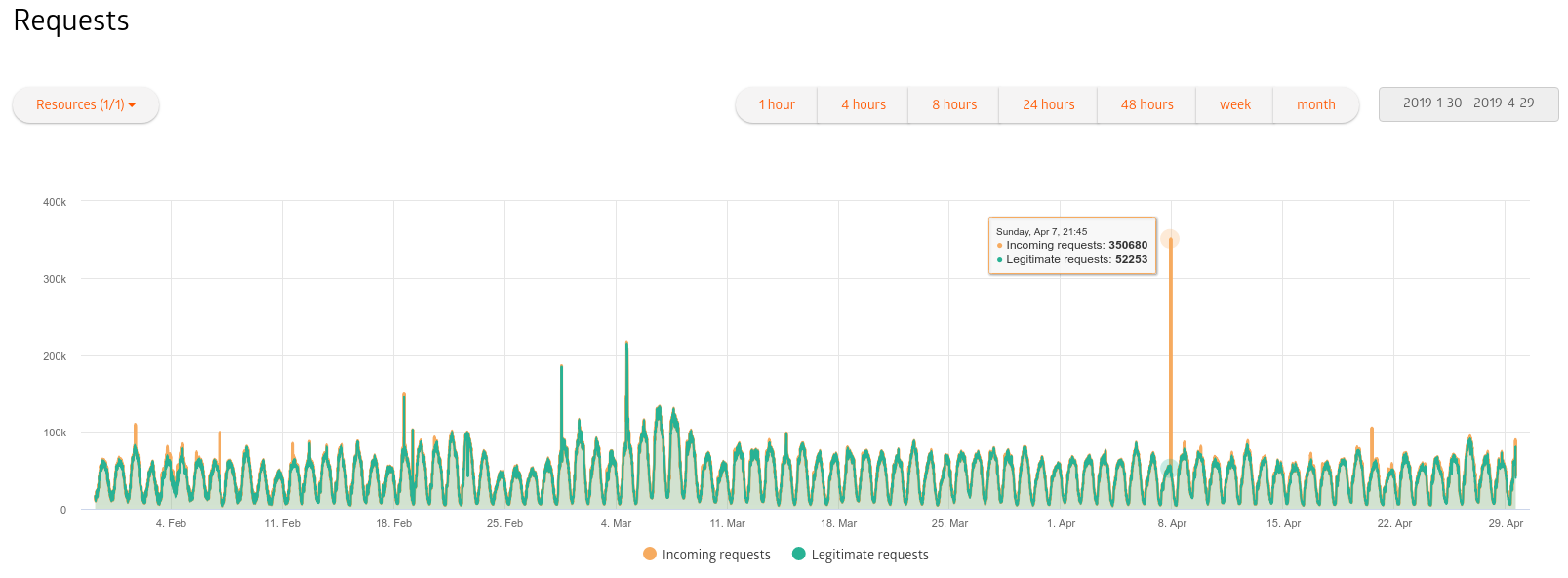
I’ll tell you what I learned about him, supporting websites and Internet services that have been under constant attack for the past few years. Regular attacks. 350k req total, 52k req legitimate The first attacks appeared almost simultaneously with the Internet. DDoS as a phenomenon has become widespread since the late 2000s ( see www.cloudflare.com/learning/ddos/famous-ddos-attacks
)
From about 2015-2016, almost all hosting providers came under protection from DDoS attacks, like most prominent sites in competitive areas (do whois on the IP sites eldorado.ru, leroymerlin.ru, tilda.ws, see the network of protection operators).
If 10-20 years ago most of the attacks could be repelled on the server itself (evaluate the recommendations of the Lenta.ru system administrator Maxim Moshkov from the 90s ), now everything is more complicated.
First, briefly about the types of attacks.
These attacks aim to “fill up” the channel with the server or “kill” its ability to receive new traffic.
Although SYN / ACK flood and amplification are very different, many companies deal with them equally well. Problems arise with attacks from the following group.
The goal is to make the server “work hard”, process a lot of “as if real requests” and be left without resources for real requests.
Although there are other attacks, these are the most common.
Serious attacks at the L7 level are created in a unique way for each attacked project.
Why 2 groups?
Because there are many who know how to beat off attacks at the L3 / L4 level well, but either do not take up protection at the application level (L7) at all, or so far deal with them weaker than the alternatives.
(my personal look)
To fight off attacks with amplification (“blocking” the server’s channel), there are enough wide channels (many of the protection services connect to most major backbone providers in Russia and have channels with a theoretical capacity of more than 1 Tbit). Do not forget that very rare attacks with amplification last longer than an hour. If you are Spamhaus and everyone does not like you - yes, you can try to put down channels for several days, even at the risk of further survival of the used world botnet. If you just have an online store, even if it is mvideo.ru - 1 Tbit for several days, you will see very soon (I hope).
In order to repel attacks with SYN / ACK flood, packet fragmentation, there is a need for equipment or software systems to detect and block such attacks.
Such equipment is manufactured by many (Arbor, Cisco, Huawei have software solutions, Wanguard software implementations, etc.), many backbone operators have already installed it and sell DDoS protection services (I know about installations at Rostelecom, Megafon, TTK, MTS , in fact, for all large providers, the hosters do the same with their a-la protection OVH.com, Hetzner.de, faced the protection in ihor.ru itself). Some companies are developing their software solutions (technologies like DPDK allow you to handle tens of gigabits of traffic on one physical x86 machine).
Of the well-known players, L3 / L4 DDoS is more or less effective in repelling everyone. I’m not going to say who has the maximum channel capacity (this is insider information), but usually it’s not so important, and the only difference is how quickly the protection works (instantly or after a few minutes of the project’s downtime, like in Hetzner).
The question is how qualitatively this is done: an attack with amplification can be repelled by blocking traffic from countries with the most harmful traffic, or you can discard only really unnecessary traffic.
But at the same time, based on my experience, all serious players in the Russian market can cope with this without problems: Qrator, DDoS-Guard, Kaspersky, G-Core Labs (formerly SkyParkCDN), ServicePipe, Stormwall, Voxility, etc.
Companies in Russia rarely work with foreign security operators, with the exception of Cloudflare. I’ll write about Cloudflare separately.
I didn’t encounter protection from operators like Rostelecom, Megafon, TTK, Beeline, according to colleagues, they provide these services quite qualitatively, but for now, lack of experience periodically affects: sometimes you need to tighten something through the support of the protection operator.
Some operators have a separate service “protection against attacks at the L3 / L4 level”, or “protection of channels”, it costs much cheaper than protection at all levels.
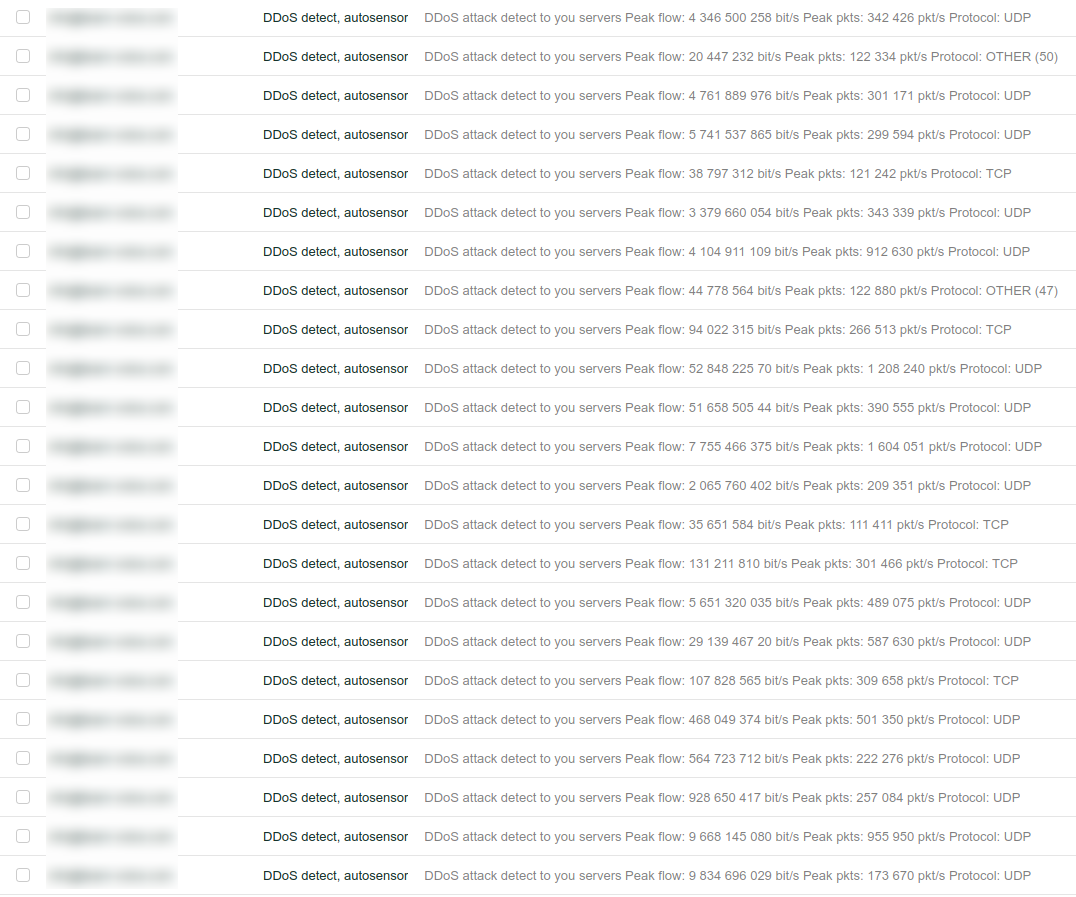
These are the reports from the superior L3 / L4 protection that I regularly received, supporting the hosting provider system.
Attacks at the L7 level (application level) are able to beat units steadily and efficiently.
I have a real big enough experience with
They charge for every megabit of net traffic, a megabit costs about several thousand rubles. If you have at least 100 Mbps of pure traffic - oh. Protection will be very expensive. I can tell in the following articles how to design applications in order to save very well on the capacity of protection channels.
The real "king of the hill" is Qrator.net, the rest are somewhat behind them. Qrator is the only ones in my practice who give a close to zero percentage of false positives, but at the same time they are several times more expensive than other market players.
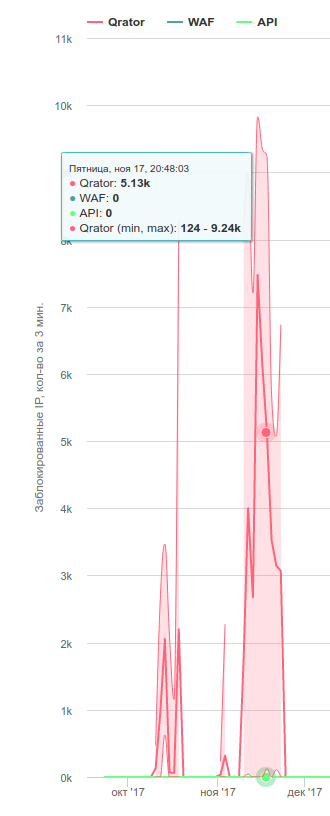
Other operators have high-quality and stable protection. Many of the services we support (including very famous in the country!) Are protected by DDoS-Guard, G-Core Labs, and are quite happy with the result, I can recommend them. Attacks repelled by Qrator
There is still experience with small protection operators such as cloud-shield.ru, ddosa.net, etc. I definitely can’t recommend it, because the experience is not very large, I will talk about the principles of their work. The cost of protection is often 1-2 orders of magnitude lower than that of large players. As a rule, they buy a partial defense service (L3 / L4) from one of the larger players + make their own defense against attacks at higher levels. It can be quite effective + you can get good service for less money, but these are still small companies with a small staff, please consider.
CloudFlare is a separate phenomenon. This is already a huge company that costs several billion dollars, their customers are half the traffic generators in the world, and the DDoS protection service is simply the most famous among their services. We also constantly use them for DNS hosting, CDN, as a traffic proxy service.
For a site / service that does not have complex attacks, Cloudflare is quite ok, but with serious attacks (when they’re not just “filling up” the channel, but combining many types of attacks), their Business plan for $ 200 never saved us, but talking about them Enterprise protection for Russia makes no sense, it’s cheaper and more effective to turn to other players.
Why is that? I think it’s difficult to make a massive almost free service very high quality.
By the way, a lot of Russian-speaking engineers work in CF :)
I once had real experience with Dragonara.net (once the largest security operator in the world), which no longer exists now.
There are already a lot of articles on Habré about modern operators, I’ll just give a link to a recent review: habr.com/en/post/350384
Surely many of them are very good if the project is not aimed at the Russian market, but in Russia there are problems with them.
The first - effective protection should be as close as possible to the defender and should take into account local features (in Russia alone, in China the second, in South America the third).
The second reason: a truly difficult and expensive task is protection at the L7 level. And yes, it is expensive for everyone, in principle, not many companies in the world make good L7 protection, and Russian services often simply win the competition.
All applications are unique, and you need to allow traffic that is useful to them and block harmful traffic. It’s not always possible to weed out bots unequivocally, so you have to use a lot of really MANY degrees of traffic purification.
Once the nginx-testcookie module was enough , and now it is enough to repel a large number of attacks. When I worked in the hosting industry, my L7 protection was built just on nginx-testcookie. By the way, Beget.ru, Netangels.ru, FastVPS.ru had a similar system.
Alas, attacks have become more difficult. testcookie uses checks for bots based on JS, and many modern bots can successfully pass them.
Attacking botnets are also unique, and you need to consider the features of each large botnet.
Amplification, direct flood from the botnet, filtering traffic from different countries (different filtering for different countries), SYN / ACK flood, packet fragmentation, ICMP, http flood, while at the application / http level you can come up with an unlimited number of different attacks.
In total, at the level of protection of channels, specialized equipment for cleaning traffic, special software, additional filtering settings for each client, there can be tens and hundreds of filtering levels.
To properly manage this and correctly tune the filtering settings for different users, you need a lot of experience and qualified personnel. Even a major operator who has decided to provide protection services cannot “stupidly throw a problem at the money”: experience will have to be gained on lying sites and false positives on legitimate traffic.
For the protection operator, there is no “hit DDoS" button, there are a large number of tools, you need to be able to use them.
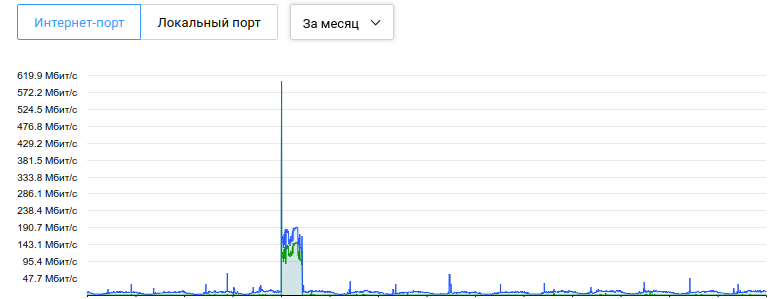
And one more bonus example. The server without protection was blocked by the hoster during an attack with a capacity of 600 Mbps (traffic loss was not noticeable, since only 1 site was attacked, it was removed from the server for a while and the lock was released within an hour). The same server is protected. The attackers “surrendered” after a day of repulsed attacks. The attack itself was not the strongest. L3 / L4 attacks and protection against them are more trivial, mainly they depend on the channel thickness, algorithms for detecting and filtering attacks.

L7 attacks are more complex and original, they depend on the attacked application, the capabilities and imagination of the attackers. Protection from them requires great knowledge and experience, and the result may not be immediately and not one hundred percent. Until Google came up with another neural network for protection.
Attacks on the Internet have also developed quite well during this time :)
But the DDoS protection market and the anti-attack technology used by operators are still quite closed.
I’ll tell you what I learned about him, supporting websites and Internet services that have been under constant attack for the past few years. Regular attacks. 350k req total, 52k req legitimate The first attacks appeared almost simultaneously with the Internet. DDoS as a phenomenon has become widespread since the late 2000s ( see www.cloudflare.com/learning/ddos/famous-ddos-attacks

)
From about 2015-2016, almost all hosting providers came under protection from DDoS attacks, like most prominent sites in competitive areas (do whois on the IP sites eldorado.ru, leroymerlin.ru, tilda.ws, see the network of protection operators).
If 10-20 years ago most of the attacks could be repelled on the server itself (evaluate the recommendations of the Lenta.ru system administrator Maxim Moshkov from the 90s ), now everything is more complicated.
First, briefly about the types of attacks.
Types of DDoS attacks in terms of choosing a protection operator
L3 / L4 attacks (OSI model)
- UDP flood from the botnet (many requests are sent directly from infected devices to the attacked service, the channel is blocked by servers);
- DNS / NTP / etc amplification (many requests for vulnerable DNS / NTP / etc are sent from infected devices, the sender’s address is spoofed, a cloud of packets responding to requests floods the channel of the attacker; this is how the most massive attacks on the modern Internet are performed);
- SYN / ACK flood (many connection requests are sent to the attacked servers, the connection queue overflows);
- attacks with packet fragmentation, ping of death, ping flood (google plz);
- etc.
These attacks aim to “fill up” the channel with the server or “kill” its ability to receive new traffic.
Although SYN / ACK flood and amplification are very different, many companies deal with them equally well. Problems arise with attacks from the following group.
Attacks on L7 (application level)
- http flood (if a website or some http api is being attacked);
- attack on vulnerable parts of the site (without a cache, very heavy load on the site, etc.).
The goal is to make the server “work hard”, process a lot of “as if real requests” and be left without resources for real requests.
Although there are other attacks, these are the most common.
Serious attacks at the L7 level are created in a unique way for each attacked project.
Why 2 groups?
Because there are many who know how to beat off attacks at the L3 / L4 level well, but either do not take up protection at the application level (L7) at all, or so far deal with them weaker than the alternatives.
Who is who in the market for DDoS protection
(my personal look)
L3 / L4 protection
To fight off attacks with amplification (“blocking” the server’s channel), there are enough wide channels (many of the protection services connect to most major backbone providers in Russia and have channels with a theoretical capacity of more than 1 Tbit). Do not forget that very rare attacks with amplification last longer than an hour. If you are Spamhaus and everyone does not like you - yes, you can try to put down channels for several days, even at the risk of further survival of the used world botnet. If you just have an online store, even if it is mvideo.ru - 1 Tbit for several days, you will see very soon (I hope).
In order to repel attacks with SYN / ACK flood, packet fragmentation, there is a need for equipment or software systems to detect and block such attacks.
Such equipment is manufactured by many (Arbor, Cisco, Huawei have software solutions, Wanguard software implementations, etc.), many backbone operators have already installed it and sell DDoS protection services (I know about installations at Rostelecom, Megafon, TTK, MTS , in fact, for all large providers, the hosters do the same with their a-la protection OVH.com, Hetzner.de, faced the protection in ihor.ru itself). Some companies are developing their software solutions (technologies like DPDK allow you to handle tens of gigabits of traffic on one physical x86 machine).
Of the well-known players, L3 / L4 DDoS is more or less effective in repelling everyone. I’m not going to say who has the maximum channel capacity (this is insider information), but usually it’s not so important, and the only difference is how quickly the protection works (instantly or after a few minutes of the project’s downtime, like in Hetzner).
The question is how qualitatively this is done: an attack with amplification can be repelled by blocking traffic from countries with the most harmful traffic, or you can discard only really unnecessary traffic.
But at the same time, based on my experience, all serious players in the Russian market can cope with this without problems: Qrator, DDoS-Guard, Kaspersky, G-Core Labs (formerly SkyParkCDN), ServicePipe, Stormwall, Voxility, etc.
Companies in Russia rarely work with foreign security operators, with the exception of Cloudflare. I’ll write about Cloudflare separately.
I didn’t encounter protection from operators like Rostelecom, Megafon, TTK, Beeline, according to colleagues, they provide these services quite qualitatively, but for now, lack of experience periodically affects: sometimes you need to tighten something through the support of the protection operator.
Some operators have a separate service “protection against attacks at the L3 / L4 level”, or “protection of channels”, it costs much cheaper than protection at all levels.
And if not the backbone provider repels attacks of hundreds of Gbps, it does not have its own channels?
The protection operator can connect to any of the major providers and repel attacks "at its expense." You will have to pay for the channel, but all these hundreds of Gbps will not always be utilized, there are options for a significant reduction in the cost of channels in this case, so the scheme remains operational.

These are the reports from the superior L3 / L4 protection that I regularly received, supporting the hosting provider system.
L7 protection (application level)
Attacks at the L7 level (application level) are able to beat units steadily and efficiently.
I have a real big enough experience with
- Qrator.net;
- DDoS-Guard;
- G-Core Labs;
- Kaspersky
They charge for every megabit of net traffic, a megabit costs about several thousand rubles. If you have at least 100 Mbps of pure traffic - oh. Protection will be very expensive. I can tell in the following articles how to design applications in order to save very well on the capacity of protection channels.
The real "king of the hill" is Qrator.net, the rest are somewhat behind them. Qrator is the only ones in my practice who give a close to zero percentage of false positives, but at the same time they are several times more expensive than other market players.
Other operators have high-quality and stable protection. Many of the services we support (including very famous in the country!) Are protected by DDoS-Guard, G-Core Labs, and are quite happy with the result, I can recommend them. Attacks repelled by Qrator

There is still experience with small protection operators such as cloud-shield.ru, ddosa.net, etc. I definitely can’t recommend it, because the experience is not very large, I will talk about the principles of their work. The cost of protection is often 1-2 orders of magnitude lower than that of large players. As a rule, they buy a partial defense service (L3 / L4) from one of the larger players + make their own defense against attacks at higher levels. It can be quite effective + you can get good service for less money, but these are still small companies with a small staff, please consider.
Cloudflare
CloudFlare is a separate phenomenon. This is already a huge company that costs several billion dollars, their customers are half the traffic generators in the world, and the DDoS protection service is simply the most famous among their services. We also constantly use them for DNS hosting, CDN, as a traffic proxy service.
For a site / service that does not have complex attacks, Cloudflare is quite ok, but with serious attacks (when they’re not just “filling up” the channel, but combining many types of attacks), their Business plan for $ 200 never saved us, but talking about them Enterprise protection for Russia makes no sense, it’s cheaper and more effective to turn to other players.
Why is that? I think it’s difficult to make a massive almost free service very high quality.
By the way, a lot of Russian-speaking engineers work in CF :)
Foreign security operators
I once had real experience with Dragonara.net (once the largest security operator in the world), which no longer exists now.
There are already a lot of articles on Habré about modern operators, I’ll just give a link to a recent review: habr.com/en/post/350384
Surely many of them are very good if the project is not aimed at the Russian market, but in Russia there are problems with them.
The first - effective protection should be as close as possible to the defender and should take into account local features (in Russia alone, in China the second, in South America the third).
The second reason: a truly difficult and expensive task is protection at the L7 level. And yes, it is expensive for everyone, in principle, not many companies in the world make good L7 protection, and Russian services often simply win the competition.
What is the difficulty of repelling attacks at the L7 level?
All applications are unique, and you need to allow traffic that is useful to them and block harmful traffic. It’s not always possible to weed out bots unequivocally, so you have to use a lot of really MANY degrees of traffic purification.
Once the nginx-testcookie module was enough , and now it is enough to repel a large number of attacks. When I worked in the hosting industry, my L7 protection was built just on nginx-testcookie. By the way, Beget.ru, Netangels.ru, FastVPS.ru had a similar system.
Alas, attacks have become more difficult. testcookie uses checks for bots based on JS, and many modern bots can successfully pass them.
Attacking botnets are also unique, and you need to consider the features of each large botnet.
Amplification, direct flood from the botnet, filtering traffic from different countries (different filtering for different countries), SYN / ACK flood, packet fragmentation, ICMP, http flood, while at the application / http level you can come up with an unlimited number of different attacks.
In total, at the level of protection of channels, specialized equipment for cleaning traffic, special software, additional filtering settings for each client, there can be tens and hundreds of filtering levels.
To properly manage this and correctly tune the filtering settings for different users, you need a lot of experience and qualified personnel. Even a major operator who has decided to provide protection services cannot “stupidly throw a problem at the money”: experience will have to be gained on lying sites and false positives on legitimate traffic.
For the protection operator, there is no “hit DDoS" button, there are a large number of tools, you need to be able to use them.
And one more bonus example. The server without protection was blocked by the hoster during an attack with a capacity of 600 Mbps (traffic loss was not noticeable, since only 1 site was attacked, it was removed from the server for a while and the lock was released within an hour). The same server is protected. The attackers “surrendered” after a day of repulsed attacks. The attack itself was not the strongest. L3 / L4 attacks and protection against them are more trivial, mainly they depend on the channel thickness, algorithms for detecting and filtering attacks.


L7 attacks are more complex and original, they depend on the attacked application, the capabilities and imagination of the attackers. Protection from them requires great knowledge and experience, and the result may not be immediately and not one hundred percent. Until Google came up with another neural network for protection.
