Asymmetric encryption in practice
I greet you, habravchane!
Security concerns are a weak spot for most of us. It is unpleasant for all of us to collide, much less lose something valuable due to an accidental mouse click. And that is why I decided to share the materials I found with you.
In an effort to dispel the most frequently asked question - why will they attack me? Who do I need? - we will start the article with him.
Keep in mind that not only a person can attack you. This can be done, for example, by a bot.
Each of us is connected to the Internet provider. And on him, most likely, attacks occur literally every day. Have you noticed the spam section in your mail? Each such email potentially has a phishing attack. This attack is not personal to you. This is a large-scale attack targeted at a wide range of faces. We are the potential victims.
More often than not, their goal is money. How can they get them?
For example, use your computer as a web server, steal your content, perform email attacks, botnet activity, account theft, and extortion attacks. Yes, and an email account is a potentially important thing, because we all often use the same password on several services.
Time is expensive and we want to spend as little time as possible on security related issues.
And so the first thing to do is to answer a few questions for yourself:
Well, for example, laptop theft. Yes, it hurts and is sad. But how can this threaten you?
This may be the loss of data to enter the social network. This may be confidential information obtained during work. Or maybe it's personal photos.
Okay, we decided what we need to protect. The next step is to choose a protection method.
Yes, of course, there are many attacks in the world and it is simply impossible to defend oneself from everyone.
Therefore, we will consider one of the most effective tools - encryption.
To make the right choice in the field of security, you need to understand what encryption is. It is not necessary to know hardcore math. Enough to understand at a basic level. This is one of the best and indispensable tools in our arsenal.
Encryption is a method of converting data that is readable by a person into a form that a person cannot read. Due to this, the data remains confidential and private.
Decryption is the reverse operation. Convert unreadable data to readable.
OK, where does this apply? Actually in many places. For example, did you pay attention to the https protocol? It is due to him that your 3rd person cannot intercept your data during your climb on the Internet. I will explain in more detail. You go to www.google.com", Make any request. At the same time, all the data that is necessary for displaying the results is transmitted using the https protocol. So, if any person decides to look at the data about your traffic (Man In the Middle attack), then he will only see that you are logged in to Google. In addition, he will receive many encrypted packets. That is, we can say that he will not receive anything.
But back to the basic theory. The encryption process involves 2 main components - the algorithm and the key.
An algorithm is, in a sense, a lock that allows you to keep your data secret. Due to it, the text is converted.
The key is, sorry for the tautology, the key to the lock. A piece of unique data that converts text
Hm, alright. We are going further. Slightly increase the voltage.
How else can we use encryption for our own selfish purposes? For ease of understanding, we will consider archive encryption. When archiving, many archivers have the ability to set a password. In this case, the archiver uses some kind of algorithm for encryption. And most often it is a symmetric algorithm.
Symmetric encryption algorithm - an algorithm in which the same key is used for encryption and decryption. A striking and, at the same time simple example, will be Caesar's code.
The whole work of this algorithm is to change the character to another with a certain step.
For example, with an offset of 5 characters, the character that stands in the first position is replaced by a character in the 6th position and so on.
The most robust at the moment is considered the AES (Advanced Encryption Standard) algorithm.
Another point worth mentioning is the power of the password. Password strength is measured in bits. One of the most common solutions is 128 or 256 bits. This is the number of bits that will be allocated for the password. This number also means the number of passwords that you can get with this encryption algorithm. But the longer the key length, the slower the process of encryption or decryption.
And so, we encrypted the letter, but how to send it to our friend? Send to social networks or text messaging is not a good idea. Like talking to him on the phone.
And this leads us to a new type of encryption.
In asymmetric encryption, 2 keys are used - public and private (secret).
Public key for encryption, private key for decryption.
What algorithms allow using this technology?
Here is a list:
Advantages of asymmetric algorithms:
Minuses:
3) Now the most time-consuming part is the choice of the exponent and an arbitrary coefficient.
The fact is that with the selected coefficients the value of "d" must be integer. “D” is a necessary component of the algorithm
e = 5
k = 9
d = (k * f + 1) / e
Now our public key (for encrypting the message) consists of the values of the variables “e” and “n”, and the private key (for decryption) from the values of "d" and "n".
That is, in our case ...
Then the message is encrypted using the formula: crypt = m ^ e% n.
And decryption: decrypt = crypt ^ d% n.
Well, from the point of view of the programmer, we can use this information as follows:
How can asymmetric encryption be used for my purposes?
Now, knowing the theory, the pros and cons of the algorithm, and also why you need to use it at all, we can talk about practical application.
Among all the programs found, gpg4usb seemed the most convenient to me.
This program uses PGP encryption. Why do I recommend using it?
Everything is simple. This type of encryption has not yet been cracked. To nobody. So use it.
Using the program is quite simple. You just need to know where to click.
And that is exactly what will be discussed now.
The first thing to do is download the program. You can do this at the link:
link .
I will say right away - this program is cross-platform. That is, you can use it on both Windows and Linux.
The second is to create an encryption key pair.
This can be done by following these steps:
1) Go to the “Key Manager” section
2) Select “Key” in the top panel, then “Generate key”
It should look something like this:
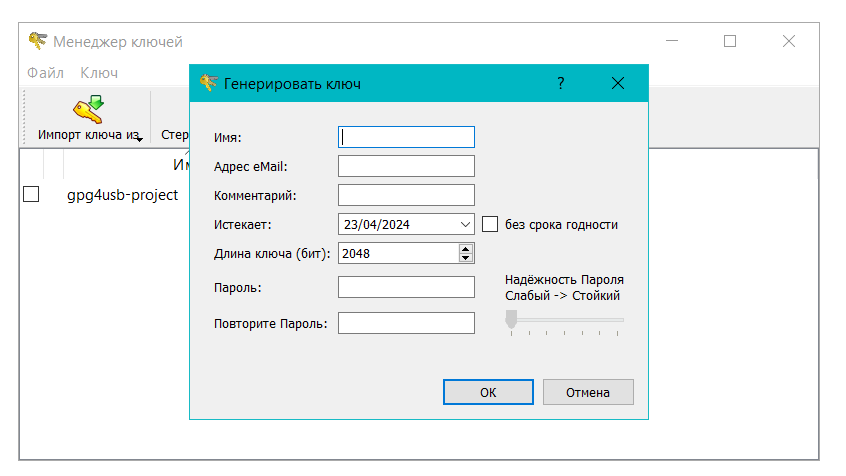
3) Fill in the required fields. I’ll warn you right away - it’s better to write down the password (or remember) somewhere, because it will be needed later to decrypt the message.
Now the key is created, and we can proceed directly to the encryption.
There is a text field on the main screen - this is our springboard for creating messages. In the right sidebar, tick off your key.

Having entered the message in the field, boldly click "Encrypt" in the upper panel.
Congratulations, you can encrypt messages.
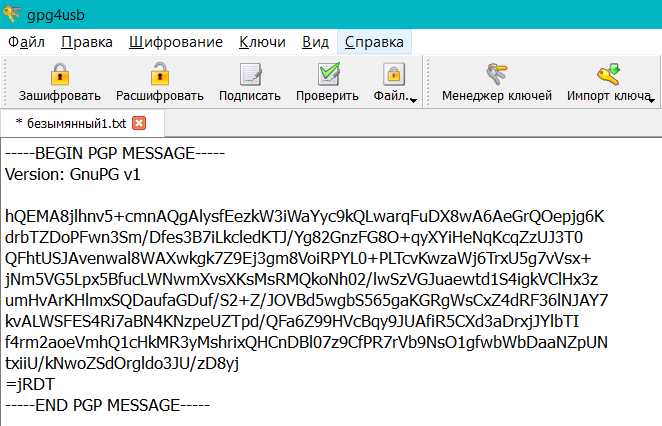
Decryption takes place in the same way, except that instead of “Encrypt” you use the button “Decrypt”.
And now the moment that the brain took me for half an hour: how to pass the key to a friend?
Yes, we set up an encryption system, and it works, yes, we can give a friend a public key and not be afraid that the message will be read. But where to get it?
As it turned out, everything is quite simple. In the window in which we created the keys for encryption, we tick off the desired key and select "Export to file" in the upper panel. We got the public key and can pass it on to anyone to receive encrypted messages from it that only we can read.
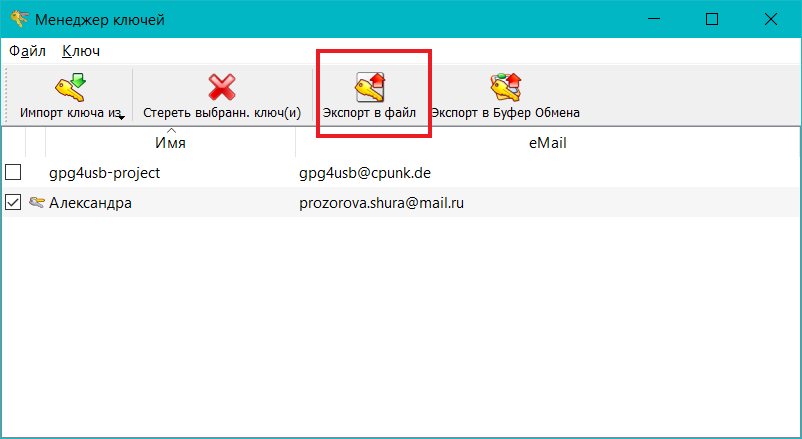
So, now I want to get the private key (what if I’m working from another computer? After all, the keys are stored locally).
To solve this problem, we again return to the main screen, in the right side panel, right-click on the desired key and select "Show key properties". And in the window that opens, select "Export Private Key".
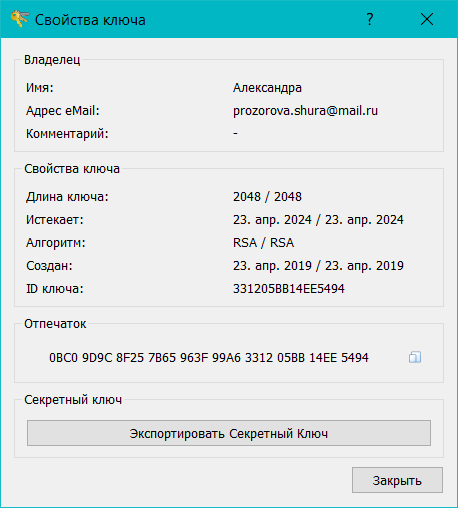
Done, now you have “public” public and private encryption keys, which you can use at your discretion.
Well, at the end of the article I want to share a useful technique: threat modeling and risk assessment.
The first thing to understand is that you cannot ensure 100% security, nor can you reduce all risks to zero. You cannot get 100% anonymity. You cannot get 100% security (unless you use a phone and a PC).
Using the Internet, we somehow accept the risks. It gives us a chance to expand our capabilities, but there is a risk of losing our data. Therefore, security is a balancing act between convenience, expansion of knowledge, comfort and preservation of already defined, important data for us.
We must use a risk-based approach.
For example, laptop theft. What we can do? Encrypt the entire disk, add additional authorization steps.
To ensure quality protection, you need to go through several stages:
Security concerns are a weak spot for most of us. It is unpleasant for all of us to collide, much less lose something valuable due to an accidental mouse click. And that is why I decided to share the materials I found with you.
In an effort to dispel the most frequently asked question - why will they attack me? Who do I need? - we will start the article with him.
Keep in mind that not only a person can attack you. This can be done, for example, by a bot.
Each of us is connected to the Internet provider. And on him, most likely, attacks occur literally every day. Have you noticed the spam section in your mail? Each such email potentially has a phishing attack. This attack is not personal to you. This is a large-scale attack targeted at a wide range of faces. We are the potential victims.
More often than not, their goal is money. How can they get them?
For example, use your computer as a web server, steal your content, perform email attacks, botnet activity, account theft, and extortion attacks. Yes, and an email account is a potentially important thing, because we all often use the same password on several services.
Time is expensive and we want to spend as little time as possible on security related issues.
And so the first thing to do is to answer a few questions for yourself:
- Which files store the most important data?
- What accounts in social networks can you not lose?
- What could be most harmful?
- And what could hit your reputation?
Well, for example, laptop theft. Yes, it hurts and is sad. But how can this threaten you?
This may be the loss of data to enter the social network. This may be confidential information obtained during work. Or maybe it's personal photos.
Okay, we decided what we need to protect. The next step is to choose a protection method.
Yes, of course, there are many attacks in the world and it is simply impossible to defend oneself from everyone.
Therefore, we will consider one of the most effective tools - encryption.
What is encryption?
To make the right choice in the field of security, you need to understand what encryption is. It is not necessary to know hardcore math. Enough to understand at a basic level. This is one of the best and indispensable tools in our arsenal.
Encryption is a method of converting data that is readable by a person into a form that a person cannot read. Due to this, the data remains confidential and private.
Decryption is the reverse operation. Convert unreadable data to readable.
OK, where does this apply? Actually in many places. For example, did you pay attention to the https protocol? It is due to him that your 3rd person cannot intercept your data during your climb on the Internet. I will explain in more detail. You go to www.google.com", Make any request. At the same time, all the data that is necessary for displaying the results is transmitted using the https protocol. So, if any person decides to look at the data about your traffic (Man In the Middle attack), then he will only see that you are logged in to Google. In addition, he will receive many encrypted packets. That is, we can say that he will not receive anything.
But back to the basic theory. The encryption process involves 2 main components - the algorithm and the key.
An algorithm is, in a sense, a lock that allows you to keep your data secret. Due to it, the text is converted.
The key is, sorry for the tautology, the key to the lock. A piece of unique data that converts text
Hm, alright. We are going further. Slightly increase the voltage.
Types of Encryption
How else can we use encryption for our own selfish purposes? For ease of understanding, we will consider archive encryption. When archiving, many archivers have the ability to set a password. In this case, the archiver uses some kind of algorithm for encryption. And most often it is a symmetric algorithm.
Symmetric encryption
Symmetric encryption algorithm - an algorithm in which the same key is used for encryption and decryption. A striking and, at the same time simple example, will be Caesar's code.
The whole work of this algorithm is to change the character to another with a certain step.
For example, with an offset of 5 characters, the character that stands in the first position is replaced by a character in the 6th position and so on.
The most robust at the moment is considered the AES (Advanced Encryption Standard) algorithm.
Another point worth mentioning is the power of the password. Password strength is measured in bits. One of the most common solutions is 128 or 256 bits. This is the number of bits that will be allocated for the password. This number also means the number of passwords that you can get with this encryption algorithm. But the longer the key length, the slower the process of encryption or decryption.
But asymmetric encryption is most commonly used.
And so, we encrypted the letter, but how to send it to our friend? Send to social networks or text messaging is not a good idea. Like talking to him on the phone.
And this leads us to a new type of encryption.
In asymmetric encryption, 2 keys are used - public and private (secret).
Public key for encryption, private key for decryption.
What algorithms allow using this technology?
Here is a list:
- Rivest — Shamir — Adleman (RSA) (most common)
- Elliptic curve cryptosystem (ECC)
- Diffie — Hellman (DH)
- El gamal
Advantages of asymmetric algorithms:
- You can freely share the public key and anyone can send you a secret message.
Minuses:
- encryption / decryption speed.
For advanced
Since I have a programmer’s core in me, as well as a love of mathematics, I just can’t help but talk about how everything works “under the hood”
Let's look at the example of the RSA algorithm.
The first thing we need to do is generate the public and private keys. The sequence of actions is approximately the following:
1) We choose two primes. It is desirable that they be close enough
p = 19
s = 13
2) We calculate their product, as well as the Euler function
n = p * s
f = (p - 1) * (s - 1)
Let's look at the example of the RSA algorithm.
The first thing we need to do is generate the public and private keys. The sequence of actions is approximately the following:
1) We choose two primes. It is desirable that they be close enough
p = 19
s = 13
2) We calculate their product, as well as the Euler function
n = p * s
f = (p - 1) * (s - 1)
3) Now the most time-consuming part is the choice of the exponent and an arbitrary coefficient.
The fact is that with the selected coefficients the value of "d" must be integer. “D” is a necessary component of the algorithm
e = 5
k = 9
d = (k * f + 1) / e
Now our public key (for encrypting the message) consists of the values of the variables “e” and “n”, and the private key (for decryption) from the values of "d" and "n".
That is, in our case ...
Then the message is encrypted using the formula: crypt = m ^ e% n.
And decryption: decrypt = crypt ^ d% n.
Well, from the point of view of the programmer, we can use this information as follows:
- Create an array of matches to the character and its code (for example, ASCII code)
- Apply an algorithm for each character, creating an array of converted values
- Convert the resulting array back to string form
- Profit!
How can asymmetric encryption be used for my purposes?
Now, knowing the theory, the pros and cons of the algorithm, and also why you need to use it at all, we can talk about practical application.
Among all the programs found, gpg4usb seemed the most convenient to me.
This program uses PGP encryption. Why do I recommend using it?
Everything is simple. This type of encryption has not yet been cracked. To nobody. So use it.
Using the program is quite simple. You just need to know where to click.
And that is exactly what will be discussed now.
The first thing to do is download the program. You can do this at the link:
link .
I will say right away - this program is cross-platform. That is, you can use it on both Windows and Linux.
The second is to create an encryption key pair.
This can be done by following these steps:
1) Go to the “Key Manager” section
2) Select “Key” in the top panel, then “Generate key”
It should look something like this:

3) Fill in the required fields. I’ll warn you right away - it’s better to write down the password (or remember) somewhere, because it will be needed later to decrypt the message.
Now the key is created, and we can proceed directly to the encryption.
There is a text field on the main screen - this is our springboard for creating messages. In the right sidebar, tick off your key.

Having entered the message in the field, boldly click "Encrypt" in the upper panel.
Congratulations, you can encrypt messages.

Decryption takes place in the same way, except that instead of “Encrypt” you use the button “Decrypt”.
And now the moment that the brain took me for half an hour: how to pass the key to a friend?
Yes, we set up an encryption system, and it works, yes, we can give a friend a public key and not be afraid that the message will be read. But where to get it?
As it turned out, everything is quite simple. In the window in which we created the keys for encryption, we tick off the desired key and select "Export to file" in the upper panel. We got the public key and can pass it on to anyone to receive encrypted messages from it that only we can read.

So, now I want to get the private key (what if I’m working from another computer? After all, the keys are stored locally).
To solve this problem, we again return to the main screen, in the right side panel, right-click on the desired key and select "Show key properties". And in the window that opens, select "Export Private Key".

Done, now you have “public” public and private encryption keys, which you can use at your discretion.
Well, at the end of the article I want to share a useful technique: threat modeling and risk assessment.
The first thing to understand is that you cannot ensure 100% security, nor can you reduce all risks to zero. You cannot get 100% anonymity. You cannot get 100% security (unless you use a phone and a PC).
Using the Internet, we somehow accept the risks. It gives us a chance to expand our capabilities, but there is a risk of losing our data. Therefore, security is a balancing act between convenience, expansion of knowledge, comfort and preservation of already defined, important data for us.
We must use a risk-based approach.
Risk = Vulnerability * Threats * Consequences
For example, laptop theft. What we can do? Encrypt the entire disk, add additional authorization steps.
To ensure quality protection, you need to go through several stages:
- Choose
- Customize
- Estimate. Check that the drive is fully encrypted
- We control. Check for Security Updates
