ADB vs Spy Cam & Mic
How to check if any application on Android- smartphone leads photo or video reportage, although it never comes to anything? The following option is not perfect, but does not require a "root" or custom firmware.
PS I added a description of the application access monitoring to the microphone to the article.
What you need to install:
We turn on the debugging mode via USB on the phone and connect the smartphone to the USB port of the computer, and select the USB connection mode other than “Charging Only”.
Open the command line in the directory in which the "tools" are installed.
Check that the connection is successful (the serial number of the connected smartphone is displayed):
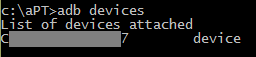
For Linux, the command would look like this:
If the computer is not authorized for use with this smartphone (for Android 4.2.2 and later), then the warning message " unauthorized " will appear next to the serial number .
For authorization, you must confirm the debugging permission via USB on your smartphone .
Run the shell on the device (we get the "$" prompt):
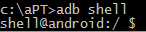
Then enter the following "magic" characters:
Improved version that removes the output "NAME" and empty lines:
And nothing happens :-) Until something decides to shoot a little :-) The
marked “magic” character set starts monitoring the access to the camera service at media.camera (the service is implemented by the library libcameraservice.so ) as quickly as possible . If the camera is not active, dumpsys gives something like this:
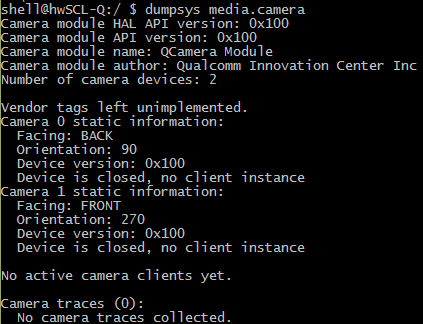
And if you need a camera, this appears:
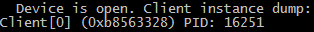
grep checks for the presence of a " PID " and, if there is this chain, then cut out the process number from the line and feed it to the ps command , which displays the data about this process, and another grepcuts out his name. After detecting the activity of the camera, we pause for a second so that the messages do not fall out too often. To interrupt the command, use the CTRL-C key combination , and to exit the shell - CTRL-D .
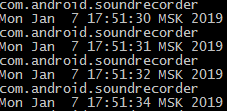
The simplest example is that after launching a regular smartphone photo / video application, messages with the process name and date / time begin to spill at 1 second intervals:
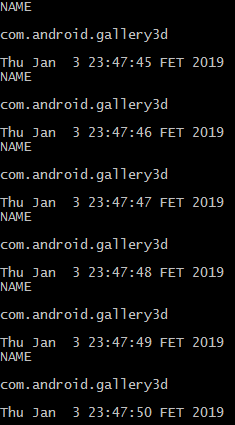 "
"
But there are more tricky applications, you can find them using the keyword" spy cam "(using the trick for example, with a single-pixel preview ( http://www.ez.ai/2014/05/exploring-limits-of-covert-data.html )). Such a creation collapses and reports when you start shooting, but the messages are regularly:
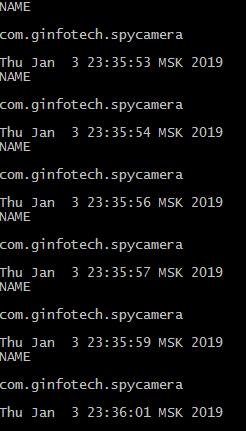
I also checked the performance of the proposed method on an application that takes a single shot when I press the floating button without any visible preview window.
without any visible preview window.
The script successfully caught the call to the camera and issued two messages with each shot:

But nothing prevents to implement similar functionality in the application with a more harmless name ( https://www.zdnet.com/article/this-scary-android-malware- can-record-audio-video-and-steal-your-data / ), and permissions - well, there are all sorts of cases. Yes, and the "legal" application can keep a report when it pleases (I met the mention of one such case). And for good reason in Android P took measures to prevent access to the camera background applications.
The method has been tested on Huawei SCL-L01 smartphones ( Android 5.1.1) and Huawei G700-U20 ( Android 4.2.1), on other smart phone models the output format of the dumpsys may differ (for media.camera service it is not standardized), which will require code correction .
Message Format tightly "sewn up" in the library /system/lib/libcameraservice.so - for example, a smartphone Huawei's the SCL-L01 :
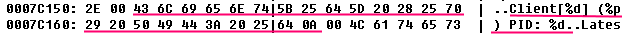
In the comments - a clue how to change the code to work with a smartphone under the All Android 9.
In this commentary is a log of calls to cell that leadsHTC U11 .
But, for example, on the “ancient” Huawei U8650 ( Android 2.3.4), dumpsys works fine:
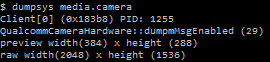
But you don’t have enough rights for ... grep :-)
Monitoring microphone access You
can use a similar method to monitor application access to a microphone. In this case, you need to monitor the media.audio_flinger service .
Enter the command in the shell (the code above works for the Huawei SCL-L01 smartphone ( Android 5.1.1)):
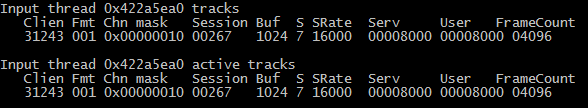
If an application records sound through a microphone, then there is a similar fragment in the output of dumpsys media.audio_flinger :

( Input thread is the input stream, 22467 is the PID of the audio recording process).
When recording audio through the standard Voice Recorder application and monitoring turned on (using the above code), the following messages appear:
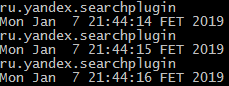
Here are the messages that are generated when Google’s voice input is activated for the translator:

On other smartphone models, the output format of the dumpsys may differ, which will require code correction.
For example, on the smartphone Huawei G700-U20 (Android 4.2.1):
In this case, the monitoring code will be:
Here is how Alice “revived” in this case:
PS I added a description of the application access monitoring to the microphone to the article.
What you need to install:
- ADB ( Android Debug Bridge ) (for example, as part of the Android SDK Platform Tools — you can download it here );
- driver for the phone (if necessary, for example, Google USB Driver can be downloaded here ).
We turn on the debugging mode via USB on the phone and connect the smartphone to the USB port of the computer, and select the USB connection mode other than “Charging Only”.
Hidden text
В «Диспетчере устройств» смартфон отображается, например, так:
в режиме «Фото» или «Файлы»
в режиме «USB-диск»

А вот так — в выводе команды lsusb:
в режиме «Фото» или «Файлы»
в режиме «USB-диск»

А вот так — в выводе команды lsusb:

Open the command line in the directory in which the "tools" are installed.
Check that the connection is successful (the serial number of the connected smartphone is displayed):
adb devices
For Linux, the command would look like this:
./adb devicesIf the computer is not authorized for use with this smartphone (for Android 4.2.2 and later), then the warning message " unauthorized " will appear next to the serial number .
For authorization, you must confirm the debugging permission via USB on your smartphone .
Hidden text
Под Linux может появляться сообщение "no permissions" — в моем случае удалось решить проблему переключением смартфона в режим «Медиаустройство (MTP)».
Run the shell on the device (we get the "$" prompt):
adb shell
Then enter the following "magic" characters:
whiletrue; do ps `while ! (dumpsys media.camera | grep -E "PID") dodone | grep -o "[^PID: ][0-9]*$"` | grep -o "[^S ]*$" ; date; sleep 1; doneImproved version that removes the output "NAME" and empty lines:
whiletrue; do ps `while ! (dumpsys media.camera | grep -E "PID") dodone | grep -o "[^PID: ][0-9]*$"` | grep -o "[^S ]*$" | grep -v "NAME" | grep .; date; sleep 1; doneAnd nothing happens :-) Until something decides to shoot a little :-) The
marked “magic” character set starts monitoring the access to the camera service at media.camera (the service is implemented by the library libcameraservice.so ) as quickly as possible . If the camera is not active, dumpsys gives something like this:

And if you need a camera, this appears:

grep checks for the presence of a " PID " and, if there is this chain, then cut out the process number from the line and feed it to the ps command , which displays the data about this process, and another grepcuts out his name. After detecting the activity of the camera, we pause for a second so that the messages do not fall out too often. To interrupt the command, use the CTRL-C key combination , and to exit the shell - CTRL-D .
The simplest example is that after launching a regular smartphone photo / video application, messages with the process name and date / time begin to spill at 1 second intervals:
 "
" But there are more tricky applications, you can find them using the keyword" spy cam "(using the trick for example, with a single-pixel preview ( http://www.ez.ai/2014/05/exploring-limits-of-covert-data.html )). Such a creation collapses and reports when you start shooting, but the messages are regularly:

I also checked the performance of the proposed method on an application that takes a single shot when I press the floating button
 without any visible preview window.
without any visible preview window. The script successfully caught the call to the camera and issued two messages with each shot:

But nothing prevents to implement similar functionality in the application with a more harmless name ( https://www.zdnet.com/article/this-scary-android-malware- can-record-audio-video-and-steal-your-data / ), and permissions - well, there are all sorts of cases. Yes, and the "legal" application can keep a report when it pleases (I met the mention of one such case). And for good reason in Android P took measures to prevent access to the camera background applications.
The method has been tested on Huawei SCL-L01 smartphones ( Android 5.1.1) and Huawei G700-U20 ( Android 4.2.1), on other smart phone models the output format of the dumpsys may differ (for media.camera service it is not standardized), which will require code correction .
Message Format tightly "sewn up" in the library /system/lib/libcameraservice.so - for example, a smartphone Huawei's the SCL-L01 :
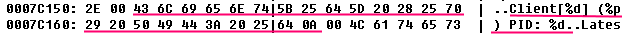
In the comments - a clue how to change the code to work with a smartphone under the All Android 9.
In this commentary is a log of calls to cell that leadsHTC U11 .
But, for example, on the “ancient” Huawei U8650 ( Android 2.3.4), dumpsys works fine:

But you don’t have enough rights for ... grep :-)

Monitoring microphone access You
can use a similar method to monitor application access to a microphone. In this case, you need to monitor the media.audio_flinger service .
Enter the command in the shell (the code above works for the Huawei SCL-L01 smartphone ( Android 5.1.1)):
whiletrue; do ps `while ! (dumpsys media.audio_flinger | grep -A20 Input| grep -A1 Client | grep yes | grep -o "[^yes ].*" | grep -o [0-9]*) dodone` | grep -o "[^S ]*$" | grep -v "NAME" | grep .; date; sleep 1; doneIf an application records sound through a microphone, then there is a similar fragment in the output of dumpsys media.audio_flinger :

( Input thread is the input stream, 22467 is the PID of the audio recording process).
When recording audio through the standard Voice Recorder application and monitoring turned on (using the above code), the following messages appear:

Here are the messages that are generated when Google’s voice input is activated for the translator:

On other smartphone models, the output format of the dumpsys may differ, which will require code correction.
For example, on the smartphone Huawei G700-U20 (Android 4.2.1):

In this case, the monitoring code will be:
whiletrue; do ps `while ! (dumpsys media.audio_flinger | grep -A3 Input| grep -A1 Clien | grep -o "[^ ].*" | grep -o [0-9]*) dodone` | grep -o "[^S ]*$" | grep -v "NAME" | grep .; date; sleep 1; doneHere is how Alice “revived” in this case:

