Critical Security Vulnerability on fl.ru
1. Prologue
Recently, colorful headlines about various revelations have begun to appear in the media: from publicly available photos of celebrities to open personal mailboxes of major figures. What can I say about everyday life in some ordinary company, when an employee uses the same password to access absolutely all resources.
But today we will talk about a less vivid event for the public, but at the same time much more resonant for those who, by the will of fate, worked and works on fl.ru.
2. Critical vulnerability in information security fl.ru
Go straight to the point. If you conduct private correspondence with the person you are talking to and think that no one except the two of you has access to this correspondence, then you will be right (at least the opposite has not yet been proved). But as soon as you attach a file with textual content to the correspondence, be sure that it will be included in the Yandex search engine index.
Maybe the above is not a bug at all, but a feature? Maybe I just don't understand much about open systems?
I decided to analyze the possible bottlenecks.
To do this, I used the “safe transaction”, and specifically - three documents that are generated as a result of the conclusion of this transaction:
- Agreement
- Contract
- Technical task
No one will argue with me if I say that all 3 documents are strictly confidential. Especially the “terms of reference”, since the document contains the personal information of the participants in the transaction, as well as the cost of the work.
Let's try to find out if Yandex can access the technical specifications of a safe transaction. We take the keywords from this document: " Appendix No. 1 to the OFFER ON THE CONCLUSION OF THE AGREEMENT " and add the operand localizing the search exclusively within the framework of the site fl.ru. As a result, the search query is obtained as follows: “Appendix No. 1 to the OFFER FOR CONCLUSION OF THE AGREEMENT site: fl.ru” . We start, watch, enjoy.
If you wish, you can write a crawler that downloads terms of referenceall safe transactions and calculates the total amount of transactions. I think this is just the beginning of using the identified “hole”.
3. Attempting to communicate with technical support
A separate point is worth noting my zealous attempts to convey the whole horror of the situation to technical support.
Below I attach a screenshot of our correspondence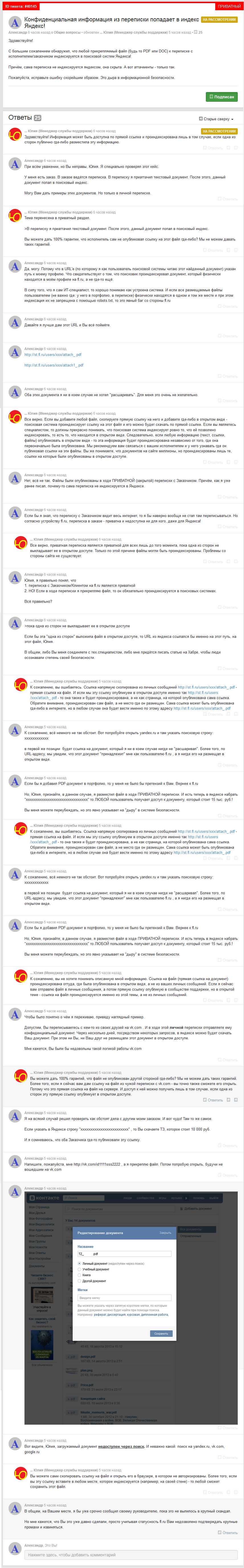

Not only was the support service employee too lazy to reproduce the error on his own, but he still persistently convinced me of what he himself, apparently, did not very willingly believe.
4. Epilogue
I hope this fact will serve as a good lesson for employees of all levels of fl.ru: starting from testers and technical support, ending with stakeholders. When your project takes on a large scale, then it's time to take care of information security.
In this whole story, I felt like the main character in the movie “The Fool”, which “was most needed” and which no one believed.
Good luck to all.
