Reconnect - Facebook Login Vulnerability

Everything is very simple - if we can log in to our Facebook, then we can connect our Facebook to the victim’s account on other websites. The victim downloads our page and we gain access to the victim’s account on Booking.com, Bit.ly, About.me, Stumbleupon, Angel.co, Mashable.com, Vimeo and a bunch of other websites.
Step 1. Downloading this URL www.facebook.com/n/?mid=9dd1fd7G5af48de9ca58G0G86G119bb48c logs out any FB user
Step 2. To log in a victim under our Facebook account requires Origin = *. Facebook.com when requesting login.php. Origin is transmitted by the browser itself and contains the domain of the page from where the request was made. In other words, we need to find a way to make a POST request from Facebook itself. This is not necessary for Firefox - it does not send Origin at all for regular form-based requests. Therefore, further hack specifically for Chrome.
Let's create a Canvas application with the following settings:
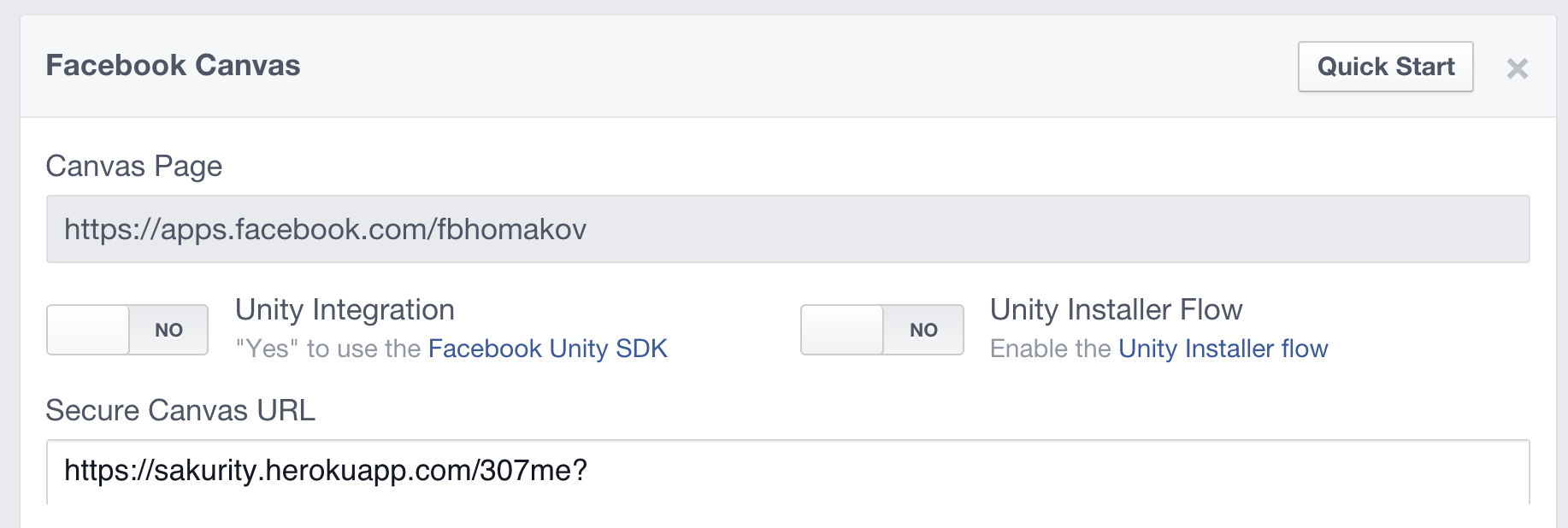
When the victim lands on apps.facebook.com/482922061740192, Facebook sends a POST request to this URL (it should not be on facebook.com). We, in turn, use a 307 redirect (saves HTTP verb as opposed to 302) and this leads to a POST request at www.facebook.com/login.php?email=attacker@email.com&pass=passwordtogether with Origin: apps.facebook.com and our username / password. Now the victim is logged into our Facebook account.
Step 3. It remains to start the connection process. Normal

Now that our facebook is connected to the victim’s account, we can directly log into the victim’s account, cancel reservations on booking.com or read private messages, or change the password.
This simple bug uses three CSRFs at the same time - on logout, login and on joining a social account. The first two should fix Facebook (but they refused, this is WontFix), the last is the task of the developer.
Reconnect is a tool for hijacking accounts , you can copy the code and break anyone - I do not mind. Examples include Booking.com, Bit.ly, About.me, Stumbleupon, Angel.co, Mashable.com, Vimeo, but any other Facebook Connect website may be vulnerable. For example, all Rails sites using omniauth-facebook are vulnerable.
