The evolution of Zeus. Part III
The previous part is here .
At the end of March 2012, Microsoft held a set of activities, codenamed Operation b71 , aimed at disabling some elements of the Zeus infrastructure, as well as SpyEye and Ice IX (a project based on Zeus source code). As a result, the work of the command servers on two hosting sites was stopped: in the cities of Scranton (Pennsylvania) and Lombard (Illinois). Also, two IP addresses and about 800 domains were removed from the control structure of the botnets.
This operation was sharply criticized.from the community of IT security professionals. In particular, Fox-IT specialists noted that Microsoft in its reporting documents not only disclosed information about suspects, including authors and individual users, but also persons completely unrelated to them. Moreover, all these data were the property of the IT security community and were not subject to disclosure in connection with the conduct of operational-search measures. In addition, some domain names belonged to legal, but hacked resources. Among other things, it was found that, despite the statement by Microsoft that there was simply a disconnection for the withdrawn domain names, this was not the case and the syncing process was in full swing, that is, during it not only the IP addresses of the victims were saved, but also recorded HTTP requests with all headers, which,
In addition, this operation had almost no effect on the Zeus Gameover botnet. That's how Microsoft works, a lot of PR plus the setup of its colleagues on the shop for the sake of a moment of fame. The materials feature Slavik and Gribodemon, whose personalities we will return to.
However, while unwinding the chain of ties of cybercriminals, experts also took Citadel and its developer AquaBox at gunpoint. He, clearly noting the close attention to his person, at the end of 2012 laid down and stopped the open sale of his product.
A decisive blow to Citadel infrastructure was struck in May-June 2013 during Operation b54conducted jointly by Microsoft and the FBI. The essence of the operation was to seize 4,000 domain names that were used by Citadel. In fact, 1,462 domain names were seized, for which they were redirected to the Microsoft server for the synchol. According to experts, the entire Trojan Citadel infected about 5 million computers, mainly in the USA, Europe, Hong Kong, Singapore, India and Australia.
But here Microsoft could not help but improve. As it turned out , about 1000 domain names belonged to other security companies and were used precisely for surveillance. The owner of the abuse.ch tracker Roman Hyussi drew attention to this circumstance, and at the same time about 300 domain names used for the sync were lost.
The ultimate goal of the control interception is to send out specially configured Microsoft configuration files for Citadel, in which the websites of anti-virus companies were blocked. This feature, redirection for sites from the black list, was distinctive for Citadel, it appeared in version 1.3.5.1 of the Rain Edition, in the original Zeus it was not. And here a natural ethical question arises, and what other teams could Microsoft potentially give through “their” config? In general, it is strange that Citadel developers did not implement a digital signature mechanism for the configuration file.
Meanwhile, Citadel developers continued closed sales. In June 2013, Trend Micro specialists discovered Citadel version 3.1.0.0, which had a distribution function via USB devices. And in July, the press appearedreports that the banking systems of Japan are attacked with just such a version. 9 command servers were identified, which were accessed from about 20 thousand unique IP addresses, while 96% of infected systems were in Japan.
While security guards struggled with numerous variations of Zeus version 2 (a small digression is the information on the x64 version of Zeus 2 with C&C on the TOR network from December 2013 here ), KINS - Kasper Internet Non Security appeared on the underground scene . According to Fox-IT, a private version of KINS, almost entirely based on Zeus source codes, has been used since December 2011 to attack banking systems in Germany and the Netherlands. And then some confusion begins. The fact is that close attention to KINS was drawn much later, in 2013.
As already mentioned here, in 2012-2013 there was a wave of operations against banking Trojans. In addition to Operation b71 and Operation b54, in 2012 there were mass arrests of members of cyber groups using Carberp, which ended in the arrest of Carberp developers in Ukraine in March 2013. So, one way or another, the underground since 2012 began to urgently need another tool with the appropriate support for bank robberies.
Apparently, the name KINS was subsequently used as a kind of brand, that is, in 2013 they released a relatively new product, which the security guards began to call according to the old one - KINS. However, it is more correct to call this version PowerZeus or ZeusVM.
Distinctive features of this version:
In addition, it is noticeable that the base for the dropper was PowerLoader 2 (hence the PowerZeus). In fact, it uses the source code of the Zeus and SpyEye grabbers as dlls as modules. French researcher Xylitol conducted his source-based KINS study and came to the conclusion that KINS = Zeus 2.0.8.9 + Power Loader 2.0 + SpyEye Plugins. Interestingly, in the course of his research, Xylitol went to the KINS developer; he got his Jabber from the hacked KINS test admin panel. A rather interesting dialogue took place with the developer.
During the dialogue it turned out that he was hired to develop KINS, but then “something went wrong.” All his achievements were stolen during the hack, and the KINS source code that was merged into the network is very raw alpha of the final product. One way or another, the development and closed sale of KINS is underway, and KINS and ZeusVM have become forks developed by different teams.
ZeusVM, in particular, was used during the attacks of Polish RB systems in the summer of 2013. A distinctive feature of the attack was that the config with web injects was not loaded from the Internet (although there was a link to the config URL), but was entirely contained within one of the sections of the PE file.
During the development of ZeusVM, features such as the use of steganography were additionally implemented.(November 2013), when the config, after processing xor, rc4 and base64, was embedded in a jpg image, as well as a change in the hook installation mechanism (May 2014), borrowed from Carberp. Many people hastened to announce the latest change as the next super cool hybrid of Zeus and Carberp called Zberp , but in reality this is another scarecrow.
The current state of affairs shows that, for the most part, cybercriminals have switched from using Citadel to ZeusVM.
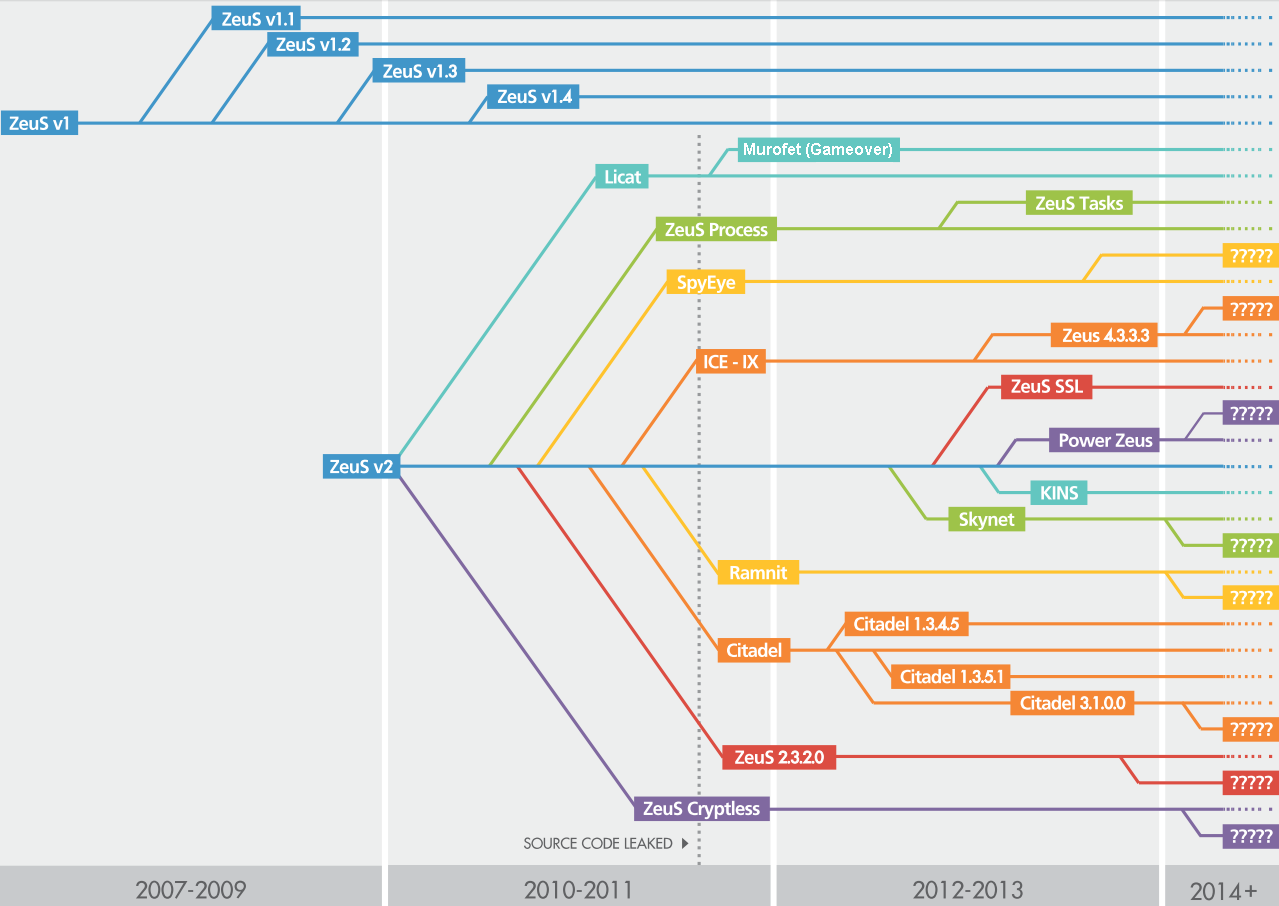
As you can see, several Zeus forks are developed in parallel by several teams of attackers. Let's go back to the “main” Zeus branch called GameOver (aka Murofet). In total, three versions can be distinguished:
Version 3 appeared after another operation called “Tovar”, carried out from April to June 2014 by the joint efforts of the FBI, Europol and a number of companies working in the field of information security, such as CrowdStrike, Dell SecureWorks, Symantec, Trend Micro and McAfee. During the investigation, it was found that Zeus GameOver was controlled by more than ten servers located on a bulletproof site of one of Odessa's hosting providers. Thus, the main control center was rendered harmless.
As a result of the disclosure of the hacker group Zeus GameOver, one of the alleged organizers was named - 30-year-old Russian resident Evgeny Bogachev, he was put on the FBI wanted list. He filed charges in absentiabased on intercepted conversations in one of the chats. In them, Bogachev, writing under the nicknames Lucky12345 and Slavik, recognizes the interlocutor that he is the creator of the Zeus Trojan.
By the way, in 2013, US authorities announced the arrest of Russian citizen Alexander Panin, who was detained on June 28 by Interpol officers and extradited from the Dominican Republic to the United States. On January 28, 2014, in a court in Atlanta, Panin admitted that he was one of the developers of SpyEye and his nickname is Gribodemon. Who knows, whether through Panin law enforcement agencies came to Bogachev?
According to Interpol, more than 1 million computers around the world were infected by Zeus GameOver, the total financial damage from the theft from remote banking systems is estimated at 75 million euros. In addition, through the Zeus GameOver, CryptoLocker malware was installed on 234 thousand computers, with which a ransom of $ 27 million was collected. To distribute Zeus GameOver, the Cutwail botnets and the PonyLoader bootloader were used.
In August 2013, Dell SecureWorks Counter Threat Unit experts discovered that in addition to PonyLoader, cybercriminals use the new Upatre bootloader to distribute Zeus GameOver. Its file is small and extremely simple. Upatre uses an SSL connection to download and run the necessary malicious file, the URL of which is hard-coded inside the bootloader code. Like Pony Loader, Upatre was distributed via the Cutwail spam botnet as an attachment, which is a zip archive.
Since late January, the scheme has been slightly improved, the Zeus GameOver executable file was compressed, encrypted with the xor operation using a 32-bit key, and the resulting file was assigned the .enc extension. When decrypting, an updated version of Upatre reverses this process and obtains the original executable file.
Since February 2014, Zeus GameOver acquired the Necurs rootkit to hide its presence. The dropper contained the x86 and x64 versions of the kernel-mode driver. To raise privileges, if there are no administrator rights necessary to install the driver, the exploit CVE-2010-4398 is used. The x64 driver is signed, but since the certificate is not included in the list of trusted ones, a standard utility bcdedit.exe is called to bypass PathGuard to set the TESTSIGNING boot option.
One way or another, after the operation "Tovar" Zeus GameOver has not disappeared. Its next version , without P2P, Necurs and with support for Fast Flux continues to be spread by cybercriminals.
In December 2014, Kaspersky Lab employees announced the discovery of a new version of Zeus, called Chthonic . This version is a kind of hybrid bootloader Andromeda and ZeusVM. Chthonic has a modular structure, the following modules have been found to date:
The version number shows that the evolution of Zeus is in full swing. Moreover, in the summer of 2014 new players in the field of banking trojans appeared on the black market - Pandemiya and Kronos (a small technical analysis here ), who do not use the Zeus and Carberp source codes.

Crusade
At the end of March 2012, Microsoft held a set of activities, codenamed Operation b71 , aimed at disabling some elements of the Zeus infrastructure, as well as SpyEye and Ice IX (a project based on Zeus source code). As a result, the work of the command servers on two hosting sites was stopped: in the cities of Scranton (Pennsylvania) and Lombard (Illinois). Also, two IP addresses and about 800 domains were removed from the control structure of the botnets.
This operation was sharply criticized.from the community of IT security professionals. In particular, Fox-IT specialists noted that Microsoft in its reporting documents not only disclosed information about suspects, including authors and individual users, but also persons completely unrelated to them. Moreover, all these data were the property of the IT security community and were not subject to disclosure in connection with the conduct of operational-search measures. In addition, some domain names belonged to legal, but hacked resources. Among other things, it was found that, despite the statement by Microsoft that there was simply a disconnection for the withdrawn domain names, this was not the case and the syncing process was in full swing, that is, during it not only the IP addresses of the victims were saved, but also recorded HTTP requests with all headers, which,
In addition, this operation had almost no effect on the Zeus Gameover botnet. That's how Microsoft works, a lot of PR plus the setup of its colleagues on the shop for the sake of a moment of fame. The materials feature Slavik and Gribodemon, whose personalities we will return to.
However, while unwinding the chain of ties of cybercriminals, experts also took Citadel and its developer AquaBox at gunpoint. He, clearly noting the close attention to his person, at the end of 2012 laid down and stopped the open sale of his product.
A decisive blow to Citadel infrastructure was struck in May-June 2013 during Operation b54conducted jointly by Microsoft and the FBI. The essence of the operation was to seize 4,000 domain names that were used by Citadel. In fact, 1,462 domain names were seized, for which they were redirected to the Microsoft server for the synchol. According to experts, the entire Trojan Citadel infected about 5 million computers, mainly in the USA, Europe, Hong Kong, Singapore, India and Australia.
But here Microsoft could not help but improve. As it turned out , about 1000 domain names belonged to other security companies and were used precisely for surveillance. The owner of the abuse.ch tracker Roman Hyussi drew attention to this circumstance, and at the same time about 300 domain names used for the sync were lost.
The ultimate goal of the control interception is to send out specially configured Microsoft configuration files for Citadel, in which the websites of anti-virus companies were blocked. This feature, redirection for sites from the black list, was distinctive for Citadel, it appeared in version 1.3.5.1 of the Rain Edition, in the original Zeus it was not. And here a natural ethical question arises, and what other teams could Microsoft potentially give through “their” config? In general, it is strange that Citadel developers did not implement a digital signature mechanism for the configuration file.
Meanwhile, Citadel developers continued closed sales. In June 2013, Trend Micro specialists discovered Citadel version 3.1.0.0, which had a distribution function via USB devices. And in July, the press appearedreports that the banking systems of Japan are attacked with just such a version. 9 command servers were identified, which were accessed from about 20 thousand unique IP addresses, while 96% of infected systems were in Japan.
Hype and confusion
While security guards struggled with numerous variations of Zeus version 2 (a small digression is the information on the x64 version of Zeus 2 with C&C on the TOR network from December 2013 here ), KINS - Kasper Internet Non Security appeared on the underground scene . According to Fox-IT, a private version of KINS, almost entirely based on Zeus source codes, has been used since December 2011 to attack banking systems in Germany and the Netherlands. And then some confusion begins. The fact is that close attention to KINS was drawn much later, in 2013.
As already mentioned here, in 2012-2013 there was a wave of operations against banking Trojans. In addition to Operation b71 and Operation b54, in 2012 there were mass arrests of members of cyber groups using Carberp, which ended in the arrest of Carberp developers in Ukraine in March 2013. So, one way or another, the underground since 2012 began to urgently need another tool with the appropriate support for bank robberies.
Apparently, the name KINS was subsequently used as a kind of brand, that is, in 2013 they released a relatively new product, which the security guards began to call according to the old one - KINS. However, it is more correct to call this version PowerZeus or ZeusVM.
Distinctive features of this version:
- Using VMProtect to complicate its analysis (hence ZeusVM);
- Detection of the execution of its code in an environment of virtual machines and sandboxes;
- Using SSL to communicate with the command center
- delete your startup key at startup and restore before rebooting.
In addition, it is noticeable that the base for the dropper was PowerLoader 2 (hence the PowerZeus). In fact, it uses the source code of the Zeus and SpyEye grabbers as dlls as modules. French researcher Xylitol conducted his source-based KINS study and came to the conclusion that KINS = Zeus 2.0.8.9 + Power Loader 2.0 + SpyEye Plugins. Interestingly, in the course of his research, Xylitol went to the KINS developer; he got his Jabber from the hacked KINS test admin panel. A rather interesting dialogue took place with the developer.
During the dialogue it turned out that he was hired to develop KINS, but then “something went wrong.” All his achievements were stolen during the hack, and the KINS source code that was merged into the network is very raw alpha of the final product. One way or another, the development and closed sale of KINS is underway, and KINS and ZeusVM have become forks developed by different teams.
ZeusVM, in particular, was used during the attacks of Polish RB systems in the summer of 2013. A distinctive feature of the attack was that the config with web injects was not loaded from the Internet (although there was a link to the config URL), but was entirely contained within one of the sections of the PE file.
During the development of ZeusVM, features such as the use of steganography were additionally implemented.(November 2013), when the config, after processing xor, rc4 and base64, was embedded in a jpg image, as well as a change in the hook installation mechanism (May 2014), borrowed from Carberp. Many people hastened to announce the latest change as the next super cool hybrid of Zeus and Carberp called Zberp , but in reality this is another scarecrow.
The current state of affairs shows that, for the most part, cybercriminals have switched from using Citadel to ZeusVM.
End of the game?
As you can see, several Zeus forks are developed in parallel by several teams of attackers. Let's go back to the “main” Zeus branch called GameOver (aka Murofet). In total, three versions can be distinguished:
- version 1, distributed since September 2011, P2P functionality was first implemented, DGA is used as a backup channel;
- version 2, discovered in February 2012, in this version both the DGA algorithm and the P2P mechanism were improved;
- version 3, began to be distributed in July 2014, its distinctive feature is the use of the Fast Flux algorithm for working with a command server, while the P2P functionality has been completely removed.
Version 3 appeared after another operation called “Tovar”, carried out from April to June 2014 by the joint efforts of the FBI, Europol and a number of companies working in the field of information security, such as CrowdStrike, Dell SecureWorks, Symantec, Trend Micro and McAfee. During the investigation, it was found that Zeus GameOver was controlled by more than ten servers located on a bulletproof site of one of Odessa's hosting providers. Thus, the main control center was rendered harmless.
As a result of the disclosure of the hacker group Zeus GameOver, one of the alleged organizers was named - 30-year-old Russian resident Evgeny Bogachev, he was put on the FBI wanted list. He filed charges in absentiabased on intercepted conversations in one of the chats. In them, Bogachev, writing under the nicknames Lucky12345 and Slavik, recognizes the interlocutor that he is the creator of the Zeus Trojan.
By the way, in 2013, US authorities announced the arrest of Russian citizen Alexander Panin, who was detained on June 28 by Interpol officers and extradited from the Dominican Republic to the United States. On January 28, 2014, in a court in Atlanta, Panin admitted that he was one of the developers of SpyEye and his nickname is Gribodemon. Who knows, whether through Panin law enforcement agencies came to Bogachev?
According to Interpol, more than 1 million computers around the world were infected by Zeus GameOver, the total financial damage from the theft from remote banking systems is estimated at 75 million euros. In addition, through the Zeus GameOver, CryptoLocker malware was installed on 234 thousand computers, with which a ransom of $ 27 million was collected. To distribute Zeus GameOver, the Cutwail botnets and the PonyLoader bootloader were used.
In August 2013, Dell SecureWorks Counter Threat Unit experts discovered that in addition to PonyLoader, cybercriminals use the new Upatre bootloader to distribute Zeus GameOver. Its file is small and extremely simple. Upatre uses an SSL connection to download and run the necessary malicious file, the URL of which is hard-coded inside the bootloader code. Like Pony Loader, Upatre was distributed via the Cutwail spam botnet as an attachment, which is a zip archive.
Since late January, the scheme has been slightly improved, the Zeus GameOver executable file was compressed, encrypted with the xor operation using a 32-bit key, and the resulting file was assigned the .enc extension. When decrypting, an updated version of Upatre reverses this process and obtains the original executable file.
Since February 2014, Zeus GameOver acquired the Necurs rootkit to hide its presence. The dropper contained the x86 and x64 versions of the kernel-mode driver. To raise privileges, if there are no administrator rights necessary to install the driver, the exploit CVE-2010-4398 is used. The x64 driver is signed, but since the certificate is not included in the list of trusted ones, a standard utility bcdedit.exe is called to bypass PathGuard to set the TESTSIGNING boot option.
One way or another, after the operation "Tovar" Zeus GameOver has not disappeared. Its next version , without P2P, Necurs and with support for Fast Flux continues to be spread by cybercriminals.
New spiral
In December 2014, Kaspersky Lab employees announced the discovery of a new version of Zeus, called Chthonic . This version is a kind of hybrid bootloader Andromeda and ZeusVM. Chthonic has a modular structure, the following modules have been found to date:
- main - the main module (version 4.6.15.0 - v4.7.0.0);
- info - collection of information about the system;
- pony - module for stealing saved passwords;
- klog - keylogger;
- http - module webinjects and formgrabber;
- vnc - remote access;
- socks - proxy;
- cam_recorder - record video from a webcam.
The version number shows that the evolution of Zeus is in full swing. Moreover, in the summer of 2014 new players in the field of banking trojans appeared on the black market - Pandemiya and Kronos (a small technical analysis here ), who do not use the Zeus and Carberp source codes.
