Digital Guardian Key_P1: History and First Results
Recently, there have been regular reports of information leaks.
In this article, I wanted to share the experience of creating a device in the field of information security.
At the end of 2013, Multiclet introduced ideas about moving forward and manufacturing not only domestic processors, but also serial devices. They considered the idea of creating an accelerator board with huge performance for ordinary PCs and a device for protecting information. Since the company was private and did not manage to attract large financing for the accelerator at that moment, it was decided to start with the production of a device for protecting information.
The idea of creating a device for protecting information arose after a test of the GOST89 algorithm on the Multiclet P1 processor. It turned out that the encryption algorithm is quite well parallelized and suitable for multicellular architecture, the rnouse user revealed encryption acceleration on a multicellular architecture compared to processors in rootkens by 4 -5 times.

Fig 1. The first image of the body
The preliminary considerations underlying the terms of reference were as follows:
- software shortcomings, which are less secure than hardware;
- for encryption flash drives, the disadvantage is limited functionality.
Therefore, it was decided to make a device that would contain the flexibility and versatility of software and an answer to new threats (for example, BadUSB) and the possibility of creating corporate hierarchical information security systems. As always, I wanted "all in one."
In early 2014, a large layout was made for the development of a device from debug boards.
At the same time, the technical specifications for the device were adjusted. The first sketch of the body is shown in Fig. 1.
An approximate work schedule was developed with the end of development in August. Tasks that could occur at the same time were parallelized depending on resources. Then we started developing a prototype board and software. At the same time, it was required to accept information security experts into the team.
The next step was an attempt to launch the project on kickstarter, but failed to raise the necessary funds. Perhaps the reason was the lack of media preparation before the start of the project and the beginning of the sanctions period. Many crowdfunding experts also noted that the project is too complicated for this site.
By April, we already had on hand the device boards with the debug part (see Fig. 2). It was possible to make the correct wiring of the board and determine the components from the second attempt.
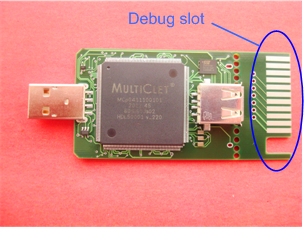
Figure 2. The device’s debug board.
At about the same time, the first prototypes of the case were made using a 3D printer, see Fig. 3. The inscription was made in the form of a sticker that wrapped the entire case printed on the printer.

Figure 3. Body prototypes
And after that, the start was given to the development of molds for the manufacture of plastic cases at one of the enterprises of Yekaterinburg. As it turned out, the process of manufacturing molds for the case and cap is quite long and required corrections, despite the fact that there were no problems with the manufacture of the case on the 3D printer. As a result, the hulls were received two months later. And so that the result was, like Apple, you need to use hot casting instead of cold.
To develop devices that have encryption functions, an enterprise must have an FSB license. Quickly enough in 2 months, including the work to fulfill the license requirements, this license was obtained.
In addition, so that users can understand that they are installing the software that we released, we received a certificate for signing applications. As it turned out, the cheapest way to get this certificate is here codesigning.ksoftware.net
Note that for the development of software that works with the Key_P1 device, for organizing support for Windows, Linux, and Mac, after a series of discussions, the Qt system was chosen.
Throughout the development phase, adjustments were made to the ToR, since only after the implementation of some functions does it come to understand how to do this conveniently and what functionality will be required. As a result, a course was determined for two versions of the device: business and professional.
The professional version differs from the business version in compliance with the KS3 security class with the FSB certificate (a number of additional conditions, including a case protected from tampering).
The business version is already mass-produced, the professional version is at the development stage. According to the main functionality of the device, the two versions will be identical.
When we started the development of the device, we did not even assume that information leaks occur so often and could cause multimillion-dollar harm to Russian companies.
Recently, a number of analytical materials on this issue have appeared.
The main problems that had to be encountered at the beta testing stage (although they conducted alpha testing on dozens of computers) and which were fixed at the time of writing this article were:
- the error “the door may have been opened” that arose when defining the device
- impossibility decrypt files with corporate keys
- an error occurred working on the scsi channel when our driver
was working - it was decided to set the names of open and closed partitions on the drives, due to problems with their perception by users
- resolved Problems with the indication of locking PIN codes after 10 attempts
It was also noted that after several openings / closures of the transparent cover protecting the Key_P1 USB connector, it began to close without a previously noticeable click, which indicates a rapid wear of the locking tabs on the case. At the same time, the cover is quite tightly fitted to the body, which in the end does not allow it to fall off from the body arbitrarily, even with significant erasure of the locking tabs.
The reject rate on the first batch of devices was about 10%. Such a percentage is obtained on the basis of permissible defects in the imported base of elements, deformation of the legs of the elements, marriage of printed circuit boards. But in further batches, after eliminating the revealed remarks, the percentage of marriage should decrease.
The device for information protection, which was released by the company Multiklet acquired the name Key_P1 MultiСlet (valid name Key_P1). The main principles that were laid down in the device:
- a friendly window interface
- data security
- focus on individual and corporate users
- mobility
In general, this device for protecting information on PCs and storage devices, developed on the basis of a multicellular processor and made in the form of a portable gadget with three connectors : USB - socket and plug, as well as a slot for SD cards. The device that turned out is shown in Fig. 4.

Fig. 4. The result of the work.
A brief comparison of software and hardware solutions.
The difference between hardware information protection devices from software, such as (Verba OW 6.1, Lissi CSP 2.0, Bikript 4.0, Crypto Pro 3.6) consists in storing keys on the device itself, without the need to install software. The difference between the Key_P1 device itself and such hardware devices as Samurai, Shipka, DataShur is that the device in question does not have an internal memory for storing information (only memory for encryption keys, firmware, etc.), and is designed to work with unlimited number of drives. And also has encryption on drives by sectors 1024 keys. Thus, Key_P1 has a wide functionality of software and increased protection of hardware.
Для работы с устройством Key_P1 Multiclet необходимо загрузить приложение Key_P1 Manager. Программа Key_P1 Manager поддерживает весь функционал устройства, обеспечивает инициализацию устройства, инициализацию накопителей, формирует корпоративные ключи и др.
Отличительные особенности программы:
1) Программа не требует установки на операционную систему
2) Для поддержки кроссплатформенной работы рекомендуется сохранить на открытый раздел накопителя версию программы для ОС Windows и Linux
3) Программа, как и устройство Key_P1 Multiclet, не привязывается к конкретному ПК или накопителю, что позволяет обеспечить работу устройства на различных ПК и обеспечить поддержку неограниченного количества накопителей
4) Программа имеет простой и удобный интерфейс, а также обеспечивает разграничение прав доступа к функционалу устройства (по ПИН коду для пользователя и администратора, который может быть от 4-х до 16-ти символов)
Для начала работы с устройством в полном объёме необходимо выполнить следующие шаги:
1) Установить внутреннюю прошивку устройства
2) Провести инициализацию устройства (установка 1024 ключей, PIN администратора
PIN пользователя, тревожного PIN кода, имени устройства)
3) Провести инициализацию накопителей (разбиение на два раздела (открытый и закрытый), установка меток разделов)
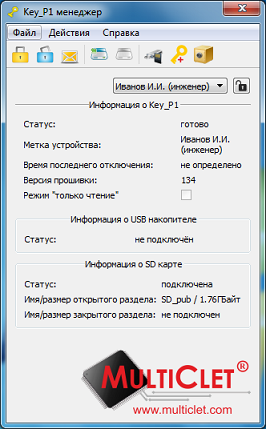
Рис 5. Основное окно программы Key_P1 Manager
1) Protecting your PC from spyware
Key_P1 only allows the operation of ordinary information storage devices, the operation of "spy devices" (represented simultaneously by the keyboard and the drive and others) will be blocked. Key_P1 is protected from the “BadUSB” problem. Control of connected devices is carried out at the hardware level. The PC simply won’t see the malicious device connected to Key_P1.
2) Information encryption Information
encryption is possible on drives and PCs. Encryption is performed according to the GOST 28147-89 algorithm with a 256-bit key width.
Files are encrypted on the Key_P1 device in the following ways:
1) automatically when copying files to a private partitioninitialized drive: in this case, the files on the drive will be encrypted on:
- the drive by sector groups using several keys out of 1024 created;
- during device initialization.
A user PIN is used to connect a private partition.
2) by choosing the encryption method in the “File Encryption” item : in this case, files can be encrypted in one of 3 ways:
- using a random key (using several keys out of the 1024 specified during initialization, 1024 parts of one file can be encrypted keys);
- a synchronized key (using the selected synchronized key);
- a corporate key (one of several keys used to encrypt files of a selected corporate group):
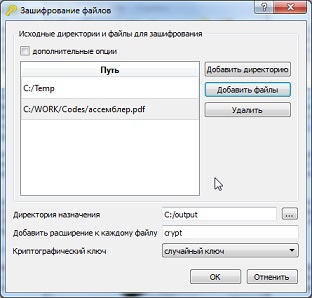
Figure 6. File encryption.
The window for decryption looks similar to the window shown in Figure 6.
3) Password safe
The device allows you to save user passwords and logins to the internal protected memory of the Key_P1 device. In the future, the user can, by clicking on the mouse, copy the login to the clipboard of the operating system and paste it into the desired field for entering the login. A similar operation can be done for the password. In this way, we provide convenient use and storage of our passwords, as well as we protect ourselves from keyloggers on a PC.
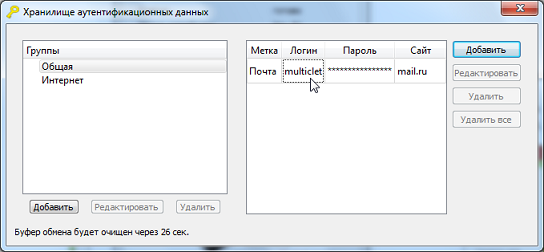
Figure 7. Storage of personal data
4) Log of actions and time
5) read-only mode
6) Three types of encryption keys
A) Random
B) synchronous
C) Corporate
The same window is used for encryption with these types of keys - “File Encryption”, see fig. 6
7) Fast crypto
conversion Key_P1 device allows fast encryption or decryption of information. Thus, users can easily and quickly exchange encrypted text messages that are sent via e-mail, various messaging systems (such as skype), social networks, etc.
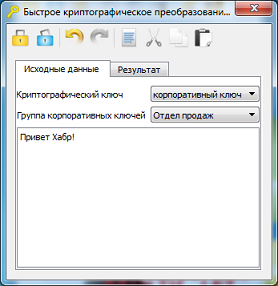
Fig 11. The original message

Figure 12. Encryption Result
Purpose: the device is designed to encrypt small amounts of confidential information.
Speed: with an open drive partition - up to 3.2 Mbit / s, with a closed drive partition up to 1.2 Mbit / s.
Supported USB port types: 1.1, 2.0, 3.0
Supported OS: WindowsXP, Windows 7, Windows 8, Linux 2.6.x, Linux 3.x
Supported drive types: USB, SD, microSD, miniSD, MMC
The production of Key_P1 devices (business version) was launched in the city of Yekaterinburg.
The device is patented, made on the basis of the multicell processor Multiclet P1.
The device has foreign components, but the development, the main processor, the manufacture, including the cases, soldering, testing, are Russian in the amount of 80% of the cost, which made the inscription “Made in Russia” possible. At the moment, work is underway to bring a series of professional version of the device and obtain permits for export, because foreign companies show interest in the device.
Key_P1 device has the ability to update the firmware (with checking the digital signature before starting).
Therefore, a decent list has been compiled for updating the firmware and software, the main points of which are:
1) Mac OS support
2) Settings menu, the parameters of which are stored on Key_P1
3) The ability to set personal keys for encryption
4) Support for the digital signature functionality
5) Setting PIN installation criteria user code
6) Generating a password for the authentication data store
7) Configuring the list of trusted devices and allowing them to work with them, as well as monitoring them
8) Server-client system for remote control of devices
9) Secure browser
In the future, it is possible to introduce Key_P1 in the Mozilla Thunderbird email client, although there are a number of issues that need to be addressed. It is also potentially feasible to create your own messenger or work together with existing ones, such as qip, icq.
Of interest is the release of the device for implementation in system units, with a direct connection to the motherboard and protection of all peripheral USB ports. Such a device can be based on the domestic Multiclet R1 processor, which will increase productivity tenfold. Key_P1 in this case can protect against the problems described in the article about the security of 4G USB modem habrahabr.ru/company/pt/blog/243697/#first_unread. Although the modern version of Key_P1 after the release of a special update will be able to protect your PC from malicious devices.
In addition, an important feature of the device is its simple integration into software security systems, as The device does not require installation of software and drivers for the OS.
The device for identification in the OS uses standard system drivers.
We carefully consider useful tips and user comments, as well as analyze customer reviews. It is on the basis of this information that the selection of the next updates of the device and the directions of its development will be made. We are aimed at making a high-quality and popular device for protecting information with a wide range of applications.
In 1988, the American Computer Equipment Association declared November 30 (the first recorded Morris worm epidemic) International Computer Security Day. The purpose of the Day is to remind users of the need to protect their computers and all information stored in them.
Congratulations to all the professionals who stand guard over information security!
UPD1: also in the process of developing the device, we received a VID for our USB device, which cost us $ 5.000 on usb.org and this is the price without using the usb logo on the case.
PS To the current moment, for the business version, the following requirements have been received:
- weakening algorithms: 0
- adding special keys: 0
- creating firmware for hacking: 0
In this article, I wanted to share the experience of creating a device in the field of information security.
1. History of creation
At the end of 2013, Multiclet introduced ideas about moving forward and manufacturing not only domestic processors, but also serial devices. They considered the idea of creating an accelerator board with huge performance for ordinary PCs and a device for protecting information. Since the company was private and did not manage to attract large financing for the accelerator at that moment, it was decided to start with the production of a device for protecting information.
The idea of creating a device for protecting information arose after a test of the GOST89 algorithm on the Multiclet P1 processor. It turned out that the encryption algorithm is quite well parallelized and suitable for multicellular architecture, the rnouse user revealed encryption acceleration on a multicellular architecture compared to processors in rootkens by 4 -5 times.

Fig 1. The first image of the body
Formulation of the problem
The preliminary considerations underlying the terms of reference were as follows:
- software shortcomings, which are less secure than hardware;
- for encryption flash drives, the disadvantage is limited functionality.
Therefore, it was decided to make a device that would contain the flexibility and versatility of software and an answer to new threats (for example, BadUSB) and the possibility of creating corporate hierarchical information security systems. As always, I wanted "all in one."
In early 2014, a large layout was made for the development of a device from debug boards.
At the same time, the technical specifications for the device were adjusted. The first sketch of the body is shown in Fig. 1.
An approximate work schedule was developed with the end of development in August. Tasks that could occur at the same time were parallelized depending on resources. Then we started developing a prototype board and software. At the same time, it was required to accept information security experts into the team.
The next step was an attempt to launch the project on kickstarter, but failed to raise the necessary funds. Perhaps the reason was the lack of media preparation before the start of the project and the beginning of the sanctions period. Many crowdfunding experts also noted that the project is too complicated for this site.
By April, we already had on hand the device boards with the debug part (see Fig. 2). It was possible to make the correct wiring of the board and determine the components from the second attempt.

Figure 2. The device’s debug board.
At about the same time, the first prototypes of the case were made using a 3D printer, see Fig. 3. The inscription was made in the form of a sticker that wrapped the entire case printed on the printer.

Figure 3. Body prototypes
Some points of development
And after that, the start was given to the development of molds for the manufacture of plastic cases at one of the enterprises of Yekaterinburg. As it turned out, the process of manufacturing molds for the case and cap is quite long and required corrections, despite the fact that there were no problems with the manufacture of the case on the 3D printer. As a result, the hulls were received two months later. And so that the result was, like Apple, you need to use hot casting instead of cold.
To develop devices that have encryption functions, an enterprise must have an FSB license. Quickly enough in 2 months, including the work to fulfill the license requirements, this license was obtained.
In addition, so that users can understand that they are installing the software that we released, we received a certificate for signing applications. As it turned out, the cheapest way to get this certificate is here codesigning.ksoftware.net
Note that for the development of software that works with the Key_P1 device, for organizing support for Windows, Linux, and Mac, after a series of discussions, the Qt system was chosen.
Throughout the development phase, adjustments were made to the ToR, since only after the implementation of some functions does it come to understand how to do this conveniently and what functionality will be required. As a result, a course was determined for two versions of the device: business and professional.
The professional version differs from the business version in compliance with the KS3 security class with the FSB certificate (a number of additional conditions, including a case protected from tampering).
The business version is already mass-produced, the professional version is at the development stage. According to the main functionality of the device, the two versions will be identical.
When we started the development of the device, we did not even assume that information leaks occur so often and could cause multimillion-dollar harm to Russian companies.
Recently, a number of analytical materials on this issue have appeared.
November analytics and information leaks
More than 90% of companies encounter major data leaks, leading to serious financial problems, including bankruptcy, Zecurion Analytics made such conclusions based on a survey conducted among companies using information leakage protection systems.
Zecurion analysts conducted more than 100 interviews with company executives and cybersecurity experts and examined real cases of the detection of intentional and accidental leaks of corporate information. It turned out that only 8% of organizations do not suffer from data leaks, and in 30% of large and medium-sized companies record on average two attempts a month to steal valuable information, the loss of which affects the financial stability of the company. This is also confirmed by the maximum amount of damage of $ 30 million that the Russian company suffered from the leak of confidential data.
Some of the most famous data leaks in the last couple of months:
1) As a result of a hacker attack, the data of employees, management and customers of the US Postal Service (USPS) were compromised. 800 thousand records, including names, addresses and social security numbers of Americans, may have appeared in the hands of the attackers, reports The Wall Street Journal.
2) The names, addresses, phone numbers, email addresses of about 83 million household and business owners were stolen through the JPMorgan Chase system, Vedomosti reports citing Reuters. The bank does not have information about whether hackers got access to account numbers, passwords, birth dates and SSN.
3) Home Depot, the world's largest building materials and repair tool company, said 53 million store email addresses were compromised. According to preliminary estimates, Home Depot losses due to the hack amounted to $ 56 million, the securitylab.ru portal reports with reference to the company's report.
Zecurion analysts conducted more than 100 interviews with company executives and cybersecurity experts and examined real cases of the detection of intentional and accidental leaks of corporate information. It turned out that only 8% of organizations do not suffer from data leaks, and in 30% of large and medium-sized companies record on average two attempts a month to steal valuable information, the loss of which affects the financial stability of the company. This is also confirmed by the maximum amount of damage of $ 30 million that the Russian company suffered from the leak of confidential data.
Some of the most famous data leaks in the last couple of months:
1) As a result of a hacker attack, the data of employees, management and customers of the US Postal Service (USPS) were compromised. 800 thousand records, including names, addresses and social security numbers of Americans, may have appeared in the hands of the attackers, reports The Wall Street Journal.
2) The names, addresses, phone numbers, email addresses of about 83 million household and business owners were stolen through the JPMorgan Chase system, Vedomosti reports citing Reuters. The bank does not have information about whether hackers got access to account numbers, passwords, birth dates and SSN.
3) Home Depot, the world's largest building materials and repair tool company, said 53 million store email addresses were compromised. According to preliminary estimates, Home Depot losses due to the hack amounted to $ 56 million, the securitylab.ru portal reports with reference to the company's report.
Error handling
The main problems that had to be encountered at the beta testing stage (although they conducted alpha testing on dozens of computers) and which were fixed at the time of writing this article were:
- the error “the door may have been opened” that arose when defining the device
- impossibility decrypt files with corporate keys
- an error occurred working on the scsi channel when our driver
was working - it was decided to set the names of open and closed partitions on the drives, due to problems with their perception by users
- resolved Problems with the indication of locking PIN codes after 10 attempts
It was also noted that after several openings / closures of the transparent cover protecting the Key_P1 USB connector, it began to close without a previously noticeable click, which indicates a rapid wear of the locking tabs on the case. At the same time, the cover is quite tightly fitted to the body, which in the end does not allow it to fall off from the body arbitrarily, even with significant erasure of the locking tabs.
The reject rate on the first batch of devices was about 10%. Such a percentage is obtained on the basis of permissible defects in the imported base of elements, deformation of the legs of the elements, marriage of printed circuit boards. But in further batches, after eliminating the revealed remarks, the percentage of marriage should decrease.
The device for information protection, which was released by the company Multiklet acquired the name Key_P1 MultiСlet (valid name Key_P1). The main principles that were laid down in the device:
- a friendly window interface
- data security
- focus on individual and corporate users
- mobility
In general, this device for protecting information on PCs and storage devices, developed on the basis of a multicellular processor and made in the form of a portable gadget with three connectors : USB - socket and plug, as well as a slot for SD cards. The device that turned out is shown in Fig. 4.

Fig. 4. The result of the work.
A brief comparison of software and hardware solutions.
The difference between hardware information protection devices from software, such as (Verba OW 6.1, Lissi CSP 2.0, Bikript 4.0, Crypto Pro 3.6) consists in storing keys on the device itself, without the need to install software. The difference between the Key_P1 device itself and such hardware devices as Samurai, Shipka, DataShur is that the device in question does not have an internal memory for storing information (only memory for encryption keys, firmware, etc.), and is designed to work with unlimited number of drives. And also has encryption on drives by sectors 1024 keys. Thus, Key_P1 has a wide functionality of software and increased protection of hardware.
2. How Key_P1 Works
Для работы с устройством Key_P1 Multiclet необходимо загрузить приложение Key_P1 Manager. Программа Key_P1 Manager поддерживает весь функционал устройства, обеспечивает инициализацию устройства, инициализацию накопителей, формирует корпоративные ключи и др.
Отличительные особенности программы:
1) Программа не требует установки на операционную систему
2) Для поддержки кроссплатформенной работы рекомендуется сохранить на открытый раздел накопителя версию программы для ОС Windows и Linux
3) Программа, как и устройство Key_P1 Multiclet, не привязывается к конкретному ПК или накопителю, что позволяет обеспечить работу устройства на различных ПК и обеспечить поддержку неограниченного количества накопителей
4) Программа имеет простой и удобный интерфейс, а также обеспечивает разграничение прав доступа к функционалу устройства (по ПИН коду для пользователя и администратора, который может быть от 4-х до 16-ти символов)
Для начала работы с устройством в полном объёме необходимо выполнить следующие шаги:
1) Установить внутреннюю прошивку устройства
2) Провести инициализацию устройства (установка 1024 ключей, PIN администратора
PIN пользователя, тревожного PIN кода, имени устройства)
3) Провести инициализацию накопителей (разбиение на два раздела (открытый и закрытый), установка меток разделов)

Рис 5. Основное окно программы Key_P1 Manager
3. Функционал устройства
1) Protecting your PC from spyware
Key_P1 only allows the operation of ordinary information storage devices, the operation of "spy devices" (represented simultaneously by the keyboard and the drive and others) will be blocked. Key_P1 is protected from the “BadUSB” problem. Control of connected devices is carried out at the hardware level. The PC simply won’t see the malicious device connected to Key_P1.
2) Information encryption Information
encryption is possible on drives and PCs. Encryption is performed according to the GOST 28147-89 algorithm with a 256-bit key width.
Files are encrypted on the Key_P1 device in the following ways:
1) automatically when copying files to a private partitioninitialized drive: in this case, the files on the drive will be encrypted on:
- the drive by sector groups using several keys out of 1024 created;
- during device initialization.
A user PIN is used to connect a private partition.
2) by choosing the encryption method in the “File Encryption” item : in this case, files can be encrypted in one of 3 ways:
- using a random key (using several keys out of the 1024 specified during initialization, 1024 parts of one file can be encrypted keys);
- a synchronized key (using the selected synchronized key);
- a corporate key (one of several keys used to encrypt files of a selected corporate group):

Figure 6. File encryption.
The window for decryption looks similar to the window shown in Figure 6.
3) Password safe
The device allows you to save user passwords and logins to the internal protected memory of the Key_P1 device. In the future, the user can, by clicking on the mouse, copy the login to the clipboard of the operating system and paste it into the desired field for entering the login. A similar operation can be done for the password. In this way, we provide convenient use and storage of our passwords, as well as we protect ourselves from keyloggers on a PC.

Figure 7. Storage of personal data
4) Log of actions and time
Detailed description
The event log displays the connection and disconnection times of the Key_P1 device and is not available for adjustment. Thus, unregulated shutdowns of the device will provide information to the security service about a possible unauthorized insider leak.
In the future, it is also planned to display the main user actions.
In the future, it is also planned to display the main user actions.
5) read-only mode
Detailed description
The ability to record information from computers to removable drives connected to Key_P1 can be blocked by the administrator's PIN code. For this, the “read-only" mode is set so that Key_P1 blocks any unauthorized recording of confidential data, viruses or other programs to the drive at the hardware level.
6) Three types of encryption keys
A) Random
Detailed description
Creation: Formed in the process of initializing the device.
Quantity: 1024 pieces (fixed)
Application: for encrypting information on a closed drive section and for encrypting ordinary information.
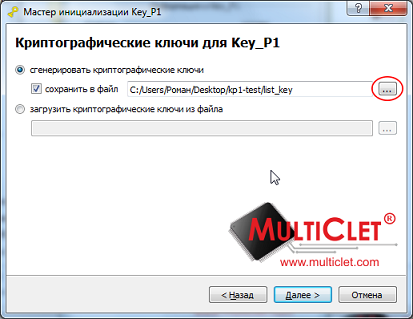
Fig 8. The formation of random keys
Quantity: 1024 pieces (fixed)
Application: for encrypting information on a closed drive section and for encrypting ordinary information.

Fig 8. The formation of random keys
B) synchronous
Detailed description
Creation: Before starting to create synchronous keys, subscribers who plan to send encrypted information must exchange the
following data among themselves : Algorithm No. (first, second or third) and initial value
(code word or phrase) in order to be generated identical keys for
all subscribers.
Quantity: 104 pieces
Application: to encrypt information between users when you need to quickly exchange confidential information (for example, on a business trip).
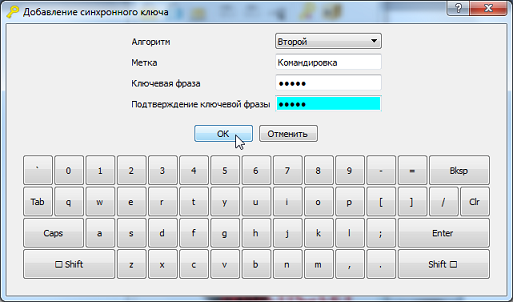
Fig 9. The formation of synchronous keys
following data among themselves : Algorithm No. (first, second or third) and initial value
(code word or phrase) in order to be generated identical keys for
all subscribers.
Quantity: 104 pieces
Application: to encrypt information between users when you need to quickly exchange confidential information (for example, on a business trip).

Fig 9. The formation of synchronous keys
C) Corporate
Detailed description
Creation: Key_P1 provides for differentiation of access rights to encrypted files. The enterprise security service will be able to create different delineations of rights by department. In this case, the head will have access to all files. Company employees can encode files for their colleagues using the Key_P1 Manager program with the appropriate access level.
Quantity: 512 pieces
Application: for encryption of information between users within the company.

Figure 10. Formation of corporate keys
Quantity: 512 pieces
Application: for encryption of information between users within the company.

Figure 10. Formation of corporate keys
The same window is used for encryption with these types of keys - “File Encryption”, see fig. 6
7) Fast crypto
conversion Key_P1 device allows fast encryption or decryption of information. Thus, users can easily and quickly exchange encrypted text messages that are sent via e-mail, various messaging systems (such as skype), social networks, etc.

Fig 11. The original message

Figure 12. Encryption Result
4. Specifications
Purpose: the device is designed to encrypt small amounts of confidential information.
Speed: with an open drive partition - up to 3.2 Mbit / s, with a closed drive partition up to 1.2 Mbit / s.
Supported USB port types: 1.1, 2.0, 3.0
Supported OS: WindowsXP, Windows 7, Windows 8, Linux 2.6.x, Linux 3.x
Supported drive types: USB, SD, microSD, miniSD, MMC
5. Current status
The production of Key_P1 devices (business version) was launched in the city of Yekaterinburg.
The device is patented, made on the basis of the multicell processor Multiclet P1.
The device has foreign components, but the development, the main processor, the manufacture, including the cases, soldering, testing, are Russian in the amount of 80% of the cost, which made the inscription “Made in Russia” possible. At the moment, work is underway to bring a series of professional version of the device and obtain permits for export, because foreign companies show interest in the device.
6. Further development
Key_P1 device has the ability to update the firmware (with checking the digital signature before starting).
Therefore, a decent list has been compiled for updating the firmware and software, the main points of which are:
1) Mac OS support
2) Settings menu, the parameters of which are stored on Key_P1
3) The ability to set personal keys for encryption
4) Support for the digital signature functionality
5) Setting PIN installation criteria user code
6) Generating a password for the authentication data store
7) Configuring the list of trusted devices and allowing them to work with them, as well as monitoring them
8) Server-client system for remote control of devices
9) Secure browser
In the future, it is possible to introduce Key_P1 in the Mozilla Thunderbird email client, although there are a number of issues that need to be addressed. It is also potentially feasible to create your own messenger or work together with existing ones, such as qip, icq.
Of interest is the release of the device for implementation in system units, with a direct connection to the motherboard and protection of all peripheral USB ports. Such a device can be based on the domestic Multiclet R1 processor, which will increase productivity tenfold. Key_P1 in this case can protect against the problems described in the article about the security of 4G USB modem habrahabr.ru/company/pt/blog/243697/#first_unread. Although the modern version of Key_P1 after the release of a special update will be able to protect your PC from malicious devices.
In addition, an important feature of the device is its simple integration into software security systems, as The device does not require installation of software and drivers for the OS.
The device for identification in the OS uses standard system drivers.
One of the reasons why we are here
We carefully consider useful tips and user comments, as well as analyze customer reviews. It is on the basis of this information that the selection of the next updates of the device and the directions of its development will be made. We are aimed at making a high-quality and popular device for protecting information with a wide range of applications.
In 1988, the American Computer Equipment Association declared November 30 (the first recorded Morris worm epidemic) International Computer Security Day. The purpose of the Day is to remind users of the need to protect their computers and all information stored in them.
Congratulations to all the professionals who stand guard over information security!
UPD1: also in the process of developing the device, we received a VID for our USB device, which cost us $ 5.000 on usb.org and this is the price without using the usb logo on the case.
PS To the current moment, for the business version, the following requirements have been received:
- weakening algorithms: 0
- adding special keys: 0
- creating firmware for hacking: 0
