Conference DEFCON 22. Adrian Crenshaw. What can “burn” users TOR
- Transfer
Hello, my name is Adrian Crenshaw. I am a co-founder of Derbycon, the founder of Irongeek.com, I’m interested in information security and I work as a senior security consultant for Trusted Sec. I will tell you how people place their original documents in Darknet and how it makes them easy to catch.
These are well-known stories about people who used TOR or other anonymizers and were caught mainly due to the neglect of OPSEC rules.
The story I assigned to number 0 is the bombs that were supposedly laid at Harvard University last year. One guy sent an email to various departments of the university, including the security service and the student newspaper, indicating the places where the bombs were located: the science center, Sever Hall, Emerson Hall, Thayler Hall. He wrote that they acted quickly, because the bombs would explode soon. The announcement of this was published in the media on December 16, 2013.
So who was this guy? He used the "guerrilla" mail service to send Guerilla Mail emails one-time and sent his letter via TOR.

But he did not take into account the fact that Guerilla Mail puts the original IP address of the sender in the message header. For example, if you send a letter from home, then it will show the IP address of your home computer. The slide shows an example where I used my irongeek.com mailbox to show how it works. This guy thought of anonymity and used TOR, so his letter indicated the IP address of the TOR server. However, he did not take into account that all the TOR nodes, with the exception of “bridges”, are known and are in the public domain - they are listed, for example, on this site torstatus.blutmagie.de, and it is easy to determine if a particular computer belongs to the TOR network or not. If you don’t use the bridge, it’s very easy to track who joined the Harvard LAN and from where TOR was used when the email was sent with threats.
If this guy used the “bridge” or sent his letter from some cafe or other public place, it would be difficult to track him. But he used the university's network, connecting to it from the student dormitory. Therefore, they were able to find this 20-year-old boy named Eldo Kim, who, as it turned out, in this way wanted to achieve the abolition of exams.
At the same time, 10 students used the TOR network at the same time, and when the FBI began to interrogate them all, they found enough evidence against Kim and he had to admit what he had done.

The following lessons can be learned from this case:
In a second I will talk about a bit more correlation attacks. First, consider a correlation that compares the end point with the traffic exit point. The meaning of such an attack is that you monitor traffic and see what happens on the network. Of course, everything is encrypted here, but if you look at the request of 5 MB in size, which is sent from the client’s computer to the server, you can see interesting things. This computer with a lilac screen under the server is an observer who “sniffs out” network traffic.
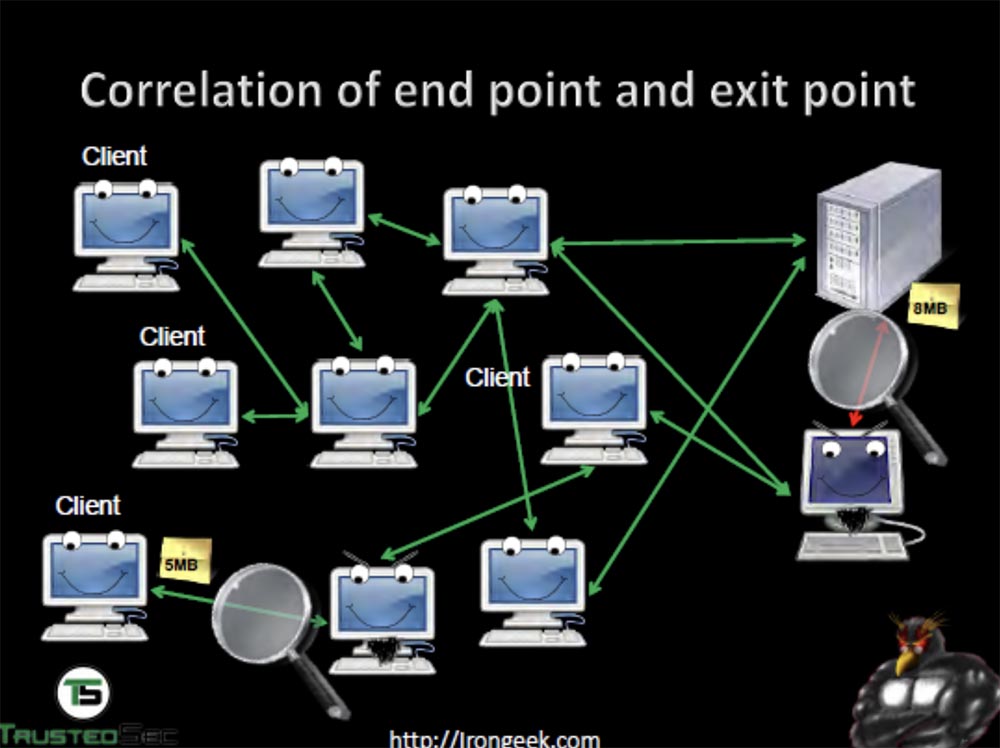
He sees that the server receives a request of 5 MB, and the answer comes back with a volume of 8 MB already, because it is “stout” due to encryption keys. Then you can compare the time during which the request was sent and the response received, and identify the computer from which the request was sent.
You can use the timing correlation to track the path of traffic between computers on the network. At the same time, a DDoS attack is used in order to change the load along the traffic path, which allows you to track the path between the network computers.
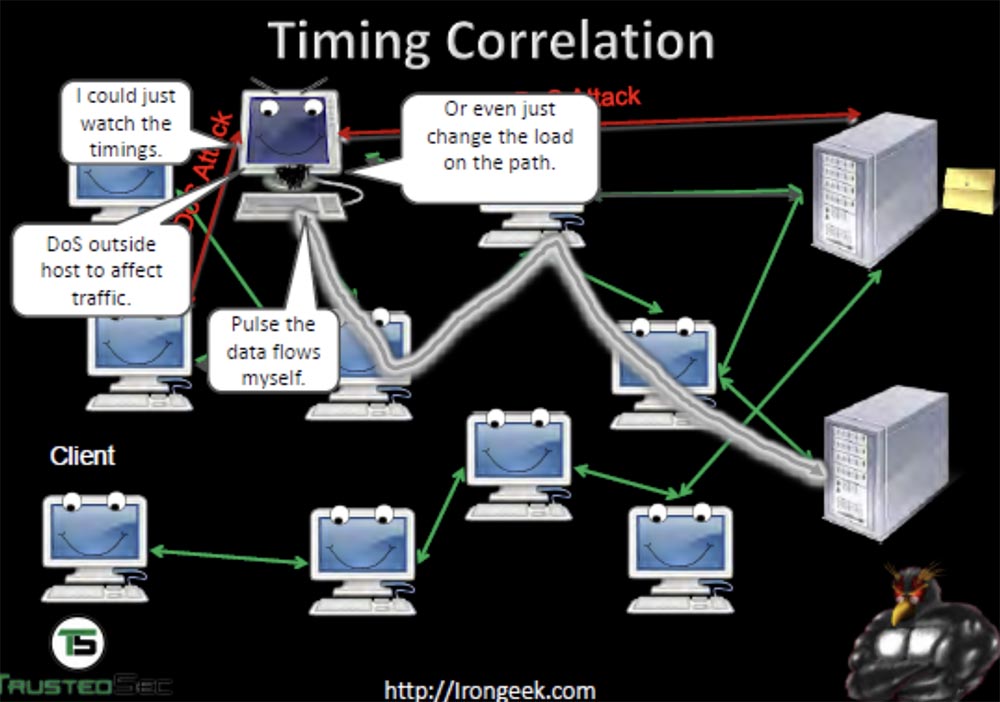
You can also generate your own traffic to create your own “pattern” of its passage and thus “ring out” the computers of the network through which it passes. This way, you can find out who is talking to whom and through what servers — first, with a DDoS attack, we “crash” one server, look at which machines have left the network, then “crash” another and so on. The NSA used a project called Maloney, which applied this method of monitoring the TOR network.
You can also monitor the activity of the DNS server and monitor the leakage data. If I do not use a proxy for DNS, and by default it is, then I can send a request to a DNS server. He cannot see where and where my traffic is coming from, but he can see which sites I visit and determine the IP address of the TOR node.

Next, consider case number 1 - LulzSec, a branch of the hacker group Anonymous, the case of Hector Xavier Monsegur, or “Sabu”. Usually he used TOR to connect to the IRC chat, but once he was too lazy to launch TOR, used an open network and got caught by the feds, after which he was forced to cooperate with them for 9 months. Hector used IRC to communicate with Jeremy Hammond, and this fact was used to arrest Hammond in 2012.
If you use this chat, always use anonymity, because a person who owns an IRC server can easily get your IP address and find out who you are. One of the members of the anonymous traffic in the UK, who owned the server, got angry at his friends and began to “drop” their IP addresses to the public.
Hammond under the nickname sub-g used TOR, so it was not possible to decrypt its messages. But the MAC address of his computer was fixed on this network, and the FBI correlated the time of his conversation with Sabu via IRC. They found that sub-g and Hammond were online at the same time, that Jeremy was at home at that time and his computer was connected to that network. They had gathered enough evidence of where Hammond got access from, they also had IRC chat messages that Sabu gave them, and so on. More information about this can be found at the link .
From this case we can draw the following conclusions:

Next, consider case # 2 - Freedom Hosting provided mail services to customers within the TOR network, that is, allowed them to create their own mailboxes within the anonymous network. They, among other things, were used to distribute child porn, although they mostly served simply to exchange letters between users. It is because of child porn that this hosting in 2011 was attacked by Anonymous during the operation of “sweeping” Darknet.
In particular, the Lolita City site hosted by Freedom Hosting was subjected to a DDoS attack, as a result of which Anonymus hackers were able to publish in public access a whole list of its users. In July 2013, the FBI compromised several Freedom Hosting mailboxes and injected malicious JavaScript code into them that used the vulnerability of CVE-2013-1690 version 17 ESR of the Firefox browser. As you know, the TOR software package is based on Firefox. Its developers have released a patch that fixes the vulnerability, but many Thor users, as usual, have not updated their on-line browser version in time.
This vulnerability allowed the FBI to gain control of the Freedom Hosting mail by deploying an exploit called Magneto. It is a tiny Windows executable. Magneto searches for the victim's Windows host name and MAC address of its computer and sends the information back to the FBI server in Virginia, exposing the victim’s real IP address. The script sends back data with a standard HTTP request outside the TOR network. Details can be read on the link .
This project is similar to a project called Egotistical Giraffe - a tool that the FBI used against TOR users through vulnerable software on their computers. Magic Lantern, FOXACID, and CIPAV, the verifier for Internet protocol and computer addresses, also belong to similar spyware used by the feds.
As a result, the FBI was able to destroy Freedom Hosting, arresting for distribution of child pornography of its owner, 28-year-old citizen of Ireland and the United States, Eric Wan Marques. He was able to connect with the server Freedom Hosting thanks to payment documents. He bought something, and the purchase information with reference to his real IP address remained in his mailbox Freedom Hosting. When the security services arrested him, he rushed to turn off his laptop so that when reloading, the data encryption system on the hard disk was activated, but he did not succeed.
The following lessons can be learned from this case:
Make the hidden server contact you to determine its real IP address and find out if it is exposed to any vulnerabilities for various attacks, for example, buffer overflow, etc.

This is necessary in order not to screw it up and not fall under the supervision of the feds, by contacting such a server within the TOR network.
Case number 3 concerns the well-known Silk Road, or Silk Road. This market Darknet was ruled by the pseudonym Dread Pirate Roberts, or "The Terrible Pirate Roberts." This was an electronic platform for buyers and sellers, where they traded, let's say, not a completely legal product. The materials of the Silk Road case file as of September 23, 2013 show that about 13,000 lists of goods were posted on the TOR network and were posted on the site and related to such requests as “marijuana”, “ecstasy”, “intoxicants”, “opioids , Precursors, psychedelics, and similar drugs. In short, it was Charlie Sheen's dream.
Also on the TOR site, 159 sites were found that provide services for hacking accounts of various networks at the request of the client, including Facebook and Twitter, so that the customer would be able to control and change the personal information of the account owner at will. It also posted 22 tutorials on hacking ATMs, as well as contacts of providers of illegal services such as “anonymous bank accounts”, “counterfeit accounts in CAD / GBP / EUR / USD currency”, “sale of firearms and ammunition”, “stolen information of bank cards and PayPal accounts "and even" hired killers in more than 10 countries. " The only thing that was not offered for sale or was not found on the network was fake diplomas, certificates, medical prescriptions and fake money. Apparently, the site owner had problems with this.
After the volume of transactions reached 1.2 billion dollars, the FBI became interested in the Silk Road. First of all, they began to check the very first links to Silk Road on the public Internet, using Google search queries, changing time intervals. They found the earliest link to this resource on the small site of addicts Shroomery, where the guy under the nickname altoid posted a link to the Silk Road page on the TOR network.

In essence, he advertised this site, stating that on the Silk Road website you can anonymously purchase anything you want. This post was posted on January 27, 2011.
Then, on the site bitcointalk.org, someone opened the topic “Heroin Store”, and the user under the nickname ShadowOfHarbringer wrote that Silk Road may not be selling heroin, but this is the first marketplace where you can buy all other drugs for bitcoins anonymously. This also sounded like an advertisement for this resource, and this user ended his post with the phrase: “guys, let me know what you think about it!”, Hinting at feedback.
Thus, the feds found that the “Silk Road” really exists and works. Later, in October of the same year, on the same site bitcointalk.org a character familiar to the Shroomery site under the nickname altoid appeared, who opened the topic “I am looking for a professional IT specialist to open a bitcoin start-up”, where he wrote that interested persons can contact him to the specified email address. And you know what he did? He wrote the address of his mailbox, registered in his real name and surname - Ross Ulbricht, rossulbricht@gmail.com. This is called a complete failure of the OPSEC principle.
Therefore, the FBI did not find it easy to establish a connection between altoid, the first mention of the “Silk Road” and bitcoins. The altoid email was the same as Ross. Ulbricht’s profile on Google+ showed that he is interested in the libertarians of Ludwig von Mises, “the world center of the Austrian School of Economics”.
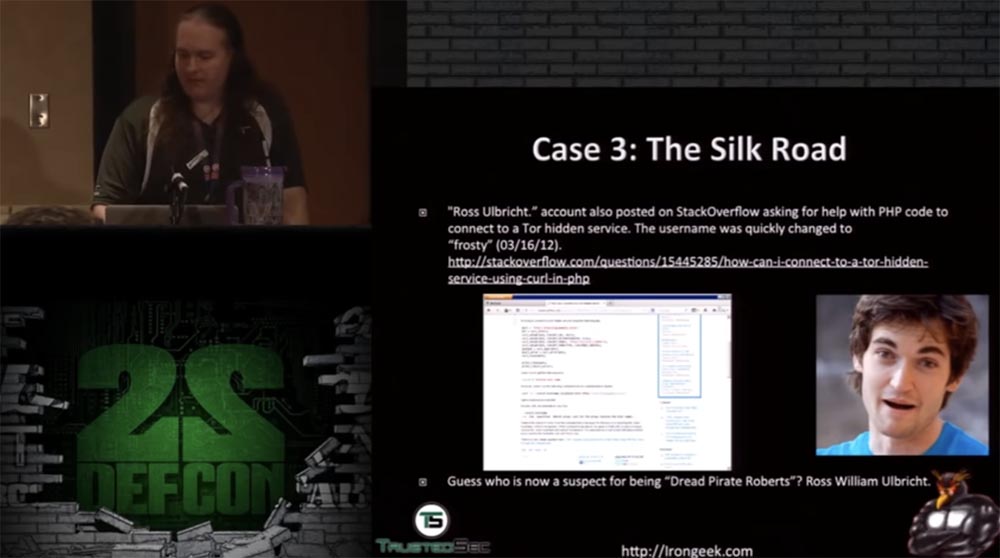
Then they found out that the Dread Pirate Roberts signature on the Silk Road forums contained a link to the Moses Institute, and the Austrian economic theory had a great influence on the Silk Road philosophy. In addition, from Ross Ulbricht account, an entry was made on StackOverflow with a request to help him in writing PHP code to communicate with the hidden TOR services.
True, this account was quickly replaced by “frosty”, but the first username corresponded to his real name and last name. The combination of this evidence allowed the FBI to obtain an arrest warrant for Ulbricht and left no doubt that Ross William Ulbricht and Dread Pirate Roberts are one and the same person.
I would probably also not hide my true face if I earned 1.2 billion dollars. The feds also found out that someone was connecting to the Silk Road host server from an Internet cafe located next to Ross’s apartment in San Francisco. Letters addressed to Pirate Roberts revealed that he lived in the Pacific time zone.
The IP address of the Silk Road server was connected to a VPN via an IP address owned by an Internet cafe on Laguna Street in San Francisco, and from there at the same time, on June 3, 2013, Ross logged into his mailbox on gmail.
In a private message to Pirate Robets, one of the users wrote that he discovered a leak of information from the site through an external IP address belonging to the VPN. Then the FBI somehow managed to capture and copy the images of the hard drives of one of the servers of the Silk Road. Presumably they paid hacker Nicholas Weaver to hack Silk Road and connect it with an external server that did not use Thor to reveal the real IP address of the Silk Road server.
On July 10, 2013, the US Customs Service intercepted 9 IDs for different names, but all of these documents contained a photograph of Ross Ulbricht. The security service interrogated Ross, however he denied that he ordered the production of these certificates, and refused to give any comments on this matter. It was very reasonable of him. But then he did something stupid, stating that, hypothetically, anyone could go to the site called “Silk Road” or “TOR” and buy drugs or fake documents there. Why did he need to talk about it at all, if, as a good citizen, he should not have known anything about it?
However, private correspondence showed that Dread Pirate Roberts was interested in buying fake IDs.
Then, one of the servers of the Silk Road used SSH and private keys that contained the entry frosty @ frosty. This server used the same code that was once hosted on StackOverflow. Finally, on October 1, the FBI arrested Ulbricht in the public library just after he entered the password into his laptop. A lot of incriminating evidence was discovered in the laptop.
Further information on this case can be found in the article by Nate Anderson and in the documents that Agent Christopher Tarbell submitted to the court. They are located on the links ( one and two ).
The following lessons can be learned from this case:
So, we have a little time left to tell you how the de-anonymization of TOR users works and show you several ways to reveal the anonymity of the user.
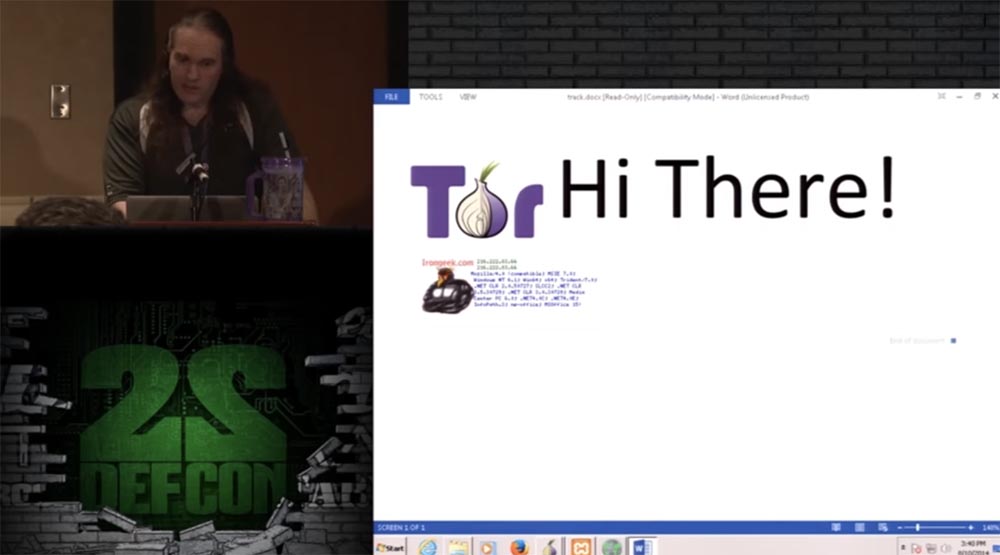
First you need to configure the proxy on the local machine. Then you access something on the TOR network, and I want to convince you to go to a specific site and download the Word document called track.docx from there, that is, follow the link .

Now I'm trying to connect to the TOR network, it depends on how your browser is configured, because it may not allow the use of proxy connections. So, TOR has started, and now I need to follow the link to a specific site and open the document track.docx.

It is a trap. You see the TOR greeting and the loaded document lines on the screen. That's it, you opened this document on your computer.
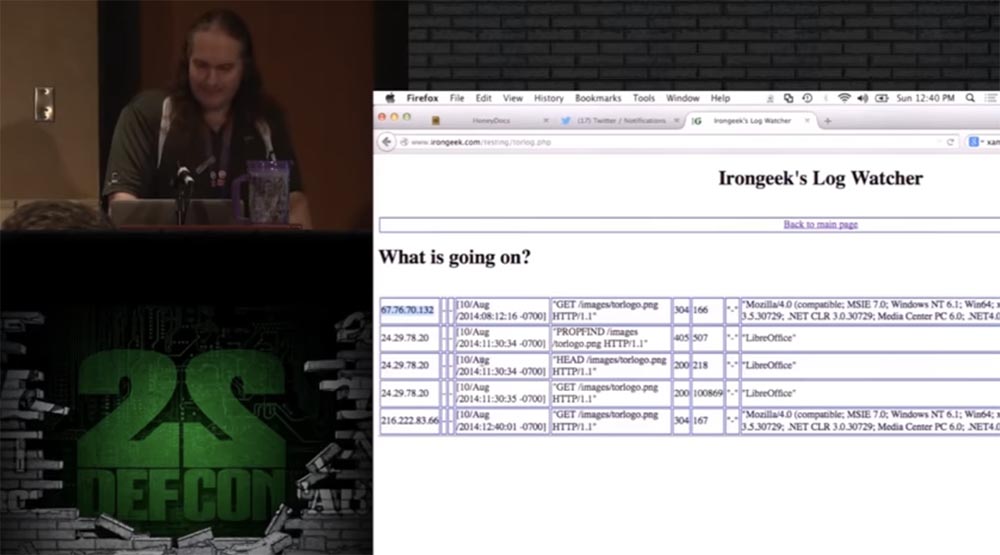
Now I go to my irongeek.com website, open a log of logs and see the real IP address of the computer on which this document was opened, the opening time and the characteristics of the browser used.
What else can I do? Ask the user to download the archived credit_card.zip document containing a bunch of stolen credit card data. After he does this, on my screen on honeydocx.com/hive/sting/4254/buzz I will be able to see who opened this document and its real IP address.

To open the buzz, I need to enter my username and password, which I registered on honeydocx.com. I do this and everything is ready - you see the IP address and location coordinates of the user who opened credit_card.zip.

I showed you what happens if people use TOR, but do not set up a proxy connection properly in the browser.
There are more professional tools than me, since I use documents of different formats, after opening which my exploit is launched on the user's computer.
The next thing I can do to fool a user is to install a hidden service. On the screen, you see the OWASP Mutillidae II is a deliberately vulnerable open source application that serves various security threats. If you open the menu, you can see the types of attacks that can be experienced, for example, SQL injection. In this application, you can demonstrate the pinging attack of an IP0 address using the command line, see who returns me a ping, and determine its IP address.
Then you can view links to unsafe objects and do many more such things. In this application, TOR starts up very slowly, so I can’t demonstrate how it works, I have too little time left to speak. Let me just say that the main idea of the command line injection is that you can see who ping returns you. Asking whether I can determine the IP address on the VPN in this way, I will say yes, it is possible.
If you want, you can view a detailed video about it on my site by the link .
Thank you for attention!
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
These are well-known stories about people who used TOR or other anonymizers and were caught mainly due to the neglect of OPSEC rules.
The story I assigned to number 0 is the bombs that were supposedly laid at Harvard University last year. One guy sent an email to various departments of the university, including the security service and the student newspaper, indicating the places where the bombs were located: the science center, Sever Hall, Emerson Hall, Thayler Hall. He wrote that they acted quickly, because the bombs would explode soon. The announcement of this was published in the media on December 16, 2013.
So who was this guy? He used the "guerrilla" mail service to send Guerilla Mail emails one-time and sent his letter via TOR.

But he did not take into account the fact that Guerilla Mail puts the original IP address of the sender in the message header. For example, if you send a letter from home, then it will show the IP address of your home computer. The slide shows an example where I used my irongeek.com mailbox to show how it works. This guy thought of anonymity and used TOR, so his letter indicated the IP address of the TOR server. However, he did not take into account that all the TOR nodes, with the exception of “bridges”, are known and are in the public domain - they are listed, for example, on this site torstatus.blutmagie.de, and it is easy to determine if a particular computer belongs to the TOR network or not. If you don’t use the bridge, it’s very easy to track who joined the Harvard LAN and from where TOR was used when the email was sent with threats.
If this guy used the “bridge” or sent his letter from some cafe or other public place, it would be difficult to track him. But he used the university's network, connecting to it from the student dormitory. Therefore, they were able to find this 20-year-old boy named Eldo Kim, who, as it turned out, in this way wanted to achieve the abolition of exams.
At the same time, 10 students used the TOR network at the same time, and when the FBI began to interrogate them all, they found enough evidence against Kim and he had to admit what he had done.

The following lessons can be learned from this case:
- do not be the only one who uses TOR in a controlled network at a given time;
- use the "bridge";
- do not confess anything;
- correlation attacks are a preparative thing.
In a second I will talk about a bit more correlation attacks. First, consider a correlation that compares the end point with the traffic exit point. The meaning of such an attack is that you monitor traffic and see what happens on the network. Of course, everything is encrypted here, but if you look at the request of 5 MB in size, which is sent from the client’s computer to the server, you can see interesting things. This computer with a lilac screen under the server is an observer who “sniffs out” network traffic.

He sees that the server receives a request of 5 MB, and the answer comes back with a volume of 8 MB already, because it is “stout” due to encryption keys. Then you can compare the time during which the request was sent and the response received, and identify the computer from which the request was sent.
You can use the timing correlation to track the path of traffic between computers on the network. At the same time, a DDoS attack is used in order to change the load along the traffic path, which allows you to track the path between the network computers.

You can also generate your own traffic to create your own “pattern” of its passage and thus “ring out” the computers of the network through which it passes. This way, you can find out who is talking to whom and through what servers — first, with a DDoS attack, we “crash” one server, look at which machines have left the network, then “crash” another and so on. The NSA used a project called Maloney, which applied this method of monitoring the TOR network.
You can also monitor the activity of the DNS server and monitor the leakage data. If I do not use a proxy for DNS, and by default it is, then I can send a request to a DNS server. He cannot see where and where my traffic is coming from, but he can see which sites I visit and determine the IP address of the TOR node.

Next, consider case number 1 - LulzSec, a branch of the hacker group Anonymous, the case of Hector Xavier Monsegur, or “Sabu”. Usually he used TOR to connect to the IRC chat, but once he was too lazy to launch TOR, used an open network and got caught by the feds, after which he was forced to cooperate with them for 9 months. Hector used IRC to communicate with Jeremy Hammond, and this fact was used to arrest Hammond in 2012.
If you use this chat, always use anonymity, because a person who owns an IRC server can easily get your IP address and find out who you are. One of the members of the anonymous traffic in the UK, who owned the server, got angry at his friends and began to “drop” their IP addresses to the public.
Hammond under the nickname sub-g used TOR, so it was not possible to decrypt its messages. But the MAC address of his computer was fixed on this network, and the FBI correlated the time of his conversation with Sabu via IRC. They found that sub-g and Hammond were online at the same time, that Jeremy was at home at that time and his computer was connected to that network. They had gathered enough evidence of where Hammond got access from, they also had IRC chat messages that Sabu gave them, and so on. More information about this can be found at the link .
From this case we can draw the following conclusions:
- Use the TOR network all the time, not from time to time. The fact is that your browser stores cookies, and if you’ve been to a website and then open it again without using TOR, the browser will send it your cookies again. So they can be easily intercepted and find out who you are. TOR is also good because it does not store cookies and clears the entire history when you turn it off;
- Do not give personal information to anyone, because if you share a whole bunch of data with someone who can be arrested, you too can be arrested;
- as I said, remember that correlation attacks are a preparative thing.

Next, consider case # 2 - Freedom Hosting provided mail services to customers within the TOR network, that is, allowed them to create their own mailboxes within the anonymous network. They, among other things, were used to distribute child porn, although they mostly served simply to exchange letters between users. It is because of child porn that this hosting in 2011 was attacked by Anonymous during the operation of “sweeping” Darknet.
In particular, the Lolita City site hosted by Freedom Hosting was subjected to a DDoS attack, as a result of which Anonymus hackers were able to publish in public access a whole list of its users. In July 2013, the FBI compromised several Freedom Hosting mailboxes and injected malicious JavaScript code into them that used the vulnerability of CVE-2013-1690 version 17 ESR of the Firefox browser. As you know, the TOR software package is based on Firefox. Its developers have released a patch that fixes the vulnerability, but many Thor users, as usual, have not updated their on-line browser version in time.

This vulnerability allowed the FBI to gain control of the Freedom Hosting mail by deploying an exploit called Magneto. It is a tiny Windows executable. Magneto searches for the victim's Windows host name and MAC address of its computer and sends the information back to the FBI server in Virginia, exposing the victim’s real IP address. The script sends back data with a standard HTTP request outside the TOR network. Details can be read on the link .
This project is similar to a project called Egotistical Giraffe - a tool that the FBI used against TOR users through vulnerable software on their computers. Magic Lantern, FOXACID, and CIPAV, the verifier for Internet protocol and computer addresses, also belong to similar spyware used by the feds.
As a result, the FBI was able to destroy Freedom Hosting, arresting for distribution of child pornography of its owner, 28-year-old citizen of Ireland and the United States, Eric Wan Marques. He was able to connect with the server Freedom Hosting thanks to payment documents. He bought something, and the purchase information with reference to his real IP address remained in his mailbox Freedom Hosting. When the security services arrested him, he rushed to turn off his laptop so that when reloading, the data encryption system on the hard disk was activated, but he did not succeed.
The following lessons can be learned from this case:
- Never mess with hosting related to Captain Picard or Julian Bashir. If you are familiar with the 4chan culture, then you know what these two nicknames denote - the first is abbreviated CP, or “child pornography” (child porno), and the second - JB, or “jailbait”,
update, update and update again . If all these people had just installed a patch with the “patches” of the Firefox vulnerability, the FBI would not have been able to inject the Magneto explorer into TOR. Now, if you are using an outdated version of Torah, a line appears at the top with an invitation to update it; - Do not let yourself be tracked by your “bills”; do not use mail to store payment documents that contain your personal information;
- Leave your laptop in an encrypted state when not in use.
Make the hidden server contact you to determine its real IP address and find out if it is exposed to any vulnerabilities for various attacks, for example, buffer overflow, etc.

This is necessary in order not to screw it up and not fall under the supervision of the feds, by contacting such a server within the TOR network.
Case number 3 concerns the well-known Silk Road, or Silk Road. This market Darknet was ruled by the pseudonym Dread Pirate Roberts, or "The Terrible Pirate Roberts." This was an electronic platform for buyers and sellers, where they traded, let's say, not a completely legal product. The materials of the Silk Road case file as of September 23, 2013 show that about 13,000 lists of goods were posted on the TOR network and were posted on the site and related to such requests as “marijuana”, “ecstasy”, “intoxicants”, “opioids , Precursors, psychedelics, and similar drugs. In short, it was Charlie Sheen's dream.
Also on the TOR site, 159 sites were found that provide services for hacking accounts of various networks at the request of the client, including Facebook and Twitter, so that the customer would be able to control and change the personal information of the account owner at will. It also posted 22 tutorials on hacking ATMs, as well as contacts of providers of illegal services such as “anonymous bank accounts”, “counterfeit accounts in CAD / GBP / EUR / USD currency”, “sale of firearms and ammunition”, “stolen information of bank cards and PayPal accounts "and even" hired killers in more than 10 countries. " The only thing that was not offered for sale or was not found on the network was fake diplomas, certificates, medical prescriptions and fake money. Apparently, the site owner had problems with this.
After the volume of transactions reached 1.2 billion dollars, the FBI became interested in the Silk Road. First of all, they began to check the very first links to Silk Road on the public Internet, using Google search queries, changing time intervals. They found the earliest link to this resource on the small site of addicts Shroomery, where the guy under the nickname altoid posted a link to the Silk Road page on the TOR network.

In essence, he advertised this site, stating that on the Silk Road website you can anonymously purchase anything you want. This post was posted on January 27, 2011.
Then, on the site bitcointalk.org, someone opened the topic “Heroin Store”, and the user under the nickname ShadowOfHarbringer wrote that Silk Road may not be selling heroin, but this is the first marketplace where you can buy all other drugs for bitcoins anonymously. This also sounded like an advertisement for this resource, and this user ended his post with the phrase: “guys, let me know what you think about it!”, Hinting at feedback.
Thus, the feds found that the “Silk Road” really exists and works. Later, in October of the same year, on the same site bitcointalk.org a character familiar to the Shroomery site under the nickname altoid appeared, who opened the topic “I am looking for a professional IT specialist to open a bitcoin start-up”, where he wrote that interested persons can contact him to the specified email address. And you know what he did? He wrote the address of his mailbox, registered in his real name and surname - Ross Ulbricht, rossulbricht@gmail.com. This is called a complete failure of the OPSEC principle.

Therefore, the FBI did not find it easy to establish a connection between altoid, the first mention of the “Silk Road” and bitcoins. The altoid email was the same as Ross. Ulbricht’s profile on Google+ showed that he is interested in the libertarians of Ludwig von Mises, “the world center of the Austrian School of Economics”.
Then they found out that the Dread Pirate Roberts signature on the Silk Road forums contained a link to the Moses Institute, and the Austrian economic theory had a great influence on the Silk Road philosophy. In addition, from Ross Ulbricht account, an entry was made on StackOverflow with a request to help him in writing PHP code to communicate with the hidden TOR services.
True, this account was quickly replaced by “frosty”, but the first username corresponded to his real name and last name. The combination of this evidence allowed the FBI to obtain an arrest warrant for Ulbricht and left no doubt that Ross William Ulbricht and Dread Pirate Roberts are one and the same person.
I would probably also not hide my true face if I earned 1.2 billion dollars. The feds also found out that someone was connecting to the Silk Road host server from an Internet cafe located next to Ross’s apartment in San Francisco. Letters addressed to Pirate Roberts revealed that he lived in the Pacific time zone.
The IP address of the Silk Road server was connected to a VPN via an IP address owned by an Internet cafe on Laguna Street in San Francisco, and from there at the same time, on June 3, 2013, Ross logged into his mailbox on gmail.

In a private message to Pirate Robets, one of the users wrote that he discovered a leak of information from the site through an external IP address belonging to the VPN. Then the FBI somehow managed to capture and copy the images of the hard drives of one of the servers of the Silk Road. Presumably they paid hacker Nicholas Weaver to hack Silk Road and connect it with an external server that did not use Thor to reveal the real IP address of the Silk Road server.
On July 10, 2013, the US Customs Service intercepted 9 IDs for different names, but all of these documents contained a photograph of Ross Ulbricht. The security service interrogated Ross, however he denied that he ordered the production of these certificates, and refused to give any comments on this matter. It was very reasonable of him. But then he did something stupid, stating that, hypothetically, anyone could go to the site called “Silk Road” or “TOR” and buy drugs or fake documents there. Why did he need to talk about it at all, if, as a good citizen, he should not have known anything about it?
However, private correspondence showed that Dread Pirate Roberts was interested in buying fake IDs.
Then, one of the servers of the Silk Road used SSH and private keys that contained the entry frosty @ frosty. This server used the same code that was once hosted on StackOverflow. Finally, on October 1, the FBI arrested Ulbricht in the public library just after he entered the password into his laptop. A lot of incriminating evidence was discovered in the laptop.
Further information on this case can be found in the article by Nate Anderson and in the documents that Agent Christopher Tarbell submitted to the court. They are located on the links ( one and two ).
The following lessons can be learned from this case:
- use the separate identification of your person in the network, never use the real names, use different user names and log in from different places,
create a consistent legend in which there would be no contradictions for which you can catch on. Do not use the old nicknames, as Ross did with the name "Josh," by which his fellow students and roommates knew him; - do not discuss your interests with anyone and do not post questions or requests for help that are publicly interested;
- Do not give any voluntary admissions or assumptions like: “anyone can buy these things on the Silk Road”.
So, we have a little time left to tell you how the de-anonymization of TOR users works and show you several ways to reveal the anonymity of the user.
First you need to configure the proxy on the local machine. Then you access something on the TOR network, and I want to convince you to go to a specific site and download the Word document called track.docx from there, that is, follow the link .

Now I'm trying to connect to the TOR network, it depends on how your browser is configured, because it may not allow the use of proxy connections. So, TOR has started, and now I need to follow the link to a specific site and open the document track.docx.

It is a trap. You see the TOR greeting and the loaded document lines on the screen. That's it, you opened this document on your computer.

Now I go to my irongeek.com website, open a log of logs and see the real IP address of the computer on which this document was opened, the opening time and the characteristics of the browser used.

What else can I do? Ask the user to download the archived credit_card.zip document containing a bunch of stolen credit card data. After he does this, on my screen on honeydocx.com/hive/sting/4254/buzz I will be able to see who opened this document and its real IP address.

To open the buzz, I need to enter my username and password, which I registered on honeydocx.com. I do this and everything is ready - you see the IP address and location coordinates of the user who opened credit_card.zip.

I showed you what happens if people use TOR, but do not set up a proxy connection properly in the browser.
There are more professional tools than me, since I use documents of different formats, after opening which my exploit is launched on the user's computer.
The next thing I can do to fool a user is to install a hidden service. On the screen, you see the OWASP Mutillidae II is a deliberately vulnerable open source application that serves various security threats. If you open the menu, you can see the types of attacks that can be experienced, for example, SQL injection. In this application, you can demonstrate the pinging attack of an IP0 address using the command line, see who returns me a ping, and determine its IP address.
Then you can view links to unsafe objects and do many more such things. In this application, TOR starts up very slowly, so I can’t demonstrate how it works, I have too little time left to speak. Let me just say that the main idea of the command line injection is that you can see who ping returns you. Asking whether I can determine the IP address on the VPN in this way, I will say yes, it is possible.
If you want, you can view a detailed video about it on my site by the link .
Thank you for attention!
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
