SourceFire FirePower next-generation firewall and intrusion prevention system overview
Good day dear readers. In this article, I would like to introduce you to Cisco's flagship information security solution.
We are talking about the product SourceFire Firepower, which is an integrated system of intrusion protection, a new generation of firewalls and protection against Malware.
SourceFire was acquired by Cisco in October 2013, and its solutions are currently the leader according to the Gartner rating agency in the field of intrusion prevention systems.
About SourceFire
A few words about SourceFire. The company was founded in January 2001 in the state of Colombia by Martin Roesch, creator of the world-famous open source intrusion prevention system Snort IPS, which is currently the most widely used IPS system in the world (more than 4 million copies are currently downloaded) . In addition to Snort, the company is developing such well-known opensource products to the community as ClamAV and Razorback. In addition to the very successful opensource projects that the company is very proud of, the company’s commercial product is also developing under the SourceFire trademark, which has earned its place as a leader in the field of intrusion detection and prevention systems in the information security market according to the results of the Gartner rating agency (unchanged leader for the past 6 years!),others . A separate group of experts, the VRT team (Vulnerability Research Team), is responsible for developing the rules for detecting attacks and updating them in a timely manner. SourceFire’s commercial line consists of two products:
SourceFire FirePower is a next-generation intrusion prevention system with integrated application-level firewalls, content filtering, and Malware protection at the network level.
SourceFire FireAmp - a system of protection against Malware threats at the host level, running Windows / MAC OSX, Android. It can integrate with Malware protection at the network level - SourceFire FirePower.
Overview of FirePower Platforms
The product is presented in two deployment options: in the form of a 64-bit virtual (VMWare hypervisor) and hardware systems. The functionality of the virtual platform does not support routing, switching, and fault tolerance functions. At the same time, the virtual appliance works fine as an Inline bridge or IDS system on the SPAN port.
A large number of hardware models are available with different performance, modular interface cards, stacking and clustering functions. Model performance starts with the lowest rulers - 50 Mb / s, ending with solutions of the class of large data centers - 60 Gbit / s (Fig. 1).
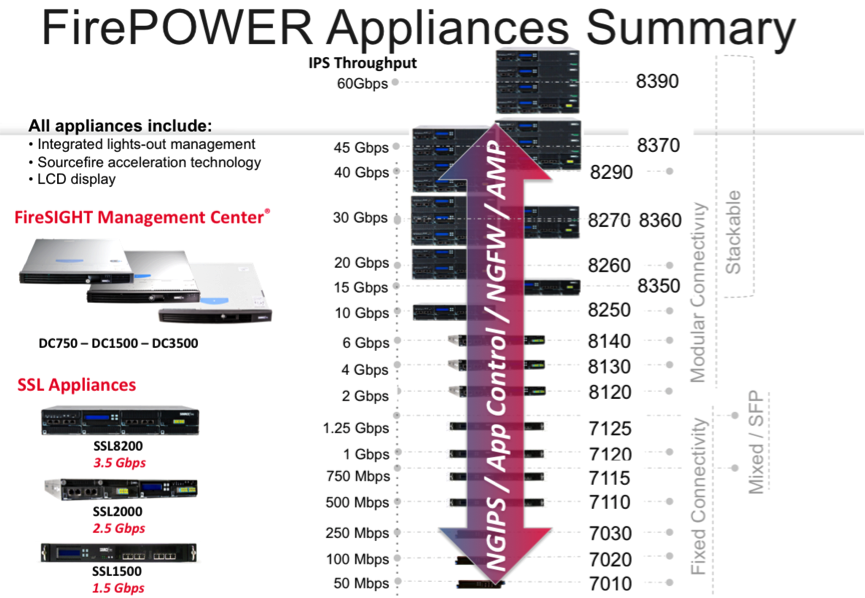
Fig. 1 The
performance of the virtual model is 100-150 Mb / s per core.
The 7000/7100 Series models have RJ45 / SFP ports fixed on board, depending on the specific model.
The 8100 Series models have modular interface cards with the supported interface types 1 Gbit / s copper / optics and 10 Gbit / s optics MM-SR and SM-LR. The 8200 and 8300 Series also support 40 Gb / s MM-SR optical interfaces. Most interface modules have the ability to configure hardware bypass (including optical) in case of failure of the device.
The older FirePower 8200/8300 range supports the flexible stacking performance feature. For example, you can buy a 8350 sensor with an IPS performance of 15 Gb / s (30 Gb / s platform performance) and at the time when you need to increase the system performance, just buy another 8350, stack them and get a 30 Gb / s IPS performance, and so This way you can stack up to 4 devices with IPS performance up to 60 Gb / s.
Fault tolerance functions are implemented through clustering of complexes into an Active / Standby bundle with synchronization of session statuses.
FirePower hardware solutions are built on the RISC architecture, optimized code and a powerful computing platform with specialized network processors make it possible to achieve and exceed the performance declared by the manufacturer. The claimed performance characteristics are real performance figures that the customer will receive during heavy load tests with the functionality fully turned on. This fact is confirmed by annual tests of NSS Labs.
Defense Center Management System
FirePower is built using a centralized management system - Defense Center. Locally, only the initial settings are available on the FirePower complexes themselves, which allow you to connect the device to the network and configure communication with the control center. All further settings, reporting and monitoring are done centrally in the Defense Center admin console.
Defense Center is presented both in the form of hardware platforms (see Fig. 2) with a maximum number of connected sensors - 150 pieces, and as a virtual machine for a VMWare hypervisor with a maximum number of sensors - 25 pieces.

Fig. 2
The control system in its hardware version has fault tolerance functions for the DC1500 and DC3500 models.
Available Deployment Topologies
For the virtual sensor, configurations of both Inline allocation (see Fig. 3) with inspection and filtering of active traffic are available, as well as placement in IDS mode on a copy of traffic (SPAN) (see Fig. 4).
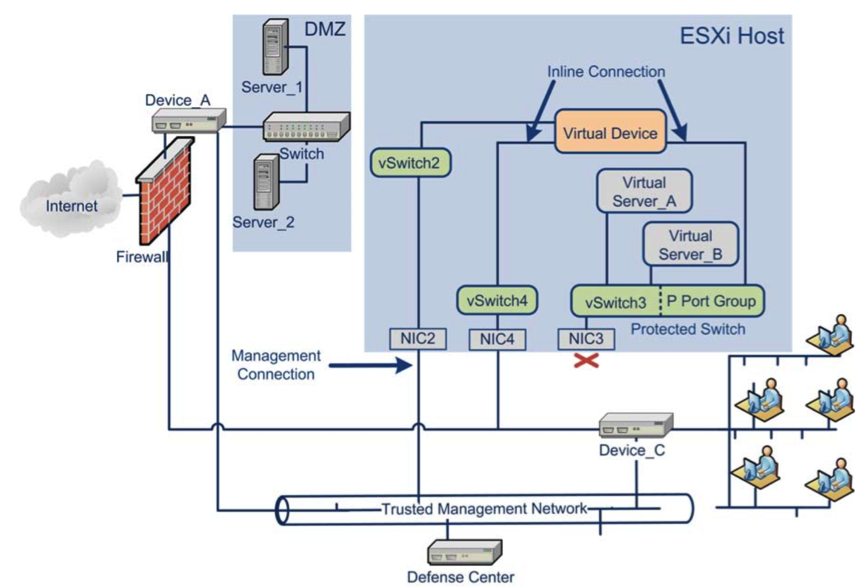
Fig. 3
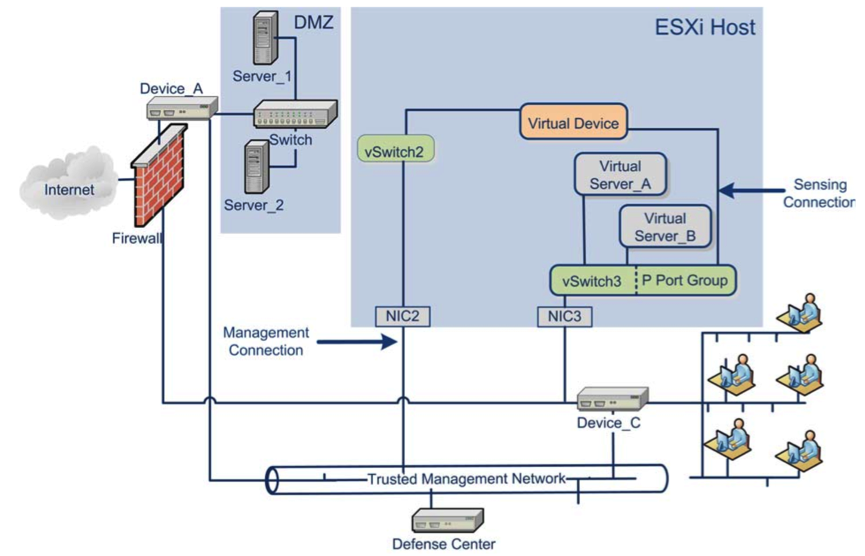
Fig. 4
In the case of using the hardware platform, more complex topologies become available to us, since the hardware systems support hardware-level switching functions with Spanning Tree Protocol (STP) support and have routing functions using OSPF and RIP protocols.
The platform allows you to build hybrid topologies (see. Fig. 5).
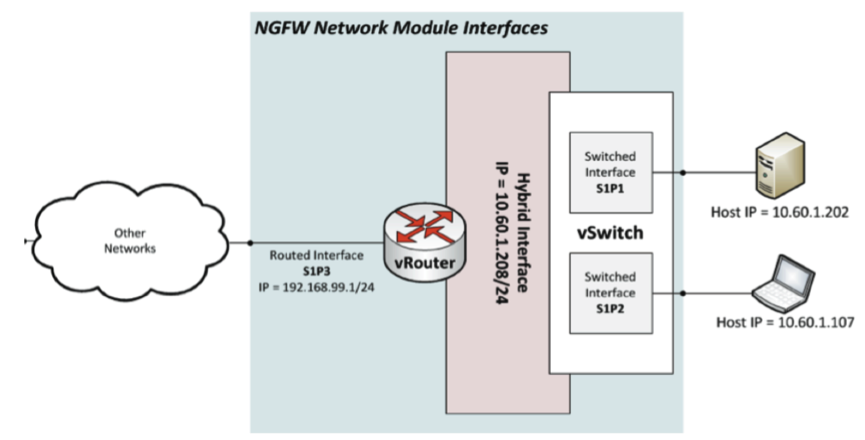
Fig. 5
For the IPS engine to correctly handle asymmetric traffic flow in the customer’s network, the concept of Inline Set is introduced, for an example of such a configuration, see Fig. 6.
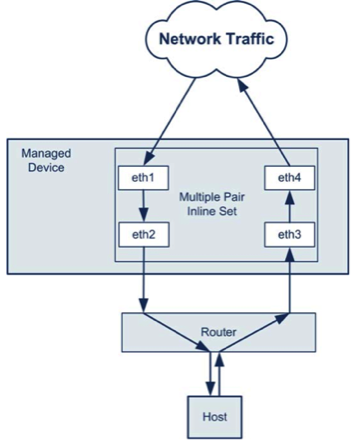
Fig. 6
Let's not forget that many interface cards make it possible to configure bypass in the event of a reboot or a failure on the platform, thus avoiding interruption of services on the network. FireSight
functional review “ You cannot protect what you don’t know ” is one of SourceFire’s slogans and it’s hard to disagree. Having huge corporate networks in management, the information security service is finding it increasingly difficult to track the emergence of new vulnerabilities on company resources such as:
It is becoming increasingly difficult to monitor all these and other changes with the growth of the network, and every day the process of tracking incidents and the response to them takes more time, and the effectiveness of the fight against real threats is reduced. It is good if periodic active scanning for vulnerabilities is carried out by the IS team, but in addition to scanning, it is necessary to block the possibility of using detected vulnerabilities on the side of the intrusion prevention system. Unfortunately, practice shows that the vast majority of administrators are not able to perform tuning of the IPS signature set as often as required by a changing network. After all, to assess the level of the possible implementation of an attack on a target is possible only by understanding whether the target is vulnerable to this attack, and for this you need to know:
But what if CIO itself can sit behind the attacked host ?! Knowing all these and many other characteristics of attack objects or possible attack objects, it is possible to more effectively filter non-hazardous attacks and block really dangerous intrusions with the necessary escalation.
SourceFire is fundamentally different from competing solutions, including in its approach to the analysis of characteristic vulnerabilities in a protected network with the ability to automatically fine-tune the signature set ! The technology under the brand name FireSight allows you to visualize the network and gain visibility (see Fig. 7):

Fig. 7
The sensor analyzes traffic that is actively passing through it or traffic from the SPAN session, looks at the traffic headers down to the application level and, based on the collected data, builds a “map” of the protected network with all its characteristic vulnerabilities. This map is updated in real time. Settings allow the complex to activate / deactivate signatures in active signature sets that correspond to detected vulnerabilities in the network. Testing the 2014 NSS Labs Datacenter IPS results in 99.4% attack blocking efficiency and 100% protection against evasion techniques.
In addition to passively analyzed traffic, the solution supports the upload of the results of active scanning into it, for example, from Nessus.
As an example of the information collected, I will give a profile of one of the hosts (see Fig. 8,9,10,11).
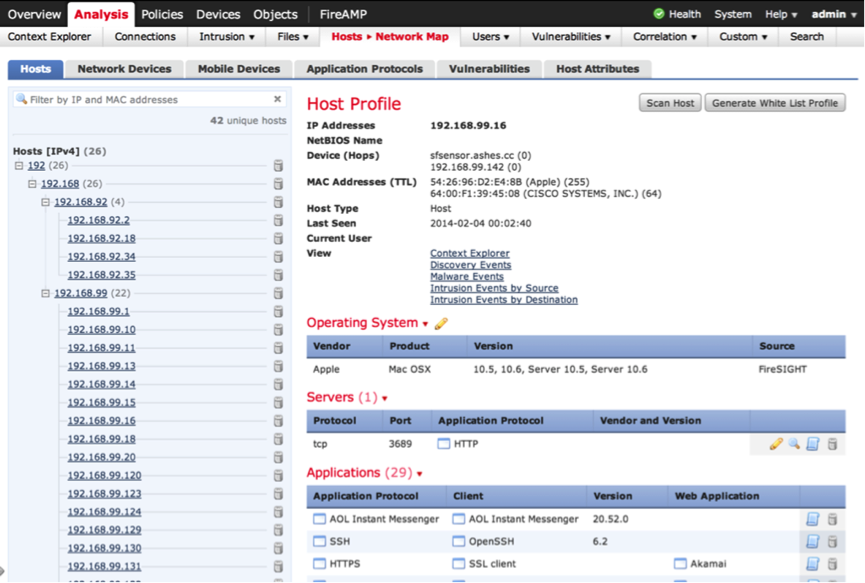
Fig. 8
List of applications on the host:
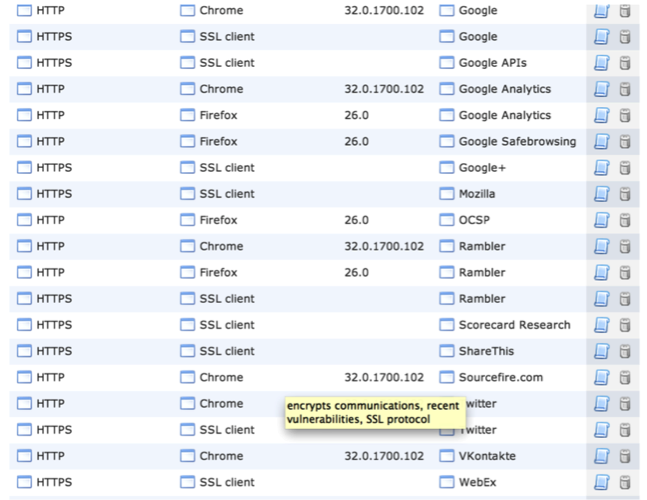
Fig. 9
List of vulnerabilities on the host:
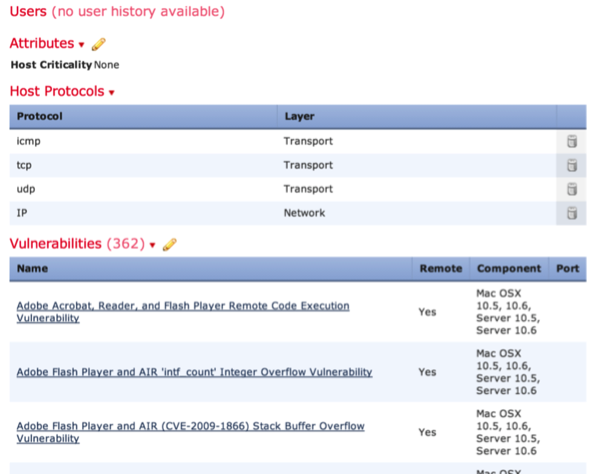
Fig. 10
An example of a description of one of the identified vulnerabilities with links to patches:
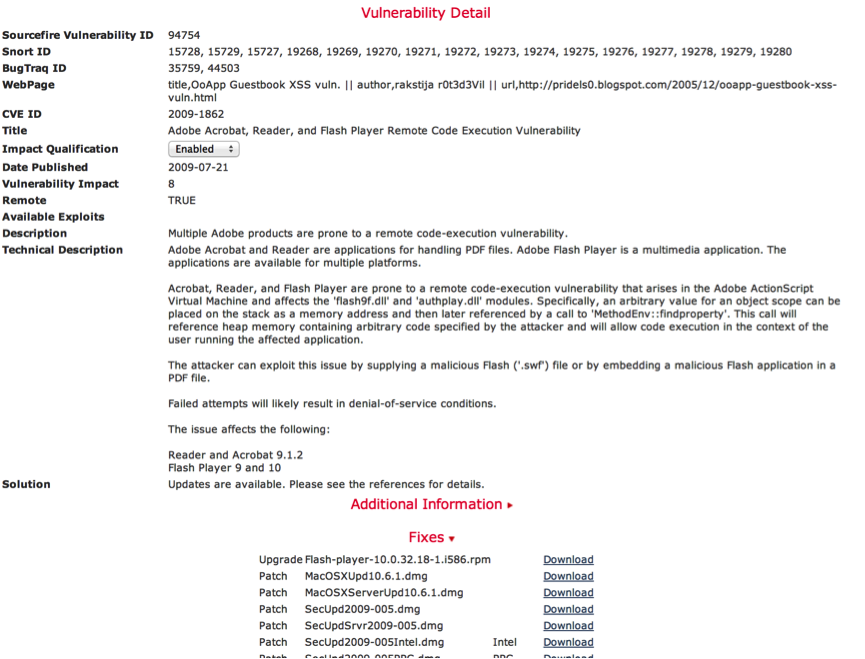
Fig. 11
An example of recommended changes to the signature set based on the analysis of vulnerabilities and systems in the internal network is shown in Figure 12.

Fig. 12
Next-Generation Firewall (NGFW)
A new generation of firewalls, as it is now commonly called, content ITU application level is implemented in SourceFire FirePower and uses signatures for determining the types of applications provided by the intrusion detection engine. NGFW is designed to perform filtering not only at the port and protocol level, as it is classically implemented in the ITU with statefull inspection, but at the protocol level of the application level and the functions of the applications themselves, thus looking deep into transactions and stopping, for example, such activities like transferring a file via Skype or accessing the games feature on Facebook (see Figure 13.14). Note, for example, that Facebook and Google work through the protocol of the 7th level of the OSI model - HTTP. However, these “portals” provide a huge amount of functionality in the form of web applications,
NGFW Access Policy:

Figure 13
Example of Skype File Transfer blocking rule:
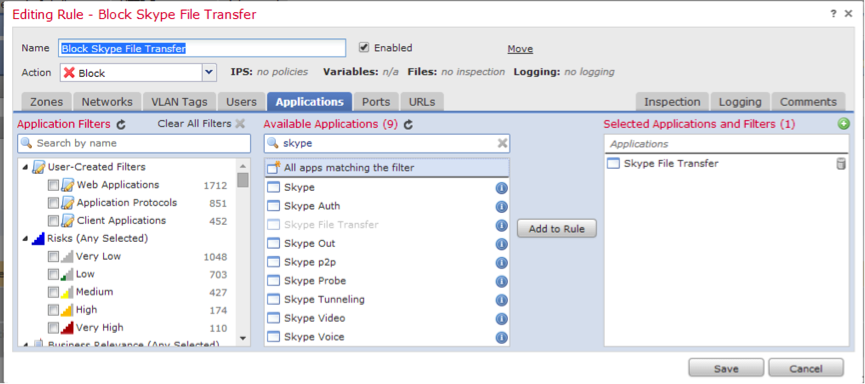
Fig. 14
As can be seen from Figure 13, we formulate our application filtering policy and intrusion detection policy in the access policy. Each line of the access policy acts as an Access Control List entry that governs the access rule with the appropriate conditions.
ACL conditions can be of the following types:
All these conditions can simultaneously appear in one rule and will be used as a logical AND.
After each ACL, you can see three icons (see Figure 15), which mean associated policies from left to right:

Fig. 15
If your own network contains applications of your own design and they are not in the application database for filtering, you can easily add your own application to the application database. Import the appropriate Pattern ASCII / HEX for searching, or download an example of network activity of the application from a PCAP file.

Fig. 16
For each access policy, which can be many, you can assign a Security Intelligence filtering policy (Fig. 17). This policy contains constantly updated lists of IP addresses of spammers, C&C botnet centers, open proxies, etc. You can choose from the available lists, or load your own filter lists from a file, or indicate to the system the URL where to get these lists from.
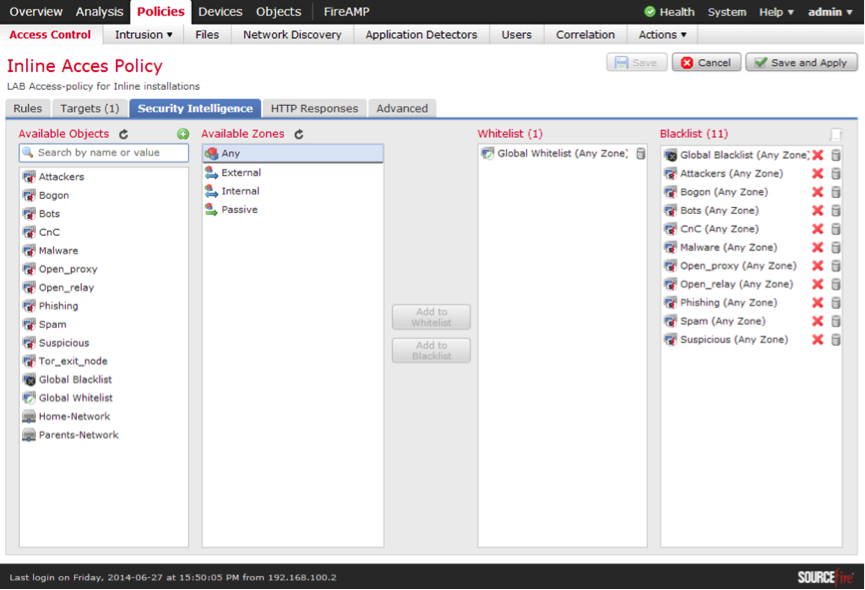
Fig. 17
FireAMP Malware Protection
FirePower solutions provide Malware protection at the network level. The system analyzes the files transmitted through the device specified in the file policy (Fig. 18) formats and transmitted through the specified types of protocols. You can read about the features of the Malware protection solution in an article by Alexey Lukatsky ( alukatsky ).

Fig. 18
The principle of protection against Malware is as follows. The SHA-256 hash is removed from the file sent through the device and sent to the Defense Center, which in turn makes a request (Cloud Lookup) in the SourceFire cloud, figuring out the location of this file (whether the file is clean or Malware) using the cloud base of the well-known Malware . For customers who do not want to send any data to the cloud, the server with the Malware base can be deployed directly to the corporate network, this configuration is called Private Cloud.
If, based on the results of removing the hash and the request, the file cannot be set to the database, the file can be sent by the device to the cloud “sandbox”, where the file’s behavior, its survival after reboot, generated network traffic, and testing to run in a virtual environment will be analyzed. , created processes, files, registry entries and techniques for hiding processes, attempts to reproduce themselves and so on. According to the results of this testing, indices of malicious behavior are calculated, a small excerpt of the report is shown in Figure 19.

Fig. 19
In case the file is executable, FirePower removes more than 400 variables from the file (links to connected libraries, library names, used icons, environment variables, compiler settings, etc.) for analysis by the Spero engine using the fuzzy fingerprint algorithm ( Fuzzy fingerprinting). The algorithm, referring to the logical self-learning trees of signs and behaviors of various kinds of Malware, located in the SourceFire cloud, gets a decision on the file disposition.
A very important difference from classical anti-virus protection systems is that classic systems work at a certain point in time. For example, a file is called for execution, it is checked against the signature base and / or sandbox, and it is forgotten after the conclusion about its cleanliness / infection. However, do not forget that every day in the modern world there are more than 65,000 (SourceFire statistics) instances of the new Malware, for which there are no signatures yet. Malware can use launch delay techniques to avoid detection in sandboxes. In view of the above arguments, Malware can bypass the network antivirus and settle on the end nodes, where, over time, the distribution and operation of Malware will begin. The anti-virus will not leave any records about the past file time of its appearance and source. According to statistics, up to 30% of unknown Malware are carried with them and up to 70% of known Malware are downloaded and vice versa.
The FireAMP system provides a new approach with a retrospective analysis, which remembers all the distribution paths of files and their attributes. In the case of a host-based FireAMP solution, all associated process activities, network activities, all I / O operations on the local host are remembered. And when, after 4 days, it turns out that the downloaded file was previously unknown to Malware, a notification will be received from the SourceFire cloud and the file will be centrally blocked both at the network level and at the level of all endpoint infected systems. Moreover, the system will show the distribution path of the file both over the network and in the host system, all additional components and Malware programs downloaded by the file, access to the processes and the parent process, which made it possible to become infected and give rise to the spread of the threat.
Network-Level Malware Detection Example, Figure 20a, 21

Figure 20a
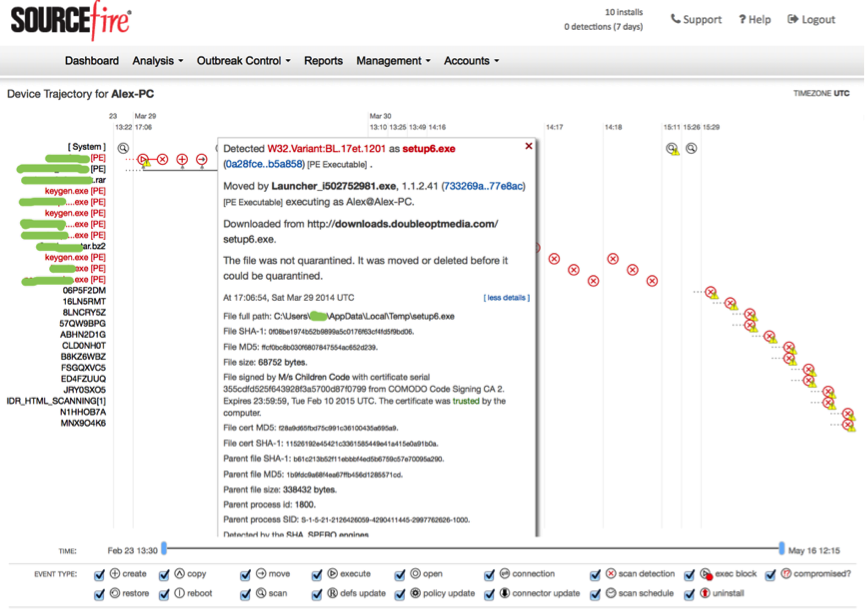
Fig. 20b
In particular, in Figure 21 you can see the path to the file and further distribution of the file over the network, affected hosts, the time of infection, the ports and protocols used.
In Figure 20b, you can see more detailed information about the distribution and method of getting the threat directly to the host with all associated I / O operations.
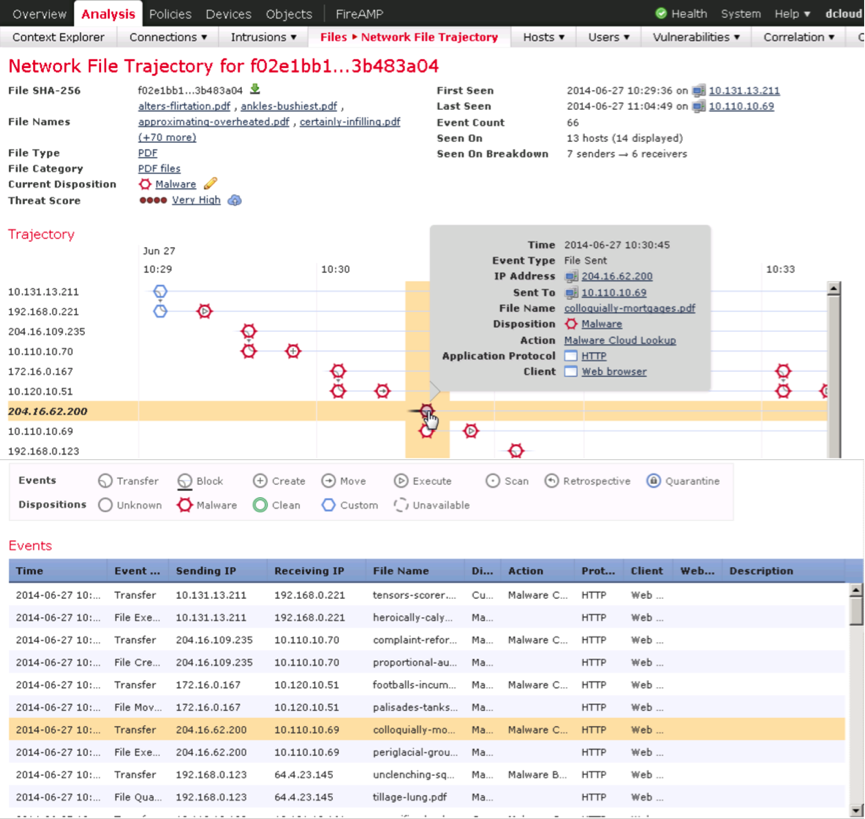
Fig. 21
Compliance Whitelist Function
Separately, I want to note the useful function of the white list of systems on the network. Since FirePower can passively see the activity of users and applications on the network in real time, the system makes it possible to build profiles of Compliant systems. Thus, you can specify which operating systems with which patches, client programs and applications in them we want to see on our network. In case of deviation from the template, you can notify the administrator and use the correlation methods (see the next chapter), including executing your own scripts and commands, and perform quarantine / troubleshooting.
It should be noted that FirePower provides the ability to create and assign attributes to various hosts and expose attributes as a result of the correlation action. You can use attributes when generating automatic notifications, including to increase the level of criticality of an attack, and much more. For example, to increase the criticality level of an attack when it is detected in the direction of the host with the value of the base attribute - non-compliant.
The generated attributes can be of the following types:
By default, each WhiteList has only one attribute, which takes a value:
Each host will have a WhiteList attribute assigned to it with the value of this attribute from the above list.
An example of creating a WhiteList can be seen in Figure 22. You select the allowed types and versions of operating systems, in each operating system, select allowed client applications, web applications, and allowed transport and network layer protocols.

Fig. 22
Traffic Profiles
As you may recall, FireSight technology also monitors the parameters of connections established by hosts on the network. Based on the collected statistics, and at least 29 connection parameters are collected, the so-called basic connection profile for each host is built. In the configuration, you can set which specific types of connections or application traffic will be profiled and for how long to build a basic profile (Example Fig. 23).
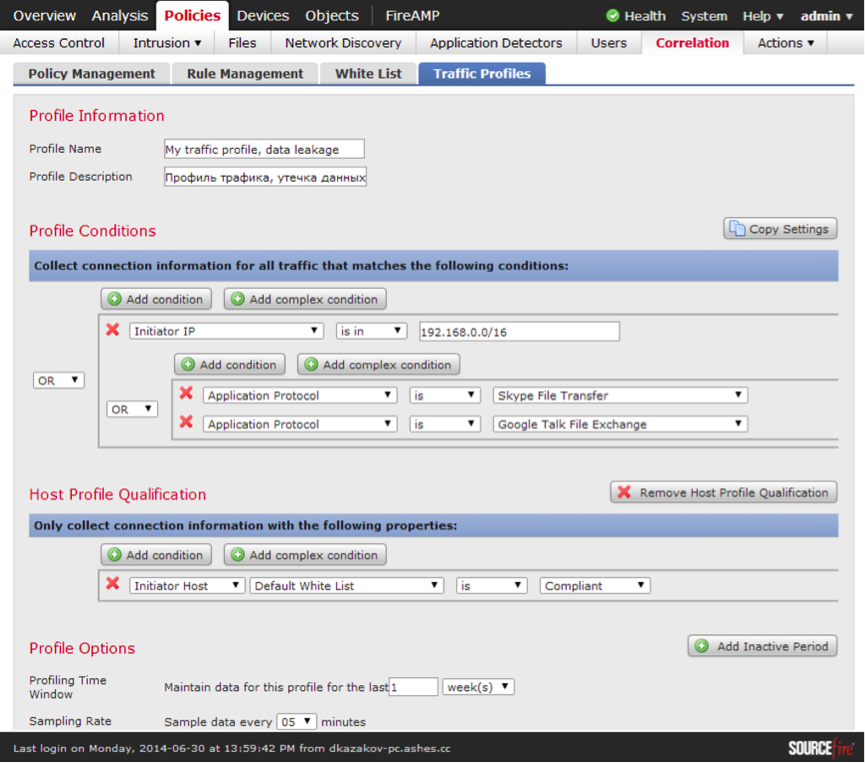
Fig. 23 The
example in Figure 23 shows that it is possible to build profiles on the basis of all transmitted traffic as well as to more accurately select the necessary flows.
Event correlation
A very powerful function for tracking, escalating and responding to events is embedded in the system - this is a correlation function. Especially this function will appeal to enthusiasts and security professionals.
In fact, this function provides an opportunity to set sets of conditions with logical connectives for the generation of reactive action (see the correlation condition in Figure 24 for an example).
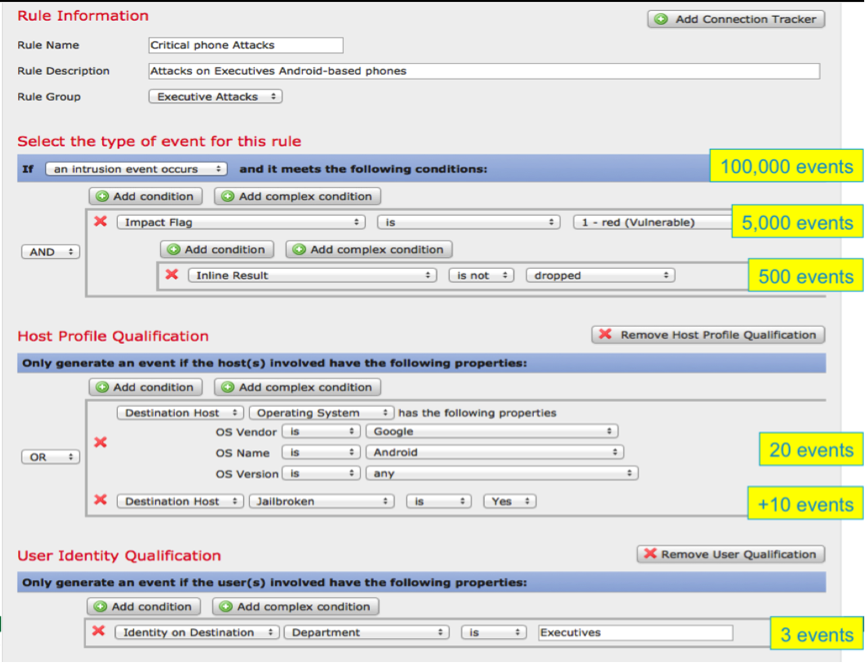
Fig. 24
As a result of applying the above correlation condition, there will be an invasion event:
As a small example, correlation conditions can be created for the following types of events (see Fig. 25, 26):
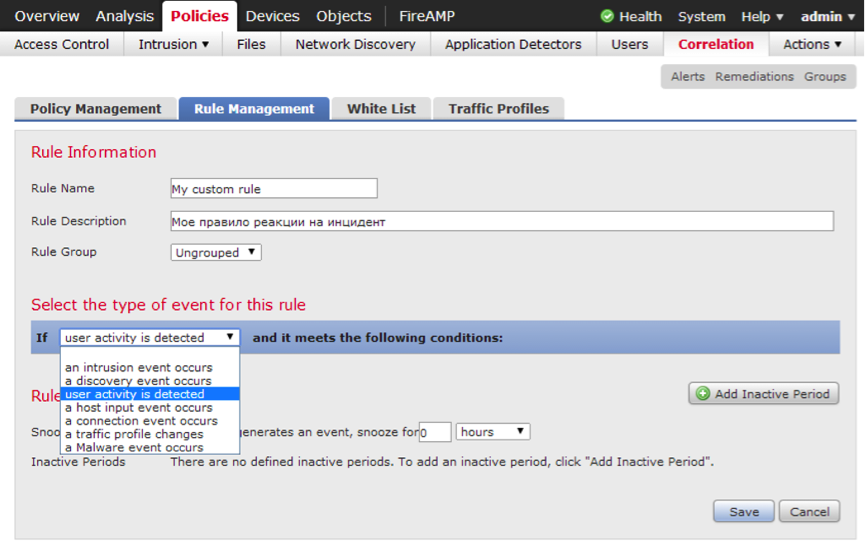
Fig. 25

Fig. 26
We examined the possibility of setting correlation conditions, and now we will see how we can respond to the fulfillment of these conditions.
The result of the correlation rule can be one or more actions, such as:

Fig. 27
Monitoring and reporting
system The Defense Center management system provides very clear statistical information on the system as a whole, as well as the opportunity to delve into the details of detected activities from any schedule.
To familiarize the administrator with the current picture of the use of network services, applications, operating systems, analysis of the relevance of activities to business processes and risks, the primary Summary Dashboard overview screen is available (see Figure 28).
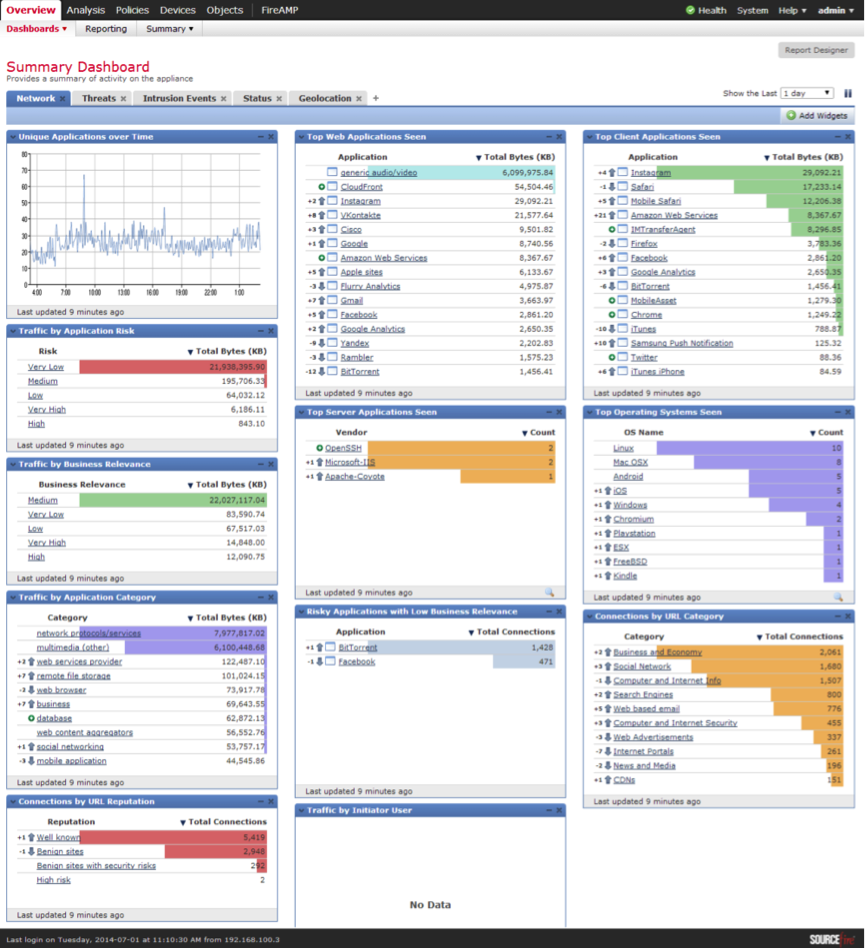
Fig. 28
To begin the analysis of past information security incidents, you can go to the Intrusion Events tab and see aggregated information on detected and blocked attacks, statistics and go on to a detailed examination of each event of interest separately (see Figure 29).

Fig. 29
Each incident can be examined in detail, including the contents of the packet that triggered the signature, see Fig. 30. From the information window about the event you can see the text of the triggered signature, the attack signatures are written in SNORT, which has de facto already become the standard for writing IPS rules for many IS administrators. In the same window, you can perform signature tuning, configure filtering and summarize events, change the action associated with the detection of this activity.
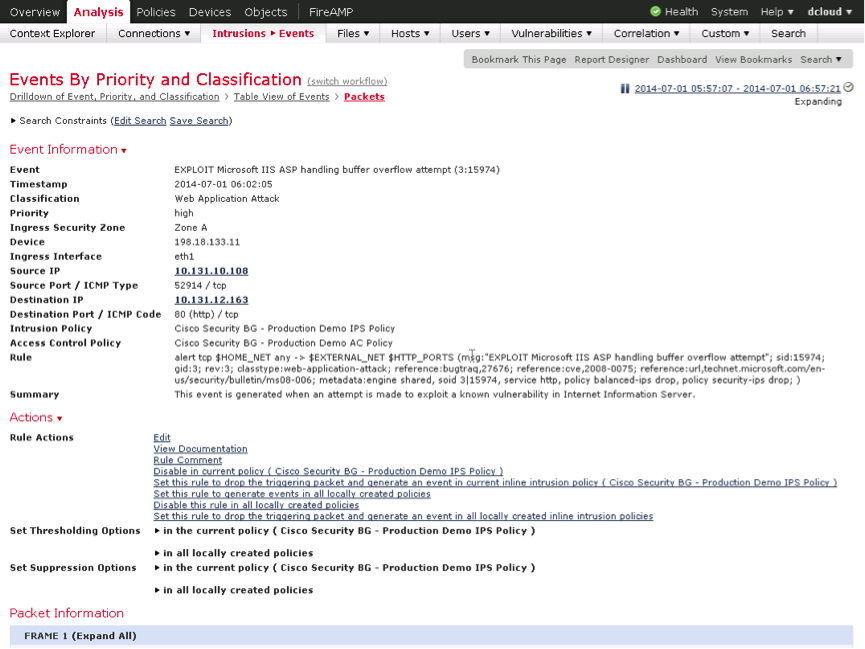
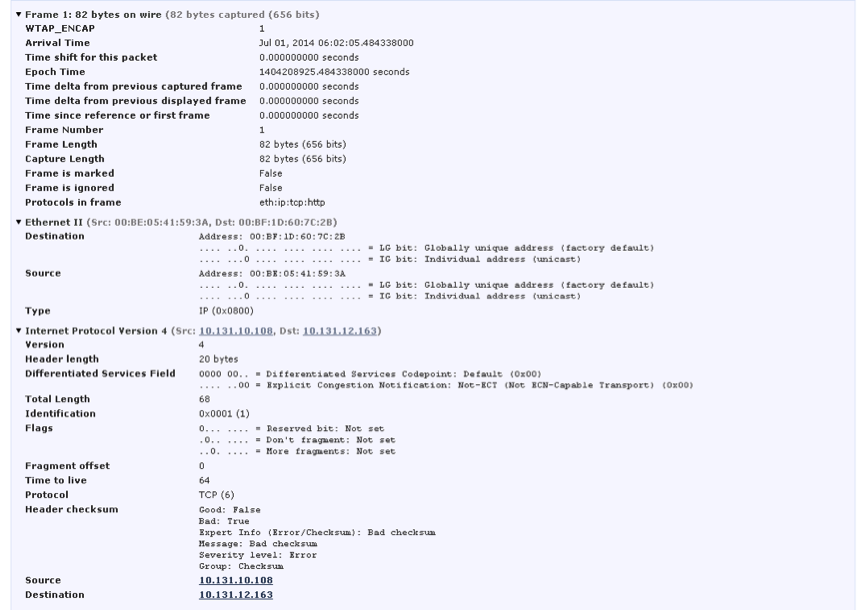

Fig. 30
In addition to information about attacks, you can analyze and filter information of interest that the system receives about the network as a whole. To obtain general information about the network, or, if necessary, about its specific segments, the Context Explorer interface exists (see Fig. 31).
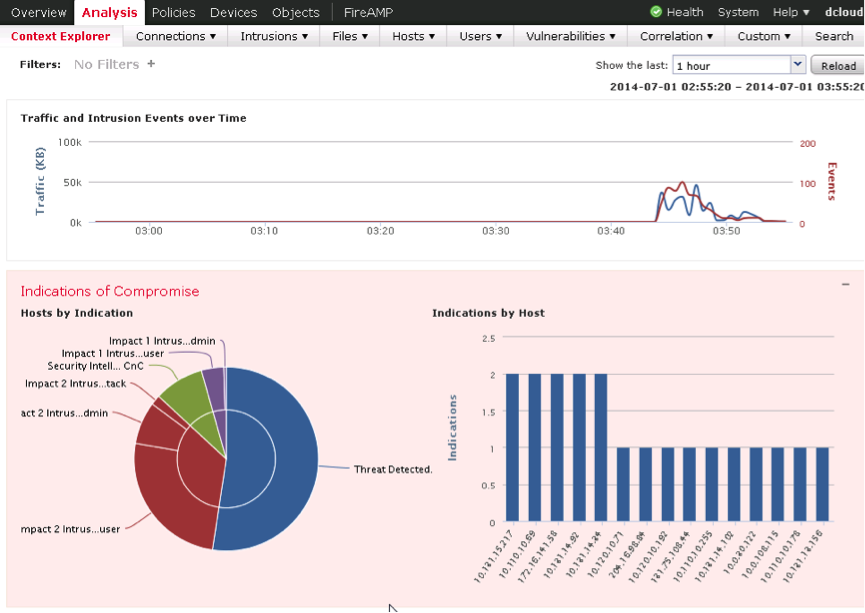

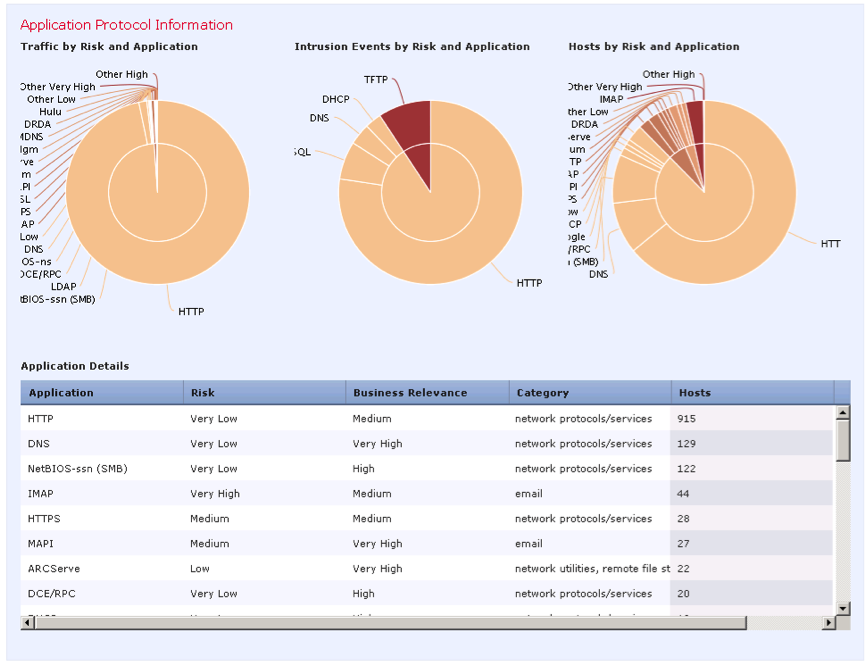
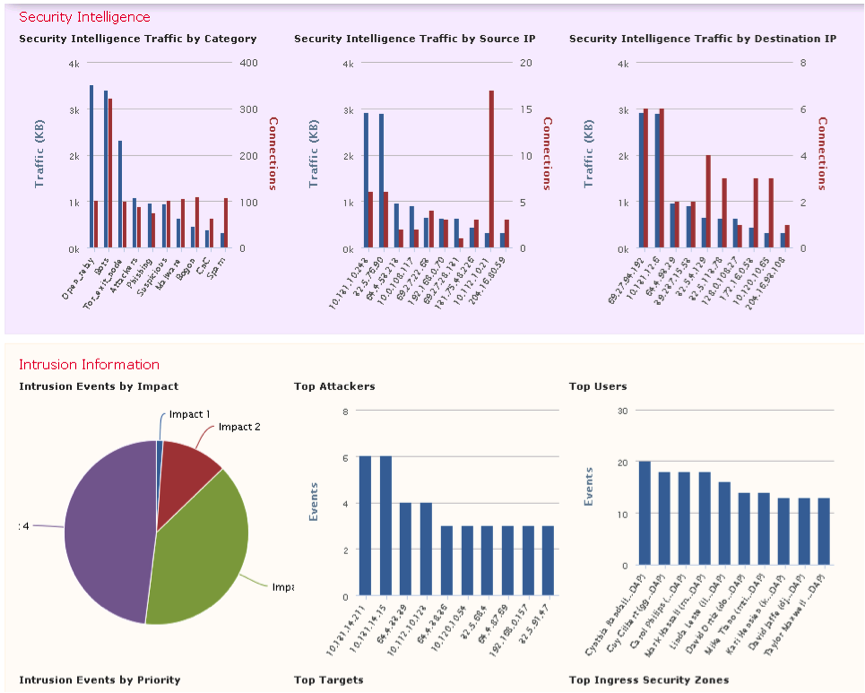
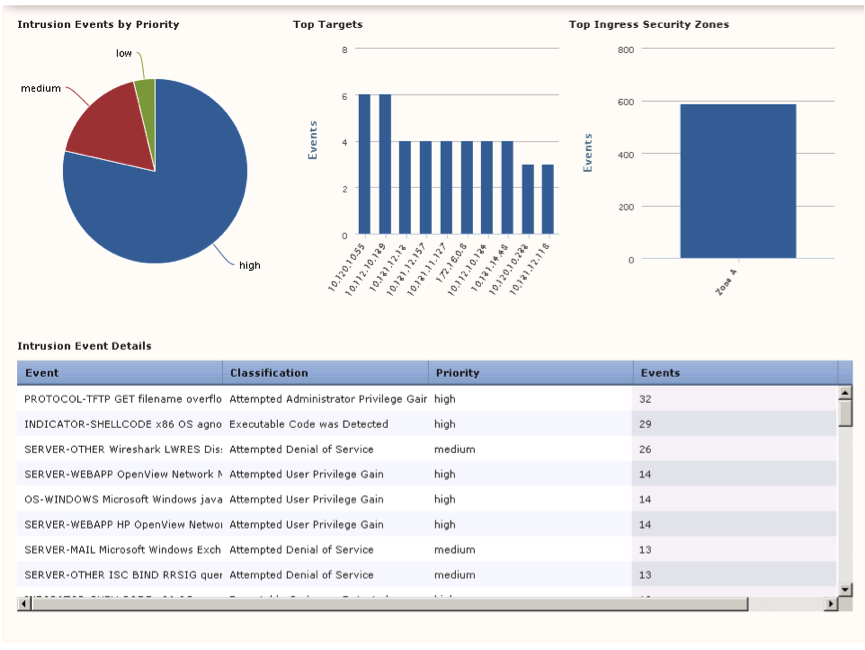
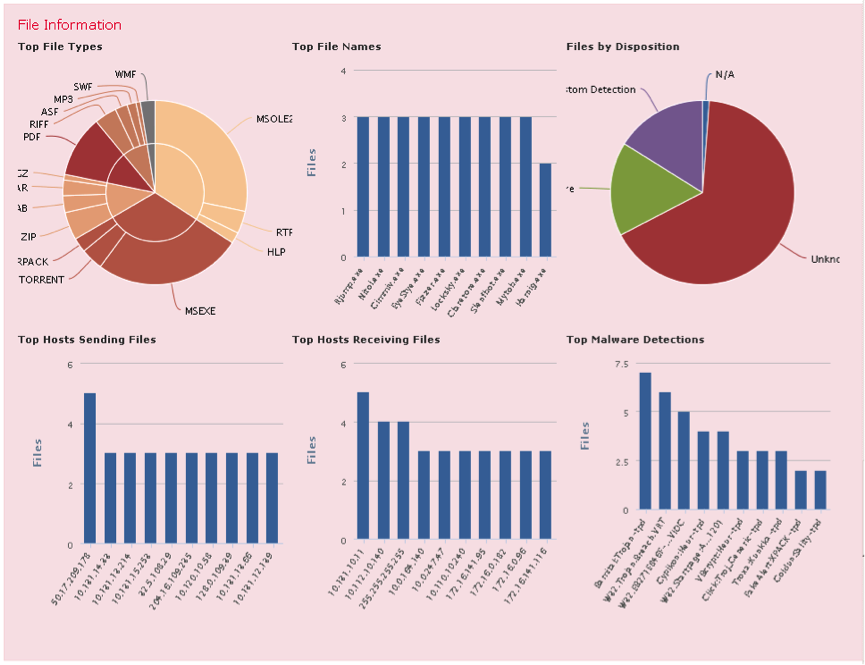
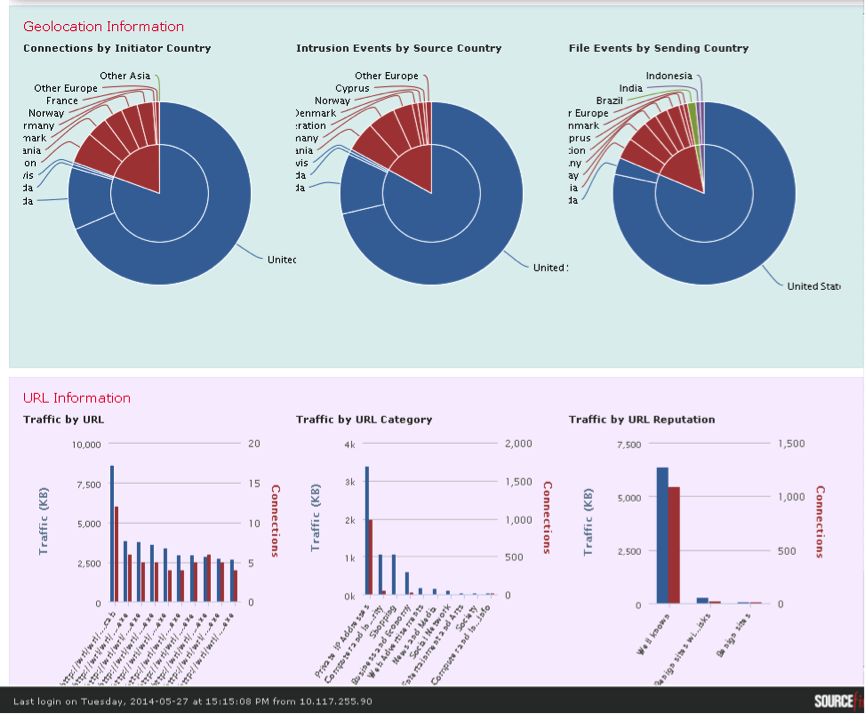
Fig. 31
In figure 31 you can see the statistical information:
The system provides the ability to generate your own reports both according to pre-formed templates, and create templates yourself. To create your own report templates, there is a whole Wizard (see Fig. 32), which allows you to include various types of graphical statistics objects, tabular data and directly the contents of packages with suspicious activity. For the purpose of more flexible reporting, it is possible to set your own variables to substitute them into the template when generating the report. Reports can be generated on a schedule and distributed to responsible persons.

Fig. 32
Conclusion
In conclusion, I would like to note that the comprehensive system for protecting the network against attacks, managing application policies and combating the spread of Malware, considered in the article, based on the products of the acquired SourceFire company, organically complement and strengthen Cisco's portfolio of information security products. We distinguish this class of solutions as promising and will actively develop them. The company makes large investments in the development of the technological branch of information security solutions, which undoubtedly is one of the strategic for the company. In the near future, we expect an increasingly closer integration of SourceFire technologies with Cisco classic architectural solutions and company product solutions.
We are talking about the product SourceFire Firepower, which is an integrated system of intrusion protection, a new generation of firewalls and protection against Malware.
SourceFire was acquired by Cisco in October 2013, and its solutions are currently the leader according to the Gartner rating agency in the field of intrusion prevention systems.

About SourceFire
A few words about SourceFire. The company was founded in January 2001 in the state of Colombia by Martin Roesch, creator of the world-famous open source intrusion prevention system Snort IPS, which is currently the most widely used IPS system in the world (more than 4 million copies are currently downloaded) . In addition to Snort, the company is developing such well-known opensource products to the community as ClamAV and Razorback. In addition to the very successful opensource projects that the company is very proud of, the company’s commercial product is also developing under the SourceFire trademark, which has earned its place as a leader in the field of intrusion detection and prevention systems in the information security market according to the results of the Gartner rating agency (unchanged leader for the past 6 years!),others . A separate group of experts, the VRT team (Vulnerability Research Team), is responsible for developing the rules for detecting attacks and updating them in a timely manner. SourceFire’s commercial line consists of two products:
SourceFire FirePower is a next-generation intrusion prevention system with integrated application-level firewalls, content filtering, and Malware protection at the network level.
SourceFire FireAmp - a system of protection against Malware threats at the host level, running Windows / MAC OSX, Android. It can integrate with Malware protection at the network level - SourceFire FirePower.
Overview of FirePower Platforms
The product is presented in two deployment options: in the form of a 64-bit virtual (VMWare hypervisor) and hardware systems. The functionality of the virtual platform does not support routing, switching, and fault tolerance functions. At the same time, the virtual appliance works fine as an Inline bridge or IDS system on the SPAN port.
A large number of hardware models are available with different performance, modular interface cards, stacking and clustering functions. Model performance starts with the lowest rulers - 50 Mb / s, ending with solutions of the class of large data centers - 60 Gbit / s (Fig. 1).

Fig. 1 The
performance of the virtual model is 100-150 Mb / s per core.
The 7000/7100 Series models have RJ45 / SFP ports fixed on board, depending on the specific model.
The 8100 Series models have modular interface cards with the supported interface types 1 Gbit / s copper / optics and 10 Gbit / s optics MM-SR and SM-LR. The 8200 and 8300 Series also support 40 Gb / s MM-SR optical interfaces. Most interface modules have the ability to configure hardware bypass (including optical) in case of failure of the device.
The older FirePower 8200/8300 range supports the flexible stacking performance feature. For example, you can buy a 8350 sensor with an IPS performance of 15 Gb / s (30 Gb / s platform performance) and at the time when you need to increase the system performance, just buy another 8350, stack them and get a 30 Gb / s IPS performance, and so This way you can stack up to 4 devices with IPS performance up to 60 Gb / s.
Fault tolerance functions are implemented through clustering of complexes into an Active / Standby bundle with synchronization of session statuses.
FirePower hardware solutions are built on the RISC architecture, optimized code and a powerful computing platform with specialized network processors make it possible to achieve and exceed the performance declared by the manufacturer. The claimed performance characteristics are real performance figures that the customer will receive during heavy load tests with the functionality fully turned on. This fact is confirmed by annual tests of NSS Labs.
Defense Center Management System
FirePower is built using a centralized management system - Defense Center. Locally, only the initial settings are available on the FirePower complexes themselves, which allow you to connect the device to the network and configure communication with the control center. All further settings, reporting and monitoring are done centrally in the Defense Center admin console.
Defense Center is presented both in the form of hardware platforms (see Fig. 2) with a maximum number of connected sensors - 150 pieces, and as a virtual machine for a VMWare hypervisor with a maximum number of sensors - 25 pieces.

Fig. 2
The control system in its hardware version has fault tolerance functions for the DC1500 and DC3500 models.
Available Deployment Topologies
For the virtual sensor, configurations of both Inline allocation (see Fig. 3) with inspection and filtering of active traffic are available, as well as placement in IDS mode on a copy of traffic (SPAN) (see Fig. 4).

Fig. 3

Fig. 4
In the case of using the hardware platform, more complex topologies become available to us, since the hardware systems support hardware-level switching functions with Spanning Tree Protocol (STP) support and have routing functions using OSPF and RIP protocols.
The platform allows you to build hybrid topologies (see. Fig. 5).

Fig. 5
For the IPS engine to correctly handle asymmetric traffic flow in the customer’s network, the concept of Inline Set is introduced, for an example of such a configuration, see Fig. 6.

Fig. 6
Let's not forget that many interface cards make it possible to configure bypass in the event of a reboot or a failure on the platform, thus avoiding interruption of services on the network. FireSight
functional review “ You cannot protect what you don’t know ” is one of SourceFire’s slogans and it’s hard to disagree. Having huge corporate networks in management, the information security service is finding it increasingly difficult to track the emergence of new vulnerabilities on company resources such as:
- New patches in client applications, bearing new vulnerabilities;
- Uncontrolled installation of applications by users;
- The ability to bring your device to the network and its uncontrolled connection;
- The release and installation of operating system updates that cure old vulnerabilities and open new ones;
- The emergence of new network segments with new types of operating systems, such as for example process control equipment, etc .;
It is becoming increasingly difficult to monitor all these and other changes with the growth of the network, and every day the process of tracking incidents and the response to them takes more time, and the effectiveness of the fight against real threats is reduced. It is good if periodic active scanning for vulnerabilities is carried out by the IS team, but in addition to scanning, it is necessary to block the possibility of using detected vulnerabilities on the side of the intrusion prevention system. Unfortunately, practice shows that the vast majority of administrators are not able to perform tuning of the IPS signature set as often as required by a changing network. After all, to assess the level of the possible implementation of an attack on a target is possible only by understanding whether the target is vulnerable to this attack, and for this you need to know:
- which service is susceptible to attack;
- what version of the operating system is installed on the attacked host and the version of its patch;
- what version of the patch for the attacked service is used;
- list of known vulnerabilities for the above options, etc .;
But what if CIO itself can sit behind the attacked host ?! Knowing all these and many other characteristics of attack objects or possible attack objects, it is possible to more effectively filter non-hazardous attacks and block really dangerous intrusions with the necessary escalation.
SourceFire is fundamentally different from competing solutions, including in its approach to the analysis of characteristic vulnerabilities in a protected network with the ability to automatically fine-tune the signature set ! The technology under the brand name FireSight allows you to visualize the network and gain visibility (see Fig. 7):
- actual hosts / systems;
- operating systems with versions and patches on hosts;
- client software and its versions;
- users behind hosts;
- inherent vulnerabilities;
- passive data exchange between hosts;

Fig. 7
The sensor analyzes traffic that is actively passing through it or traffic from the SPAN session, looks at the traffic headers down to the application level and, based on the collected data, builds a “map” of the protected network with all its characteristic vulnerabilities. This map is updated in real time. Settings allow the complex to activate / deactivate signatures in active signature sets that correspond to detected vulnerabilities in the network. Testing the 2014 NSS Labs Datacenter IPS results in 99.4% attack blocking efficiency and 100% protection against evasion techniques.
In addition to passively analyzed traffic, the solution supports the upload of the results of active scanning into it, for example, from Nessus.
As an example of the information collected, I will give a profile of one of the hosts (see Fig. 8,9,10,11).

Fig. 8
List of applications on the host:

Fig. 9
List of vulnerabilities on the host:

Fig. 10
An example of a description of one of the identified vulnerabilities with links to patches:

Fig. 11
An example of recommended changes to the signature set based on the analysis of vulnerabilities and systems in the internal network is shown in Figure 12.

Fig. 12
Next-Generation Firewall (NGFW)
A new generation of firewalls, as it is now commonly called, content ITU application level is implemented in SourceFire FirePower and uses signatures for determining the types of applications provided by the intrusion detection engine. NGFW is designed to perform filtering not only at the port and protocol level, as it is classically implemented in the ITU with statefull inspection, but at the protocol level of the application level and the functions of the applications themselves, thus looking deep into transactions and stopping, for example, such activities like transferring a file via Skype or accessing the games feature on Facebook (see Figure 13.14). Note, for example, that Facebook and Google work through the protocol of the 7th level of the OSI model - HTTP. However, these “portals” provide a huge amount of functionality in the form of web applications,
NGFW Access Policy:

Figure 13
Example of Skype File Transfer blocking rule:

Fig. 14
As can be seen from Figure 13, we formulate our application filtering policy and intrusion detection policy in the access policy. Each line of the access policy acts as an Access Control List entry that governs the access rule with the appropriate conditions.
ACL conditions can be of the following types:
- The zones between which filtering will be performed are logical zones to which this or that device interface can belong;
- Networks between which traffic will be filtered;
- VLANs between which traffic is filtered;
- AD users whose traffic we want to filter;
- Applications we want to restrict / allow access to;
- Tcp / udp ports, which we will filter the calls from / to;
- URLs broken down by category and reputation;
All these conditions can simultaneously appear in one rule and will be used as a logical AND.
After each ACL, you can see three icons (see Figure 15), which mean associated policies from left to right:
- Intrusion prevention policy;
- File Filtering and Malware Protection Policy;
- Logging policy;

Fig. 15
If your own network contains applications of your own design and they are not in the application database for filtering, you can easily add your own application to the application database. Import the appropriate Pattern ASCII / HEX for searching, or download an example of network activity of the application from a PCAP file.

Fig. 16
For each access policy, which can be many, you can assign a Security Intelligence filtering policy (Fig. 17). This policy contains constantly updated lists of IP addresses of spammers, C&C botnet centers, open proxies, etc. You can choose from the available lists, or load your own filter lists from a file, or indicate to the system the URL where to get these lists from.

Fig. 17
FireAMP Malware Protection
FirePower solutions provide Malware protection at the network level. The system analyzes the files transmitted through the device specified in the file policy (Fig. 18) formats and transmitted through the specified types of protocols. You can read about the features of the Malware protection solution in an article by Alexey Lukatsky ( alukatsky ).

Fig. 18
The principle of protection against Malware is as follows. The SHA-256 hash is removed from the file sent through the device and sent to the Defense Center, which in turn makes a request (Cloud Lookup) in the SourceFire cloud, figuring out the location of this file (whether the file is clean or Malware) using the cloud base of the well-known Malware . For customers who do not want to send any data to the cloud, the server with the Malware base can be deployed directly to the corporate network, this configuration is called Private Cloud.
If, based on the results of removing the hash and the request, the file cannot be set to the database, the file can be sent by the device to the cloud “sandbox”, where the file’s behavior, its survival after reboot, generated network traffic, and testing to run in a virtual environment will be analyzed. , created processes, files, registry entries and techniques for hiding processes, attempts to reproduce themselves and so on. According to the results of this testing, indices of malicious behavior are calculated, a small excerpt of the report is shown in Figure 19.

Fig. 19
In case the file is executable, FirePower removes more than 400 variables from the file (links to connected libraries, library names, used icons, environment variables, compiler settings, etc.) for analysis by the Spero engine using the fuzzy fingerprint algorithm ( Fuzzy fingerprinting). The algorithm, referring to the logical self-learning trees of signs and behaviors of various kinds of Malware, located in the SourceFire cloud, gets a decision on the file disposition.
A very important difference from classical anti-virus protection systems is that classic systems work at a certain point in time. For example, a file is called for execution, it is checked against the signature base and / or sandbox, and it is forgotten after the conclusion about its cleanliness / infection. However, do not forget that every day in the modern world there are more than 65,000 (SourceFire statistics) instances of the new Malware, for which there are no signatures yet. Malware can use launch delay techniques to avoid detection in sandboxes. In view of the above arguments, Malware can bypass the network antivirus and settle on the end nodes, where, over time, the distribution and operation of Malware will begin. The anti-virus will not leave any records about the past file time of its appearance and source. According to statistics, up to 30% of unknown Malware are carried with them and up to 70% of known Malware are downloaded and vice versa.
The FireAMP system provides a new approach with a retrospective analysis, which remembers all the distribution paths of files and their attributes. In the case of a host-based FireAMP solution, all associated process activities, network activities, all I / O operations on the local host are remembered. And when, after 4 days, it turns out that the downloaded file was previously unknown to Malware, a notification will be received from the SourceFire cloud and the file will be centrally blocked both at the network level and at the level of all endpoint infected systems. Moreover, the system will show the distribution path of the file both over the network and in the host system, all additional components and Malware programs downloaded by the file, access to the processes and the parent process, which made it possible to become infected and give rise to the spread of the threat.
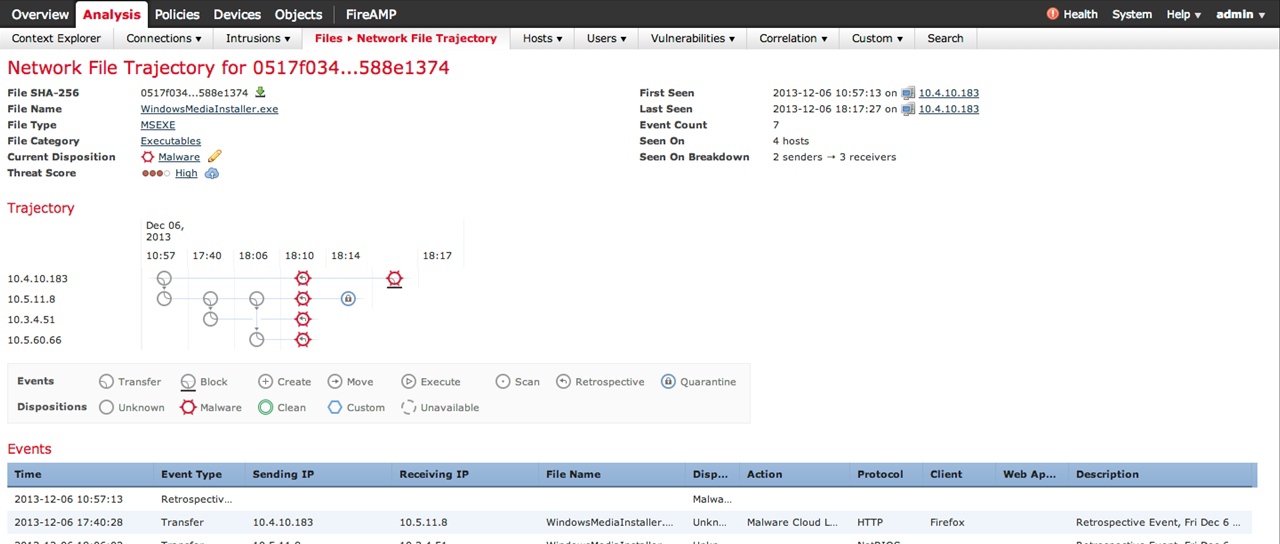
Network-Level Malware Detection Example, Figure 20a, 21

Figure 20a

Fig. 20b
In particular, in Figure 21 you can see the path to the file and further distribution of the file over the network, affected hosts, the time of infection, the ports and protocols used.
In Figure 20b, you can see more detailed information about the distribution and method of getting the threat directly to the host with all associated I / O operations.

Fig. 21
Compliance Whitelist Function
Separately, I want to note the useful function of the white list of systems on the network. Since FirePower can passively see the activity of users and applications on the network in real time, the system makes it possible to build profiles of Compliant systems. Thus, you can specify which operating systems with which patches, client programs and applications in them we want to see on our network. In case of deviation from the template, you can notify the administrator and use the correlation methods (see the next chapter), including executing your own scripts and commands, and perform quarantine / troubleshooting.
It should be noted that FirePower provides the ability to create and assign attributes to various hosts and expose attributes as a result of the correlation action. You can use attributes when generating automatic notifications, including to increase the level of criticality of an attack, and much more. For example, to increase the criticality level of an attack when it is detected in the direction of the host with the value of the base attribute - non-compliant.
The generated attributes can be of the following types:
- INTEGER
- TEXT
- List
- URL
By default, each WhiteList has only one attribute, which takes a value:
- Compliant
- Non-compliant
- Not valued
Each host will have a WhiteList attribute assigned to it with the value of this attribute from the above list.
An example of creating a WhiteList can be seen in Figure 22. You select the allowed types and versions of operating systems, in each operating system, select allowed client applications, web applications, and allowed transport and network layer protocols.

Fig. 22
Traffic Profiles
As you may recall, FireSight technology also monitors the parameters of connections established by hosts on the network. Based on the collected statistics, and at least 29 connection parameters are collected, the so-called basic connection profile for each host is built. In the configuration, you can set which specific types of connections or application traffic will be profiled and for how long to build a basic profile (Example Fig. 23).

Fig. 23 The
example in Figure 23 shows that it is possible to build profiles on the basis of all transmitted traffic as well as to more accurately select the necessary flows.
Event correlation
A very powerful function for tracking, escalating and responding to events is embedded in the system - this is a correlation function. Especially this function will appeal to enthusiasts and security professionals.
In fact, this function provides an opportunity to set sets of conditions with logical connectives for the generation of reactive action (see the correlation condition in Figure 24 for an example).

Fig. 24
As a result of applying the above correlation condition, there will be an invasion event:
- addressed to a vulnerable platform (Impact 1);
- not blocked by signature rules;
- aimed at Anroid or IPhone platform with Jailbrake;
- Owned user in the Executives department (in Active Directory)
As a small example, correlation conditions can be created for the following types of events (see Fig. 25, 26):
- Security event (alert);
- Discovery event
- User activity event;
- The host profile has changed or a vulnerability has been added (host input) (an example of events in Figure 26);
- A connection has been established;
- The traffic profile has changed;
- Malware Detection (Malware event);

Fig. 25

Fig. 26
We examined the possibility of setting correlation conditions, and now we will see how we can respond to the fulfillment of these conditions.
The result of the correlation rule can be one or more actions, such as:
- launching an NMAP scan with the given parameters for the source / direction of attack;
- attacker blocking on a Cisco router (RTBH);
- sending SHUN locks to the Cisco ASA ITU;
- setting the required attribute on the host;
- Admin notification via Email / SNMP / Syslog
- execution of a self-written program written in C / BASH / TCSH / PERL with the ability to transfer variables from the event.

Fig. 27
Monitoring and reporting
system The Defense Center management system provides very clear statistical information on the system as a whole, as well as the opportunity to delve into the details of detected activities from any schedule.
To familiarize the administrator with the current picture of the use of network services, applications, operating systems, analysis of the relevance of activities to business processes and risks, the primary Summary Dashboard overview screen is available (see Figure 28).

Fig. 28
To begin the analysis of past information security incidents, you can go to the Intrusion Events tab and see aggregated information on detected and blocked attacks, statistics and go on to a detailed examination of each event of interest separately (see Figure 29).

Fig. 29
Each incident can be examined in detail, including the contents of the packet that triggered the signature, see Fig. 30. From the information window about the event you can see the text of the triggered signature, the attack signatures are written in SNORT, which has de facto already become the standard for writing IPS rules for many IS administrators. In the same window, you can perform signature tuning, configure filtering and summarize events, change the action associated with the detection of this activity.



Fig. 30
In addition to information about attacks, you can analyze and filter information of interest that the system receives about the network as a whole. To obtain general information about the network, or, if necessary, about its specific segments, the Context Explorer interface exists (see Fig. 31).







Fig. 31
In figure 31 you can see the statistical information:
- correlation of Security Intelligence database data, security events, traffic and Malware events to assess possible threats within the network;
- the activity of specific users and their applications, detailing the level of risk of applications;
- operating systems used inside the network and information exchange activity;
- assessment of safety events by exposure level and priority level;
- statistics on malware activity detection and transmission of infected files;
- geolocation characteristics of hosts spreading malware, implementing hostile activity and the most intense information exchange;
- statistics of the most frequently visited categories of sites, including reputation and most visited URLs;
The system provides the ability to generate your own reports both according to pre-formed templates, and create templates yourself. To create your own report templates, there is a whole Wizard (see Fig. 32), which allows you to include various types of graphical statistics objects, tabular data and directly the contents of packages with suspicious activity. For the purpose of more flexible reporting, it is possible to set your own variables to substitute them into the template when generating the report. Reports can be generated on a schedule and distributed to responsible persons.

Fig. 32
Conclusion
In conclusion, I would like to note that the comprehensive system for protecting the network against attacks, managing application policies and combating the spread of Malware, considered in the article, based on the products of the acquired SourceFire company, organically complement and strengthen Cisco's portfolio of information security products. We distinguish this class of solutions as promising and will actively develop them. The company makes large investments in the development of the technological branch of information security solutions, which undoubtedly is one of the strategic for the company. In the near future, we expect an increasingly closer integration of SourceFire technologies with Cisco classic architectural solutions and company product solutions.
