Results of the quest that you have passed. Or not
Hi, Habr!
Summing up the quest from MBLT DEV 2018 : parse assignments and give gifts - conference tickets, subscriptions to all JetBrains products and Skyeng certificates are the most successful.

We know that you had to break your head. The author of your torment - damnerd . We tell what he came up with, and how you had to solve the tasks.
Log in to the quest
By tradition, they hid it in the video . Even at normal viewing speed, one could see a cipher, in time with the music, a video slips on one of the scenes:

Although some have rushed to write decorative letters from another scene:

Rewrite the cipher and get: aHR0 cHM6 Ly9t Ymx0 ZGV2 LnJ1 L3J1 L3F1 aXo =
Having seen the sign at the end =, we immediately understand that this is a string encoded in base64 format. Without thinking, we perform
echo 'aHR0 cHM6 Ly9t Ymx0 ZGV2 LnJ1 L3J1 L3F1 aXo=' | base64 --decode(or google base64 decode online) and get a link to the quest entry: https://mbltdev.ru/ru/quiz
In principle, the URL remained the same as last time, because programmers were lazy and did not change it. It is rumored that there were those who "guessed" the link from memory, or showed his skill of extrasensory perception.
Exercise 1
It was necessary to follow the link and write the name of which team we left in the tooltip. During the transition, we showed a picture:

Everything is pretty simple: Source = source code. We look that in it:
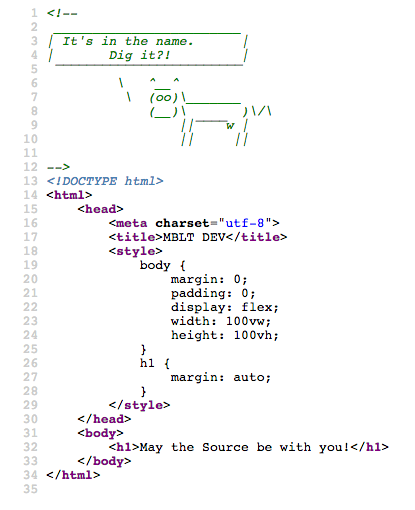
Here we did not confuse the person with any obfuscated code or something similar, but instead, in the most visible place, in the most obvious way (the words of the cow) gave a hint. As it turned out, our attempt to attract attention turned around to the contrary a distraction from the tip. Many, as a response to the question, introduced a command cowsaythat generates similar ASCII graphics. However, it was necessary to look at the text: It's in the name. Dig it ?! The command name was directly at the prompt itself: dig . Actually, we asked the team name (because the team itself can be executed with the same success with a different set of parameters, and the programmers are lazy and the answer checking system is stupid), so this was the answer to the first question.
Task 2
After executing the “dig” command, you had to see a hint with which you can proceed to the next step. We asked to write its value.
Returning to the clue from the past task, in addition to the word dig, the word name stood next to it, carrying the meaning of the domain name. Neighborhood standing name and dig suggest the next step: the need to scratch (or pokeit, if you will) domain records for the name, where the page with the hint lies. Of course, by default dig asks for an A-record, in which there is nothing but the main record with the IP address. It was necessary to guess that you need to request a TXT record:
> dig +nocmd +noall +answer q1.mbltdev.ru txt
q1.mbltdev.ru. 10108IN TXT "quest@95.163.108.79:10022"Or google dig online and use a simple web-muzzle, without reading mana on dig:
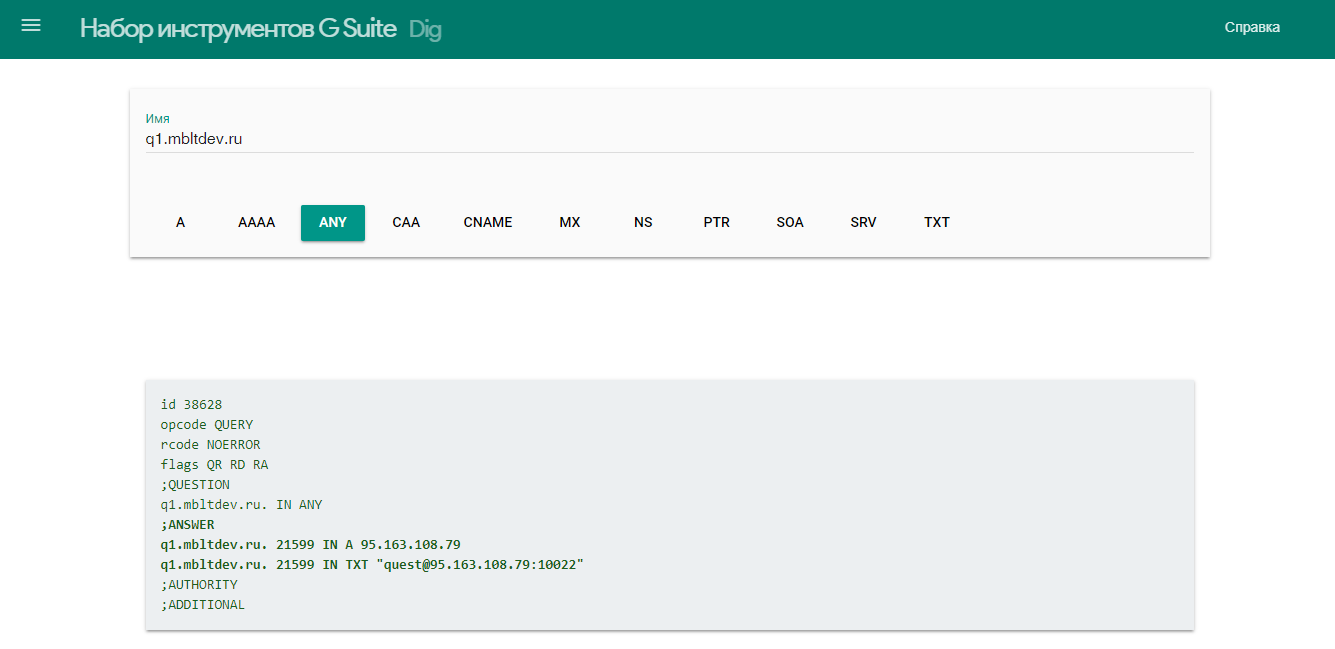
The meaning of this text entry itself was both a response to the task and a hint to the next step — go over SSH to the host 95.163.108.79under the user questper port 10022: ssh quest@95.163.108.79 -p 10022.
Task 3
We made a rebus about what is common between Android and iOS. Asked to calculate the password and enter it.
Many wrote that it was too difficult. But this is a rebus in a quest that no one can pass! But in general, everything was in the text, even the word Parent.
The intersection of android and apple → OS
Progenitor of their OS → Unix
lowercase (Unix) → unix
sha1 (unix) → d13bbbd92b83ddaad994a12bd9d20dfba5fff139
> echo -n "unix" | shasum
d13bbbd92b83ddaad994a12bd9d20dfba5fff139 -As usual, it was possible to google sha1 online and calculate the amount without departing from the cash register.
Task 4
All that was needed to complete this task was in the home directory. We asked to get the following hint after entering the password from Task 3 and write its value.
At this stage, many wanted to give up and wrote us angry comments, but in reality everything was very simple.

There are only 4 files in the home directory, two of which are not in the business - .profileand .bashrcwere almost completely defaulted to the new user by configs. There remained two files with an “empty” name. By the way, even SSH MOTD hinted at it with his phrase /\s/. This is not a strange smiley, but a regular expression for the whitespace. In the name of the first file there was an ordinary space character (U + 0020: SPACE). The second is an unusual space from Chinese writing (U + 3000 IDEOGRAPHIC SPACE).
ITerm2 users on Mac OS had an additional difficulty: this emulator did not want to copy an unusual space. The usual Terminal easily copied the symbol, and it was possible to simply execute commands on it with a simple ⌘C-⌘V. But for users of curves emulators, as well as lovers of perversions, there were other methods, for example ls -li, to find out the inode number of a file, and then execute commands using find:
find . -inum 660402 | xargs catBy the way, this command simply spits out many empty lines in the terminal. Here, knowledgeable people could immediately guess that this is a listing of the program in the Whitespace language, google whitespace interpreter online and get the following hint. Ignorant people could just guess that we need to somehow combine the two files that they have at their disposal. An additional hint was that one of these files has a flag for execution (+ x) and pearl barley. Anyway, the execution of the program gave the answer: http://q1.mbltdev.ru/q.webp
Task 5
In the fourth task, we hid the link http://q1.mbltdev.ru/q.webp . In the fifth it was necessary to go over it and answer the question.
The final task was simple to defuse the situation. At this URL, there was a picture in a format tiffsaved with permission webp. Some smart graphic viewers opened it without question. Some did not open. But it was enough to ask someone who knows:
> file q.webp
q.webp: TIFF image data
> mv q.{webp,tiff}In the very same picture was a simple question:

Answer: 0. MBLT DEV always takes place in Moscow. This year we meet on September 28.
By the way, they say, some found a picture of a detour. This was possible if you rummaged around the server from the 4th task, because the page from the first task, and the picture from the last, and tasks 3 and 4 were hosted on the same machine (do not forget about the developers' laziness). In short:
quest@questmblt2018:~$ grep root /etc/nginx/sites-enabled/quest
root /var/www/html;
quest@questmblt2018:~$ ls /var/www/html/
index.html index.nginx-debian.html q.webpPost mortem
By the way, about the laziness of the developers: although we knew that it would not be without a coochacker in such a quest, we were too lazy to protect ourselves from all possible problems. For example, people began to correspond with broadcast messages, making it difficult for others to complete the quest.
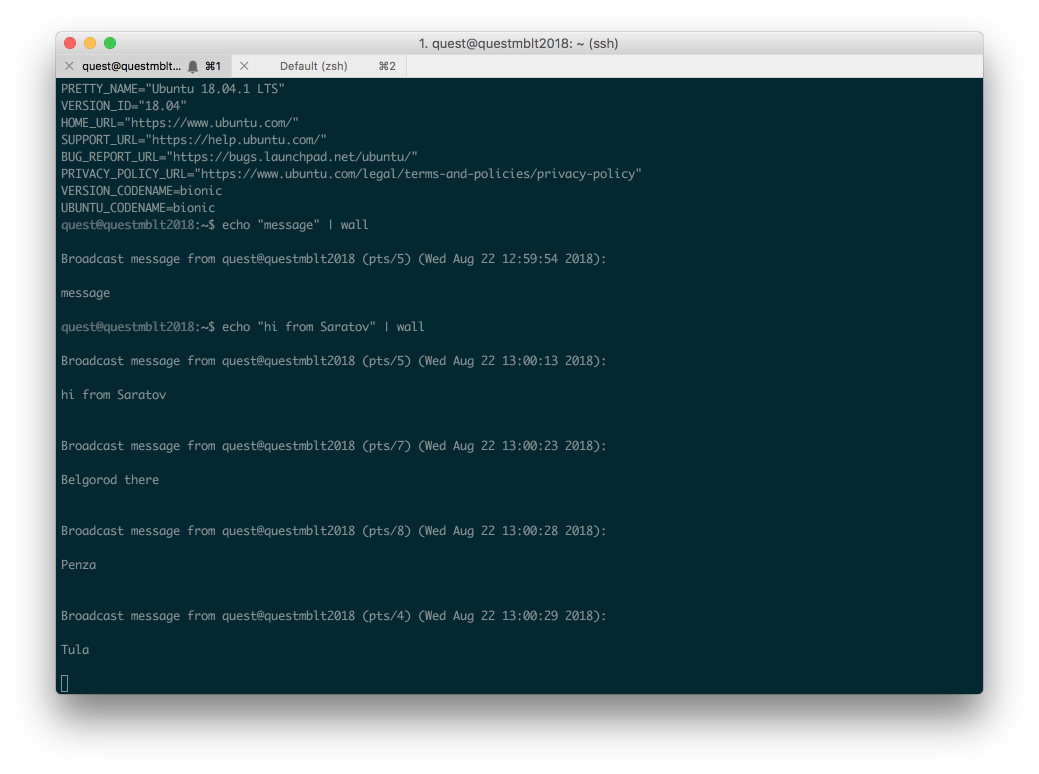
There was some craftsman who uploaded 15 GB of data to the server, having exhausted the disk space. Of course, there were also script-kiddisy, launching fork-bombs, breaking login for other users. Well, it was not without the “spam” bots, who tried, knowing the right answers, to stake out more chances for themselves in the final lottery.
We apologize to those who were prevented by unscrupulous participants.
Gifts and winners
3070 people tried to complete the quest. We received 666 answers, cleaned the cheaters, as a result, 297 people successfully coped with the quest. Among them, we played the main gifts.
Each participant was assigned a sequence number and with the help of a random number generator they won prizes. Recorded a video with a selection of winners. Emails are hidden for privacy reasons.
MBLT DEV 2018 Mobile Developer Conference Tickets
Tickets are given to Vladislav Kozlov, Dmitry and Igor.
Annual subscriptions to any JetBrains product
Subscriptions are Pavel Parfyonov, Vadim Skrypnyk and Andrey.
4 free English classes at Skyeng Online School
Certificates receive Sergey and Valentine.
2 free English classes at Skyeng Online School
Certificates receive Alex and Eugene.
The rest of the quest participants, we also sent small gifts. Check mail!
We meet at MBLT DEV 2018
The conference will be held on September 28 in Moscow. Participants are waiting for useful reports from developers from Netflix, Uber, Revolut, Badoo and other companies, networking and fan. We have prepared some more quests with cool prizes. Tickets are available on the MBLT DEV website .
