Analysis of Turla Cybergroup Outlook Backdoor
Turla (Snake, Uroboros) is a cyber spy group that gained fame in 2008 after breaking into protected objects, including the network of the US Central Command . Since then, specializes in attacks on military facilities and diplomatic departments around the world. Notable victims include the Ministry of Foreign Affairs of Finland in 2013, the Swiss Defense Corporation RUAG in the period from 2014 to 2016. and the German government in late 2017 - early 2018.
After the last incident, several media outlets published information about the methods of attackers — the use of email attachments to manage malware and transfer stolen data from the system. However, no technical information was provided on the backdoor. In this report, we publish the results of the Turla backdoor analysis, which was managed using PDF attachments in email.

According to media reports , several computers of the Ministry of Foreign Affairs of Germany were infected with a backdoor. Apparently, the attack began in 2016 and was discovered by the security services at the end of 2017. The attackers initially compromised the Federal Higher School of Public Administration (Hochschule des Bundes), after which they moved within its network until they got access to the Foreign Ministry network in March 2017 . Turla operators had access to some confidential data (for example, e-mail of employees of the German Foreign Ministry) for about a year.
Our investigation also shows that this malware, aimed at Microsoft Outlook, was used against various political and military departments. We were convinced that the foreign ministries of two other European countries and a major defense contractor were also compromised. Our investigation allowed us to identify dozens of email addresses registered by Turla operators for this campaign, and used to obtain exfiltered victim data.
1. Basic Theses
The Turla Group Outlook backdoor has two functions.
First, it is the theft of outgoing emails that are sent by the attacker. It mainly affects Microsoft Outlook, but is also relevant for The Bat!, Which is popular in Eastern Europe.
Secondly, the use of letters as the transport level of its C & C protocol. Files requested by the backdoor command are exfiltered in specially created PDF documents attached to letters. Backdoor commands are also sent as PDF attachments. This allows for secrecy. It is important to note that attackers do not exploit any vulnerabilities in PDF readers or Microsoft Outlook. Malicious software can decode data from PDF documents and interpret them as commands.
Campaign goals are typical for Turla. We identified several European government agencies and defense companies compromised by this backdoor. It is likely that attackers use it to ensure persistence in restricted access networks, where well-configured firewalls or other network security tools effectively block traditional communications with C & C servers via HTTP (S). The figure below lists the lines of the backdoor code that mention some top-level government domains. mfa is the MFA domain, .gouv is a subdomain of the French government (.gouv.fr), ocse is the Organization for Security and Cooperation in Europe.

Figure 1. Domains related to civil services found in the Malvari code
Based on the analysis and telemetry data, we found that this backdoor has been distributed in the wild at least since 2013. As always with Turla, we cannot focus on compile timestamps, as they are usually faked. Nevertheless, we believe that the first versions were compiled before 2013, since this year’s version was already quite advanced. After that we found a version more similar to the base one, the compilation of which was dated 2009. To determine the exact release date is not yet possible. The chronology below is based on our telemetry and open source data:
2009 : Compile timestamp (maybe fake) of a basic version of Outlook backdoor. Only a snapshot of email content.
2013 : Improved: backdoor can execute commands. They are sent by email in XML format.
2013 : The latest known version focused on The Bat! ..
2016 : Improved: teams are sent as attachments in specially created PDF documents.
2017 : Improved: backdoor is able to create PDF documents for exfiltration of data by an attacker.
March 2018 : Report on the compromise of the German government network.
April 2018 : Improved: the backdoor can execute PowerShell commands using Empire PSInject.
2. Global architecture
In the latest versions, the backdoor is a standalone DLL, which has code for self-installation and interaction with Outlook and The Bat! Email clients, even if only the installation for Outlook is implemented. It can easily be reset by any Turla component, allowing additional processes to be performed.
In this section, our analysis is based on a sample released in the first half of 2017. Information on older or newer samples may be included.
2.1. Installation
To install the backdoor, attackers export a DLL called Install or register it using regsvr32.exe. The argument is the target mail client. The figure below shows the possible values. In recent versions, only installation for Outlook is implemented.

Figure 2. Possible arguments for installation
Because the hard-coded path is missing, the DLL file can be located anywhere on the disk.
2.1.1. Microsoft Outlook
Turla developers rely on COM object capture (COM object hijacking) to ensure the persistence of malware. This is a well-known method used in the wild for many years, including by the Turla group . The essence of the method is to redirect the COM object used by the target application by modifying the corresponding CLSID entry in the Windows registry.
In our case, the following changes have been made in the Windows registry:
HKCU\Software\Classes\CLSID\{49CBB1C7-97D1-485A-9EC1-A26065633066} =
Mail Plugin
HKCU\Software\Classes\CLSID\{49CBB1C7-97D1-485A-9EC1-A26065633066}\InprocServer32 =
[Path to the backdoor DLL]
HKCU\Software\Classes\CLSID\{49CBB1C7-97D1-485A-9EC1-A26065633066}\InprocServer32\ThreadingModel =
Apartment
HKCU\Software\Classes\CLSID\{84DA0A92-25E0-11D3-B9F7-00C04F4C8F5D}\TreatAs =
{49CBB1C7-97D1-485A-9EC1-A26065633066}{84DA0A92-25E0-11D3-B9F7-00C04F4C8F5D}- captured CLSID. It corresponds to the Outlook Protocol Manager and in theory loads the legitimate Outlook DLL OLMAPI32.DLL. {49CBB1C7-97D1-485A-9EC1-A26065633066}not associated with any known software. This CLSID value is arbitrary and is used only as a placeholder for redirecting COM.
When the modification is completed, the backdoor DLL will load every time Outlook loads its COM object. According to our observations, this happens during the launch of Outlook.
COM forwarding does not require administrator privileges, since it applies only to the current user. To prevent such malicious redirects, protection measures are provided. According to MSDN : "With Windows Vista and Windows Server 2008, if the integrity level of the process is above average, the COM runtime environment ignores the user's COM configuration and gets access only to the COM configuration for each machine."
The Outlook process runs at medium integrity, as shown in the figure below. Thus, it is not protected from COM forwarding for each user.

Figure 3. Outlook process integrity level
Finally, using the COM object capture allows the backdoor to avoid detection, since the path to the backdoor ( C:\Users\User\Documents\mapid.tlbin our example) is not displayed in the plug-in list, as shown in the following figure.

Figure 4. Outlook plugins list - mapid.tlb is not displayed
Even if the malware is not displayed in the list of add-ons, the standard Microsoft API, MAPI (Messaging Application Programming Interface), is used to interact with Outlook.
2.1.2. The Bat!
As specified in the chronology, the latest versions of the backdoor no longer include the code for registering the plug-in The Bat! .. However, all the code for managing mailboxes and messages still exists. If necessary, you can configure it manually.
To register as a plugin for The Bat! the malware has modified the file %appdata%\The Bat!\Mail\TBPlugin.INI. This is a legitimate way to register a plugin for The Bat !, some plugins (like antispam) also use it.
After registering each time The Bat! Backdoor DLL is called. The figure below shows how the DLL implements the export necessary for plugins.

Figure 5. Standard export for The Bat!
2.2. Interaction with the mail client
Interaction with the mail client depends on the goal.
2.2.1. Microsoft Outlook
Microsoft supports the Messaging Application Programming Interface (MAPI), which allows applications to interact with Outlook . The Turla backdoor uses this API to access and manage the mailboxes of the compromised system users / users.
First, the backdoor connects to the messaging system using MAPILogonEx, as shown in the figure.

Figure 6. MAPI logon
The second parameter (lpszProfileName) is empty, a flag is set MAPI_USE_DEFAULT. According to the documentation: "The messaging subsystem should replace the default profile name for the lpszProfileName parameter. The flag is MAPI_EXPLICIT_PROFILEignored, unless lpszProfileName is NULL or empty."
In contrast, the flag is MAPI_NEW_SESSIONnot set. According to the documentation: "The parameter is lpszProfileNameignored if there is a previous session called MapiLogonEx with the specified flag MAPI_ALLOW_OTHERSand if the flag is MAPI_NEW_SESSIONnot set."
In our opinion, Outlook opens a default session with a flag MAPI_ALLOW_OTHERS. Thus, the backdoor will use the previously open session to access the default mailbox profile. This explains the lack of a prompt for a username and password when initializing the backdoor plugin.
By doing this, the backdoor will gain access to the mailbox and will be able to easily manage it using other MAPI functions. It will iterate through various message repositories, analyze letters, and add callbacks to incoming and outgoing messages. The log file displays this process (the username and address have been changed):
<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<
========= Analyzing msg store ( 1 / 1 ) =========
Service name:MSUPST MS
Pst path:C:\Users\[username]\Documents\Outlook Files\[email address].pst
Wait main windowbeforeopencurrent store
Loop count = 46
This isdefault message store
PUSH store to list
>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>
_____________ FOLDERS _____________
Setting sink on folders in1 stores.
========Process msg store ( 1 / 1 ) =========
Account: [email address]
Successfull set sink on Outbox folder ofcurrent store.
Successfull set sink on Inbox folder ofcurrent store.It sets up a callback in each inbox and outbox, using a function HrAllocAdviseSinkas shown in the figure.

Figure 7. Register a callback in the Outbox
2.2.1.1. Callback in your inbox
A callback in the inbox folder records the metadata of the incoming letter, including sender and recipient addresses, subject and attachment names. The example below (spelled developer spelling):
RECIVE->{
From: sender@example.com
To: receiver@example.net
Cc:
Bcc:
Subj: Mail subject
Att: an_attachment.pdf
}Then he analyzes the letter and attachments for commands from the attackers. This feature is described in section 2.3.
Finally, it intercepts bounce reports, checking incoming messages with the operator’s email address. Any letter containing the operator’s address will be rejected. This can cause problems if the victim suspects that something is wrong and will contact the support service without seeing the answers.
2.2.1.2. Callback in outbox
As in the inbox, the outbox records the metadata of all emails sent. The following entry is generated (operator's address is changed):
21:57:56SEND <-{
From:
To: recipient@example.com
Cc:
Bcc:
Subj: My title
Att: [1] "last_presentation.pdf"
}
21:57:56Sendingdatamessage
21:57:56MessageENTRYID: [Message ENTRYID]
21:57:56Datamessagewassend. To: [redacted]@gmx[.]com From: Subj: My title
21:57:56 Set last time.
21:57:56 Spawned thread for cleaning up outgoing messages (id 2848)
21:58:34 Ending work, client: Outlook
21:58:34 Number of messages to remove: 121:58:34 Message ENTRYID: [Message ENTRYID]
21:58:34 DeleteMessages executed successfully.
21:58:34 Number of not removed messages: 0You may notice that it sends every outgoing mail message to the attackers […]@gmx[.]com. GMX is a popular free mail service; the attackers probably chose it because organizations usually do not block the gmx.com domain.
This email address is hard-coded in the sample we studied, as shown in the figure below. However, it can be updated using one of the backdoor functions. It seems that the attackers register at least one email address for each target
organization, using the format firstname.lastname@gmx[.]comwith the name of the real employee. This avoids detection because it is often difficult to distinguish such an address from an employee’s actual personal box. At the time of analysis of the sample in June 2018, the address was unavailable.

Figure 8. Hard-coded operator address
The backdoor sends reports at certain intervals to the address of the operators. The report includes unique identifiers, including the MAC address, the complete log file and the results of command execution, if any. It then encrypts the data using MISTY1, as described later in section 2.3.2.2, and creates a valid PDF file with encrypted content. Before this encrypted data blob, the document contains a white 1x1 image in jpeg, hard-coded in malware. This allows you to create a valid PDF that, when opened, displays only one blank page.
Finally, the backdoor attaches a PDF and sends an email to the attackers address. The figure below is an example of a PDF file created by a backdoor.

Figure 9. Beginning PDF document created by backdoor for exfiltration of data
The report is sent using the callback function in the outbox. This means that the letter will leave at the same time as sending legitimate messages from the user. The backdoor cannot send emails with stolen data at uncharacteristic time for the user and therefore avoids detection. Due to its secrecy, this control and monitoring mechanism is very difficult to detect in the wild.
2.2.2. Disguise malicious behavior from the user
Since the backdoor works when the user is working with the computer and Outlook, the malware tries to hide malicious activity, for example, incoming emails from operators.
First of all, the backdoor always deletes mail sent to operators or received from them. As shown in the figure below, within a few seconds you can see that a new message has appeared, which, however, is not displayed in the mailbox.

Figure 10. Unread message
Secondly, the backdoor intercepts the function CreateWindowsEx, as shown in the figures below. This prevents the creation of windows of type NetUIHWND, used by Outlook for notifications, which are displayed in the lower right part of the screen.

Figure 11. Configuring the CreateWindowsEx function interception

Figure 12. CreateWindowsEx Interception
The figure below shows an example of the NetUIHWND window, which is usually displayed on the desktop when a new message is received. As a result of the interception CreateWindowEx, the notification is not displayed when the attackers send a letter to the backdoor.

Figure 13. Notification of a new message
2.2.3. The Bat!
Despite the fact that the registration function of the plugin for The Bat! no longer exists, there is an inherited code that performs the same functions as for Outlook using the API The Bat! ..
As shown in the following figure, the backdoor uses the communication channel with The Bat! To receive information from users, read and send letters. However, all other functions, such as those used for logging letters or executing commands, are identical to Outlook.
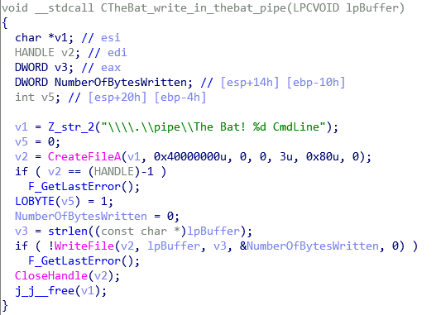
Figure 14. The Bat!
2.3. Backdoor
As shown in the previous section, malware can process and exfilter messages. However, it is a full-featured backdoor, managed via email, which can work independently of any other Turla component. The backdoor does not need a permanent Internet connection and can work on any computer that sends messages to external addresses. This is useful in highly-controlled networks, for example, using Internet traffic filtering. Moreover, even if the email address of the attackers is inactive, they can regain control by sending a command from another address. In this case, the letter will also be hidden from the user, since it will contain commands interpreted by the backdoor. Thus, the backdoor is as fault-tolerant as the rootkit checking incoming network traffic.
2.3.1. PDF format
In early 2018, several media outlets stated that Turla operators use email attachments to manage infected computers. The media were right. Turla's Outlook backdoor analysis revealed how it sends and interprets commands.
Commands are emailed using specially created PDF attachments. We were unable to find a real PDF sample with commands, but these are probably valid PDF documents, as well as PDF files created by the backdoor for exfiltration.
From PDF documents, a backdoor can restore what operators call containers in magazines. This is a blob with a special format that contains encrypted commands for the backdoor. The figure below shows the procedure for retrieving this container. Technically, an application should not be a valid PDF document. The only requirement is that it includes the container in the correct format.

Figure 15. Extract command container from PDF
The container has a complex structure with many different checks. It could be designed to prevent communication errors, but we believe that the structure was created primarily to counteract reverse engineering. The structure of the container is shown in the figure below.

Figure 16. Command Container Structure
Immediately before the initialization vector there is a list of command descriptors. Different ID values are presented in the table:

ID 2 and 4 descriptors are used to extract the encryption and decompression functions, as shown in the following figure. However, the malicious program implements only one encryption algorithm and one compression algorithm. Thus, the only purpose of these fields is to complicate the analysis of the backdoor.

Figure 17. Offset decompression and decryption functions
The teams are in the last part of the structure. They are encrypted using MISTY1 and compressed with bzip2. There can be many different commands in the same PDF file, and each can have several arguments.
2.3.2. Cryptography
Here we describe the encryption algorithms used.
2.3.2.1. XOR encryption
Part of the container (starting with the first CRC32) is encrypted with XOR with a byte stream generated by the user function. A seed is required, which is passed in srandto generate the second number by calling rand. The second seed is used in the function shown below as an argument with the data in the XOR.
int __usercall F_bytestream_xor@<eax>(unsignedint len@<edx>, int ciphertext@<ecx>,
unsignedint seed)
{
unsignedint v3; // ebxint v4; // esiunsignedint v5; // ediint result; // eaxunsignedint v7; // ecxchar *v8; // edxunsignedint v9; // esi
byte key[512]; // [esp+Ch] [ebp-204h]char *v11; // [esp+20Ch] [ebp-4h]
v3 = len;
v11 = (char *)ciphertext;
srand(seed);
v4 = 0;
v5 = 0;
do
{
result = rand();
*(_DWORD *)&key[4 * v5++] = result;
}
while ( v5 < 128 );
v7 = 0;
if ( !v3 )
return result;
v8 = v11;
do
{
v8[v7] ^= key[v4];
v9 = v4 + 1;
result = -(v9 < 512);
v4 = result & v9;
++v7;
}
while ( v7 < v3 );
return result;
}2.3.2.2. MISTY1
Turla developers prefer to use less common or modified encryption algorithms in their backdoors:
- in Carbon and Snake - CAST-128
- in Gazer - custom implementation of RSA
- in Mosquito - Blum Blum Shub as a random number generator for the XOR byte stream
- in the Uroburos rootkit - a modified version of ThreeFish
In the Outlook backdoor, they implemented MISTY1, a symmetric encryption algorithm developed by Mitsubishi Electric cryptographers in 1995. It has the following properties:
- is symmetrical
- has a 128-bit key
- uses two pre-computed tables: s7 (128 bytes) and s9 (2048 bytes)
- uses three functions: FL, FO, FI
o FL performs some XOR operations between byte writing and the extended key
. FO performs XOR operations between the recording and the extended key, and also uses FI
o FI performs non-linear substitution using s7 and s9 - operates in blocks of 64 bits
- performs eight cycles (loop - calling the FO function)
- uses the Feistel cipher

Figure 18. MISTY1

Figure 19. Eight cycles for block encryption
Turla developers slightly modified the algorithm:
- Added two XOR operations to the FI function, as shown in the figure below.
- 128-bit key is generated from two hard-coded 1024-bit keys plus a 2048-bit initialization vector
- changed the tables s7 and s9. This disrupts the operation of all tools that recognize cryptographic algorithms based on the values of s-tables. Both modified and original s-tables contain the same values, they were just shuffled
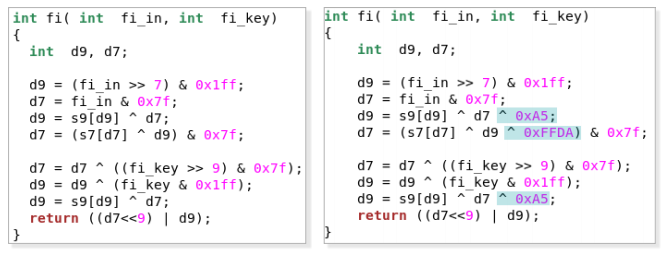
Figure 20. Comparison of FI functions (on the left is the original, on the right is Turla development)
2.3.3. Functions
The backdoor implements many functions - from exfiltration of files to the execution of commands. A description of the various functions is in the table below.

For the 0x29 function, Turla developers copied code from the Empire PSInject project . This allows you to run PowerShell code in a special executable file called PowerShell Runner without calling powershell.exe. The main advantage is that malware can still execute PowerShell commands, even if the file is powershell.exelocked on a compromised computer.
After analyzing the backdoor, we were able to create a PDF document that can be successfully interpreted by malware. The following figure shows the execution of the MessageBox and the launch of the calculator ( calc.exe) after Outlook has received an email containing this PDF document. This demonstrates that the backdoor, probably intended for receiving commands in PDF attachments, is functional and can be managed by anyone who understands this custom format.

Figure 21. Execution of commands specified in a PDF document
2.4. Additional functions
In addition to the backdoor features implemented as a plug-in for the email client, the malware has other functions.
2.4.1. Virtual file system
The malware does not use any configuration files, but supports a small virtual file system in the Windows registry key HKCU\Software\Microsoft\Windows\CurrentVersion\Settings\ZonePolicy\. Other Turla backdoors, such as Gazer , also store a virtual file system in the Windows registry. We were able to determine some registry values, as shown in the following table.
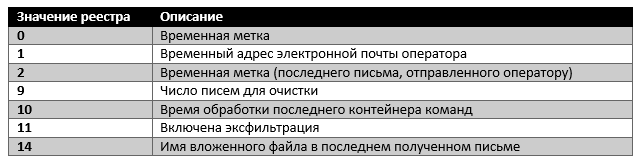
2.4.2. Magazines
As mentioned earlier, the program saves a journal, which is regularly sent to the operator by e-mail in a specially created PDF-document. It is stored in %appdata%/Microsoft/Windows/scawrdot.dband encrypted using a hard-coded 512-byte XOR key. The log file is cleared after each exfiltration to the operators. Thus, during the forensic examination it would be impossible to see all the past actions of the backdoor, only the last.
The logs are quite informative, they allow Turla operators to track backdoor actions. The figure below shows an example of a decrypted log.

Figure 22. Decrypted log file
3. Conclusions
The report showed that Turla developers have enough ideas when they develop backdoors. As far as we know, Turla is the only cyber spy group that currently uses a backdoor, fully managed via email, more precisely, PDF attachments.
Turla backdoor is not the first to use the victim's real mailbox to receive commands and exfiltrate data. However, this is the first studied backdoor using the standard API (MAPI) to interact with Microsoft Outlook. This is a significant improvement over the previous version that we studied , which used Outlook Express. In contrast, the new Turla backdoor even works with the latest versions of Outlook.
Thanks to the ability to control the seemingly legitimate communications of the infected workstation, as well as independence from any specific email address, the Turla backdoor is hidden and fault tolerant. In this regard, it resembles rootkits, such as Uroburos, which receive commands from incoming network traffic.
Our research shows that compromised organizations can be monitored not only by Turla, who introduced the backdoor, but also by other cyber groups. The backdoor simply executes any commands that it receives, without being able to recognize the operator. It is possible that other intruders have already performed the reverse engineering backdoor and figured out how to manage and use them for their own purposes.
Given the severity of the incident, we decided to document the format of PDF files that can manage the Turla backdoor to help professionals understand the principle of action, track activity and reduce risks.
ESET continues to monitor Turla to help security professionals protect their networks.
Indicators of compromise are also available on GitHub .
4. Indicators of compromise
4.1. Hashes
8A7E2399A61EC025C15D06ECDD9B7B37D6245EC2 - Win32 / Turla.N backdoor; Compile time (GMT) 2013-06-28 14:15:54
F992ABE8A67120667A01B88CD5BF11CA39D491A0 - Win32 / Turla.AW dropper; GMT 2014-12-03 20:50:08
CF943895684C6FF8D1E922A76B71A188CFB371D7 - Win32 / Turla.R backdoor; GMT 2014-12-03 20:44:27
851DFFA6CD611DC70C9A0D5B487FF00BC3853F30 - Win32 / Turla.DA backdoor; GMT 2016-09-15 08:14:47
4.2. File names
% appdata% / Microsoft / Windows / scawrdot.db
% appdata% / Microsoft / Windows / flobcsnd.dat
mapid.tlb
4.3. Registry keys
HKCU \ Software \ Microsoft \ Windows \ CurrentVersion \ Settings \ ZonePolicy \
HKCU \ Software \ Classes \ CLSID {49CBB1C7-97D1-485A-9EC1-A26065633066}
HKCU \ Software \ Classes \ CLSID {84DA0A92-25E0-11D3-B9F7-00CC
