Eight zero-day vulnerabilities in one bottle, and that's not all.
Our experts went on the trail of a cybercriminal group that carried out large-scale targeted attacks conducted as part of an activity called the Elderwood Project.
For the first time, this group attracted the attention of our analysts in 2009 by launching an attack on Google and other organizations using the Hydraq (Aurora) Trojan program.

Over the past three years, its attacks have been directed at enterprises in various sectors of industry, as well as at non-governmental organizations. The victims were mainly companies from the USA and Canada, as well as China, Hong Kong, Australia, as well as some European and Asian countries. Recent attacks demonstrate a shift in the interest of attackers towards enterprises that produce weapons components and defense systems. Moreover, one of the main working scenarios is penetration through one of the partner organizations that is part of the supply chain.
Attackers exploit a large number of zero-day vulnerabilities and use a systematic approach to organizing attacks and creating malicious code. We have recorded their repeated use of the components of the platform, called the “Elderwood Platform” (by the name of one of the exploits from their arsenal), which provides quick application of exploits to zero-day vulnerabilities. The methodology of such conducted attacks usually involves the use of phishing emails, but now they are supplemented with attacks of the “watering hole” class - a compromise of the websites most likely visited by the victim.
Comparing the facts, our analysts came to the conclusion that a certain group uses zero-day vulnerabilities and seems to have unlimited access to information about them. Hackers steal information from the computers of selected victims, infecting them with a Trojan program through the sites they often visit. The main target of scammers is the internal information of defense industry companies.
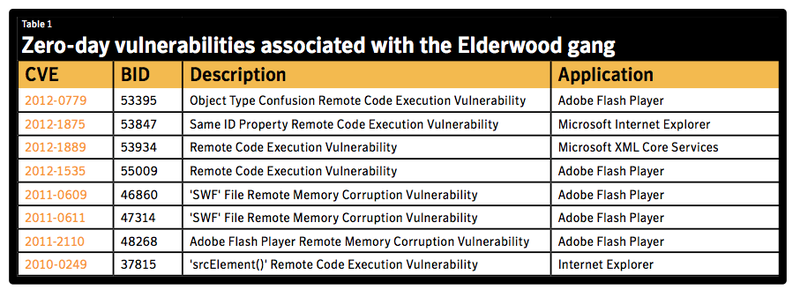
As you know, serious zero-day vulnerabilities that provide unauthorized access to widely used software components are very rarely found in the public domain. For example, in the framework of perhaps the most widely known Stuxnet project, only four of them were used. However, within the framework of the Elderwood Project, they are already used twice as much - eight. And no other group has ever demonstrated anything like this. Applying so many exploits to zero-day vulnerabilities indicates a very high level of training - in order to identify such vulnerabilities, hackers had to access the source code of a number of widely used software applications or decompile them, which requires very, very serious resources. Looks like, that the group has an almost unlimited number of zero-day vulnerabilities. Vulnerabilities are exploited on demand - one after another, and often one replaces the other if the previous one is already closed.
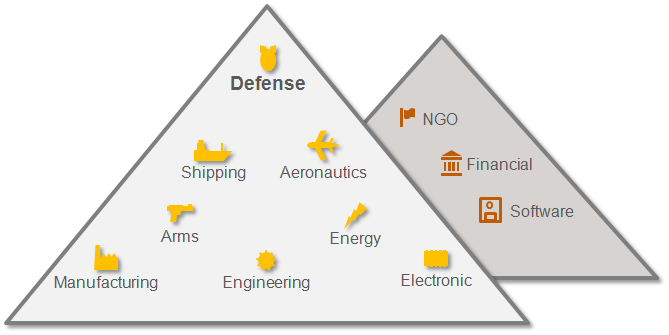
The main objectives of the recorded attacks were organizations from the supply chain of defense industry enterprises, mainly leading defense industry enterprises. The group is interested in companies that produce electronic or mechanical components of weapons and systems, which are sold to leading defense corporations. Attackers, apparently, count on a lower level of protection for such manufacturers, and use them as steps on the stairs leading to intellectual property intended for the production of components or large products by leading suppliers. The diagram below shows the distribution of the various industries that make up the supply chain for the defense industry.

One of the vectors of attacks of the “Elderwood” group is the use of so-called “watering hole” sites, which demonstrates an unambiguous change in the methods used by attackers. The concept of attack in this case is similar to the actions of a predator waiting for his prey in an oasis in the middle of the desert. He knows that the victim, sooner or later, will come to the watering place, and is waiting, instead of conducting an active hunt. Attackers also act in the same way - they identify websites that are visited by specific people of interest to them, hack them and embed exploits on the pages that the victim must visit. Any site visitor will be affected by the implemented exploits, and if their computer is hacked by them, a Trojan will be installed on it.
Facts and Figures:
0-days summary:
Details and technical details in the full Symantec report “ The Elderwood Project ”

For the first time, this group attracted the attention of our analysts in 2009 by launching an attack on Google and other organizations using the Hydraq (Aurora) Trojan program.

Over the past three years, its attacks have been directed at enterprises in various sectors of industry, as well as at non-governmental organizations. The victims were mainly companies from the USA and Canada, as well as China, Hong Kong, Australia, as well as some European and Asian countries. Recent attacks demonstrate a shift in the interest of attackers towards enterprises that produce weapons components and defense systems. Moreover, one of the main working scenarios is penetration through one of the partner organizations that is part of the supply chain.

Attackers exploit a large number of zero-day vulnerabilities and use a systematic approach to organizing attacks and creating malicious code. We have recorded their repeated use of the components of the platform, called the “Elderwood Platform” (by the name of one of the exploits from their arsenal), which provides quick application of exploits to zero-day vulnerabilities. The methodology of such conducted attacks usually involves the use of phishing emails, but now they are supplemented with attacks of the “watering hole” class - a compromise of the websites most likely visited by the victim.
Comparing the facts, our analysts came to the conclusion that a certain group uses zero-day vulnerabilities and seems to have unlimited access to information about them. Hackers steal information from the computers of selected victims, infecting them with a Trojan program through the sites they often visit. The main target of scammers is the internal information of defense industry companies.
As you know, serious zero-day vulnerabilities that provide unauthorized access to widely used software components are very rarely found in the public domain. For example, in the framework of perhaps the most widely known Stuxnet project, only four of them were used. However, within the framework of the Elderwood Project, they are already used twice as much - eight. And no other group has ever demonstrated anything like this. Applying so many exploits to zero-day vulnerabilities indicates a very high level of training - in order to identify such vulnerabilities, hackers had to access the source code of a number of widely used software applications or decompile them, which requires very, very serious resources. Looks like, that the group has an almost unlimited number of zero-day vulnerabilities. Vulnerabilities are exploited on demand - one after another, and often one replaces the other if the previous one is already closed.
The main objectives of the recorded attacks were organizations from the supply chain of defense industry enterprises, mainly leading defense industry enterprises. The group is interested in companies that produce electronic or mechanical components of weapons and systems, which are sold to leading defense corporations. Attackers, apparently, count on a lower level of protection for such manufacturers, and use them as steps on the stairs leading to intellectual property intended for the production of components or large products by leading suppliers. The diagram below shows the distribution of the various industries that make up the supply chain for the defense industry.

One of the vectors of attacks of the “Elderwood” group is the use of so-called “watering hole” sites, which demonstrates an unambiguous change in the methods used by attackers. The concept of attack in this case is similar to the actions of a predator waiting for his prey in an oasis in the middle of the desert. He knows that the victim, sooner or later, will come to the watering place, and is waiting, instead of conducting an active hunt. Attackers also act in the same way - they identify websites that are visited by specific people of interest to them, hack them and embed exploits on the pages that the victim must visit. Any site visitor will be affected by the implemented exploits, and if their computer is hacked by them, a Trojan will be installed on it.
Facts and Figures:
- 8 zero day vulnerabilities
- Attacked 2 applications - Internet Explorer and Adobe Flash Player
- 2 Basic Attack Methods - Phishing Email and Watering Hole
- Possible motives: theft of intellectual property or trade secrets, reconnaissance of plans, contacts, information about infrastructure, analytics for further attacks
- Suspects: (1) a large well-funded criminal gang, (2) a group behind which the state stands, (3) the state
- The main geography of attacks: USA - 72%, Canada - 9%, China - 6%, Australia - 3%, Hong Kong - 3%, the rest - less
- Recommended protection: at the file level - antivirus, at the network level - protection against intrusions. Advanced reputation technology and SONAR
0-days summary:

Details and technical details in the full Symantec report “ The Elderwood Project ”

