Apple introduced a new anti-hacking feature for devices running iOS
Apple has introduced to the public a new feature to protect against hacking their devices running iOS 11.4.1 and higher. The principle of protection is based on disabling data transmission through the device's Lightning port an hour after the screen is locked. This is done in order to limit the ability to connect third-party devices to the smartphone without the knowledge of the owner. The new feature was called USB Restricted mode (USB accesories in the settings) and, according to company representatives, will be able to significantly increase the security of Apple products against hacking in the event of loss or theft of the device.
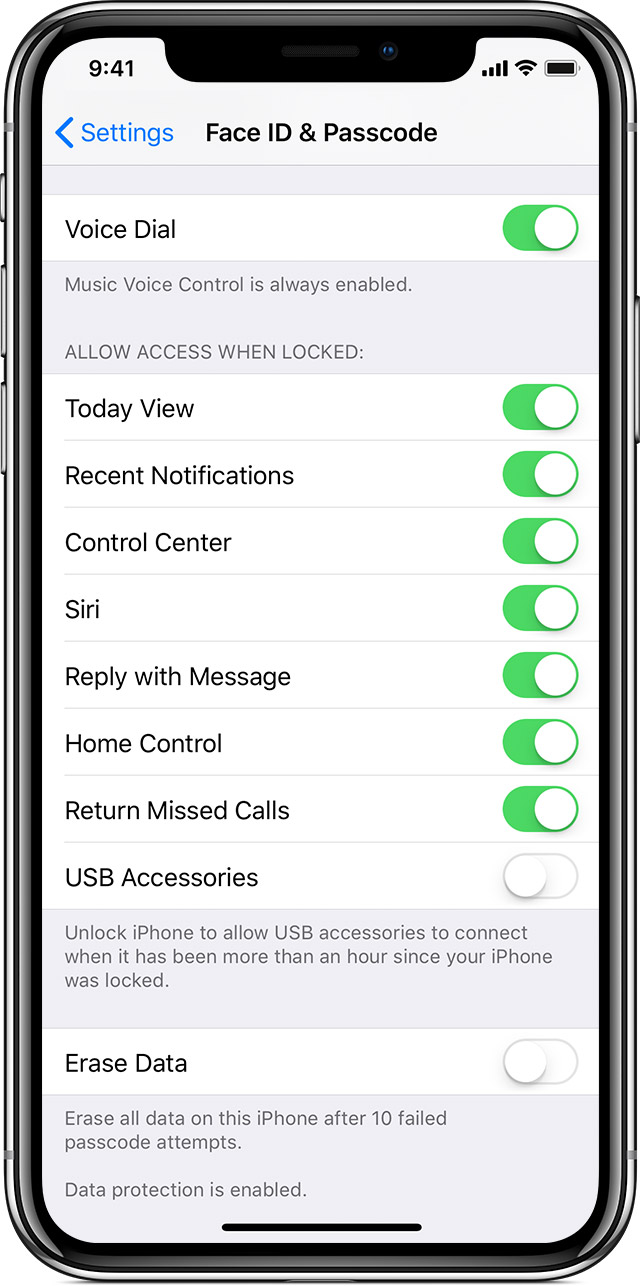
In addition to the obvious inability to communicate with the device via Lightning-port, the new protection system has another feature: the smartphone continues to charge, but becomes completely “dumb”, that is, not detected by other devices, as something “smart” and having its own memory. Thus, if you lose a locked iPhone with USB enabled, Restricted device will quickly turn into a banal brick that can only be charged so that the owner can detect it.
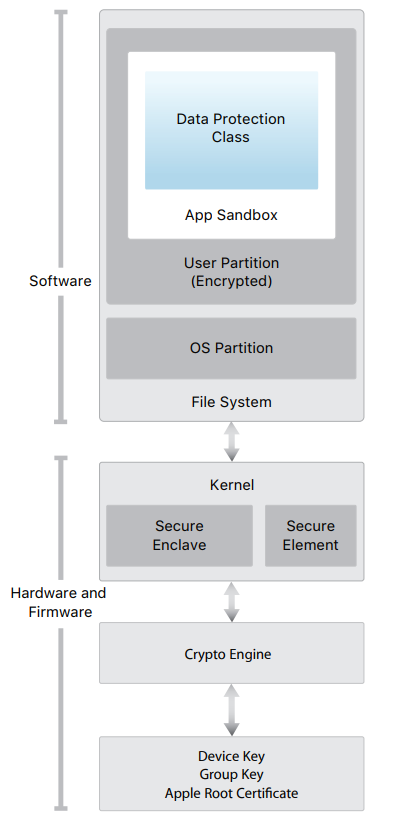
The company took the course to increase the security of the iPhone back in 2014, when in iOS 8 encryption was enabled by default. Then the US law enforcement agencies, and other special services, very negatively perceived such a move by the company. In addition to encryption, Apple devices have physical protection built into the physical layer in the architecture of their processors, starting with A7. This component is called Secure Enclave (SE), it has a common buffer and memory with the rest of the ARM cores of the processor, but does not depend on them. It is through it that the flash memory of the smartphone is encrypted, and the UID, the user-defined password and other device keys are used as the key. The process is as follows: SE generates a 256-bit key for AES encryption based on these keys and a special key available only to the module,
But this is only one of the levels of data protection in the iPhone. The complete security architecture in a schematic view is as follows:
 The technical documentation of Apple in the form of an extensive guide on this topic can be found here .
The technical documentation of Apple in the form of an extensive guide on this topic can be found here .
Already in 2016, the US special services had a real reason to put pressure on the company from Cupertino. Then, the iPhone 5C smartphone Syed Rizvan Farouk, one of the terrorists who had fired at the disabled center in San Bernandino, got into the hands of the FBI.
Then the FBI put forward a number of requirements for Apple, which dealt with cooperation with the Bureau and assisting in hacking the criminal's device in order to identify his possible accomplices and prevent other terrorist attacks in the United States. It is worth noting that up to this point, Apple willingly cooperated with the authorities: the company's specialists helped to crack more than 70 iPhones from 2008 to 2013 at the request of the US intelligence services, but this practice was stopped after the secret documentation had been drained by Edward Snowden. After that, Apple stopped helping the government.
The San Bernandino shooter’s smartphone has literally become a stumbling block between the FBI and Apple. The first ones demanded to remove the restriction on 10 pin-code entries, provide automatic password brute force tools and remove restrictions on the entry speed (after the fifth attempt, the smartphone sets a delay to enter the pin-code at one minute, and after the ninth attempt - at one hour).
Apple experts strongly opposed the work of the FBI and pointed out that the creation of such tools for the target iPhone is impossible - upon receipt of the required FBI software can use it to hack any device. At the time, many people joined the scandal around the terrorist device, including people like McAfee and Gates. Tim Cook has published an open letterfor consumers, in which he argued that the FBI request was illegal and they were required from the company to create a backdoor to attack their devices ( full translation of the letter in Habré ):
After this incident, the Cupertino company was not seen in collaboration with the authorities and continued to increase the protection of its devices. USB Restricted has become another feature.
Immediately after the publication of Apple about the new function of protecting devices on the network, it appeared that this system could be deceived and the Lightning-port would remain fully functional under certain conditions. In the blog of the company Elcomsoft was published an extensive entry, which examines the principle of operation and deception of the new USB Restricted function. So, the company's specialists say that to preserve the operability of the device port and transfer data through it, it is enough to use any MFi module, and both Apple-certified “native” models and Chinese replicas can participate in this scenario.
Why is maintaining full port health so important? Law enforcement agencies need time to transport, receive orders and work on hacking the device, and a one-hour restriction prevents such activities on the vine. However, when connected to an iPhone with the USB function Restricted on any MFi device, the timer counting down from the time it was blocked will stop. For 100% effect, experts recommend connecting additional power to the iPhone to avoid discharging the device, as well as placing the entire “kit” in the Faraday bag (cage). The scenario is quite working, since according to statistics, the average smartphone user performs an unlocking of the screen 80 times a day (that is, every 12 minutes while awake for 16 hours a day).
This life hack only works if less than an hour has passed since the screen was locked. In case of an attempt to connect an MFi device to an already locked iPhone, the phone will return a message stating that it must be unlocked for the module to work. That is, the process of blocking data transmission through the lightning port can only be stopped, but not reversed.
Some consider Apple’s actions against the security services, if you remember the reaction to the FBI’s demands. However, it is for certain known about the possibility of bootforce 4-digit iPhone pincodes, for example, using the GreyKey Machine , and the developers sell their "boxes" to everyone.
Any device connected via Lightning-port, if it is more complicated than a conventional cable or a “cube”, exchanges open-source codes with the smartphone so that the smartphone can determine exactly what is connected to it. This feature is especially relevant after the complete failure of the 3.5 mm Jack jack and the appearance on the market of multiple adapters for every taste and color.
Obviously, Apple engineers could not go a step when any MFi device will be forcibly turned off an hour after the screen lock: this is about the base stations on which the smartphone can be used as a player, adapters to memory cards and even banal wired headphones for listening music
It is possible that such a flaw will be eliminated through the compulsory formation of a white-list of connected devices that can receive priority and stop the timer USB Restricted function. Now it looks like the most likely scenario. At the same time, Apple can once again focus on its own products and users of Chinese replicas will have to choose: either to guarantee the safety of their device, or use cheaper adapters and modules. True, there is always a radical way - the transition to the Android platform.

In addition to the obvious inability to communicate with the device via Lightning-port, the new protection system has another feature: the smartphone continues to charge, but becomes completely “dumb”, that is, not detected by other devices, as something “smart” and having its own memory. Thus, if you lose a locked iPhone with USB enabled, Restricted device will quickly turn into a banal brick that can only be charged so that the owner can detect it.
Why Apple strengthens the protection of its devices
The company took the course to increase the security of the iPhone back in 2014, when in iOS 8 encryption was enabled by default. Then the US law enforcement agencies, and other special services, very negatively perceived such a move by the company. In addition to encryption, Apple devices have physical protection built into the physical layer in the architecture of their processors, starting with A7. This component is called Secure Enclave (SE), it has a common buffer and memory with the rest of the ARM cores of the processor, but does not depend on them. It is through it that the flash memory of the smartphone is encrypted, and the UID, the user-defined password and other device keys are used as the key. The process is as follows: SE generates a 256-bit key for AES encryption based on these keys and a special key available only to the module,
But this is only one of the levels of data protection in the iPhone. The complete security architecture in a schematic view is as follows:

Already in 2016, the US special services had a real reason to put pressure on the company from Cupertino. Then, the iPhone 5C smartphone Syed Rizvan Farouk, one of the terrorists who had fired at the disabled center in San Bernandino, got into the hands of the FBI.
Then the FBI put forward a number of requirements for Apple, which dealt with cooperation with the Bureau and assisting in hacking the criminal's device in order to identify his possible accomplices and prevent other terrorist attacks in the United States. It is worth noting that up to this point, Apple willingly cooperated with the authorities: the company's specialists helped to crack more than 70 iPhones from 2008 to 2013 at the request of the US intelligence services, but this practice was stopped after the secret documentation had been drained by Edward Snowden. After that, Apple stopped helping the government.
The San Bernandino shooter’s smartphone has literally become a stumbling block between the FBI and Apple. The first ones demanded to remove the restriction on 10 pin-code entries, provide automatic password brute force tools and remove restrictions on the entry speed (after the fifth attempt, the smartphone sets a delay to enter the pin-code at one minute, and after the ninth attempt - at one hour).
Apple experts strongly opposed the work of the FBI and pointed out that the creation of such tools for the target iPhone is impossible - upon receipt of the required FBI software can use it to hack any device. At the time, many people joined the scandal around the terrorist device, including people like McAfee and Gates. Tim Cook has published an open letterfor consumers, in which he argued that the FBI request was illegal and they were required from the company to create a backdoor to attack their devices ( full translation of the letter in Habré ):
Specifically, the FBI wants us to make a new version of the operating system for the iPhone, bypassing several important security elements, and install it on the iPhone restored during the investigation. In the wrong hands, such software that does not currently exist can unlock any iPhone that is physically accessible.
The authorities say that this tool will be used once, only on one phone. But this is simply not the case. Once it is created, it can be used again and again, on any number of devices. In the real world, this is equivalent to a universal key that can open hundreds of millions of locks, from restaurants and banks to shops and houses. No sane person would find it acceptable.As a result, the security forces had to pay an unknown amount of hackers from $ 1 to $ 1.3 million in order to access the data on Farouk’s iPhone.
After this incident, the Cupertino company was not seen in collaboration with the authorities and continued to increase the protection of its devices. USB Restricted has become another feature.
USB Restricted is not perfect
Immediately after the publication of Apple about the new function of protecting devices on the network, it appeared that this system could be deceived and the Lightning-port would remain fully functional under certain conditions. In the blog of the company Elcomsoft was published an extensive entry, which examines the principle of operation and deception of the new USB Restricted function. So, the company's specialists say that to preserve the operability of the device port and transfer data through it, it is enough to use any MFi module, and both Apple-certified “native” models and Chinese replicas can participate in this scenario.
Why is maintaining full port health so important? Law enforcement agencies need time to transport, receive orders and work on hacking the device, and a one-hour restriction prevents such activities on the vine. However, when connected to an iPhone with the USB function Restricted on any MFi device, the timer counting down from the time it was blocked will stop. For 100% effect, experts recommend connecting additional power to the iPhone to avoid discharging the device, as well as placing the entire “kit” in the Faraday bag (cage). The scenario is quite working, since according to statistics, the average smartphone user performs an unlocking of the screen 80 times a day (that is, every 12 minutes while awake for 16 hours a day).
This life hack only works if less than an hour has passed since the screen was locked. In case of an attempt to connect an MFi device to an already locked iPhone, the phone will return a message stating that it must be unlocked for the module to work. That is, the process of blocking data transmission through the lightning port can only be stopped, but not reversed.
Some consider Apple’s actions against the security services, if you remember the reaction to the FBI’s demands. However, it is for certain known about the possibility of bootforce 4-digit iPhone pincodes, for example, using the GreyKey Machine , and the developers sell their "boxes" to everyone.
Why such a banal method of cheating the USB Restricted timer works at all
Any device connected via Lightning-port, if it is more complicated than a conventional cable or a “cube”, exchanges open-source codes with the smartphone so that the smartphone can determine exactly what is connected to it. This feature is especially relevant after the complete failure of the 3.5 mm Jack jack and the appearance on the market of multiple adapters for every taste and color.
Obviously, Apple engineers could not go a step when any MFi device will be forcibly turned off an hour after the screen lock: this is about the base stations on which the smartphone can be used as a player, adapters to memory cards and even banal wired headphones for listening music
It is possible that such a flaw will be eliminated through the compulsory formation of a white-list of connected devices that can receive priority and stop the timer USB Restricted function. Now it looks like the most likely scenario. At the same time, Apple can once again focus on its own products and users of Chinese replicas will have to choose: either to guarantee the safety of their device, or use cheaper adapters and modules. True, there is always a radical way - the transition to the Android platform.
