VolgaCTF through the eyes of the participant

On April 15, the qualifying stage of the VolgaCTF-2012 information security competition ended , in which 29 teams from various cities of the Volga Federal District took part. The teams were given 48 hours to solve problems in the areas of:
- Crypto –cryptographic tasks;
- Web - various web vulnerabilities;
- Reverse engineering - reverse engineering;
- StegaSic (Steganography & Forensic) - steganography and research in the field of computer crimes;
- PPC (Professional programming and coding) - various programming tasks;
- Joy - tasks for the general erudition in the field of information security;
- Blackbox Admin - network administration tasks;
I would like to share my impressions with you and write how such competitions look exactly from the side of the participant.
First of all, I express my deep gratitude to the organizers of this competition and the admins for their chic tasks that were not simple, but were interesting.
Our team participated in such competitions for the first time. The start of the competition was delayed by an hour, during which time we managed to get comfortable, set up computers and set ourselves up a bit with various jokes and talk about anything.
A VPN server was raised by admins, keys for connecting teams were distributed, and the game began!
04/13/19:00
Teams were given the internal and external address of the site with tasks. We distributed tasks within the team and started working.
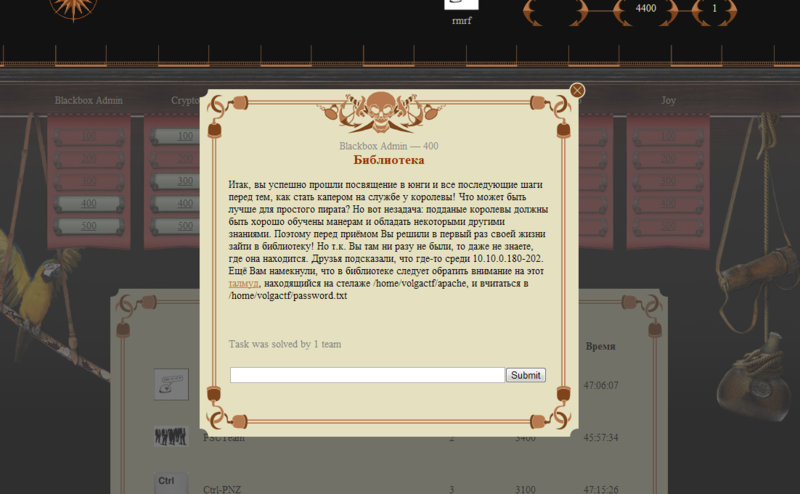
Level 100 across regions varied greatly in complexity. Two tasks were immediately solved:
1) An html page with a large table was given. Each cell of the table contained its own color, after a little game with css, a picture of the island was received, transferred to JPG, uploaded to Google and found the name of the island, which turned out to be key
2) We were sent an archive in which photos of famous pirates and hackers were stored, it’s necessary was to find out their full names and send to the organizers. With the help of Google and a little work with a graphical editor quickly found.
13.04 19:20
The problems of finding and exploiting vulnerabilities in web sites turned out to be much more interesting. The first target was a pirate blog about the ranks of a pirate fraternity. Fifteen minutes later, the rivals introduced a code that hides the contents of some parts of the page. This gave us information about the presence of XSS vulnerabilities. Later we noticed that blogs were regularly updated, new topics were added. Although most likely the information was updated by the program (as it seemed to us), we decided to try to exploit the XSS vulnerability and get the user cookie with administrator rights using standard methods. On the sniffer raised on the Internet, only information about the participants of other teams was displayed, but we did not give up. Migrated XSS to the IP address inside the VPN and the traffic analyzer detected an administrator connection attempt. The key has been taken!
Less successfully solved were the problems of cryptography, reverse, professional programming (ppc), which we immediately dubbed the short and simple word "PPC".
In the problem from the PPC area, the guys immediately recognized the reverse Polish notation . Due to the large amount of work, the processor did not start writing the program immediately; it took quite a lot of time to develop and debug. The answer was received only the next day.
They did not master the seemingly simple task on crypto100.
04/13/20:30
Received the classic quest from the Joy area.

Encrypted archives did not begin to search for hidden meaning, they decided to first try to do what is asked in the photograph. Photographed, sent, earned their 200 points) True, I had to take a little photoshop - add pirated attributes, but the result was excellent)
Around the same time, they solved the problem with Web200, where a link to the administrator’s link was left in robots.txt.
04/13 21:15
Unfortunately, it is not allowed to be at university at night, so our team was asked to vacate the premises. Full of strength and fighting spirit, we went to the apartment to continue to solve problems there.
04/13 10:30 p.m.
Around this time, the first administration task was opened. A server was made available. There were more than a thousand open ports. We began to look for clues. Request for 1000 port always returned "P". A request for port 1001 after referring to port 1000 is always “i”. A similar situation was at 1002, 1003, etc. ports. The letters connected in a row from 1000 to 1005 port gave the word "Pirat". A request for port 1000 discarded the sequence of characters. With a long delay between calls to neighboring ports, the algorithm did not work.
The stage of information collection showed that it is necessary to write a program to sort and display information on all server ports. A simple perl program was soon written. The result of her work was an English text, after several tens of thousands of characters lay the key to the task.
13.04 23:45
Now I would like to talk about really interesting and original tasks from the web area.
Task 3 referred to the site of the pirate bar.
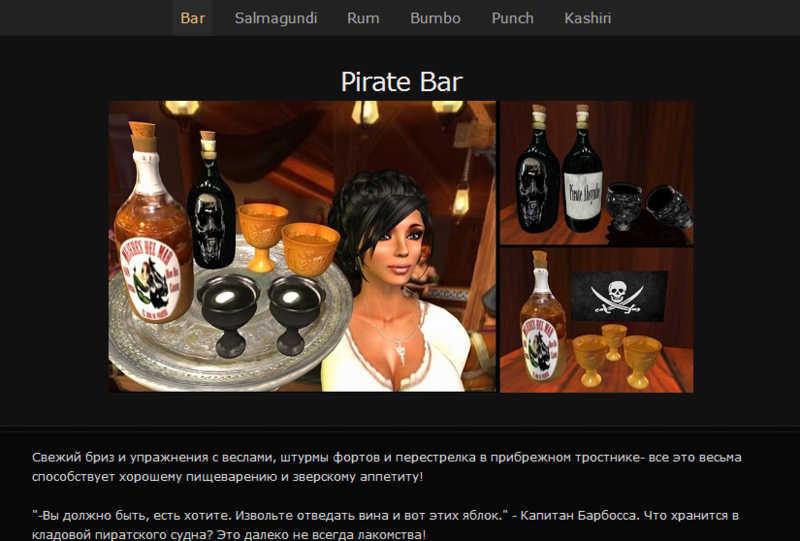
A quick look at the site did not give visible vulnerabilities. The eye settled on hidden comments in html code. An Internet search of the "Pirate Browser" and substitution of all possible names in the User - Agent did not yield a result. But they soon discovered SQL-injection in this field. It would seem nothing complicated, but it was Insert injection. It turned out to be interesting that commands like SELECT, OR, WHERE, ORDER, GROUP, AND were cut out, I had to type the query into a form. What else was interesting, the key parameter in COOKIE, which was always nullified.
Сайт адаптирован для пиратского браузера
Ведется учет пользователей
SELECT TABLE_NAME FROM information_schema.tables WHERE TABLE_NAME LIKE 'k%' SELSELECTECT TABLE_NAME FRFROMOM infoORrmation_schema.tables WHWHEREERE TABLE_NAME LIKE 'k%' The result of the execution was not displayed anywhere (although maybe we did not find it), it was simply written to the database. INTO OUTFILE and other methods did not work, I had to resort to non-standard ones. The decision was delayed until the morning.
The first thing that came to mind was to lead to a script error in cases where the number of rows satisfying the subquery condition is zero. The first I tried to divide the real number by COUNT (*), but in cases where COUNT (*) was equal to zero, MySQL calmly swallowed it.
Search MySQL - functions in which must be the required parameters of the result is not given.
But it turned out to use the so-called timing attack. A query to search for the name of the table in which the key could be converted to a view.
pirat'),((SELSELECTECT if(COUNT(*)!=0,BENCHMARK(100000000000,NOW()),1) FRFROMOM infoorrmation_schema.tables WHERE TABLE_NAME LIKE 'k%'))#Roughly speaking, if there is not a single line satisfying the condition, the site opens slowly, if there is, then quickly. The BENCHMARK function provides a slow operation speed of 1,000,000,000 times repeating a typical operation.
Search through LIKE was initially rejected by SUBSTR (TABLE_NAME, 1,1)> 'a'. It took a long time to sort through one letter, so it was possible to set a range. (note. It was possible to implement a script that automates these actions) After selecting the first few letters of the table name, I remembered the existence of the REGEXP () function, with which you can specify the search with regular expressions, the selection of letters has become much easier. In addition to the name of the table with the flag, I found similar actions, the name of the field with the flag and the flag itself, a total of about 25 characters had to be sorted by manual binary search.
The found key turned out to be the word 'elpirata', which did not fit as an answer to the assignment. But setting the variable key in this cookie with this word made it possible to get the key from the job.
04/14 02:00
After not the first coffee mug, the team solved the problem of finding exploit in a PDF file, spent more than one hour searching for a key in a wav file (which turned out to be at the edge of the signal spectrum), such a gif was decrypted:
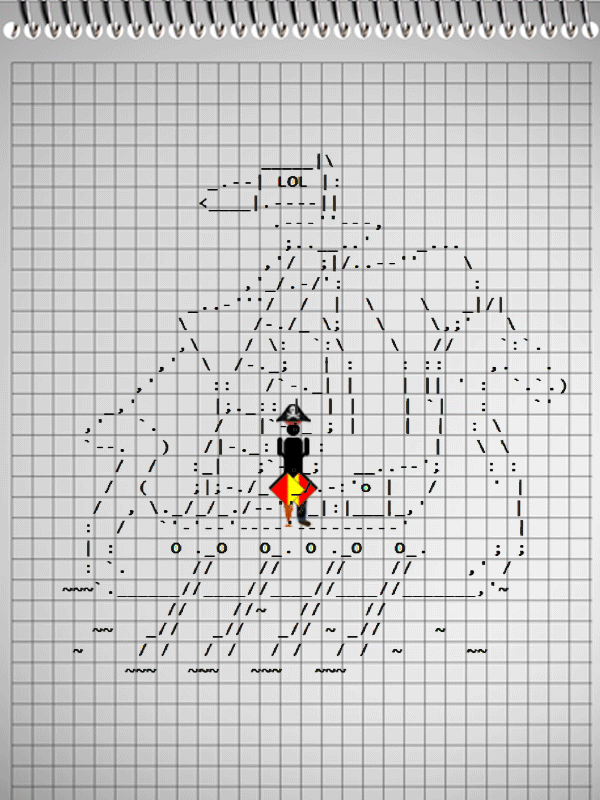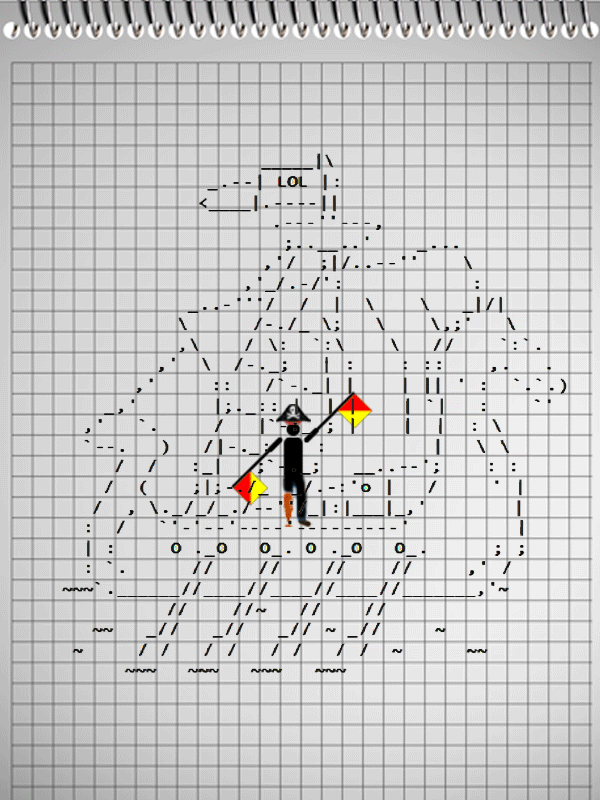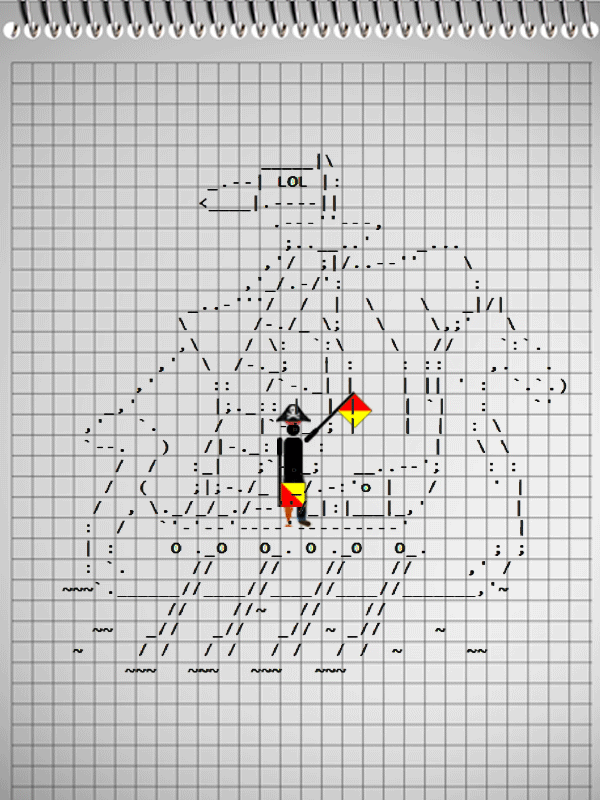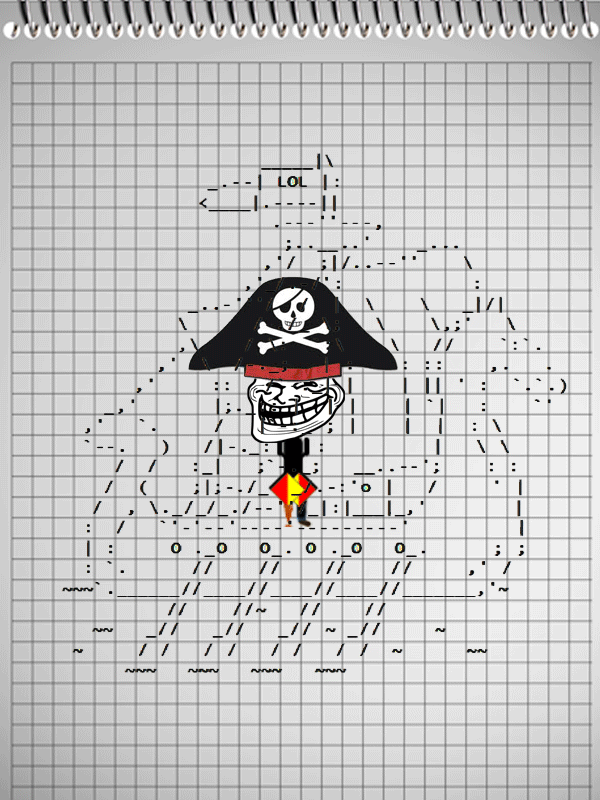
Which Under certain conditions, the signal flags transmitted a message containing the key to the task.
In one of the tasks containing a lot of text in a 35 MB graphic JPEG file, they saw a fountain.
04/14 05:00
In the same task, they saw a palm tree, realized that it was time to go to sleep ...
Here is the task ...
04/14 11:00
We arrived at the university and began to work on previously unfinished tasks.
April 14 15:00
We received an interesting assignment from the area of WEB 400 level. To search for vulnerabilities, a couple of sites were prepared.

The first server had a treasure website, the second contained a web studio website. Enumerating the input parameters revealed a blind SQL-injection, in which it was impossible to use the UNION command. A random search of known words found the user table, with the id and user fields containing 1 record.
In contrast to the previous task, the REGEXP function did not work, and we developed a script that sorted letters in LIKE.
The final query to the database:
0 OR (SELECT user from user where user like 'adm%') LIKE '%'Instead of the word adm in the request above, the script substituted various combinations of letters, if a user was found to start with a given combination, the content on the page was displayed.
Finding a user was slightly surprised. Nick turned out to be postgres. It was logical to assume that the PostgresSQL DBMS was used.
Reading the documentation for this DBMS helped us find the table replacing the table in information_schema in mysql, and with its help the name of the user table field containing the password. This password was stored in md5, after decryption it turned out 16 character postgrespostgres. This login did not go to the site administrator’s panel, which entered into a stupor. The DB control panel on the remote server was not found, access from outside was closed. It was a shame enough to have a login from the database, but the inability to connect to it.
We began to select the names of the tables and found the administrators table, which contains the login itself from the site admin panel. In the admin panel, we were waiting for the source code of a couple of pages of the site, access to which had to be obtained. On these pages it was possible to read the files specified in _GET with the fread function if you know the address to them. There was a hidden link to a folder open for listing from a browser and not containing files.
We went through and looked through all the standard configuration folders for unix systems, tried to access .bash_history and access_log, but to no avail. Fortunately, they soon found the .htaccess file in a hidden folder. It had a rule prohibiting the display of a file with a flag in a directory listing. Downloading hidden files displayed encrypted JavaScript code. We started to get upset that the task would drag out, but after a minute an alert was executed on the page containing the flag from the task.
The whole task took 5 hours.
Seeing in web500 a task with basic authorization at the entrance to the site, we decided to postpone it.

On this day, the rest of the team members solved interesting problems, including on administration with privilege escalation, one of the tasks of cryptography and an interesting task about torrents. In each downloaded torrent, it was recursively proposed to download other torrents, after assembling all the parts, a Slax image was obtained, it contained a key.
14.04 20:00
Our team was the leader, the tired went home. We decided to sleep well, although during the night someone nevertheless completed a number of tasks.
15.04 11:00
On the last day, only two tasks of level 5 were solved, for which the most points were given.
Both tasks were interesting, so I would like to talk about them in detail.
The web500 task deferred yesterday succumbed. It is noticed that if you send POST data to the index.php file, then the page was given.
Intuition said that it simply would not. There can be no talk of any common vulnerabilities. The unopened image turned out to be base64 encoded png of the smiling troll-face pirate. A search for similar images gave a picture of an identical canvas size, but a different size on the disk. The search for hidden information in the file failed.
Having a little desperation, I inserted the address /index.php.bak into the address bar and got the code of the original page , which was rather upset, because it was well obfuscated.
The eyes are afraid, but the hands are doing ... Decoded.
function __autoload($classname) {
$classpath = './inc/class/'.$classname.'.php';
if(file_exists($classpath))
include $classpath;
}
require_once('inc/config.php');
echo 'Ты не пройдешь, пират! ";
}
}
The attentive reader will notice the vulnerable string string echo "Hello, {$ auth ['name']}!"; and __autoload.
Soon, a script was written that prepared cookie data, after unserialize which the variable $ auth ['name'] contained an object of an unknown class. This called the autoload function, and the execution of a vulnerability like php-injection.
$value=new arrayObject();
$value->offsetSet('login','pirate');
$value->offsetSet('password','pirate1');
$value->offsetSet('name',new index);
$value=serialize($value);
echo 'auth='.urlencode($value).';';
Downloading the index file returned a list of files in the folder. Soon the sources of other files with project classes were received .
I was pleased and energized by the Flag class, which said that a little more remained.
A study of other classes revealed more vulnerabilities.
In particular, it turned out that the textbox class contains a function
function __toString() {
return $this->obj->printObj();
}
Object contains a function
public function printObj() {
return serialize($this);
}
User contains a function
public function __sleep() {
return $this->login->{$this->password}();
}
As a result, a structure was constructed to return to the script that returned the key. (approx. in fact, in the user class, they found an error in the name of the __contuct () function and before the correction the developers did not work;)
$value->offsetSet('name',new Textbox(new Object(new User(new Flag,'getFlags'))));
The whole task took 7 hours.
In parallel, another part of the team found a solution to the original Joy500 assignment.
The script chose random girls from vk.com. Team members should have asked them to register on a site designed for the contest.
It seems to be nothing complicated,
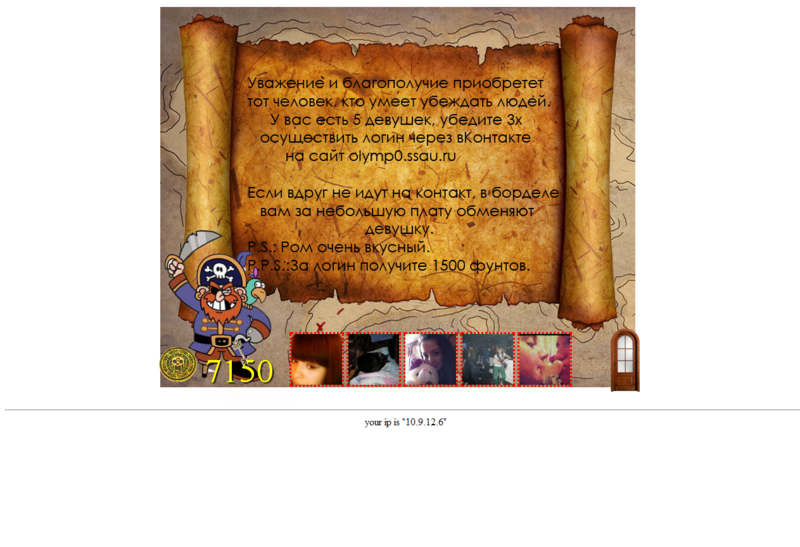
We look at the site on which it is necessary to lure, we see a window:
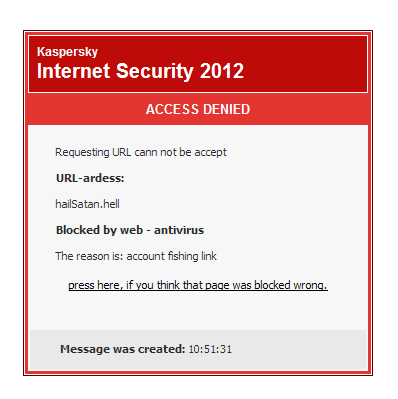
Then this:
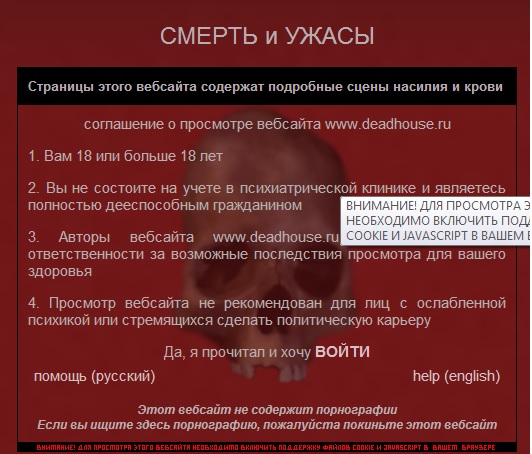
And the site itself:
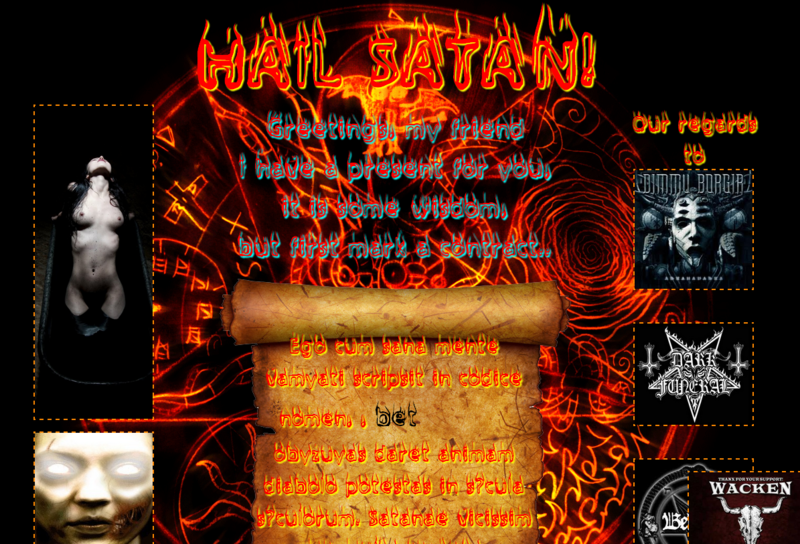
Ominous music plays in the background, you need to wait 333 seconds before registration. Modal windows go out all this time. In general, a satanic website) It wasn’t so easy to persuade unfamiliar girls to register.
This concludes the story about VolgaCTF. Our team won by a good margin, gained a lot of experience, got a ticket to Samara for a full-time summer tour. And also we lit admins on cool t-shirts.
Team photography in response to the Joy200.

