Networks for the smallest. Part three. Static routing
- Tutorial
The boy told his mother: “I want to eat.” Mom sent him to dad.
The boy told dad: “I want to eat.” Dad sent him to mom.
The boy told his mother: “I want to eat.” Mom sent him to dad.
And so the boy ran, until at one moment he fell.
What happened to the boy? TTL is over.
So, a turning point in the history of the company “Lift mi Up”. Management understands that a company manufacturing elevators traveling only up will not stand up in a highly competitive market. Need to expand the business. A decision was made to purchase two plants: in St. Petersburg and Kemerovo.
An urgent need to organize a connection to new offices, and you still have not even worked lokalka.
Today:
1. We configure routing between vlanes in our network (InterVlan routing)
2. We try to deal with the processes occurring in the network, and what is happening with the data.
3. We plan network expansion (IP addresses, vlana, switching tables)
4. We configure static routing and understand how it works.
5. We use the L3 switch as a gateway
Content:
A little practice for cheering up.
The last time we configured the switches of our local network. At the moment, devices of different vlanes do not see each other. That is, in fact, FEO and VET, for example, are in completely different networks and are not connected to each other. Likewise, the server network exists by itself. It would be necessary to fix this annoying nuisance.
In our Moscow network, we will use the cisco 2811 router for routing between vlanes. In other words, it will terminate vlans. Frames here end their lives: IP packets are retrieved from them, and link layer headers are discarded.

The router setup process is very simple:
0) First, finish with the msk-arbat-dsw1 switch. On it we need to configure the trunk port towards the router, which we did not do the last time.
1) We assign the name of the router with the hostname command , and in order to develop a good tone, we must mention that it is better to immediately configure the time on the device. This will help you correctly identify log entries.
It is advisable to distribute time to network devices via NTP (any tsisk can be made an NTP server, by the way)
2) Next, go to the configuration mode of the interface facing our local network and turn it on, since by default it is in the Administratively down state.
3) Create a virtual interface or else it is called a subinterface or another subinterface (sub-interface).
The logic here is simple. First, we indicate in the usual way the physical interface to which the desired network is connected, and after the dot we put some unique identifier for this virtual interface. For convenience, usually the subinterface number is made similar to the vlan, which it terminates.
4) Now let's recall the 802.1q standard , which describes tagging a frame with a vlan label. By the following command, you indicate that frames coming from this virtual interface will be tagged with the 2nd display. And the frames entering the physical interface FastEthernet0 / 0 with the tag of this vlan will be accepted by the virtual interface FastEthernet0 / 0.2.
5) Well, just like on a regular physical L3 interface, let's determine the IP address. This address will be the default gateway for all devices in this vlan.
Similarly, for example, configure the 101st vlan:
and now we’ll make sure that from the computer from the VET network we see the control network:
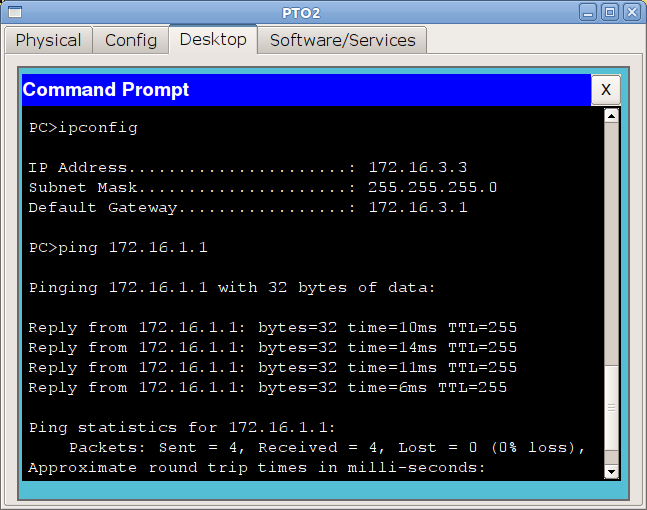
Works and fine, configure all the other interfaces for now. Problems with this should not arise.
What happens to your data at this time?
The last time we discussed what happens if you try to connect to a device from the same subnet as you are.
By the same subnet we mean the following.
For example, the following is configured on your computer:
IP: 172.16.3.2
Mask: 255.255.255.0
GW: 172.16.3.1
All devices whose addresses will be in the range 172.16.3.1-172.16.3.254 with the same mask as yours will be members your subnet. What happens to the data if you send it to a device with an address in this range?
Repeat this with some additions.
To send data, they must be packed into an Ethernet frame, in the header of which the MAC address of the remote device must be inserted. But where to get it?
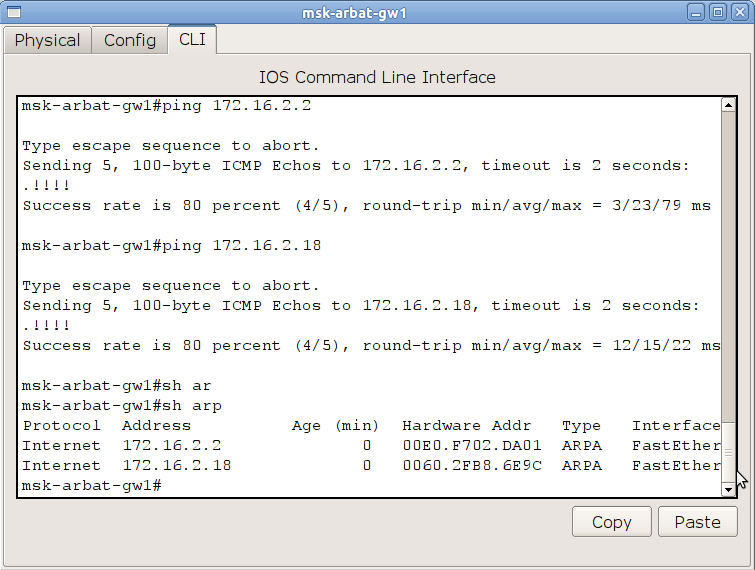
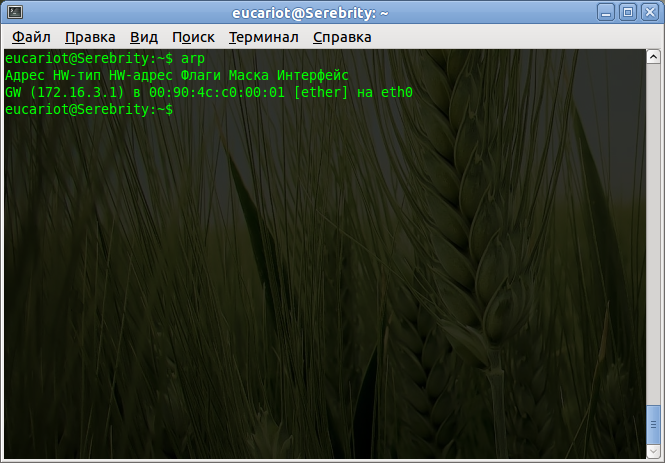
To do this, your computer sends out a broadcast ARP request. The IP address of the destination host will be placed in the IP packet with this request as the IP address of the destination host. When encapsulated, the network card indicates the MAC address FF: FF: FF: FF: FF: FF - this means that the frame is intended for all devices. Then it goes to the nearest switch and copies are sent to all ports of our Vlan (well, except, of course, the port from which the frame was received). Recipients see that the request is broadcast and they may turn out to be the desired host, therefore, they extract data from the frame. All those devices that do not have the IP address specified in the ARP request simply ignore the request, but the real receiver will respond to it and send its original MAC address to the original sender. Sender (in this case, our computer) puts the received MAC in its IP and MAC address mapping table aka ARP cache. What does the ARP cache look like on your computer right now, you can see with the commandarp -a
Then your useful data is packed into an IP packet, where the address you specified in the command / application is put as the recipient, then into the Ethernet frame, in the header of which the MAC address received by the ARP request is placed. Next, the frame is sent to the switch, which, according to its table of MAC addresses, decides which port to forward it to.
But what happens if you try to reach the device in another vlan? An ARP request will not return anything, because broadcast L2 messages end on the router (i.e., within the broadcast L2 domain), the desired network is located behind it, and the switch will not send frames from one vlan to the port of another. And for this, you need a default gateway on your computer.
That is, if the recipient device is on your own subnet, the frame is simply sent to the port with the mac address of the final recipient. If the message is addressed to any other subnet, the frame is sent to the default gateway, therefore, the MAC address of the receiver is set to the MAC address of the router.
We follow the course of events.
1) The PC with the address 172.16.3.2/24 wants to send data to the computer with the address 172.16.4.5.
He sees that the address is from a different subnet, therefore, the data should go to the default gateway. But in this case, the PC needs the MAC address of the gateway. The PC checks its ARP cache to find the match. The IP address of the gateway is the MAC address and does not find the right one.
2) The PC sends a broadcast ARP request to the local network. ARP request structure:
- at the channel level, as the recipient - the broadcast address (FF: FF: FF: FF: FF: FF), as the sender - the MAC address of the interface of the device trying to find out the IP
- on the network - actually the ARP request, it contains information about what IP and by whom it is searched.
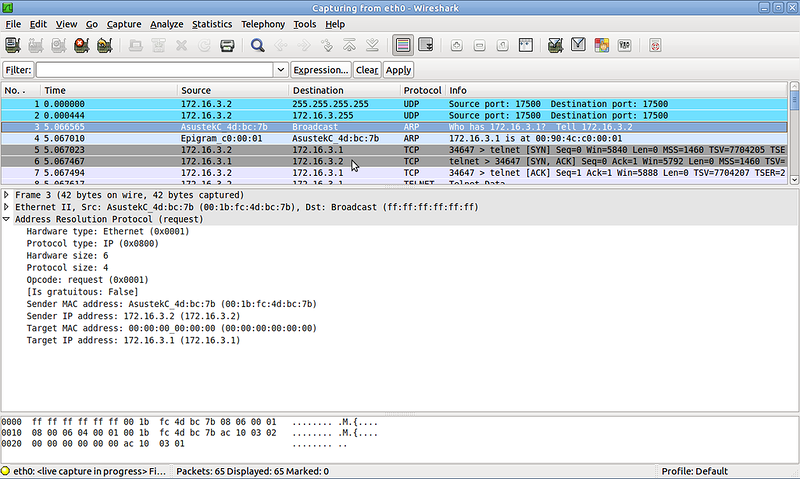
3) The switch to which the frame was sent sends its copies to all ports of this vlan (the one to which the original host belongs), except where it was received from.
4) All devices, having received this frame and seeing that it is broadcast, assume that it is addressed to them.
5) Having unpacked the frame, all hosts except the router see that their address is not in the ARP request. And the router sends a unicast ARP response with its MAC address.
6) The original host receives an ARP response, now it has the MAC address of the gateway. He forms a packet from the data that he needs to send to 172.16.4.5. The PC sets the gateway address as the destination MAC address. In this case , the recipient's IP address in the packet remains 172.16.4.5
7) The frame is sent to the network, the switches deliver it to the router.
8) On the router, in accordance with the Vlan label, the frame is received by a specific subinterface. Link level data is reclined .
9) From the header of the IP packet, the router learns the recipient’s address, and from its routing table sees that it is in the network directly connected to it at a specific subinterface (in our case FE0 / 0.102).
10) The router sends an ARP request from this subinterface - it recognizes the MAC address of the recipient.
11) The original IP packet, without changing, is encapsulated in a new frame , while:
- the gateway interface address is specified as the source MAC address - the source
IP address is the address of the original host (in our case 172.16.3.2)
- as MAC the recipient’s address indicates the address of the final host
— the recipient’s IP address — the address of the final host (in our case 172.16.4.5)
and is sent to the network from the FastEthernet0 / 0.102 subinterface, receiving the label of the 102nd vlan.
12) The frame is delivered by the switches to the destination host.
Now let's turn to planning. In the zero part, we already touched on this topic, but then we were talking only about two offices in Moscow, now the network is growing.
It will be like this:
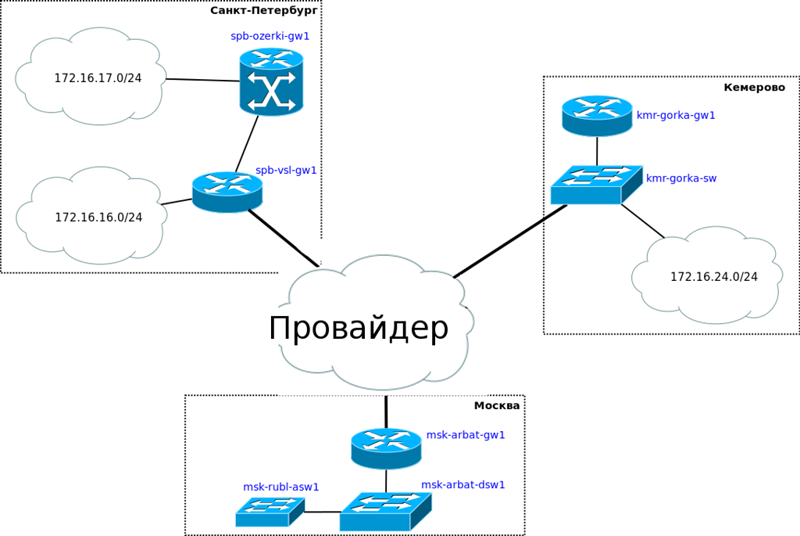
That is, two points are added in St. Petersburg: a small office on Vasilievsky Island and the factory in Ozerki itself, and one in Kemerovo in the Krasnaya Gorka area.
For simplicity, we will have one provider “Balagan Telecom”, which on favorable terms will provide us with L2VPN to both points.
In one of the next issues, we will reveal the topic of various connection options in paints. In the meantime, in short: L2VPN is, very roughly speaking, when a provider provides you with a vlan from point to point (for simplicity, you can imagine that they are included in one switch).
A few words should be said about IP addressing and subnetting.
In the zero part, we have already touched upon planning issues, and I must say very casually.
In general, in any more or less large company there should be some kind of regulation - a set of rules, following which you distribute IP addresses everywhere. Our network is expanding now and developing it is very important.
Well, for example, let's say that for offices in other cities it will be like this:
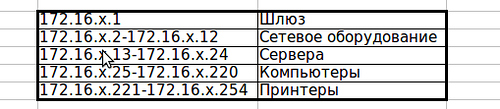
This is a very simplified regulation, but now, in any case, we know for sure that the gateway will always have the 1st address, until the 12th we will give out to the switches and any wi-fi points, and we will look for all servers in the range 172.16.x .13-172.16.x.23. Of course, to your taste, you can specify the rules down to the address of each server, add the rule for generating device names, domain names, access list policies, etc. to it.
The more accurately you formulate the rules and more closely monitor their implementation, the easier it is to understand the structure of the network, solve problems, adapt to the situationand punish the perpetrators .
It’s about a pattern of remembering passwords: when you have a certain rule for their formation, you do not need to keep a few dozen hard-to-remember passwords in your head, you can always calculate them.
That's the same here. I once worked in a medium-sized holding company and knew that if I come to the office somewhere in a village forgotten by cows, then there xyz1 is the tsiska, xyz2 is the distribution switch of the procurator, and xyz101 is the computer of the chief accountant from whom you must give access to some external circuit. Another question is that we still need to check it, because local IT specialists sometimes do such a thing that you wash yourself with tears through laughter.
Now it would be very useful for us to draw up an IP plan. We will proceed from the fact that at all three points we will use a standard network with a 24-bit mask (255.255.255.0) This means that there can be 254 devices in them.
Why is this so? And how do you understand all of these subnet masks? In the framework of one article, we will not be able to tell this, otherwise it will turn out to be as long as the deck of the Titanic and tangled like Odessa catacombs. We strongly recommend that you familiarize yourself with such concepts as IP address, subnet mask, their binary representation and CIDR (Classless InterDomain Routing) yourself. We will only argue the choice of a specific network size. Be that as it may, full understanding will come only with practice.
In general, this topic is very well disclosed in this article:http://habrahabr.ru/post/129664/
At the moment (remember the zero issue ) in Moscow we used the addresses 172.16.0.0-172.16.6.255. Suppose that the network can still grow here, for example, an office appears on the Sparrow Hills and reserve another subnet until 172.16.15.0/24 inclusive.
All these addresses: 172.16.0.0-172.16.15.255 - can be described as follows: 172.16.0.0/20. This network (with the / 20 prefix) will be the so-called supernet , and the operation of combining subnets in the supernets is called summing subnets (summing routes, to be precise, route summarization)
Very intuitive IP-calculator. I now use it periodically, although over time an intuitive and logical understanding of the correspondence between the length of the mask and the boundaries of the network comes.
Now let's turn to Peter. At the moment, in this beautiful city, we have 2 points and each of them has a subnet / 24. Let's say it will be 172.16.16.0/24 and 172.16.17.0/24. We reserve the addresses 172.16.18.0-172.16.23.255 for a possible expansion of the network.
172.16.16.0-172.16.23.255 can be combined into 172.16.16.0/21 - in general, based on this, we leave this range in reserve.
In Kemerovo, it makes no sense for us to leave such huge reserves of / 21 as in St. Petersburg (2048 addresses or 8 subnets / 24), or even less so / 20, as in Moscow (4096 or 16 subnets / 24). But 1024 addresses and 4/24 subnets to which the / 22 mask corresponds is quite rational.
Thus, the network 172.16.24.0/22 (addresses 172.16.24.0-172.16.27.255) will be with us for Kemerovo.

Here it should be noted: making such a reserve is generally optional and what we have reserved can be used anywhere in the network. There is no taboo in this regard. However, in large networks, this is exactly what is recommended, and this is due to the amount of information in the routing tables.
Do you understand this: if you have several consecutive subnets scattered at different ends of the network, then each of them corresponds to one entry in the routing table of each router. If at the same time you suddenly use only static routing, then this is a colossal job to configure and track the correctness of the settings.
And if they all go in a row for you, then you can summarize several small subnets into one big one.
Let us illustrate with the example of St. Petersburg. When setting up static routing, we could do this:
These are 8 teams and 8 entries in the table. But at the same time, a packet arriving at the router to any of the 172.16.16.0/21 networks will in any case be sent to the device with the address 172.16.2.2.
Instead, we will do this:
And instead of eight possible comparisons, there will be only one.
For modern devices, neither in terms of processor time nor memory usage, this is no longer a significant burden, however, such planning is considered good practice and in the end, it’s easier for you to figure it out yourself.
But, honestly, such planning is an exception rather than a rule: one way or another, fragmentation of routes with the growth of the network is inevitable.
Now a few more words about “link” networks. In a network administrator environment, these are called point-to-point networks between two routers.
Here again, in the example with Peter. Two routers (in Moscow and St. Petersburg) are connected to each other by a direct link (it doesn’t matter that the provider has a hundred switches and routers - for us it’s just vlan). That is, apart from these 2 devices, there will not be any others here. We know this for sure. In any case, on the interfaces of both devices (looking towards each other), you need to configure IP addresses. And we definitely do not need to assign a network / 24 with 254 available addresses on this section, because 252 in this case will be lost in vain. In this case, there is a wonderful way out - classless IP addressing.
Why is she classless? If you remember, in the zero part we talked about three classes of subnets: A, B and C. In theory, you could only use them when planning a network. Classless cross-domain routing (CIDR ) allows very flexible use of the IP address space.
We just take the network with the smallest possible mask - 30 (255.255.255.252) - this is a network with 4 addresses. Why can't we take a network with an even narrower mask? Well 32 (255.255.255.255), for obvious reasons, is generally one single address, network 31 (255.255.255.254) is already 2 addresses, but one of them (the first) is the network address, and the second (last) is broadcast. As a result, we have nothing left for the host addresses. Therefore, we take the mask 30 with 4 addresses and then just 2 addresses remain on our two routers.
Generally speaking, the narrowest subnet mask in cisco is / 31. Under certain conditions, they can be used on PtP links.
As for the / 32 mask, such subnets, which are one single host, are used to assign addresses to Loopback interfaces.
That is what we will do. For this, in fact, in the zero part we left the network 172.16.2.0/24 - we will split it into small / 30 grids. In total there will be 64 of them, respectively, you can assign them to 64 links .
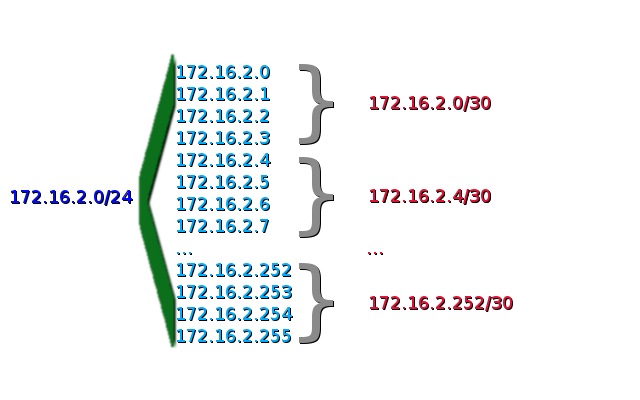
Here we did the same as in the previous case: made a small reserve for Peter, and a reserve for Kemerovo. In general, reserve is always very good no matter what we say. ;)
Before starting the configuration, you should decide what routing is needed for in general.
Consider the following network:

For example, from PC1 - 172.16.3.2, I want to connect via telnet to the L3 switch with the address 172.16.17.1.
How will my computer know what to do? Where to send the data?
1) As you already know, if the recipient address is from a different subnet, then the data must be sent to the default gateway.
2) According to the scheme already known to you, the computer uses the ARP request to obtain the MAC address of the router.
3) Then it forms a frame with the packet encapsulated in it and sends it to the port. After the frame is sent, the computer is already on the drum, what happens to it next.
4) And the frame itself then falls first to the switch, where its fate is decided according to the table of MAC addresses. And then it reaches router RT1.
5) Since the router restricts the broadcast domain - here the life of this frame ends. Tsiska simply throws back the link of the link layer - it will no longer be useful - it extracts the IP packet from it.
6) Now the router must decide what to do next. Of course, send it to some interface. But which one?
To do this, there is a routing table that is on any router. To find out what is currently in the routing table, you can use the show ip route command :
Each line in it is a way to get to a particular network.
For example, if the packet is addressed to the network 172.16.17.0/24, then the data must be sent to the device with the address 172.16.2.2.
The routing table is formed from:
- directly connected networks (directly connected) - these are networks that start directly on it. In the example, 172.16.3.0/24 and 172.16.2.0/30. In the table, they are indicated by the letter C
- static routes - these are the ones that you manually registered with the ip route command . The letter S denotes the
routes obtained using dynamic routing protocols (OSPF, EIGRP, RIP, and others).
7) So, the data in the network 172.16.17.0 (and we want to connect to the device 172.16.17.1) should be sent to the next hop - the next hop, which is the router 172.16.2.2. Moreover, the routing table shows that the next hop is behind the FE0 / 1.4 interface (subnet 172.16.2.0/30).
8) If there is no MAC address in the tsisk ARP cache, then you need to run the ARP request again to find out the MAC address of the device with the IP address 172.16.2.2. RT1 sends a broadcast frame from port FE0 / 1.4. In this broadcast domain, we have two devices, and accordingly only one recipient. RT2 receives an ARP request, discards the Ethernet header, and realizing from the data of the ARP protocol that the address it is looking for belongs to it, sends an ARP response with its MAC address.
9) The original IP packet received on RT1does not change , it is encapsulated in a completely new frame and sent to the FE0 / 1.4 port, while receiving the 4th Vlan label.
10) Completely similar actions occur on the next router. And on the next and next (if they were), until the packet reaches the last one, to which the necessary network is connected.
11) The last router sees that the address it is looking for belongs to itself, and when it extracts the data of the transport layer, it understands that it is a telnet and transfers all the data to the upper levels.
So the data travels from one hop to another and no router has any idea about the fate of the packet. Moreover, he does not even know if this network is really there - he simply trusts his routing table.
How do we organize communication channels? As we said above, in our office on Arbat there is a certain provider Balagan Telecom. He promises us to provide everything that we only want almost for nothing. And we order two L2VPN services from him, that is, he will give us two vlans on Arbat in Moscow, and one each in St. Petersburg and Kemerovo.
Generally speaking, you will have to coordinate the vlan numbers with your provider for the simple reason that they can simply be busy with it. Therefore, it is entirely possible that you will have a vlan, for example, 2912 or 754. But suppose we are lucky and we are free to choose the number ourselves.
On tsiska in Moscow, we have two interfaces, one is already connected to our local network, FE0 / 0, and we will use the second (FE0 / 1) to connect to the Internet and to connect remote offices.
As at the very beginning we will create sub-interfaces. For St. Petersburg and Kemerovo, we select 4 and 5 vlans, respectively. We take IP addresses from the new IP plan.
Of course, we will not build the entire network of the provider. Instead, we just put the switch, because in fact, the provider's network from our point of view will be one huge abstract switch.
Everything is simple here: we accept the trunk from Arbat to one port with a trunk and send them to the remote nodes from the other two ports. Once again, we want to emphasize that all these 3 ports do not belong to one switch - they are spaced hundreds of kilometers apart, between them is a complex MPLS network with a bunch of switches.
Set up the “provider emulator”:
Now turn to our spb-vsl-gw1. Here we also have 2 ports, but we will solve the issue of lack of ports otherwise: add a board here. A board with two FastEthernet ports and two slots for WIC is fine.
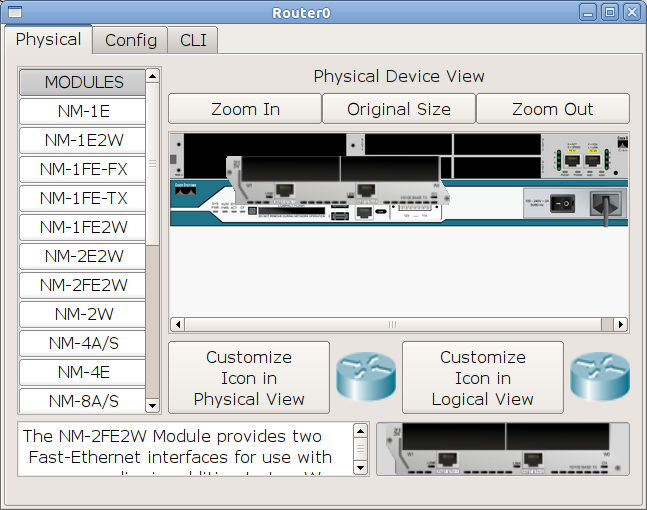
Let the built-in ports be for the local network, and we use the ports on the additional board for uplink and communication with Ozerki.
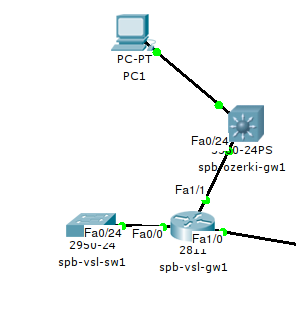
Here you can see the difference in port numbering and understand their meaning.
FastEthernet is the type of port (Ethernet, Fastethernet, GigabitEthernet, POS, Serial, or others)
x / y / zw = Slot / Sub-slot / Interface.Sub-interface.
How the provider will give you the channel here - trunk or access, you decide together. As a rule, none of the options would be a problem for him.
But we have already configured the trunk, so we accordingly configure the port on the tsiska:
Add another local network:
We will return to Moscow. With msk-arbat-gw1 we can see the address 172.16.2.2:
But also we do not see 172.16.16.1:
Again, because the router does not know where to send the packet:
Correct this misunderstanding:
Now ping appears:
Well, it would seem like happiness, but let's check the connection from the computer:
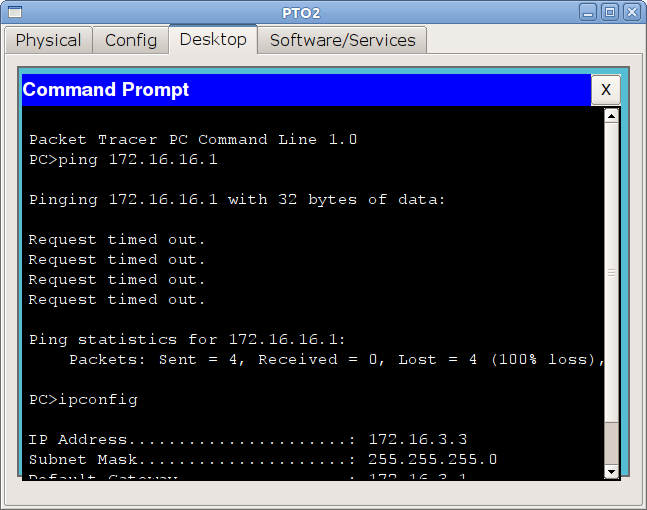
What's the matter ?!
The computer knows where to send the packet to its gateway 172.16.3.1, the router also knows to the host 172.16.2.2. The packet goes there, spb-vsl-gw1 is accepted, which knows that the pinged address 172.16.16.1 belongs to it. And you need to send a packet back to the address 172.16.3.3, but it does not have a route to the network 172.16.3.0. And packets whose destination network is unknown are simply dropped - discarded.
But, why, you ask, from msk-arbat-gw1 to 172.16.16.1 there was a ping? What is the difference 172.16.3.1 or 172.16.3.2? Everything is simple.
It can be seen from the routing table that the next hop is 172.16.2.2, and the address from 172.16.2.1 belongs to the interface of this router, therefore it is put in the header as the IP address of the sender, and not 172.16.3.1. The packet is sent to spb-vsl-gw1, it receives it, passes the data to the ping application, which generates an echo-reply. The response is encapsulated in an IP packet, where 172.16.2.1 appears as the recipient address, and 172.16.2.0/30 is the network directly connected to spb-vsl-gw1, so the packet is delivered without any problems. That is, the route is known on the 172.16.2.0/30 network, but not on 172.16.3.0/24.
To solve this problem, we can register a route to the 172.16.3.0 network on spb-vsl-gw1, but then we will have to register for all other networks. For all networks in Moscow, then in Kemerovo, then in other cities - a very large amount of configuration.
And here it is worth noting that in fact we have only one way out into the world - through Moscow. The node in the Lakes is a dead end, but there are no others. That is, basically all the data will go to Moscow, where most of the subnets will be connected to the Internet.
How can this help us? There is such a thing - the default route, also it bears the romantic name of the gateway - last hope. And there is an explanation for the second. When the router decides where to send the packet, it looks through the entire routing table and, if it does not find the desired route, the packet is discarded - this is if you haven’t configured the gateway of last resort, if configured, then the lonely packets are sent there - just without looking, providing the right to the next hop to decide their future fate. That is, if there is nowhere to send, then the last hope is the default route.
It is configured as follows:
And now tadaaam:
In the case of such dead-end areas, the gateway of last resort is often used to reduce the number of routes in the table and the complexity of the settings.
Now let's take care of the Lakes. Here we put the L3 switch. Suppose they are connected with us will be fiber rented from the provider (of course, this is an idealized situation for a small company, but you can dream about it).
The use of switches of the third level is very convenient in some cases. Firstly, interlacing routing in this case is done in hardware and does not load the processor, unlike a router. In addition, a single L3 switch will cost you significantly less than a separate L2 switch and router. True, at the same time you lose a number of functions, of course. Therefore, be careful when choosing a solution.
Configure the router on Vasilievsky Island, according to the plan:
Since we have already planned a network for Ozerkov 172.16.17.0/24, we can immediately register a route there:
As the next hop, we set the address that we allocated for the link network on Ozerki - 172.16.2.6
Now we will transfer to the Ozerki itself:
Connect the cable to the already configured port fa1 / 1 on the side of Vasilyevsky Island and to the 24th port 3560 in Ozerki.
By default, all ports of the L3 switch work in L2 mode, that is, these are the usual “switch” ports on which we can configure vlan. But we can put any of them into L3 mode, making it a router port. Then on it we can configure the IP address:
Check the connection:
Set up a local network. Recall that Cisco and other manufacturers and not only manufacturers do not recommend using the 1st vlan, therefore, we will use the 2nd:
After that, all devices in the second vlan will have a gateway 172.16.17.1
In order for the switch to turn into an almost full-fledged router, you need to give one more command:
This way we enable the routing feature.
We do not need any other routes except by default:
Communication to spb-vsl-gw1 is:
But to Moscow there:
Again, the lack of a route. Generally convenient tool for finding an approximate location of the traceroute problem:
As you can see, the answer comes from spb-vsl-gw1, and then it’s deaf. This means, as a rule, that either the hop to the address 172.16.2.5 does not have a route to the desired network (remember that we have configured a default route there, which is enough) or the next one has no route back:
Indeed, there is no route to the subnet 172.16.17.0/24. We can register it, you already know how to do it, but we can remember that we allocated the whole subnet 172.16.16.0/21 to St. Petersburg, so instead of adding a route to each new network individually, we will write an aggregated route:
We check:
But a strange surprise for you may be that with spb-ozerki-gw1 you will not see Moscow as before:
But at the same time, if we specify 172.16.17.1 as the source address:
And even from the computer 172.16.17.26 there is a connection:
How so? The answer, you won’t believe it, is just as simple - routing problems.
The fact is that msk-arbat-gw1 knows about the 172.16.17.0/24 subnet, but not about 172.16.2.4/30. Namely, the address 172.16.2.6 - the address of the interface closest to the destination (or the interface from which the IP packet is sent) substitutes by default as the source. This is not necessary to forget.
Another interesting experience: what if we write the address on the router on Vasilyevsky Island to the subnet 172.16.3.0/24 to Ozerki, and not to Moscow? Well, purely for fun. What will happen in this case?
In RT, you won’t see this, for some reason, but in real life you get a routing ring. The networks 172.16.3.0/24 and 172.16.16.0/21 will not see each other: the
packet coming from spb-ozerki-gw1 to the network 172.16.3.0 gets primarily to spb-vsl-gw1, where it says: “172.16.3.0/ 24 look for 172.16.2.6 ”, and this again is spb-ozerki-gw1, where it says:“ 172.16.3.0/24 look for 172.16.2.5 ”and so on. The packet will hop back and forth until the TTL field expires.
The fact is that when passing through each router, the TTL field in the IP header, initially having a value of 255, decreases by 1. And if it suddenly turns out that this value is 0, then the packet dies , or rather, the router that sees this will sprinkle it.
This ensures network stability - in the event of a loop, packets will not live indefinitely, loading the channel until it is fully utilized.
By the way, there is no such mechanism in Ethernet, and if you get a loop, then the switch will only do what to produce broadcast requests, completely clogging the channel - this is called a broadcast storm (this problem is solved using special technology \ STP protocol about this in the next release) .
In general, if you send ping from the network 172.16.17.0 to the address 172.16.3.1, then your IP packet will travel between the two routers until it expires, passing through the link between Ozerki and Vasilievsky Island 254 times.
By the way, a consequence of the work of this mechanism is that there cannot exist a coherent network where there are more than 255 routers between nodes. However, this is not a very urgent need. Now even the longest trail takes a couple of dozen hop-hopes.
Consider the last small example - a router on a stick.
The name is inspired by the connection scheme: The
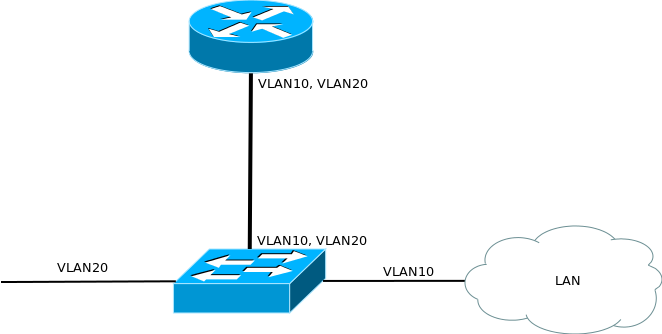
router is connected to the switch with only one cable, and traffic for both the local network and the external network is transmitted within different vlanes inside it. This is done, as a rule, to save money (there is only one port on the router and I do not want to buy an additional fee).
Connect as follows:
Switch configuration should no longer be a problem for you. On the UpLink interface, configure the 5th vlan trunk as agreed with the provider:
We will choose vlan 2 as the vlan for the local network and it’s nothing that it is already used in Moscow and St. Petersburg - if they don’t overlap and you can control it, then the numbers can match. Here, everyone decides for himself: you can use everywhere, for example, the 2nd Vlan, as a vlan of the local network or, on the contrary, develop a plan where the vlan numbers are unique throughout the network.
Trunk towards the router, where frames of external traffic will be tagged with the 5th vlan, and local traffic with the 2nd.
Router Setup:
We believe that you can now configure the routing between Moscow and Kemerovo on your own.
If routing is not all right for troubleshooting, you will need two commands:
and
The first one can be useful, as you saw, to set the source address. And the latter can be used with parameters, for example:
Despite the fact that there is no separate entry in the routing table for the 172.16.17.0 subnet, the router will show you what the next hop is.
And I would also like to repeat the most important things:
- When a data block arrives at the router, the Ethernet header is completely discarded and a completely new frame is formed upon sending. But the IP packet remains unchanged.
- In the case of static routing, each router decides on the fate of the packet exclusively on its own and does not know anything about other people's tables.
- The search in the table does NOT go until the first matching record is found, but until the most exact match is found (the narrowest mask). For example, if your routing table looks like this:
And you transfer the data to 172.16.10.5, then it will not go along the route through 172.16.2.22 or 172.16.2.26, but will select the narrowest mask (the longest) / 30 through 172.16.2.30.
- If the recipient's IP address does not match any entries in the routing table and the default route is configured (gateway of last resort), the packet will simply be discarded.
This is the first acquaintance with routing can be completed. It seems to us that the reader himself sees how many difficulties await him here, he can assume how much work he will face if the network grows to several dozen routers. But I must say that in the modern world, static routing, not only is not used, of course, it has a place, but in the vast majority of networks larger than the regional pioneer net, dynamic routing protocols are introduced. Among them are OSPF, EIGRP, IS-IS, RIP, to which we will devote a separate issue and, most likely, not one. But setting up static routing will greatly help your overall understanding of routing.
As an independent task, try to configure routing between Moscow and Kemerovo and answer the question why devices from the control network do not respond.
New IP plan, switching plans for each point and regulations.
RT file with laboratory.
Device configuration.
We apologize for the giant sheets, the video also becomes longer and more unbearable each time. We will try to be more compact next time.
All interested but unregistered are invited to speak on LiveJournal .
For the preparation of the article, many thanks to my co-author thegluck and my wife for the lion's patience.
The boy told dad: “I want to eat.” Dad sent him to mom.
The boy told his mother: “I want to eat.” Mom sent him to dad.
And so the boy ran, until at one moment he fell.
What happened to the boy? TTL is over.
All issues
8. Networks for the smallest. Part Eight. BGP and IP SLA
7. Networks for the smallest. Part Seven. VPN
6. Networks for the smallest. Part Six Dynamic Routing
5. Networks for the smallest: Part Five. NAT and ACL
4. Networks for the smallest: Part Four. STP
3. Networks for the smallest: Part Three. Static routing
2. Networks for the smallest. Part two. Switching
1. Networks for the smallest. Part one. Connecting to cisco
0. Networks for the smallest. Part zero. Planning
7. Networks for the smallest. Part Seven. VPN
6. Networks for the smallest. Part Six Dynamic Routing
5. Networks for the smallest: Part Five. NAT and ACL
4. Networks for the smallest: Part Four. STP
3. Networks for the smallest: Part Three. Static routing
2. Networks for the smallest. Part two. Switching
1. Networks for the smallest. Part one. Connecting to cisco
0. Networks for the smallest. Part zero. Planning
So, a turning point in the history of the company “Lift mi Up”. Management understands that a company manufacturing elevators traveling only up will not stand up in a highly competitive market. Need to expand the business. A decision was made to purchase two plants: in St. Petersburg and Kemerovo.
An urgent need to organize a connection to new offices, and you still have not even worked lokalka.
Today:
1. We configure routing between vlanes in our network (InterVlan routing)
2. We try to deal with the processes occurring in the network, and what is happening with the data.
3. We plan network expansion (IP addresses, vlana, switching tables)
4. We configure static routing and understand how it works.
5. We use the L3 switch as a gateway
Content:
- InterVlan Routing
- Expansion planning
- ... IP plan
- Routing Principles
- Customization
- ... Moscow. Arbat
- ... provider
- … St. Petersburg. Vasilievsky island
- … St. Petersburg. Lakes
- ... Kemerovo. Red hill
- Additionally
- Release Materials
InterVlan Routing
A little practice for cheering up.
The last time we configured the switches of our local network. At the moment, devices of different vlanes do not see each other. That is, in fact, FEO and VET, for example, are in completely different networks and are not connected to each other. Likewise, the server network exists by itself. It would be necessary to fix this annoying nuisance.
In our Moscow network, we will use the cisco 2811 router for routing between vlanes. In other words, it will terminate vlans. Frames here end their lives: IP packets are retrieved from them, and link layer headers are discarded.

The router setup process is very simple:
0) First, finish with the msk-arbat-dsw1 switch. On it we need to configure the trunk port towards the router, which we did not do the last time.
msk-arbat-dsw1 (config) #interface FastEthernet0 / 24
msk-arbat-dsw1 (config-if) # description msk-arbat-gw1
msk-arbat-dsw1 (config-if) # switchport trunk allowed vlan 2-3,101-104
msk-arbat-dsw1 (config-if) # switchport mode trunk
1) We assign the name of the router with the hostname command , and in order to develop a good tone, we must mention that it is better to immediately configure the time on the device. This will help you correctly identify log entries.
Router0 # clock set 12:34:56 august 2012
Router0 # conf t
Router0 (config) #hostname msk-arbat-gw1
It is advisable to distribute time to network devices via NTP (any tsisk can be made an NTP server, by the way)
2) Next, go to the configuration mode of the interface facing our local network and turn it on, since by default it is in the Administratively down state.
msk-arbat-gw1 (config) #interface fastEthernet 0/0
msk-arbat-gw1 (config-if) #no shutdown
3) Create a virtual interface or else it is called a subinterface or another subinterface (sub-interface).
msk-arbat-gw1 (config) #interface fa0 / 0.2
msk-arbat-gw1 (config-if) #description Management
The logic here is simple. First, we indicate in the usual way the physical interface to which the desired network is connected, and after the dot we put some unique identifier for this virtual interface. For convenience, usually the subinterface number is made similar to the vlan, which it terminates.
4) Now let's recall the 802.1q standard , which describes tagging a frame with a vlan label. By the following command, you indicate that frames coming from this virtual interface will be tagged with the 2nd display. And the frames entering the physical interface FastEthernet0 / 0 with the tag of this vlan will be accepted by the virtual interface FastEthernet0 / 0.2.
msk-arbat-gw1 (config-if) #encapsulation dot1Q 2
5) Well, just like on a regular physical L3 interface, let's determine the IP address. This address will be the default gateway for all devices in this vlan.
msk-arbat-gw1 (config-if) #ip address 172.16.1.1 255.255.255.0
Similarly, for example, configure the 101st vlan:
msk-arbat-gw1 (config) #interface FastEthernet0 / 0.101
msk-arbat-gw1 (config-if) #description PTO
msk-arbat-gw1 (config-if) #encapsulation dot1Q 101
msk-arbat-gw1 (config-if) #ip address 172.16.3.1 255.255.255.0
and now we’ll make sure that from the computer from the VET network we see the control network:

Works and fine, configure all the other interfaces for now. Problems with this should not arise.
Physics and logic of the inter-link routing process
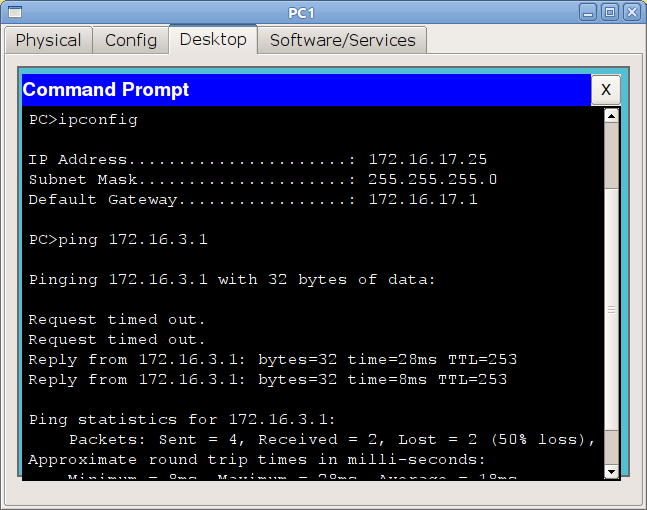
What happens to your data at this time?
The last time we discussed what happens if you try to connect to a device from the same subnet as you are.
By the same subnet we mean the following.
For example, the following is configured on your computer:
IP: 172.16.3.2
Mask: 255.255.255.0
GW: 172.16.3.1
All devices whose addresses will be in the range 172.16.3.1-172.16.3.254 with the same mask as yours will be members your subnet. What happens to the data if you send it to a device with an address in this range?
Repeat this with some additions.
To send data, they must be packed into an Ethernet frame, in the header of which the MAC address of the remote device must be inserted. But where to get it?
To do this, your computer sends out a broadcast ARP request. The IP address of the destination host will be placed in the IP packet with this request as the IP address of the destination host. When encapsulated, the network card indicates the MAC address FF: FF: FF: FF: FF: FF - this means that the frame is intended for all devices. Then it goes to the nearest switch and copies are sent to all ports of our Vlan (well, except, of course, the port from which the frame was received). Recipients see that the request is broadcast and they may turn out to be the desired host, therefore, they extract data from the frame. All those devices that do not have the IP address specified in the ARP request simply ignore the request, but the real receiver will respond to it and send its original MAC address to the original sender. Sender (in this case, our computer) puts the received MAC in its IP and MAC address mapping table aka ARP cache. What does the ARP cache look like on your computer right now, you can see with the commandarp -a

Then your useful data is packed into an IP packet, where the address you specified in the command / application is put as the recipient, then into the Ethernet frame, in the header of which the MAC address received by the ARP request is placed. Next, the frame is sent to the switch, which, according to its table of MAC addresses, decides which port to forward it to.
But what happens if you try to reach the device in another vlan? An ARP request will not return anything, because broadcast L2 messages end on the router (i.e., within the broadcast L2 domain), the desired network is located behind it, and the switch will not send frames from one vlan to the port of another. And for this, you need a default gateway on your computer.
That is, if the recipient device is on your own subnet, the frame is simply sent to the port with the mac address of the final recipient. If the message is addressed to any other subnet, the frame is sent to the default gateway, therefore, the MAC address of the receiver is set to the MAC address of the router.
We follow the course of events.
1) The PC with the address 172.16.3.2/24 wants to send data to the computer with the address 172.16.4.5.

He sees that the address is from a different subnet, therefore, the data should go to the default gateway. But in this case, the PC needs the MAC address of the gateway. The PC checks its ARP cache to find the match. The IP address of the gateway is the MAC address and does not find the right one.

2) The PC sends a broadcast ARP request to the local network. ARP request structure:
- at the channel level, as the recipient - the broadcast address (FF: FF: FF: FF: FF: FF), as the sender - the MAC address of the interface of the device trying to find out the IP
- on the network - actually the ARP request, it contains information about what IP and by whom it is searched.

3) The switch to which the frame was sent sends its copies to all ports of this vlan (the one to which the original host belongs), except where it was received from.
4) All devices, having received this frame and seeing that it is broadcast, assume that it is addressed to them.
5) Having unpacked the frame, all hosts except the router see that their address is not in the ARP request. And the router sends a unicast ARP response with its MAC address.
6) The original host receives an ARP response, now it has the MAC address of the gateway. He forms a packet from the data that he needs to send to 172.16.4.5. The PC sets the gateway address as the destination MAC address. In this case , the recipient's IP address in the packet remains 172.16.4.5

7) The frame is sent to the network, the switches deliver it to the router.
8) On the router, in accordance with the Vlan label, the frame is received by a specific subinterface. Link level data is reclined .
9) From the header of the IP packet, the router learns the recipient’s address, and from its routing table sees that it is in the network directly connected to it at a specific subinterface (in our case FE0 / 0.102).
C 172.16.0.0/24 is directly connected, FastEthernet0 / 0.3
C 172.16.1.0/24 is directly connected, FastEthernet0 / 0.2
C 172.16.2.16/30 is directly connected, FastEthernet0 / 1.5
C 172.16.3.0/24 is directly connected, FastEthernet0 /0.101
C 172.16.4.0/24 is directly connected, FastEthernet0 /
0.103
C 172.16.6.0/24 is directly connected, FastEthernet0 / 0.104
10) The router sends an ARP request from this subinterface - it recognizes the MAC address of the recipient.
11) The original IP packet, without changing, is encapsulated in a new frame , while:
- the gateway interface address is specified as the source MAC address - the source
IP address is the address of the original host (in our case 172.16.3.2)
- as MAC the recipient’s address indicates the address of the final host
— the recipient’s IP address — the address of the final host (in our case 172.16.4.5)
and is sent to the network from the FastEthernet0 / 0.102 subinterface, receiving the label of the 102nd vlan.
12) The frame is delivered by the switches to the destination host.
Expansion planning
Now let's turn to planning. In the zero part, we already touched on this topic, but then we were talking only about two offices in Moscow, now the network is growing.
It will be like this:

That is, two points are added in St. Petersburg: a small office on Vasilievsky Island and the factory in Ozerki itself, and one in Kemerovo in the Krasnaya Gorka area.
For simplicity, we will have one provider “Balagan Telecom”, which on favorable terms will provide us with L2VPN to both points.
In one of the next issues, we will reveal the topic of various connection options in paints. In the meantime, in short: L2VPN is, very roughly speaking, when a provider provides you with a vlan from point to point (for simplicity, you can imagine that they are included in one switch).
A few words should be said about IP addressing and subnetting.
In the zero part, we have already touched upon planning issues, and I must say very casually.
In general, in any more or less large company there should be some kind of regulation - a set of rules, following which you distribute IP addresses everywhere. Our network is expanding now and developing it is very important.
Well, for example, let's say that for offices in other cities it will be like this:

This is a very simplified regulation, but now, in any case, we know for sure that the gateway will always have the 1st address, until the 12th we will give out to the switches and any wi-fi points, and we will look for all servers in the range 172.16.x .13-172.16.x.23. Of course, to your taste, you can specify the rules down to the address of each server, add the rule for generating device names, domain names, access list policies, etc. to it.
The more accurately you formulate the rules and more closely monitor their implementation, the easier it is to understand the structure of the network, solve problems, adapt to the situation
It’s about a pattern of remembering passwords: when you have a certain rule for their formation, you do not need to keep a few dozen hard-to-remember passwords in your head, you can always calculate them.
That's the same here. I once worked in a medium-sized holding company and knew that if I come to the office somewhere in a village forgotten by cows, then there xyz1 is the tsiska, xyz2 is the distribution switch of the procurator, and xyz101 is the computer of the chief accountant from whom you must give access to some external circuit. Another question is that we still need to check it, because local IT specialists sometimes do such a thing that you wash yourself with tears through laughter.
It was the case the guy decided to manage all Internet access himself (I usually did this on the router). I installed a proxy server, accidentally raised NAT on it and taxied the local network traffic there, setting it on all machines as a default gateway, and then I figured it out for about 20 minutes, like this: everything works for them, but we don’t see them.
IP plan
Now it would be very useful for us to draw up an IP plan. We will proceed from the fact that at all three points we will use a standard network with a 24-bit mask (255.255.255.0) This means that there can be 254 devices in them.
Why is this so? And how do you understand all of these subnet masks? In the framework of one article, we will not be able to tell this, otherwise it will turn out to be as long as the deck of the Titanic and tangled like Odessa catacombs. We strongly recommend that you familiarize yourself with such concepts as IP address, subnet mask, their binary representation and CIDR (Classless InterDomain Routing) yourself. We will only argue the choice of a specific network size. Be that as it may, full understanding will come only with practice.
In general, this topic is very well disclosed in this article:http://habrahabr.ru/post/129664/
At the moment (remember the zero issue ) in Moscow we used the addresses 172.16.0.0-172.16.6.255. Suppose that the network can still grow here, for example, an office appears on the Sparrow Hills and reserve another subnet until 172.16.15.0/24 inclusive.
All these addresses: 172.16.0.0-172.16.15.255 - can be described as follows: 172.16.0.0/20. This network (with the / 20 prefix) will be the so-called supernet , and the operation of combining subnets in the supernets is called summing subnets (summing routes, to be precise, route summarization)
Very intuitive IP-calculator. I now use it periodically, although over time an intuitive and logical understanding of the correspondence between the length of the mask and the boundaries of the network comes.
Now let's turn to Peter. At the moment, in this beautiful city, we have 2 points and each of them has a subnet / 24. Let's say it will be 172.16.16.0/24 and 172.16.17.0/24. We reserve the addresses 172.16.18.0-172.16.23.255 for a possible expansion of the network.
172.16.16.0-172.16.23.255 can be combined into 172.16.16.0/21 - in general, based on this, we leave this range in reserve.
In Kemerovo, it makes no sense for us to leave such huge reserves of / 21 as in St. Petersburg (2048 addresses or 8 subnets / 24), or even less so / 20, as in Moscow (4096 or 16 subnets / 24). But 1024 addresses and 4/24 subnets to which the / 22 mask corresponds is quite rational.
Thus, the network 172.16.24.0/22 (addresses 172.16.24.0-172.16.27.255) will be with us for Kemerovo.

Here it should be noted: making such a reserve is generally optional and what we have reserved can be used anywhere in the network. There is no taboo in this regard. However, in large networks, this is exactly what is recommended, and this is due to the amount of information in the routing tables.
Do you understand this: if you have several consecutive subnets scattered at different ends of the network, then each of them corresponds to one entry in the routing table of each router. If at the same time you suddenly use only static routing, then this is a colossal job to configure and track the correctness of the settings.
And if they all go in a row for you, then you can summarize several small subnets into one big one.
Let us illustrate with the example of St. Petersburg. When setting up static routing, we could do this:
ip route 172.16.16.0 255.255.255.0 172.16.2.2
ip route 172.16.17.0 255.255.255.0 172.16.2.2
ip route 172.16.18.0 255.255.255.0 172.16.2.2
.......
ip route 172.16.23.0 255.255.255.0 172.16.2.2
These are 8 teams and 8 entries in the table. But at the same time, a packet arriving at the router to any of the 172.16.16.0/21 networks will in any case be sent to the device with the address 172.16.2.2.
Instead, we will do this:
ip route 172.16.16.0 255.255.248.0 172.16.2.2
And instead of eight possible comparisons, there will be only one.
For modern devices, neither in terms of processor time nor memory usage, this is no longer a significant burden, however, such planning is considered good practice and in the end, it’s easier for you to figure it out yourself.
But, honestly, such planning is an exception rather than a rule: one way or another, fragmentation of routes with the growth of the network is inevitable.
Now a few more words about “link” networks. In a network administrator environment, these are called point-to-point networks between two routers.
Here again, in the example with Peter. Two routers (in Moscow and St. Petersburg) are connected to each other by a direct link (it doesn’t matter that the provider has a hundred switches and routers - for us it’s just vlan). That is, apart from these 2 devices, there will not be any others here. We know this for sure. In any case, on the interfaces of both devices (looking towards each other), you need to configure IP addresses. And we definitely do not need to assign a network / 24 with 254 available addresses on this section, because 252 in this case will be lost in vain. In this case, there is a wonderful way out - classless IP addressing.
Why is she classless? If you remember, in the zero part we talked about three classes of subnets: A, B and C. In theory, you could only use them when planning a network. Classless cross-domain routing (CIDR ) allows very flexible use of the IP address space.
We just take the network with the smallest possible mask - 30 (255.255.255.252) - this is a network with 4 addresses. Why can't we take a network with an even narrower mask? Well 32 (255.255.255.255), for obvious reasons, is generally one single address, network 31 (255.255.255.254) is already 2 addresses, but one of them (the first) is the network address, and the second (last) is broadcast. As a result, we have nothing left for the host addresses. Therefore, we take the mask 30 with 4 addresses and then just 2 addresses remain on our two routers.
Generally speaking, the narrowest subnet mask in cisco is / 31. Under certain conditions, they can be used on PtP links.
As for the / 32 mask, such subnets, which are one single host, are used to assign addresses to Loopback interfaces.
That is what we will do. For this, in fact, in the zero part we left the network 172.16.2.0/24 - we will split it into small / 30 grids. In total there will be 64 of them, respectively, you can assign them to 64 links .

Here we did the same as in the previous case: made a small reserve for Peter, and a reserve for Kemerovo. In general, reserve is always very good no matter what we say. ;)
Routing Principles
Before starting the configuration, you should decide what routing is needed for in general.
Consider the following network:

For example, from PC1 - 172.16.3.2, I want to connect via telnet to the L3 switch with the address 172.16.17.1.
How will my computer know what to do? Where to send the data?
1) As you already know, if the recipient address is from a different subnet, then the data must be sent to the default gateway.
2) According to the scheme already known to you, the computer uses the ARP request to obtain the MAC address of the router.
3) Then it forms a frame with the packet encapsulated in it and sends it to the port. After the frame is sent, the computer is already on the drum, what happens to it next.
4) And the frame itself then falls first to the switch, where its fate is decided according to the table of MAC addresses. And then it reaches router RT1.
5) Since the router restricts the broadcast domain - here the life of this frame ends. Tsiska simply throws back the link of the link layer - it will no longer be useful - it extracts the IP packet from it.
6) Now the router must decide what to do next. Of course, send it to some interface. But which one?
To do this, there is a routing table that is on any router. To find out what is currently in the routing table, you can use the show ip route command :
172.16.0.0/16 is variably subnetted, 10 subnets, 3 masks
C 172.16.3.0/24 is directly connected, FastEthernet0 / 0.101
C 172.16.2.0/30 is directly connected, FastEthernet0 / 1.4
S 172.16.17.0/24 [1/0 ] via 172.16.2.2
Each line in it is a way to get to a particular network.
For example, if the packet is addressed to the network 172.16.17.0/24, then the data must be sent to the device with the address 172.16.2.2.
The routing table is formed from:
- directly connected networks (directly connected) - these are networks that start directly on it. In the example, 172.16.3.0/24 and 172.16.2.0/30. In the table, they are indicated by the letter C
- static routes - these are the ones that you manually registered with the ip route command . The letter S denotes the
routes obtained using dynamic routing protocols (OSPF, EIGRP, RIP, and others).
7) So, the data in the network 172.16.17.0 (and we want to connect to the device 172.16.17.1) should be sent to the next hop - the next hop, which is the router 172.16.2.2. Moreover, the routing table shows that the next hop is behind the FE0 / 1.4 interface (subnet 172.16.2.0/30).
8) If there is no MAC address in the tsisk ARP cache, then you need to run the ARP request again to find out the MAC address of the device with the IP address 172.16.2.2. RT1 sends a broadcast frame from port FE0 / 1.4. In this broadcast domain, we have two devices, and accordingly only one recipient. RT2 receives an ARP request, discards the Ethernet header, and realizing from the data of the ARP protocol that the address it is looking for belongs to it, sends an ARP response with its MAC address.
9) The original IP packet received on RT1does not change , it is encapsulated in a completely new frame and sent to the FE0 / 1.4 port, while receiving the 4th Vlan label.
10) Completely similar actions occur on the next router. And on the next and next (if they were), until the packet reaches the last one, to which the necessary network is connected.
11) The last router sees that the address it is looking for belongs to itself, and when it extracts the data of the transport layer, it understands that it is a telnet and transfers all the data to the upper levels.
So the data travels from one hop to another and no router has any idea about the fate of the packet. Moreover, he does not even know if this network is really there - he simply trusts his routing table.
Customization
How do we organize communication channels? As we said above, in our office on Arbat there is a certain provider Balagan Telecom. He promises us to provide everything that we only want almost for nothing. And we order two L2VPN services from him, that is, he will give us two vlans on Arbat in Moscow, and one each in St. Petersburg and Kemerovo.
Generally speaking, you will have to coordinate the vlan numbers with your provider for the simple reason that they can simply be busy with it. Therefore, it is entirely possible that you will have a vlan, for example, 2912 or 754. But suppose we are lucky and we are free to choose the number ourselves.
Moscow. Arbat
On tsiska in Moscow, we have two interfaces, one is already connected to our local network, FE0 / 0, and we will use the second (FE0 / 1) to connect to the Internet and to connect remote offices.
As at the very beginning we will create sub-interfaces. For St. Petersburg and Kemerovo, we select 4 and 5 vlans, respectively. We take IP addresses from the new IP plan.
msk-arbat-gw1(config)#interface FastEthernet 0/1.4
msk-arbat-gw1(config-subif)#description Saint-Petersburg
msk-arbat-gw1(config-subif)#encapsulation dot1Q 4
msk-arbat-gw1(config-subif)#ip address 172.16.2.1 255.255.255.252
msk-arbat-gw1(config)#interface FastEthernet 0/1.5
msk-arbat-gw1(config-subif)#description Kemerovo
msk-arbat-gw1(config-subif)#encapsulation dot1Q 5
msk-arbat-gw1(config-subif)#ip address 172.16.2.17 255.255.255.252
Провайдер
Of course, we will not build the entire network of the provider. Instead, we just put the switch, because in fact, the provider's network from our point of view will be one huge abstract switch.
Everything is simple here: we accept the trunk from Arbat to one port with a trunk and send them to the remote nodes from the other two ports. Once again, we want to emphasize that all these 3 ports do not belong to one switch - they are spaced hundreds of kilometers apart, between them is a complex MPLS network with a bunch of switches.
Set up the “provider emulator”:
Switch(config)#vlan 4
Switch(config-vlan)#vlan 5
Switch(config)#interface fa0/1
Switch(config-if)#switchport mode trunk
Switch(config-if)#switchport trunk allowed vlan 4-5
Switch(config-if)#exit
Switch(config)#int fa0/2
Switch(config-if)#switchport trunk allowed vlan 4
Switch(config-if)#int fa0/3
Switch(config-if)#switchport trunk allowed vlan 5
Санкт-Петербург. Васильевский остров
Now turn to our spb-vsl-gw1. Here we also have 2 ports, but we will solve the issue of lack of ports otherwise: add a board here. A board with two FastEthernet ports and two slots for WIC is fine.

Let the built-in ports be for the local network, and we use the ports on the additional board for uplink and communication with Ozerki.

Here you can see the difference in port numbering and understand their meaning.
FastEthernet is the type of port (Ethernet, Fastethernet, GigabitEthernet, POS, Serial, or others)
x / y / zw = Slot / Sub-slot / Interface.Sub-interface.
How the provider will give you the channel here - trunk or access, you decide together. As a rule, none of the options would be a problem for him.
But we have already configured the trunk, so we accordingly configure the port on the tsiska:
spb-vsl-gw1 (config) interface FastEthernet1 / 0.4
spb-vsl-gw1 (config-if) description Moscow
spb-vsl-gw1 (config-if) encapsulation dot1Q 4
spb-vsl-gw1 (config-if) ip address 172.16 .2.2 255.255.255.252
Add another local network:
spb-vsl-gw1 (config) #int fa0 / 0
spb-vsl-gw1 (config-if) #description LAN
spb-vsl-gw1 (config-if) #ip address 172.16.16.1 255.255.255.0
We will return to Moscow. With msk-arbat-gw1 we can see the address 172.16.2.2:
msk-arbat-gw1 # ping 172.16.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.2.2, timeout is 2 seconds:
!!!
Success rate is 100 percent (5/5), round-trip min / avg / max = 2/7/13 ms
But also we do not see 172.16.16.1:
msk-arbat-gw1 # ping 02.16.16.16.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.16.1, timeout is 2 seconds:
...
Success rate is 0 percent (0/5)
Again, because the router does not know where to send the packet:
msk-arbat-gw1 # sh ip route
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 8 subnets, 2 masks
C 172.16.0.0/24 is directly connected, FastEthernet0 / 0.3
C 172.16.1.0/24 is directly connected, FastEthernet0 / 0.2
C 172.16.2.0/30 is directly connected, FastEthernet0 / 1.4
C 172.16.3.0/24 is directly connected, FastEthernet0 / 0.101
C 172.16.4.0/24 is directly connected, FastEthernet0 / 0.102
C 172.16.5.0/ 24 is directly connected, FastEthernet0 /
0.104 C 172.16.6.0/24 is directly connected, FastEthernet0 / 0.104
Correct this misunderstanding:
msk-arbat-gw1(config)#ip route 172.16.16.0 255.255.255.0 172.16.2.2
msk-arbat-gw1#sh ip route
Codes: C — connected, S — static, I — IGRP, R — RIP, M — mobile, B — BGP
D — EIGRP, EX — EIGRP external, O — OSPF, IA — OSPF inter area
N1 — OSPF NSSA external type 1, N2 — OSPF NSSA external type 2
E1 — OSPF external type 1, E2 — OSPF external type 2, E — EGP
i — IS-IS, L1 — IS-IS level-1, L2 — IS-IS level-2, ia — IS-IS inter area
* — candidate default, U — per-user static route, o — ODR
P — periodic downloaded static route
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 9 subnets, 2 masks
C 172.16.0.0/24 is directly connected, FastEthernet0/0.3
C 172.16.1.0/24 is directly connected, FastEthernet0 / 0.2
C 172.16.2.0/30 is directly connected, FastEthernet0 / 1.4
C 172.16.2.16/30 is directly connected, FastEthernet0 / 1.5
C 172.16.3.0/24 is directly connected, FastEthernet0 /0.101
C 172.16.4.0/24 is directly connected, FastEthernet0 /
0.103
C 172.16.6.0/24 is directly connected, FastEthernet0 / 0.104
S 172.16.16.0/24 [1 / 0] via 172.16.2.2
Now ping appears:
msk-arbat-gw1 # ping 02.16.16.16.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.16.1, timeout is 2 seconds:
!!!
Success rate is 100 percent (5/5), round-trip min / avg / max = 4/10/24 ms
Well, it would seem like happiness, but let's check the connection from the computer:

What's the matter ?!
The computer knows where to send the packet to its gateway 172.16.3.1, the router also knows to the host 172.16.2.2. The packet goes there, spb-vsl-gw1 is accepted, which knows that the pinged address 172.16.16.1 belongs to it. And you need to send a packet back to the address 172.16.3.3, but it does not have a route to the network 172.16.3.0. And packets whose destination network is unknown are simply dropped - discarded.
spb-vsl-gw1 # sh ip route
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
C 172.16.2.0/30 is directly connected, FastEthernet1 / 0.4
C 172.16.16.0/24 is directly connected, FastEthernet0 / 0
But, why, you ask, from msk-arbat-gw1 to 172.16.16.1 there was a ping? What is the difference 172.16.3.1 or 172.16.3.2? Everything is simple.
It can be seen from the routing table that the next hop is 172.16.2.2, and the address from 172.16.2.1 belongs to the interface of this router, therefore it is put in the header as the IP address of the sender, and not 172.16.3.1. The packet is sent to spb-vsl-gw1, it receives it, passes the data to the ping application, which generates an echo-reply. The response is encapsulated in an IP packet, where 172.16.2.1 appears as the recipient address, and 172.16.2.0/30 is the network directly connected to spb-vsl-gw1, so the packet is delivered without any problems. That is, the route is known on the 172.16.2.0/30 network, but not on 172.16.3.0/24.
To solve this problem, we can register a route to the 172.16.3.0 network on spb-vsl-gw1, but then we will have to register for all other networks. For all networks in Moscow, then in Kemerovo, then in other cities - a very large amount of configuration.
And here it is worth noting that in fact we have only one way out into the world - through Moscow. The node in the Lakes is a dead end, but there are no others. That is, basically all the data will go to Moscow, where most of the subnets will be connected to the Internet.
How can this help us? There is such a thing - the default route, also it bears the romantic name of the gateway - last hope. And there is an explanation for the second. When the router decides where to send the packet, it looks through the entire routing table and, if it does not find the desired route, the packet is discarded - this is if you haven’t configured the gateway of last resort, if configured, then the lonely packets are sent there - just without looking, providing the right to the next hop to decide their future fate. That is, if there is nowhere to send, then the last hope is the default route.
It is configured as follows:
spb-vsl-gw1 (config) #ip route 0.0.0.0 0.0.0.0 172.16.2.1
And now tadaaam:

In the case of such dead-end areas, the gateway of last resort is often used to reduce the number of routes in the table and the complexity of the settings.
St. Petersburg. Lakes
Now let's take care of the Lakes. Here we put the L3 switch. Suppose they are connected with us will be fiber rented from the provider (of course, this is an idealized situation for a small company, but you can dream about it).
The use of switches of the third level is very convenient in some cases. Firstly, interlacing routing in this case is done in hardware and does not load the processor, unlike a router. In addition, a single L3 switch will cost you significantly less than a separate L2 switch and router. True, at the same time you lose a number of functions, of course. Therefore, be careful when choosing a solution.
Configure the router on Vasilievsky Island, according to the plan:
spb-vsl-gw1 (config) interface fa1 / 1
spb-vsl-gw1 (config-if) #description Ozerki
spb-vsl-gw1 (config-if) #ip address 172.16.2.5 255.255.255.252
Since we have already planned a network for Ozerkov 172.16.17.0/24, we can immediately register a route there:
spb-vsl-gw1 (config) #ip route 172.16.17.0 255.255.255.0 172.16.2.6
As the next hop, we set the address that we allocated for the link network on Ozerki - 172.16.2.6
Now we will transfer to the Ozerki itself:
Connect the cable to the already configured port fa1 / 1 on the side of Vasilyevsky Island and to the 24th port 3560 in Ozerki.
By default, all ports of the L3 switch work in L2 mode, that is, these are the usual “switch” ports on which we can configure vlan. But we can put any of them into L3 mode, making it a router port. Then on it we can configure the IP address:
Switch (config) #hostname spb-ozerki-gw1
spb-ozerki-gw1 (config) #interface fa0 / 24
spb-ozerki-gw1 (config-if) #no switchport
spb-ozerki-gw1 (config-if) #ip address 172.16.2.6 255.255.255.252
Check the connection:
spb-ozerki-gw1 # ping 172.16.2.5
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.2.5, timeout is 2 seconds:.
!!!
Success rate is 80 percent (4/5), round-trip min / avg / max = 1/18/61 ms
Set up a local network. Recall that Cisco and other manufacturers and not only manufacturers do not recommend using the 1st vlan, therefore, we will use the 2nd:
spb-ozerki-gw1 (config) #vlan 2
spb-ozerki-gw1 (config-vlan) #name LAN
spb-ozerki-gw1 (config-vlan) #exit
spb-ozerki-gw1 (config) #interface vlan 2
spb- ozerki-gw1 (config-if) #description LAN
spb-ozerki-gw1 (config-if) #ip address 172.16.17.1 255.255.255.0
spb-ozerki-gw1 (config) #interface fastEthernet 0/1
spb-ozerki-gw1 ( config-if) #description Pupkin
spb-ozerki-gw1 (config-if) #switchport mode access
spb-ozerki-gw1 (config-if) #switchport access vlan 2
After that, all devices in the second vlan will have a gateway 172.16.17.1

In order for the switch to turn into an almost full-fledged router, you need to give one more command:
spb-ozerki-gw1 (config) #ip routing
This way we enable the routing feature.
We do not need any other routes except by default:
spb-ozerki-gw1 (config) #ip route 0.0.0.0 0.0.0.0 172.16.2.5
Communication to spb-vsl-gw1 is:
spb-ozerki-gw1 # ping 02.16.16.16.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.16.1, timeout is 2 seconds:
!!!
Success rate is 100 percent (5/5), round-trip min / avg / max = 3/50/234 ms
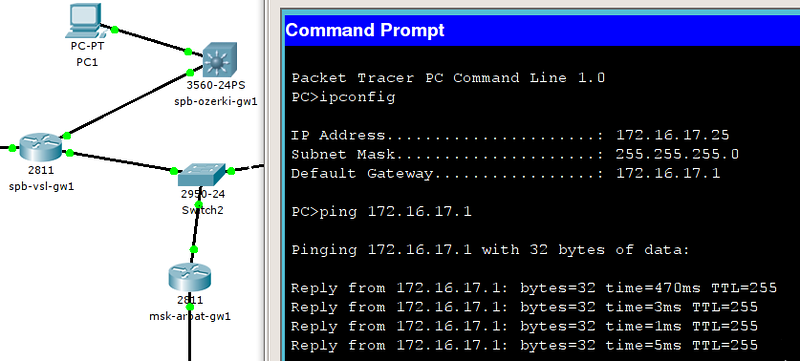
But to Moscow there:
spb-ozerki-gw1 # ping 172.16.3.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.3.1, timeout is 2 seconds:
...
Success rate is 0 percent (0/5)
Again, the lack of a route. Generally convenient tool for finding an approximate location of the traceroute problem:
spb-ozerki-gw1 # traceroute 172.16.3.1
Type escape sequence to abort.
Tracing the route to 172.16.3.1
1 172.16.2.5 4 msec 2 msec 5 msec
2 * * *
3 * * *
4 *
As you can see, the answer comes from spb-vsl-gw1, and then it’s deaf. This means, as a rule, that either the hop to the address 172.16.2.5 does not have a route to the desired network (remember that we have configured a default route there, which is enough) or the next one has no route back:
msk-arbat-gw1#sh ip rou
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 9 subnets, 2 masks
C 172.16.0.0/24 is directly connected, FastEthernet0/0.3
C 172.16.1.0/24 is directly connected, FastEthernet0/0.2
C 172.16.2.0/30 is directly connected, FastEthernet0/1.4
C 172.16.2.16/30 is directly connected, FastEthernet0/1.5
C 172.16.3.0/24 is directly connected, FastEthernet0/0.101
C 172.16.4.0/24 is directly connected, FastEthernet0/0.102
C 172.16.5.0/24 is directly connected, FastEthernet0/0.103
C 172.16.6.0/24 is directly connected, FastEthernet0/0.104
S 172.16.16.0/24 [1/0] via 172.16.2.2
Indeed, there is no route to the subnet 172.16.17.0/24. We can register it, you already know how to do it, but we can remember that we allocated the whole subnet 172.16.16.0/21 to St. Petersburg, so instead of adding a route to each new network individually, we will write an aggregated route:
msk-arbat-gw1 (config) #no ip route 172.16.16.0 255.255.255.0 172.16.2.2
msk-arbat-gw1 (config) #ip route 172.16.16.0 255.255.248.0 172.16.2.2
We check:
msk-arbat-gw1 # ping 172.16.17.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.17.1, timeout is 2 seconds:
!!!
Success rate is 100 percent (5/5), round-trip min / avg / max = 4/10/18 ms
But a strange surprise for you may be that with spb-ozerki-gw1 you will not see Moscow as before:
spb-ozerki-gw1 # ping 172.16.3.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.3.1, timeout is 2 seconds:
...
Success rate is 0 percent (0/5)
But at the same time, if we specify 172.16.17.1 as the source address:
spb-ozerki-gw1#ping
Protocol [ip]:
Target IP address: 172.16.3.1
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: ping172.16.17.1
% Invalid source
Source address or interface: 172.16.17.1
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.3.1, timeout is 2 seconds:
Packet sent with a source address of 172.16.17.1
!!!
Success rate is 100 percent (5/5), round-trip min / avg / max = 5/9/14 ms
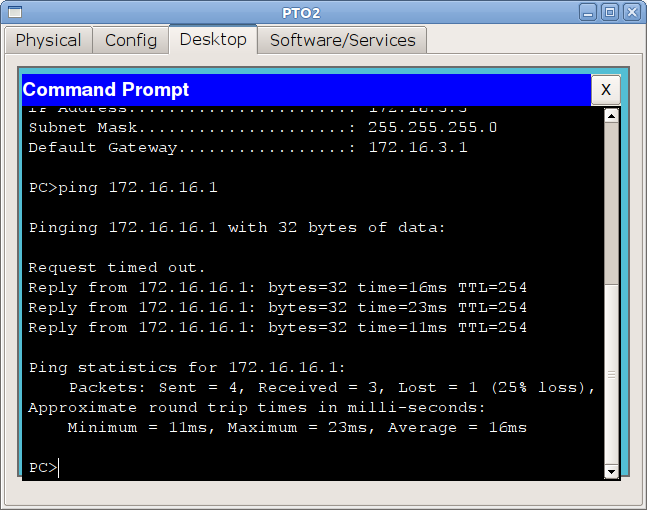
And even from the computer 172.16.17.26 there is a connection:

How so? The answer, you won’t believe it, is just as simple - routing problems.
The fact is that msk-arbat-gw1 knows about the 172.16.17.0/24 subnet, but not about 172.16.2.4/30. Namely, the address 172.16.2.6 - the address of the interface closest to the destination (or the interface from which the IP packet is sent) substitutes by default as the source. This is not necessary to forget.
msk-arbat-gw1 (config) #ip route 172.16.2.4 255.255.255.252 172.16.2.2
spb-ozerki-gw1 # ping 172.16.3.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.3.1, timeout is 2 seconds:
!!!
Success rate is 100 percent (5/5), round-trip min / avg / max = 7/62/269 ms
Another interesting experience: what if we write the address on the router on Vasilyevsky Island to the subnet 172.16.3.0/24 to Ozerki, and not to Moscow? Well, purely for fun. What will happen in this case?
spb-vsl-gw1 (config) #ip route 172.16.3.0 255.255.255.0 172.16.2.6
In RT, you won’t see this, for some reason, but in real life you get a routing ring. The networks 172.16.3.0/24 and 172.16.16.0/21 will not see each other: the
packet coming from spb-ozerki-gw1 to the network 172.16.3.0 gets primarily to spb-vsl-gw1, where it says: “172.16.3.0/ 24 look for 172.16.2.6 ”, and this again is spb-ozerki-gw1, where it says:“ 172.16.3.0/24 look for 172.16.2.5 ”and so on. The packet will hop back and forth until the TTL field expires.
The fact is that when passing through each router, the TTL field in the IP header, initially having a value of 255, decreases by 1. And if it suddenly turns out that this value is 0, then the packet dies , or rather, the router that sees this will sprinkle it.
This ensures network stability - in the event of a loop, packets will not live indefinitely, loading the channel until it is fully utilized.
By the way, there is no such mechanism in Ethernet, and if you get a loop, then the switch will only do what to produce broadcast requests, completely clogging the channel - this is called a broadcast storm (this problem is solved using special technology \ STP protocol about this in the next release) .
In general, if you send ping from the network 172.16.17.0 to the address 172.16.3.1, then your IP packet will travel between the two routers until it expires, passing through the link between Ozerki and Vasilievsky Island 254 times.
By the way, a consequence of the work of this mechanism is that there cannot exist a coherent network where there are more than 255 routers between nodes. However, this is not a very urgent need. Now even the longest trail takes a couple of dozen hop-hopes.
Kemerovo. Red hill
Consider the last small example - a router on a stick.
The name is inspired by the connection scheme: The

router is connected to the switch with only one cable, and traffic for both the local network and the external network is transmitted within different vlanes inside it. This is done, as a rule, to save money (there is only one port on the router and I do not want to buy an additional fee).
Connect as follows:

Switch configuration should no longer be a problem for you. On the UpLink interface, configure the 5th vlan trunk as agreed with the provider:
Switch (config) #hostname kmr-gorka-sw1
kmr-gorka-sw1 (config) #vlan 5
kmr-gorka-sw1 (config-vlan) #name Moscow
kmr-gorka-sw1 (config) #int fa0 / 24
kmr- gorka-sw1 (config-if) #description Moscow
kmr-gorka-sw1 (config-if) #switchport mode trunk
kmr-gorka-sw1 (config-if) #switchport trunk allowed vlan 5
We will choose vlan 2 as the vlan for the local network and it’s nothing that it is already used in Moscow and St. Petersburg - if they don’t overlap and you can control it, then the numbers can match. Here, everyone decides for himself: you can use everywhere, for example, the 2nd Vlan, as a vlan of the local network or, on the contrary, develop a plan where the vlan numbers are unique throughout the network.
kmr-gorka-sw1 (config) #vlan 2
kmr-gorka-sw1 (config-vlan) #name LAN
kmr-gorka-sw1 (config) #int fa0 / 1
kmr-gorka-sw1 (config-if) #description syn_generalnogo
kmr-gorka-sw1 (config-if) #switchport mode access
kmr-gorka-sw1 (config-if) #switchport access vlan 2
Trunk towards the router, where frames of external traffic will be tagged with the 5th vlan, and local traffic with the 2nd.
kmr-gorka-sw1 (config) #int fa0 / 23
kmr-gorka-sw1 (config-if) #description kmr-gorka-gw1
kmr-gorka-sw1 (config-if) #switchport mode trunk
kmr-gorka-sw1 ( config-if) #switchport trunk allowed vlan 2.5
Router Setup:
Router (config) #hostname kmr-gorka-gw1
kmr-gorka-gw1 (config) #int fa0 / 0.5
kmr-gorka-gw1 (config-subif) #description Moscow
kmr-gorka-gw1 (config-subif) #encapsulation dot1Q 5
kmr-gorka-gw1 (config-subif) #ip address 172.16.2.18 255.255.255.252
kmr-gorka-gw1 (config) #int fa0 / 0
kmr-gorka-gw1 (config-if) #no sh
kmr-gorka- gw1 (config) #int fa0 / 0.2
kmr-gorka-gw1 (config-subif) #description LAN
kmr-gorka-gw1 (config-subif) #encapsulation dot1Q 2
kmr-gorka-gw1 (config-subif) #ip address 172.16 .24.1 255.255.255.0
We believe that you can now configure the routing between Moscow and Kemerovo on your own.
Additionally
If routing is not all right for troubleshooting, you will need two commands:
traceroute
and
show ip route
The first one can be useful, as you saw, to set the source address. And the latter can be used with parameters, for example:
msk-arbat-gw1 # sh ip route 172.16.17.0
Routing entry for 172.16.16.0/21
Known via “static”, distance 1, metric 0
Routing Descriptor Blocks:
* 172.16.2.2
Route metric is 0, traffic share count is 1
Despite the fact that there is no separate entry in the routing table for the 172.16.17.0 subnet, the router will show you what the next hop is.
And I would also like to repeat the most important things:
- When a data block arrives at the router, the Ethernet header is completely discarded and a completely new frame is formed upon sending. But the IP packet remains unchanged.
- In the case of static routing, each router decides on the fate of the packet exclusively on its own and does not know anything about other people's tables.
- The search in the table does NOT go until the first matching record is found, but until the most exact match is found (the narrowest mask). For example, if your routing table looks like this:
172.16.0.0/16 is variably subnetted, 6 subnets, 3 masks
S 172.16.0.0/16 [1/0] via 172.16.2.22
C 172.16.2.20/30 is directly connected, FastEthernet0 / 0
C 172.16.2.24/30 is directly connected, FastEthernet0 / 0.2
C 172.16.2.28/30 is directly connected, FastEthernet0 / 0.3
S 172.16.10.0/24 [1/0] via 172.16.2.26
S 172.16.10.4/30 [1/0] via 172.16.2.30
And you transfer the data to 172.16.10.5, then it will not go along the route through 172.16.2.22 or 172.16.2.26, but will select the narrowest mask (the longest) / 30 through 172.16.2.30.
- If the recipient's IP address does not match any entries in the routing table and the default route is configured (gateway of last resort), the packet will simply be discarded.
This is the first acquaintance with routing can be completed. It seems to us that the reader himself sees how many difficulties await him here, he can assume how much work he will face if the network grows to several dozen routers. But I must say that in the modern world, static routing, not only is not used, of course, it has a place, but in the vast majority of networks larger than the regional pioneer net, dynamic routing protocols are introduced. Among them are OSPF, EIGRP, IS-IS, RIP, to which we will devote a separate issue and, most likely, not one. But setting up static routing will greatly help your overall understanding of routing.
As an independent task, try to configure routing between Moscow and Kemerovo and answer the question why devices from the control network do not respond.

Release Materials
New IP plan, switching plans for each point and regulations.
RT file with laboratory.
Device configuration.
We apologize for the giant sheets, the video also becomes longer and more unbearable each time. We will try to be more compact next time.
All interested but unregistered are invited to speak on LiveJournal .
For the preparation of the article, many thanks to my co-author thegluck and my wife for the lion's patience.
Для очень недовольных: эта статья не абсолют, она не раскрывает теоретические аспекты в полной мере и, потому не претендует на роль полноценной документации. С точки зрения авторов это вспомогательной средство для новичков, волшебный стимул, если желаете. На хабре у вас есть возможность поставить минус, а не доказывать нашу неправоту. Прошу вас, поступите именно так, потому что ваши недовольства встретят лишь вышеприведённые аргументы.
Для очень недовольных: эта статья не абсолют, она не раскрывает теоретические аспекты в полной мере и, потому не претендует на роль полноценной документации. С точки зрения авторов это вспомогательной средство для новичков, волшебный стимул, если желаете. На хабре у вас есть возможность поставить минус, а не доказывать нашу неправоту. Прошу вас, поступите именно так, потому что ваши недовольства встретят лишь вышеприведённые аргументы. 