About Spanning Tree Unnecessary

Just a reservation, do not take the title too literally. If the stars light ... and so on.
Nevertheless, the Spannning Tree protocol family, if it does not become obsolete as the main backup tool in ethernet networks, at least smoothly flows into narrow and specific niches (of course, their discussion is beyond the scope of this article, but it is welcome in comments).
And yes, of course, no one has canceled the Spanning Tree as a technology to protect against human error.
Why is it needed
First, allow yourself a couple of commonplace. They, of course, can be gleaned from Wikipedia, but we cannot resist.
Since the BOC model (aka ISO / OSI, if you like it more) forgot to give the channel layer the functions of choosing the optimal transmission path and eliminating loops, putting them on the network layer, Ethernet technology does not have such functions. Instead of trouble with preliminary calculation of the path to the destination address, the Ethernet switch, if it does not know where to send the frame, sends it to all ports except the port through which the transmitted frame was received. And there, you see, there is a recipient who is able to figure out from the content that this is a frame for him. (When we talk about flooding in all ports, with the exception of very special cases, we are talking only about the ports of one VLAN.)
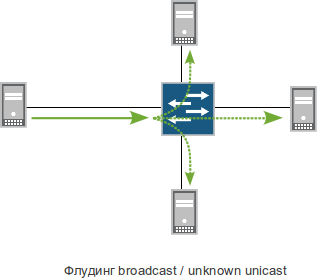
A switch would not be a switch if it were limited to this. Still, he is not so stupid, and in order not to send everything to everyone always, he peeks at the addresses of the sources and writes them to his nameplate: the MAC address of such and such is located at such and such a port. The process is called MAC address learning (“mac-lening”). Having formed such a table (switching table), the switch sends frames only to the necessary ports.
If IP traffic is transmitted over Ethernet, and most often it is, then frames with unknown destination MAC addresses should not occur with a good deal (and direct hands), but you can’t do without special frames with the destination address “Send to everyone”, the transmission of which boils down to the same.
In total, in ethernet networks, flooding, that is, copying a frame to all possible output ports is an integral part of the switching process.
Now imagine what will happen if a loopback is detected in the network topology. One of the copies of the frame will return to the switch that has lost it, which will lose it again, and so on, until all the devices on the network load the processors to one hundred percent. The situation described is called a Broadcast storm. Anyone who has observed it will not let you lie, the sight is not for the faint of heart.

If you and your neighbor conspired to go home lokalka by buying a couple of plastic sweaters at the store, do not try to connect them with two wires instead of one for greater speed and greater reliability: it won’t get better, that's at least.
On the one hand - what is easier? - do not stick extra wires, and that’s it. But not so easy. After all, I want the network to be fault tolerant, with redundant connections, redundant nodes and automatic failover. In other words, so that the L2 network is like L3. To achieve the desired and, at the same time, to protect themselves from the horror of Broadcast storms, people came up with special technologies for finding cycles in the topology and forcing them to break by blocking individual links. These technologies are called the word Spanning Tree.
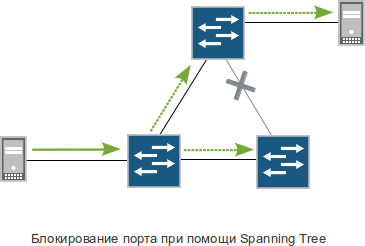
It is technology, in the plural. After all, it’s not enough to say “block”, it’s also important to understand which link to block, after what period of time to check, whether it is time to unlock, how to do it, which ports you can not check for loops, which VLANs to transmit to which links, how quickly all this happens, etc. Different views on these and many other issues have generated a whole bunch of protocols with the general name Spanning Tree: STP, RSTP, PVST, PVST +, PVRST, MSTP, VSTP, there are certainly more.
Readers who have seriously studied any of the above, are probably familiar with the sensation similar to the combination of drowsiness and toothache that arises in the process of studying all these endless port states, weight formation mechanisms, root switch selection algorithms, and other boring things that are inferior in boring unless an anatomy textbook. Those who successfully coped with the implementation, operation, troubleshooting and network development of at least one and a half dozen switches built on the basis of the spanning tree can safely submit to
Spanning Tree translated from English means "branching tree." And the tree is, in turn, a “connected acyclic graph”, that is, a graph without cycles (loops), between which there is at least one path between two vertices.
Why is it not needed
Now, finally, about why the Spanning Tree is rapidly losing its relevance.
You, of course, have already heard that in the bright future, everything will be firstly shared, secondly virtual,
The technology of linking links into aggregated LAG aka EtherChannel groups did not appear yesterday.
By the way, you should not confuse the association of links in LAG itself and the LACP protocol, which helps to make this association (semi) automatically, but because of inept handling in life, it has more problems than good.
The idea is simple. Two switches - however, not necessarily a switch, any devices operating at the second and higher levels - are connected for reliability by two wires, and not one. At the same time, the switches are configured (manually or through LACP) in such a way that for them these two wires are one link. We won’t go into too much detail, there are a lot of articles about it for every taste, we’ll just say that aggregation can be according to one of two schemes: “active – active” (the most popular): traffic is transmitted simultaneously through two wires with load balancing; and “active – passive”: while one link is in the “up”, the second is in the “down”, when the main one falls, it switches to the backup one.
In fact, the above is the easiest way to get rid of the Spanning Tree at the “one-level” level. However, this method generally requires that both links on each side be connected to the same switch. Otherwise, all the same loops or complications associated with the constant updating of the MAC address table are possible.
But here a relatively (very relatively) modern invention comes to the rescue - clustering of switches. With its help, several physical devices can be combined into one logical one. Traditionally, this function is considered to be "beautiful", designed primarily to simplify management. However, the main advantages of cluster clustering are completely different. In addition to some technical and commercial aspectsClustering is also a reduction in the number of nodes in the topology while maintaining redundancy of physical devices.

Today, the main driver of the growing popularity of clustered switches is precisely the ability to combine ports located on different physical devices of the cluster into LAGs. Thus, we get the opportunity to connect one access switch (into which user links are stuck) to two aggregation switches without any Spanning Tree. Similarly, if there are more levels, aggregation switches can be connected to the core (if you have one) or backbones using the LAG-group.

A word about scale
Initially, clustering appeared on 24/48 × 1GE (+ 2 × 10GE) format switches, i.e. devices of a relatively small scale. Depending on the manufacturer and model, such switches can be combined into a cluster either using special interfaces (PCI Express, InfiniBand, etc.), which are limited in length to several meters, or through the usual 1 or 10 Gigabit Ethernet ports, including optical. In the latter cases, it becomes possible to build geographically distributed switches and even small metro-ethernet networks . Depending on the specific implementation and model, it is usually possible to combine from two to ten devices into one cluster.
After some time, manufacturers began to introduce clustering on large modular switches. In them, for intra-cluster links, as a rule, several 10 Gigabit Ethernet interfaces are used. The maximum number of such devices in one cluster is usually significantly less (2–4), however, this is not a special crime.
In addition to modular switches, clustering is also found on high-grade hardware routers of senior rulers of individual manufacturers. From a theoretical point of view, this function is less relevant for routers due to the presence of “native” routing, load balancing, and traffic engineering mechanisms in IP / MPLS networks. But since such devices are often used to perform L2 functions (PE for L2VPN / VPLS services or combining L3 and L2 in one box), clustering support on them is also important and is used primarily for the same thing: combining different interfaces into LAGs physical devices to reserve second-level connections.
Nevertheless, a bright future will not be free. In some aspects, a cluster of switches is worse than many separate switches. For example, the table of MAC addresses on all devices is usually one. Accordingly, the upper bar of the maximum number of entries in it applies to the entire cluster. For a network of 10 devices of a small city scale, the limit of 10-15 thousand MAC addresses can be a significant limitation; some implementations, for example, require a simultaneous reboot of all cluster devices when updating software. There may be quite a lot of nuances of this kind, depending on the specific model of devices. All this makes clustering a dubious approach for building carrier networks.
Total
Combining the clustering of switches and aggregating the interfaces of different devices into LAG groups is the most effective way today to build fault-tolerant L2 networks of enterprises, campuses (several adjacent buildings of a single administrative management), data centers and individual nodes of provider networks. For most parameters: switching speed, stability, reliability, ease of operation and Troubleshoot tuning, load balancing - this approach significantly exceeds the variations on the Spanning Tree theme.
However, this technology is not a panacea, you should not perceive it as a mechanism for constructing real L2 networks of an operator scale.
In addition, the Spanning Tree, although losing its relevance as a mechanism for building a fault-tolerant topology and balancing, but, as has already been said, remains an urgent way to protect against human error. Therefore, if, for example, RSTP or PVST + is enabled by default on the switch, you should not turn it off unless you are sure that you know exactly why. It is also desirable that all switches use the same protocol, but this is a completely different story.
