Anonymous Networks and Timing Attacks: Low Cost Attack
- Transfer
Introduction | Tor | Tarzan and MorphMix | Low Cost Attack | Low Cost Attack on Tarzan and Morphmix | Principles of Building Safe Systems (Conclusion)
In this section, we will consider the Low cost attack 8 on Tor described in (Murdoch & Danezis 2005). The term Low-cost attack means that for an attacker to succeed, it’s enough to be able to observe only part of the network, for example, to be one of the Tor nodes. Murdoch and Danezis showed Tor vulnerability for some timing attack option, which does not go beyond the threat model. They refuted the claim that Tor's anonymity cannot be violated without the help of a global passive observer.
The basic idea is to use the seemingly inevitable restriction of all anonymizing systems with low latency - time. The purpose of the attack is to determine which nodes are currently used to organize Tor chains. If successful, this will hit Tor anonymizing strongly. The authors confirm the theoretical calculations with the results of real experiments. And in the end, they conclude that all anonymizing networks with low latencies are subject to their attack, including Tarzan and MorphMix.
The attack is based on the fact that systems with small delays cannot afford to introduce any delays into the stream. Thus, the temporal characteristics (timing pattern) of packets are stored throughout the chain. The attack became possible due to the fact that Tor developers considered the appearance of a global passive observer on the network unbelievable. This situation was not considered and was not included in the threat model. However, the low-cost attack revealed the fallacy of the developers' judgment and showed that Tor is still vulnerable to some timing attack options.
Indeed, the attacker does not see all the connections in the network. But nothing prevents him from acting as one of the Tor nodes and measuring the delays between himself and all other nodes. Using knowledge of these delays, one can indirectly estimate the amount of traffic that each node transmits at any given time. Further, knowing the picture of the distribution of the traffic volume over time for all network catch, it is possible, using the technique (Danezis 2004), to build fairly good guesses about which nodes transmit traffic with the same characteristics. In other words, reveal anonymizing chains.
Tor architecture is conducive to attack. The Tor node allocates a separate buffer for each connection, buffer processing is in round robin fashion * mode. If there is no stream in the buffer, it is ignored; processing of the next buffer begins. Note that for performance reasons, mixing has been removed. In this way
For a successful attack, an attacker just needs to be one of the Tor network clients. Such a node is called a malicious (corrupt node) or probe (probe node).
The main stages of the attack:
The attack will be even more effective if the attacker controls the server to which the Tor user connects. Since in this case it is not necessary to identify the traffic pattern, the attacker himself can modify the traffic so that it can be easily detected. The purpose of the attack: to find the path between the client node of the victim and the captured server. This will reduce the anonymizing ability of the system to the level of a regular proxy. As a result, the authors conclude that the attack will be effective for all anonymizing systems with low latency systems, including Tarzan and MorphMix.
In the next section, we will verify this statement and show that it is true only if certain conditions are met. Figure 5 shows the attack model, and table 6 shows its algorithm.
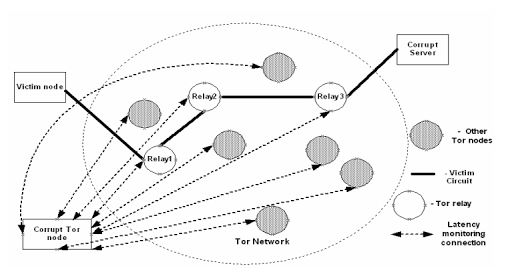
Figure 4. Low-cost timing attack on Tor.
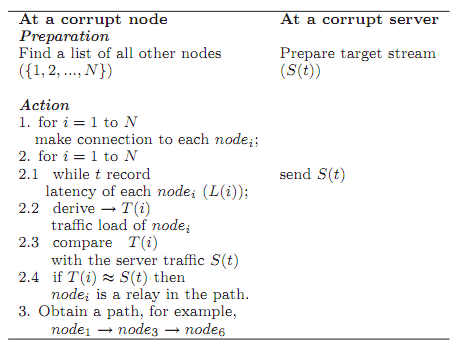
Figure 5. Low cost attack algorithm.
Note by translators
8 “Low-cost attack” in this context is a proper name.
* what is round robin fashion see in the introduction .
In this section, we will consider the Low cost attack 8 on Tor described in (Murdoch & Danezis 2005). The term Low-cost attack means that for an attacker to succeed, it’s enough to be able to observe only part of the network, for example, to be one of the Tor nodes. Murdoch and Danezis showed Tor vulnerability for some timing attack option, which does not go beyond the threat model. They refuted the claim that Tor's anonymity cannot be violated without the help of a global passive observer.
The basic idea is to use the seemingly inevitable restriction of all anonymizing systems with low latency - time. The purpose of the attack is to determine which nodes are currently used to organize Tor chains. If successful, this will hit Tor anonymizing strongly. The authors confirm the theoretical calculations with the results of real experiments. And in the end, they conclude that all anonymizing networks with low latencies are subject to their attack, including Tarzan and MorphMix.
Idea of attack
The attack is based on the fact that systems with small delays cannot afford to introduce any delays into the stream. Thus, the temporal characteristics (timing pattern) of packets are stored throughout the chain. The attack became possible due to the fact that Tor developers considered the appearance of a global passive observer on the network unbelievable. This situation was not considered and was not included in the threat model. However, the low-cost attack revealed the fallacy of the developers' judgment and showed that Tor is still vulnerable to some timing attack options.
Indeed, the attacker does not see all the connections in the network. But nothing prevents him from acting as one of the Tor nodes and measuring the delays between himself and all other nodes. Using knowledge of these delays, one can indirectly estimate the amount of traffic that each node transmits at any given time. Further, knowing the picture of the distribution of the traffic volume over time for all network catch, it is possible, using the technique (Danezis 2004), to build fairly good guesses about which nodes transmit traffic with the same characteristics. In other words, reveal anonymizing chains.
Tor architecture is conducive to attack. The Tor node allocates a separate buffer for each connection, buffer processing is in round robin fashion * mode. If there is no stream in the buffer, it is ignored; processing of the next buffer begins. Note that for performance reasons, mixing has been removed. In this way
- when a new connection is established;
- or the existing connection is deleted;
- or when traffic changes in the current connection
Attack participants
For a successful attack, an attacker just needs to be one of the Tor network clients. Such a node is called a malicious (corrupt node) or probe (probe node).
Attack model
The main stages of the attack:
- The malicious Tor node establishes connections with other Tor nodes to measure the delays of these links.
- The malicious Tor node has been monitoring delays in all of these connections for some time.
- Delay measurements are used to estimate the volume of traffic transmitted by each Tor node (traffic loads on Tor nodes) with which the malicious node is connected.
- Based on the knowledge of the volumes of traffic, traffic patterns are displayed.
- When an attacker knows the traffic patterns of all nodes, he can perform an attack (Danezis 2004, Levine et al. 2004).
The attack will be even more effective if the attacker controls the server to which the Tor user connects. Since in this case it is not necessary to identify the traffic pattern, the attacker himself can modify the traffic so that it can be easily detected. The purpose of the attack: to find the path between the client node of the victim and the captured server. This will reduce the anonymizing ability of the system to the level of a regular proxy. As a result, the authors conclude that the attack will be effective for all anonymizing systems with low latency systems, including Tarzan and MorphMix.
In the next section, we will verify this statement and show that it is true only if certain conditions are met. Figure 5 shows the attack model, and table 6 shows its algorithm.

Figure 4. Low-cost timing attack on Tor.

Figure 5. Low cost attack algorithm.
Note by translators
8 “Low-cost attack” in this context is a proper name.
* what is round robin fashion see in the introduction .
