OTRS: LDAP Authentication, Authorization, and Synchronization (FreeIPA, AD)
- Tutorial

OTRS is an open source (Ticket Request System) application processing system written in Perl.
There are two options:
- OTRS Business Solution - paid version
- ((OTRS)) Community Edition - free version
I will list a few from the fuktsionala that supports this system:
- ITSM module (Service Level Management, Change Management, Configuration Management, CMDB)
- responsive web interface
- API
- SLA and services
- multi-tenancy
- escalation
- Authentication: DB, LDAP, HTTPBasicAuth, Radius
- support for MySQL, MariaDB, PostgreSQL, Oracle
And if you look for flaws in it - this is the unusual interface and the complexity of setting up. Under the cat - about the basics of authorization (group, RBAC, support for several client companies), authentication and synchronization of metadata (name, phone, etc.) using various LDAP directories
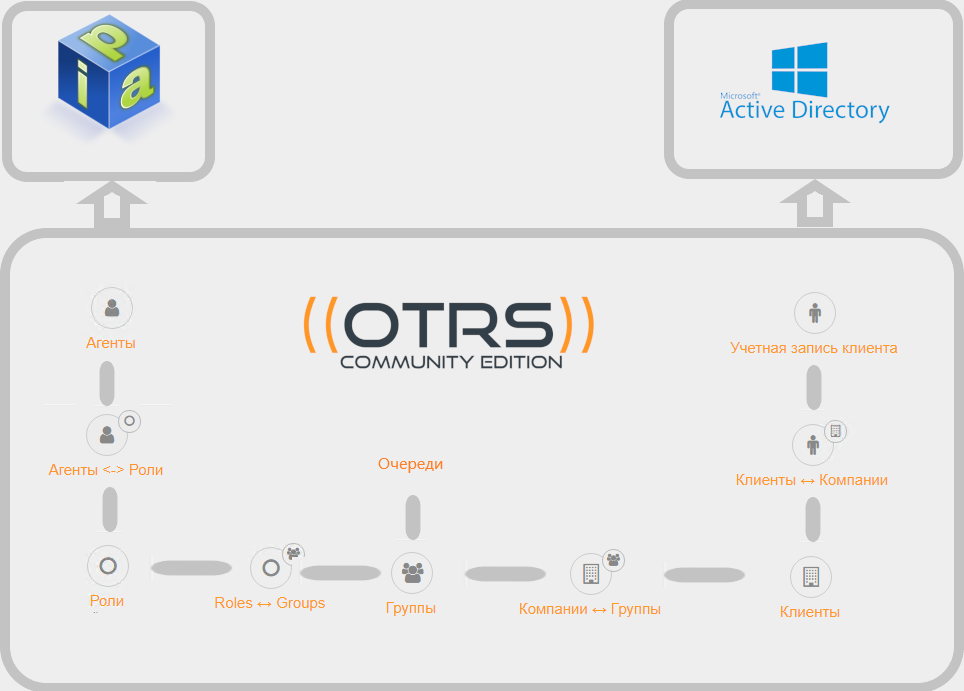
Clients, queues, agents and groups
After installing OTRS, you will be immediately available:
- clients - can create applications by sending a letter or using web access
- queues - each application is in one of the queues of applications
- agents - IT professionals working on the execution of applications from the queues available to them
- Groups - an entity that connects queues, clients and agents, as well as specifies agent rights - for example, only reading, changing the priority of an application, etc.

Standard groups
After installing the system, you will see three groups created:
- admin - group members can administer (configure) OTRS
- stats - the ability to customize and run reports
- users - standard group for clients, queues and agents
Rights Associated with Groups
Basic rights
The basic rights that can be configured in the group, limiting the actions of agents:
- read only - read only permissions in this group / queue
- move - rights to move applications to this group / queue
- creation - rights to create applications in this group / queue
- note - rights to add notes to requests in this group / queue
- owner - rights to change the owner of applications in this group / queue
- priority - the right to change the priority of applications in this group / queue
- read / write - full read and write permissions for requests in this group / queue
Additional rights
There are also additional rights, the display of which can be enabled in the settings (System :: Permission):
- reports - provides access to the reports page
- redirect - the right to redirect / bounce the mail message (link redirect / bounce to ticketZoom)
- create - the right to make a response to the application
- customer - the right to change the customer for this application
- forward - the right to forward messages (using the Forward button)
- pending - the right to transfer the request pending
- phone - the right to add the contents of the customer’s call to the application in the form of a message / note
- Responsible - The right to change the person responsible for the application
Consider this in more detail:
- each client can be included in one or several groups, initially all clients belong to the users group
- each order queue is associated with any one of the groups
- through the web interface, the client can make applications in those queues to which groups have access, in which it is included
- When the client sends an application via e-mail, it is possible to change the characteristics of the application, including the queue to which the application falls, by analyzing the attributes of the letter (for example, the sender's address or the message header).
- if the client made a phone call, the agent can make a request manually by selecting any of the queues available to the agent
- It is desirable that the client request is always in the queues available to the client, otherwise he will not be able to access it through the web interface
- agents can perform actions in applications in accordance with the rights to the queue in which the application is located

Database Authentication
The standard way to authenticate and authorize agents and clients is the database.
For example, setting agent authentication using a database looks like this:
$Self->{'AuthModule'} = 'Kernel::System::Auth::DB';Customers:
$Self->{'Customer::AuthModule'} = 'Kernel::System::CustomerAuth::DB';
$Self->{'Customer::AuthModule::DB::Table'} = 'customer_user';
$Self->{'Customer::AuthModule::DB::CustomerKey'} = 'login';
$Self->{'Customer::AuthModule::DB::CustomerPassword'} = 'pw';We will also leave this authentication method and add LDAP authentication in addition to it.
Roles and Companies
We will also expand authorization capabilities by adding roles and companies:
- Roles - allow you to more flexibly manage access, linking groups and agents together
- companies - allow you to isolate applications of different customers (whether they are different departments or companies)
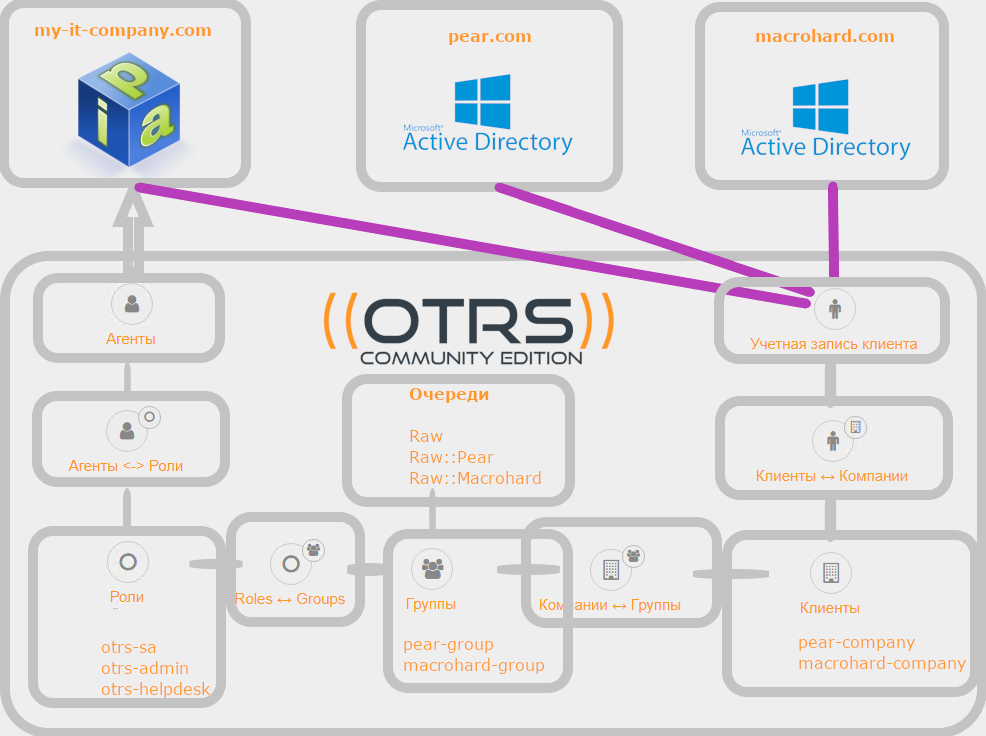
Formulation of the problem
You are the OTRS system administrator at my-it-company.com, which provides services to other companies (or divisions within your holding).
You really wouldn’t want to manually create accounts for new agents and clients, as well as fill out additional information, such as email address, phone number, position, address and account number - this is all already in LDAP directories.
And your company will also get obvious advantages - a single employee password to all systems, blocking an LDAP account will block access to all other services.
my-it-company.comruns on Linux and uses Red Hat FreeIPA as the directory server, and the units you serve are various Microsoft Active Directory forests with which you do not have federation, but you can connect to domain controllers.
You need to separate the flow of requests from different clients, as well as implement different levels of agent access to the queues - managers should be able to change the priority of tasks in the system.
Your company's employees can also set tasks in the system for the internal needs of my-it-company.com , sometimes being both agents and clients at the same time (and sometimes not).
Training
Accounts to view LDAP
If anonymous browsing of the directory tree is prohibited, then we will create accounts in the domains my-it-company.com , pear.com and macrohard.com , which will be enough for us to make requests to LDAP (let's call them, for example, ldap-bot)
FreeIPA groups for synchronization with OTRS roles
Let's get three groups of users on FreeIPA, which will be synchronized with our OTRS roles, for example:
- otrs-sa - members of this group will have access to the administration of OTRS, but we will not give access to the queues, so that there is no desire to always work under the administrator)
- otrs-admins - our managers who have the right to change the priority of applications) and
- otrs-helpdesk - accounts of our specialists
Attribute that defines belonging to the company
Select the attribute by which we will determine the affiliation to the company. Let it be the attribute "Organization". For example, you did everything organizationally and technically, and all users in all domains always have a value in the "Organization" field:
- my-it-company - for my-it-company.com employees
- pear-company - for employees pear.com
- macrohard-company - for employees at macrohard.com
Define user attributes used by FreeIPA
We study the FreeIPA scheme, finding out the names of the attributes that we need to synchronize (name, login, phone, etc.).
kinit laptevs
ipa user-show --all --raw laptevsWe get a similar conclusion:
dn: uid=laptevs,cn=users,cn=accounts,dc=my-it-company,dc=com
uid: laptevs
givenname: Stanislav
sn: Laptev
cn: Laptev Stanislav
initials: SL
homedirectory: /home/laptevs
gecos: Laptev Stanislav
loginshell: /bin/sh
krbcanonicalname: laptevs@MY-IT-COMPANY.COM
krbprincipalname: laptevs@MY-IT-COMPANY.COM
mail: laptevs@MY-IT-COMPANY.COM
uidnumber: 1344600003
gidnumber: 1344600003
l: Moscow
telephonenumber: +7(863)999-99-99
mobile: +7(999)999-99-99
ou: My-it-company
title: SysAdm
sshpubkeyfp: SHA256:Yi8mKF+j28/r2cpxLgIbvZ/Oymt57rhliHKhqBuJxqE laptevs-putty (ssh-rsa)
nsaccountlock: FALSE
has_password: TRUE
has_keytab: TRUE
displayName: Laptev Stanislav
ipaSshPubKey: c3NoLXJzYSBBQUFBQjNOemFDMXljMkVBQUFBQkpRQUFBZ0VBNjQ1RTJjSjIvWXVVYm9GNzdZY3hLNzBndm1jWlgrZjBZTVpsaXRQVXNCWFZ0cENtTEtwcjRwK2JEeUdhRzNLTWx1T08ydW9wS0pXRk9mWE83Zzl3OTYzdklQblN3MzVHSmI3VGhhbk1pTXpNUE82T1lQZEY0em14b2k4N 0RGYkdXV2V6aGwzcitsbmFGYTB0dEQ5TkFWRU1Fb3BMdmkzcHZ1UXpyVmNjVlMxamFxY1dNT2ZGUC9TRlVoY1dGeVpZd3Z6eW0wWnZObUZtdjVjVHJGNzJMSXZOdHlsNkZGK2ZaU3ZpS01mcXZ6NStkT2xZZGd5bVVSOG5iaVpkTXZKaTIvbzhjTy84ekpoMFhtSnVRSjJXNEVvYVEvajVTTm8ySjZ6NklXNk I3cFB4Y002a0tJcUp5N08zTkNOcGRrVmVQbEFHbThsOFZDREpVa1RLSjRGOS9mSTZFUkhxVUZwK3p1VENTR1R3ZWlKdXppenFSZWJTTkNiMXh3RldmUitvYzFLdWNZSU5QbTYxRi93YXhOcC9aSG9OK2w1dCtkYWI4cElZSGZzTnNUNWx2RWt4Ukh0bnNyeUxsbWk1ZVdzd3RBbDB3TUpWd1cvUWNJcjhOaVN Ybm96Q3dHWTZCaTQ2L0FGTGVidmFLV0tKRmpKZFgxOFlRVDRpVzZGaE83aW40TGlUamlNaENXbStvbjNQbERYeXZpdkJ1WkFXUldXNEdjbXREVW8rSVhZT2t3MWh3UldqdkJtcExHMVZpMFhPckltbmQybTVZdWk1bHo0b1ZlekFRN1NjYVlrdDBoVEdQU1Z2UHpmVlowYWJCQlpiRmViK1hUV2tpSnBPMHBO T3dodGNadHYrN3RMMnc1OFN3QnhVTUk4NzUzdG5Sc1h1blBXZERqcUsxSDA9IGxhcHRldnMtcHV0dHk=
ipaUniqueID: 68d46dac-1d3c-11e9-82fd-0242ac110002
krbExtraData: AAL4VkVcbGFwdGV2c0BPTUlLUk9OLlBSTwA=
krbLastFailedAuth: 20190123084142Z
krbLastPwdChange: 20190121052200Z
krbLoginFailedCount: 0
krbPasswordExpiration: 20190421052200Z
memberof: cn=otrs-admins,cn=groups,cn=accounts,dc=my-it-company,dc=com
memberof: cn=ipausers,cn=groups,cn=accounts,dc=my-it-company,dc=com
mepManagedEntry: cn=laptevs,cn=groups,cn=accounts,dc=my-it-company,dc=com
objectClass: top
objectClass: person
objectClass: organizationalperson
objectClass: inetorgperson
objectClass: inetuser
objectClass: posixaccount
objectClass: krbprincipalaux
objectClass: krbticketpolicyaux
objectClass: ipaobject
objectClass: ipasshuser
objectClass: ipaSshGroupOfPubKeys
objectClass: mepOriginEntry
uid: laptevs
givenname: Stanislav
sn: Laptev
cn: Laptev Stanislav
initials: SL
homedirectory: /home/laptevs
gecos: Laptev Stanislav
loginshell: /bin/sh
krbcanonicalname: laptevs@MY-IT-COMPANY.COM
krbprincipalname: laptevs@MY-IT-COMPANY.COM
mail: laptevs@MY-IT-COMPANY.COM
uidnumber: 1344600003
gidnumber: 1344600003
l: Moscow
telephonenumber: +7(863)999-99-99
mobile: +7(999)999-99-99
ou: My-it-company
title: SysAdm
sshpubkeyfp: SHA256:Yi8mKF+j28/r2cpxLgIbvZ/Oymt57rhliHKhqBuJxqE laptevs-putty (ssh-rsa)
nsaccountlock: FALSE
has_password: TRUE
has_keytab: TRUE
displayName: Laptev Stanislav
ipaSshPubKey: c3NoLXJzYSBBQUFBQjNOemFDMXljMkVBQUFBQkpRQUFBZ0VBNjQ1RTJjSjIvWXVVYm9GNzdZY3hLNzBndm1jWlgrZjBZTVpsaXRQVXNCWFZ0cENtTEtwcjRwK2JEeUdhRzNLTWx1T08ydW9wS0pXRk9mWE83Zzl3OTYzdklQblN3MzVHSmI3VGhhbk1pTXpNUE82T1lQZEY0em14b2k4N 0RGYkdXV2V6aGwzcitsbmFGYTB0dEQ5TkFWRU1Fb3BMdmkzcHZ1UXpyVmNjVlMxamFxY1dNT2ZGUC9TRlVoY1dGeVpZd3Z6eW0wWnZObUZtdjVjVHJGNzJMSXZOdHlsNkZGK2ZaU3ZpS01mcXZ6NStkT2xZZGd5bVVSOG5iaVpkTXZKaTIvbzhjTy84ekpoMFhtSnVRSjJXNEVvYVEvajVTTm8ySjZ6NklXNk I3cFB4Y002a0tJcUp5N08zTkNOcGRrVmVQbEFHbThsOFZDREpVa1RLSjRGOS9mSTZFUkhxVUZwK3p1VENTR1R3ZWlKdXppenFSZWJTTkNiMXh3RldmUitvYzFLdWNZSU5QbTYxRi93YXhOcC9aSG9OK2w1dCtkYWI4cElZSGZzTnNUNWx2RWt4Ukh0bnNyeUxsbWk1ZVdzd3RBbDB3TUpWd1cvUWNJcjhOaVN Ybm96Q3dHWTZCaTQ2L0FGTGVidmFLV0tKRmpKZFgxOFlRVDRpVzZGaE83aW40TGlUamlNaENXbStvbjNQbERYeXZpdkJ1WkFXUldXNEdjbXREVW8rSVhZT2t3MWh3UldqdkJtcExHMVZpMFhPckltbmQybTVZdWk1bHo0b1ZlekFRN1NjYVlrdDBoVEdQU1Z2UHpmVlowYWJCQlpiRmViK1hUV2tpSnBPMHBO T3dodGNadHYrN3RMMnc1OFN3QnhVTUk4NzUzdG5Sc1h1blBXZERqcUsxSDA9IGxhcHRldnMtcHV0dHk=
ipaUniqueID: 68d46dac-1d3c-11e9-82fd-0242ac110002
krbExtraData: AAL4VkVcbGFwdGV2c0BPTUlLUk9OLlBSTwA=
krbLastFailedAuth: 20190123084142Z
krbLastPwdChange: 20190121052200Z
krbLoginFailedCount: 0
krbPasswordExpiration: 20190421052200Z
memberof: cn=otrs-admins,cn=groups,cn=accounts,dc=my-it-company,dc=com
memberof: cn=ipausers,cn=groups,cn=accounts,dc=my-it-company,dc=com
mepManagedEntry: cn=laptevs,cn=groups,cn=accounts,dc=my-it-company,dc=com
objectClass: top
objectClass: person
objectClass: organizationalperson
objectClass: inetorgperson
objectClass: inetuser
objectClass: posixaccount
objectClass: krbprincipalaux
objectClass: krbticketpolicyaux
objectClass: ipaobject
objectClass: ipasshuser
objectClass: ipaSshGroupOfPubKeys
objectClass: mepOriginEntry
dn : uid = laptevs, cn = users, cn = accounts, dc = my-it-company, dc = com
uid : laptevs
givenname : Stanislav
sn : Laptev
cn : Laptev Stanislav
mail : laptevs@my-IT-COMPANY.COM
l : Moscow
telephonenumber : +7 (863) 999-99-99
mobile : +7 (999) 999-99-99
ou : My-it-company
title : SysAdm
OTRS configuration setup
Configuration files
- / opt / otrs / - as a rule, OTRS files are located here
- Kernel / Config.pm - the configuration file you are editing
- Kernel / Config / Defaults.pm - a file with standard settings, you do not edit it, but in it you can view all existing parameters and comments to them
Agent configuration
Agent Authentication
# --------------------------------------------------- ## Agents authentication ## --------------------------------------------------- ## my-it-company.com LDAP backend
$Self->{AuthModule} = 'Kernel::System::Auth::LDAP';
# Адрес LDAP-сервера
$Self->{'AuthModule::LDAP::Host'} = 'my-it-company.com';
$Self->{'AuthModule::LDAP::BaseDN'} = 'dc=my-it-company,dc=com';
$Self->{'AuthModule::LDAP::UID'} = 'uid';
# Блок нужен, только если запрещен анонимный просмотр структуры каталогов
$Self->{'AuthModule::LDAP::SearchUserDN'} = 'uid=ldap-bot,cn=users,cn=accounts,dc=my-it-company,dc=com';
$Self->{'AuthModule::LDAP::SearchUserPw'} = 'bot-password!';
# Фильтр запроса к LDAP. Пусть у нас будут только пользователи, имеющие заполненный атрибут "электронная почта"
$Self->{'AuthModule::LDAP::AlwaysFilter'} = '(mail=*)';
# Добавляем при проблемах с кодировкой
$Self->{'AuthModule::LDAP::Charset'} = 'utf-8';
$Self->{'AuthModule::UseSyncBackend'} = 'AuthSyncBackend';
# my-it-company.com DB backend
$Self->{AuthModule2} = 'Kernel::System::Auth::DB';
$Self->{'AuthModule::DB::CryptType2'} = 'sha2';
# --------------------------------------------------- ## End Agents authentication ## --------------------------------------------------- #Agent synchronization (LDAP groups with OTRS roles)
# --------------------------------------------------- ## Agent authentication sync ## (enable agent data sync. after succsessful ## authentication) ## --------------------------------------------------- ## my-it-company.com LDAP auth sync. backend.
$Self->{AuthSyncModule} = 'Kernel::System::Auth::Sync::LDAP';
$Self->{'AuthSyncModule::LDAP::Host'} = 'my-it-company.com';
$Self->{'AuthSyncModule::LDAP::BaseDN'} = 'dc=my-it-company,dc=com';
$Self->{'AuthSyncModule::LDAP::UID'} = 'uid';
$Self->{'AuthSyncModule::LDAP::SearchUserDN'} = 'uid=ldap-bot,cn=users,cn=accounts,dc=my-it-company,dc=com';
$Self->{'AuthSyncModule::LDAP::SearchUserPw'} = 'bot-password!';
$Self->{'AuthSyncModule::LDAP::AlwaysFilter'} = '(mail=*)';
$Self->{'AuthSyncModule::LDAP::UserSyncMap'} = {
# DB -> LDAPUserFirstname =>'givenName',
UserLastname =>'sn',
UserEmail =>'mail',
};
$Self->{'AuthSyncModule::LDAP::AccessAttr'} = 'member';
$Self->{'AuthSyncModule::LDAP::UserAttr'} = 'DN';
$Self->{'AuthSyncModule::LDAP::UserSyncRolesDefinition'} = {
# ldap group'cn=otrs-sa,cn=groups,cn=accounts,dc=my-it-company,dc=com' => {
# otrs role'otrs-sa' => 1,
},
'cn=otrs-admins,cn=groups,cn=accounts,dc=my-it-company,dc=com' => {
'otrs-admins' => 1,
},
'cn=otrs-helpdesk,cn=groups,cn=accounts,dc=my-it-company,dc=com' => {
'helpdesk' => 1,
}
};
$Self->{DatabaseUserTable} = 'users';
$Self->{DatabaseUserTableUserID} = 'id';
$Self->{DatabaseUserTableUserPW} = 'pw';
$Self->{DatabaseUserTableUser} = 'login';
# --------------------------------------------------- ## End Agents authentication sync ## --------------------------------------------------- #If you decide that the roles do not suit you, and you only want groups, I’ll give two examples of synchronizing LDAP groups with OTRS groups - simplified and with rights settings for each group.
Alternative agent synchronization (LDAP groups with OTRS groups, with rights specified)
# --------------------------------------------------- ## Agent authentication sync ## (enable agent data sync. after succsessful ## authentication) ## --------------------------------------------------- ## my-it-company.com LDAP auth sync. backend.
$Self->{AuthSyncModule} = 'Kernel::System::Auth::Sync::LDAP';
$Self->{'AuthSyncModule::LDAP::Host'} = 'my-it-company.com';
$Self->{'AuthSyncModule::LDAP::BaseDN'} = 'dc=my-it-company,dc=com';
$Self->{'AuthSyncModule::LDAP::UID'} = 'uid';
$Self->{'AuthSyncModule::LDAP::SearchUserDN'} = 'uid=ldap-bot,cn=users,cn=accounts,dc=my-it-company,dc=com';
$Self->{'AuthSyncModule::LDAP::SearchUserPw'} = 'bot-password!';
$Self->{'AuthSyncModule::LDAP::AlwaysFilter'} = '(mail=*)';
$Self->{'AuthSyncModule::LDAP::UserSyncMap'} = {
# DB -> LDAPUserFirstname =>'givenName',
UserLastname =>'sn',
UserEmail =>'mail',
};
$Self->{'AuthSyncModule::LDAP::AccessAttr'} = 'member';
$Self->{'AuthSyncModule::LDAP::UserAttr'} = 'DN';
# AuthSyncModule::LDAP::UserSyncGroupsDefinition# (If "LDAP" was selected for AuthModule and you want to sync LDAP# groups to otrs groups, define the following.)
$Self->{'AuthSyncModule::LDAP::UserSyncGroupsDefinition'} = {
# ldap group'cn=otrs-admins,cn=groups,cn=accounts,dc=my-it-company,dc=com' => {
# otrs group'admin' => {
# permissionrw =>1,
move_into =>1,
create =>1,
note =>1,
owner =>1,
prioriry =>1,
ro =>1,
},
'stats' => {
rw =>1,
move_into =>1,
create =>1,
note =>1,
owner =>1,
prioriry =>1,
ro =>1,
},
'users' => {
rw =>1,
move_into =>1,
create =>1,
note =>1,
owner =>1,
prioriry =>1,
ro =>1,
},
'pear-group' => {
rw =>1,
move_into =>1,
create =>1,
note =>1,
owner =>1,
prioriry =>1,
ro =>1,
},
'macrohard-group' => {
rw =>1,
move_into =>1,
create =>1,
note =>1,
owner =>1,
prioriry =>1,
ro =>1,
},
},
'cn=otrs-helpdesk,cn=groups,cn=accounts,dc=my-it-company,dc=com' => {
'stats' => {
rw =>1,
move_into =>1,
create =>1,
note =>1,
owner =>1,
prioriry =>1,
ro =>1,
},
'users' => {
rw =>1,
move_into =>1,
create =>1,
note =>1,
owner =>1,
prioriry =>1,
ro =>1,
},
}
};
$Self->{DatabaseUserTable} = 'users';
$Self->{DatabaseUserTableUserID} = 'id';
$Self->{DatabaseUserTableUserPW} = 'pw';
$Self->{DatabaseUserTableUser} = 'login';
# --------------------------------------------------- ## End Agents authentication sync ## --------------------------------------------------- #Alternative simplified agent synchronization (LDAP groups with OTRS roles with rw rights)
# --------------------------------------------------- ## Agent authentication sync ## (enable agent data sync. after succsessful ## authentication) ## --------------------------------------------------- ## my-it-company.com LDAP auth sync. backend.
$Self->{AuthSyncModule} = 'Kernel::System::Auth::Sync::LDAP';
$Self->{'AuthSyncModule::LDAP::Host'} = 'my-it-company.com';
$Self->{'AuthSyncModule::LDAP::BaseDN'} = 'dc=my-it-company,dc=com';
$Self->{'AuthSyncModule::LDAP::UID'} = 'uid';
$Self->{'AuthSyncModule::LDAP::SearchUserDN'} = 'uid=ldap-bot,cn=users,cn=accounts,dc=my-it-company,dc=com';
$Self->{'AuthSyncModule::LDAP::SearchUserPw'} = 'bot-password!';
$Self->{'AuthSyncModule::LDAP::AlwaysFilter'} = '(mail=*)';
$Self->{'AuthSyncModule::LDAP::UserSyncMap'} = {
# DB -> LDAPUserFirstname =>'givenName',
UserLastname =>'sn',
UserEmail =>'mail',
};
$Self->{'AuthSyncModule::LDAP::AccessAttr'} = 'member';
$Self->{'AuthSyncModule::LDAP::UserAttr'} = 'DN';
# Включать агента в какие-либо группы с доступом на чтение/запись# AuthSyncModule::LDAP::UserSyncInitialGroups# (sync following group with rw permission after initial create of first agent# login)
$Self->{'AuthSyncModule::LDAP::UserSyncInitialGroups'} = [
'users',
];
$Self->{DatabaseUserTable} = 'users';
$Self->{DatabaseUserTableUserID} = 'id';
$Self->{DatabaseUserTableUserPW} = 'pw';
$Self->{DatabaseUserTableUser} = 'login';
# --------------------------------------------------- ## End Agents authentication sync ## --------------------------------------------------- #Customer setup
Client Authentication
# --------------------------------------------------- ## Сustomer authentication ## --------------------------------------------------- ## Сustomer DB auth. backend
$Self->{'Customer::AuthModule'} = 'Kernel::System::CustomerAuth::DB';
$Self->{'Customer::AuthModule::DB::Table'} = 'customer_user';
$Self->{'Customer::AuthModule::DB::CustomerKey'} = 'login';
$Self->{'Customer::AuthModule::DB::CustomerPassword'} = 'pw';
# my-it-company.com (Сustomer) LDAP auth. backend
$Self->{'Customer::AuthModule2'} = 'Kernel::System::CustomerAuth::LDAP';
$Self->{'Customer::AuthModule::LDAP::Host2'} = 'my-it-company.com';
$Self->{'Customer::AuthModule::LDAP::BaseDN2'} = 'dc=my-it-company,dc=com';
$Self->{'Customer::AuthModule::LDAP::UID2'} = 'uid';
$Self->{'Customer::AuthModule::LDAP::SearchUserDN2'} = 'uid=ldap-bot,cn=users,cn=accounts,dc=my-it-company,dc=com';
$Self->{'Customer::AuthModule::LDAP::SearchUserPw2'} = 'bot-password!';
$Self->{'Customer::AuthModule::LDAP::AlwaysFilter2'} = '(mail=*)';
# pear LDAP auth. backend.
$Self->{'Customer::AuthModule3'} = 'Kernel::System::CustomerAuth::LDAP';
$Self->{'Customer::AuthModule::LDAP::Host3'} = 'pear.com';
$Self->{'Customer::AuthModule::LDAP::BaseDN3'} = 'DC=pear,DC=com';
$Self->{'Customer::AuthModule::LDAP::UID3'} = 'sAMAccountName';
$Self->{'Customer::AuthModule::LDAP::SearchUserDN3'} = 'ldap-bot@pear.com';
$Self->{'Customer::AuthModule::LDAP::SearchUserPw3'} = 'bot-password?';
# Отфильтруем: (mail=*) - у кого есть почта и (samAccountType=805306368) - учетная запись пользователя и (!(userAccountControl:1.2.840.113556.1.4.803:=2)) - не отключена
$Self->{'Customer::AuthModule::LDAP::AlwaysFilter3'} = '(&(mail=*)(samAccountType=805306368)(!(userAccountControl:1.2.840.113556.1.4.803:=2)))';
# macrohard LDAP auth. backend.
$Self->{'Customer::AuthModule4'} = 'Kernel::System::CustomerAuth::LDAP';
$Self->{'Customer::AuthModule::LDAP::Host4'} = 'macrohard.com';
$Self->{'Customer::AuthModule::LDAP::BaseDN4'} = 'dc=macrohard,dc=com';
$Self->{'Customer::AuthModule::LDAP::UID4'} = 'sAMAccountName';
$Self->{'Customer::AuthModule::LDAP::SearchUserDN4'} = 'ldap-bot@macrohard.com';
$Self->{'Customer::AuthModule::LDAP::SearchUserPw4'} = 'bot-password!?';
$Self->{'Customer::AuthModule::LDAP::AlwaysFilter4'} = '(&(mail=*)(samAccountType=805306368)(!(userAccountControl:1.2.840.113556.1.4.803:=2)))';
# --------------------------------------------------- ## End customer authentication settings ## --------------------------------------------------- #Client synchronization (getting client attributes from LDAP, communication with OTRS companies)
# --------------------------------------------------- ## Customer authentication sync ## --------------------------------------------------- ## Customer user DB backend and settings
$Self->{CustomerUser} = {
Name => Translatable('Database Backend'),
Module =>'Kernel::System::CustomerUser::DB',
Params => {
Table =>'customer_user',
SearchCaseSensitive =>0,
},
# customer unique idCustomerKey =>'login',
# customer #CustomerID =>'customer_id',
CustomerValid =>'valid_id',
CustomerUserListFields => [ 'first_name', 'last_name', 'email' ],
CustomerUserSearchFields => [ 'login', 'first_name', 'last_name', 'customer_id' ],
CustomerUserSearchPrefix =>'*',
CustomerUserSearchSuffix =>'*',
CustomerUserSearchListLimit =>250,
CustomerUserPostMasterSearchFields => ['email'],
CustomerUserNameFields => [ 'title', 'first_name', 'last_name' ],
CustomerUserEmailUniqCheck =>1,
CustomerCompanySupport =>1,
CacheTTL =>60 * 60 * 24,
Map => [
[ 'UserTitle', Translatable('Title or salutation'), 'title', 1, 0, 'var', '', 0, undef, undef ],
[ 'UserFirstname', Translatable('Firstname'), 'first_name', 1, 1, 'var', '', 0, undef, undef ],
[ 'UserLastname', Translatable('Lastname'), 'last_name', 1, 1, 'var', '', 0, undef, undef ],
[ 'UserLogin', Translatable('Username'), 'login', 1, 1, 'var', '', 0, undef, undef ],
[ 'UserPassword', Translatable('Password'), 'pw', 0, 0, 'var', '', 0, undef, undef ],
[ 'UserEmail', Translatable('Email'), 'email', 1, 1, 'var', '', 0, undef, undef ],
[ 'UserCustomerID', Translatable('CustomerID'), 'customer_id', 0, 1, 'var', '', 0, undef, undef ],
[ 'UserPhone', Translatable('Phone'), 'phone', 1, 0, 'var', '', 0, undef, undef ],
[ 'UserFax', Translatable('Fax'), 'fax', 1, 0, 'var', '', 0, undef, undef ],
[ 'UserMobile', Translatable('Mobile'), 'mobile', 1, 0, 'var', '', 0, undef, undef ],
[ 'UserStreet', Translatable('Street'), 'street', 1, 0, 'var', '', 0, undef, undef ],
[ 'UserZip', Translatable('Zip'), 'zip', 1, 0, 'var', '', 0, undef, undef ],
[ 'UserCity', Translatable('City'), 'city', 1, 0, 'var', '', 0, undef, undef ],
[ 'UserCountry', Translatable('Country'), 'country', 1, 0, 'var', '', 0, undef, undef ],
[ 'UserComment', Translatable('Comment'), 'comments', 1, 0, 'var', '', 0, undef, undef ],
[ 'ValidID', Translatable('Valid'), 'valid_id', 0, 1, 'int', '', 0, undef, undef ],
],
# default selectionsSelections => {
# UserTitle => {# 'Mr.' => Translatable('Mr.'),# 'Mrs.' => Translatable('Mrs.'),# },
},
};
# my-it-company.com customer user ldap backend and settings
$Self->{CustomerUser2} = {
Name =>'AD my-it-company.com',
Module =>'Kernel::System::CustomerUser::LDAP',
Params => {
# ldap hostHost =>'my-it-company.com',
# ldap base dnBaseDN =>'dc=my-it-company,dc=com',
# search scope (one|sub)SSCOPE =>'sub',
UserDN =>'uid=ldap-bot,cn=users,cn=accounts,dc=my-it-company,dc=com',
UserPw =>'bot-password!',
# in case you want to add always one filter to each ldap query, use# this option. e. g. AlwaysFilter => '(mail=*)' or AlwaysFilter => '(objectclass=user)'AlwaysFilter =>'(mail=*)',
SourceCharset =>'utf-8',
Die =>0,
},
# customer unique idCustomerKey =>'uid',
# customer #CustomerID =>'ou',
CustomerUserListFields => ['uid', 'cn', 'mail'],
CustomerUserSearchFields => ['uid', 'cn', 'mail'],
CustomerUserSearchPrefix =>'',
CustomerUserSearchSuffix =>'*',
CustomerUserSearchListLimit =>250,
CustomerUserPostMasterSearchFields => ['mail'],
CustomerUserNameFields => ['sn', 'givenname'],
# Configures the character for joining customer user name parts. Join single space if it is not defined.CustomerUserNameFieldsJoin =>' ',
# show customer user and customer tickets in customer interfaceCustomerUserExcludePrimaryCustomerID =>0,
# add a ldap filter for valid users (expert setting)# CustomerUserValidFilter => '(!(description=gesperrt))',# admin can't change customer preferencesAdminSetPreferences =>1,
# cache time to live in sec. - cache any ldap queriesCacheTTL =>0,
Map => [
[ 'UserTitle', Translatable('Title or salutation'), 'title', 1, 0, 'var', '', 1, undef, undef ],
[ 'UserFirstname', Translatable('Firstname'), 'givenname', 1, 1, 'var', '', 1, undef, undef ],
[ 'UserLastname', Translatable('Lastname'), 'sn', 1, 1, 'var', '', 1, undef, undef ],
[ 'UserLogin', Translatable('Username'), 'uid', 1, 1, 'var', '', 1, undef, undef ],
[ 'UserEmail', Translatable('Email'), 'mail', 1, 1, 'var', '', 1, undef, undef ],
[ 'UserCustomerID', Translatable('CustomerID'), 'ou', 0, 1, 'var', '', 1, undef, undef ],
[ 'UserPhone', Translatable('Phone'), 'telephonenumber', 1, 0, 'var', '', 1, undef, undef ],
[ 'UserMobile', Translatable('Mobile'), 'mobile', 1, 0, 'var', '', 1, undef, undef ],
],
};
# pear customer user ldap backend and settings
$Self->{CustomerUser3} = {
Name =>'AD pear',
Module =>'Kernel::System::CustomerUser::LDAP',
Params => {
# ldap hostHost =>'pear.com',
BaseDN =>'DC=pear,DC=com',
SSCOPE =>'sub',
UserDN =>'ldap-bot@pear.com',
UserPw =>'bot-password?',
AlwaysFilter =>'(&(mail=*)(samAccountType=805306368)(!(userAccountControl:1.2.840.113556.1.4.803:=2)))',
SourceCharset =>'utf-8',
Die =>0,
},
# customer unique idCustomerKey =>'sAMAccountName',
# customer #CustomerID =>'company',
CustomerUserListFields => ['sAMAccountName', 'cn', 'mail'],
CustomerUserSearchFields => ['sAMAccountName', 'cn', 'mail'],
CustomerUserSearchPrefix =>'',
CustomerUserSearchSuffix =>'*',
CustomerUserSearchListLimit =>250,
CustomerUserPostMasterSearchFields => ['mail'],
CustomerUserNameFields => ['sn', 'givenname'],
# Configures the character for joining customer user name parts. Join single space if it is not defined.CustomerUserNameFieldsJoin =>' ',
# show customer user and customer tickets in customer interfaceCustomerUserExcludePrimaryCustomerID =>0,
AdminSetPreferences =>1,
CacheTTL =>0,
Map => [
# note: Login, Email and CustomerID needed!# var, frontend, storage, shown (1=always,2=lite), required, storage-type, http-link, readonly, http-link-target, link class(es)
[ 'UserTitle', Translatable('Title or salutation'), 'title', 1, 0, 'var', '', 1, undef, undef ],
[ 'UserFirstname', Translatable('Firstname'), 'givenname', 1, 1, 'var', '', 1, undef, undef ],
[ 'UserLastname', Translatable('Lastname'), 'sn', 1, 1, 'var', '', 1, undef, undef ],
[ 'UserLogin', Translatable('Username'), 'sAMAccountName', 1, 1, 'var', '', 1, undef, undef ],
[ 'UserFullLogin', Translatable('FullUsername'), 'userPrincipalName', 1, 1, 'var', '', 1, undef, undef ],
[ 'UserEmail', Translatable('Email'), 'mail', 1, 1, 'var', '', 1, undef, undef ],
[ 'UserCustomerID', Translatable('CustomerID'), 'company', 0, 1, 'var', '', 1, undef, undef ],
[ 'UserPhone', Translatable('Phone'), 'telephoneNumber', 1, 0, 'var', '', 1, undef, undef ],
[ 'UserMobile', Translatable('Mobile'), 'mobile', 1, 0, 'var', '', 1, undef, undef ],
[ 'UserAddress', Translatable('Address'), 'postaladdress', 1, 0, 'var', '', 1, undef, undef ],
[ 'UserOffice', Translatable('Office'), 'physicalDeliveryOfficeName', 1, 0, 'var', '', 1, undef, undef ],
[ 'UserDepartment', Translatable('Department'), 'department', 1, 0, 'var', '', 1, undef, undef ],
[ 'UserComment', Translatable('Comment'), 'description', 1, 0, 'var', '', 1, undef, undef ],
],
};
# macrohard customer user ldap backend and settings
$Self->{CustomerUser4} = {
Name =>'AD macrohard',
Module =>'Kernel::System::CustomerUser::LDAP',
Params => {
# ldap hostHost =>'macrohard.com',
# ldap base dnBaseDN =>'dc=macrohard,dc=com',
# search scope (one|sub)SSCOPE =>'sub',
UserDN =>'ldap-bot@macrohard.com',
UserPw =>'bot-password!?',
AlwaysFilter =>'(&(mail=*)(samAccountType=805306368)(!(userAccountControl:1.2.840.113556.1.4.803:=2)))',
SourceCharset =>'utf-8',
Die =>0,
},
# customer unique idCustomerKey =>'sAMAccountName',
# customer #CustomerID =>'company',
CustomerUserListFields => ['sAMAccountName', 'cn', 'mail'],
CustomerUserSearchFields => ['sAMAccountName', 'cn', 'mail'],
CustomerUserSearchPrefix =>'',
CustomerUserSearchSuffix =>'*',
CustomerUserSearchListLimit =>250,
CustomerUserPostMasterSearchFields => ['mail'],
CustomerUserNameFields => ['sn', 'givenname'],
# Configures the character for joining customer user name parts. Join single space if it is not defined.CustomerUserNameFieldsJoin =>' ',
# show customer user and customer tickets in customer interfaceCustomerUserExcludePrimaryCustomerID =>0,
AdminSetPreferences =>1,
CacheTTL =>0,
Map => [
[ 'UserTitle', Translatable('Title or salutation'), 'title', 1, 0, 'var', '', 1, undef, undef ],
[ 'UserFirstname', Translatable('Firstname'), 'givenname', 1, 1, 'var', '', 1, undef, undef ],
[ 'UserLastname', Translatable('Lastname'), 'sn', 1, 1, 'var', '', 1, undef, undef ],
[ 'UserLogin', Translatable('Username'), 'sAMAccountName', 1, 1, 'var', '', 1, undef, undef ],
[ 'UserFullLogin', Translatable('FullUsername'), 'userPrincipalName', 1, 1, 'var', '', 1, undef, undef ],
[ 'UserEmail', Translatable('Email'), 'mail', 1, 1, 'var', '', 1, undef, undef ],
[ 'UserCustomerID', Translatable('CustomerID'), 'company', 0, 1, 'var', '', 1, undef, undef ],
[ 'UserPhone', Translatable('Phone'), 'telephoneNumber', 1, 0, 'var', '', 1, undef, undef ],
[ 'UserMobile', Translatable('Mobile'), 'mobile', 1, 0, 'var', '', 1, undef, undef ],
[ 'UserAddress', Translatable('Address'), 'postaladdress', 1, 0, 'var', '', 1, undef, undef ],
[ 'UserOffice', Translatable('Office'), 'physicalDeliveryOfficeName', 1, 0, 'var', '', 1, undef, undef ],
[ 'UserDepartment', Translatable('Department'), 'department', 1, 0, 'var', '', 1, undef, undef ],
[ 'UserComment', Translatable('Comment'), 'description', 1, 0, 'var', '', 1, undef, undef ],
],
};Conclusion
As you have seen, setting up authentication and synchronization of accounts in OTRS is very simple, but still I hope that this article will help those who are just starting to get acquainted with this system.
What is left behind this article?
- In parallel with LDAP, you can also run SSO authentication, which will make life easier for customers
- If there are experts on Perl - you can write your own backend to connect to other information systems.
- The configuration is consciously simplified, for example, there are no filtering blocks by affiliation to LDAP groups, no domain suffixes, BASE DN, work with additional attributes, work with LDAP on other ports, and much more.
Tips and clarifications welcome comments, information about typos - in drugs.
Thanks for attention. Special thanks to the authors whose materials on OTRS I used many years ago when meeting this system: Turilion , supersuperoleg , wmlex
