Is there a switch, or how to turn off the Internet?
Inspired by this post about six coders and the Internet, which they will restart after the cataclysm.
True, the methods of incapacitating the Internet are not entirely clear, given that some Internet service providers have built data centers in anti-nuclear bunkers underground, with a door 40 centimeters, as in Sweden , but only God knows how the military data centers of the Russian Federation or the United States are protected.
So I decided to analyze a bit what we know about attacks on the global network and measures to repel them.
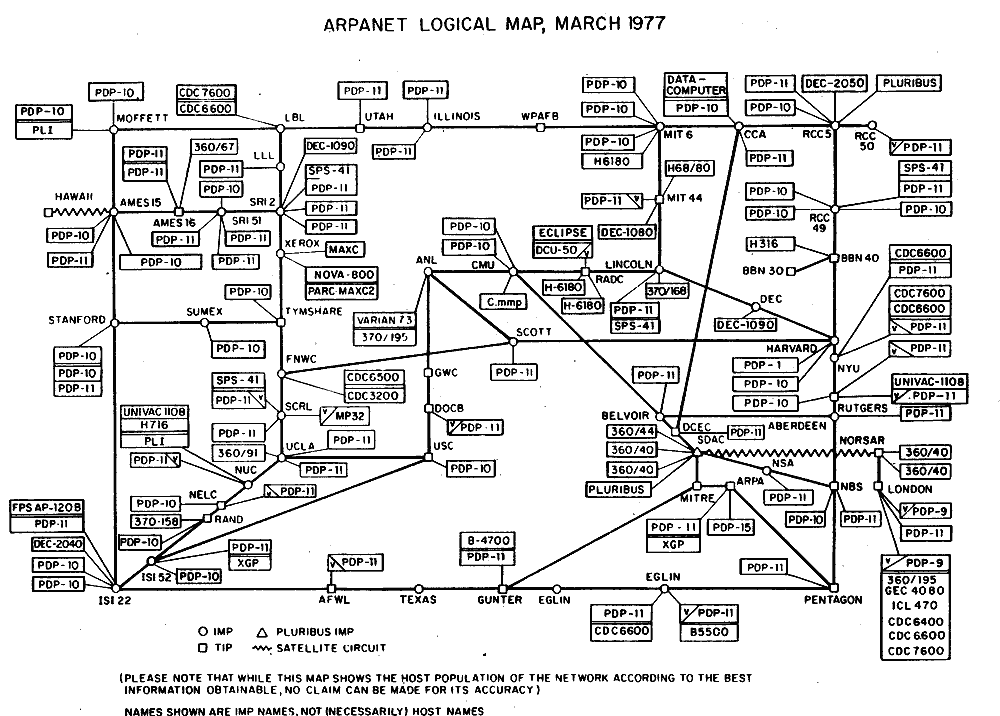
As you know, the Internet is the general son of ARPANET, whose father was the DARPA military project with a budget of $ 3.2 billion. Although Charles Herzfeld was the director of ARPANET 65-67, he did not hint that the Cold War and the fear of Nuclear War with the USSR could serve as the goal of creating the project. But, with speculation by the fact, one might think that ARPANET was just created to centralize the US command and possibly other national security goals at that time, and of course I was sure that there were talks about protecting communications during the Nuclear Attack. That raised the urgent issue of protecting the Internet, at its earliest stages of conception.
By the way, this is what Charles said about this:
30 years have passed ...
April 1997
Seven out of 13 ROOT DNS servers are due to technical problems. He doesn’t especially advertise what kind of problems they’ve got and how they were fixed, but some time before troubleshooting, the remaining 6 DNS servers served the Internet for everyone else. By the way, why is the number of root servers 13? this number quite often appears in US history and has vague symbolism; for example 13 — the first Colony States to break away from the British Lion, 13 stripes on the flag, 13 steps on the Pyramid, 13 branches of an olive tree, 13 stars above the Eagle and 13 arrows on US banknotes.
October 2002 October
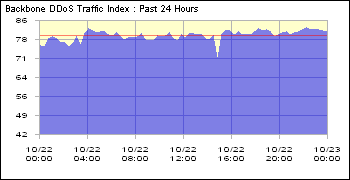
21, 2002 beganDOS attack on all 13 ROOT DNS servers - the traffic volume reached 50 to 100 Mbits / sec per server. In total, traffic was about 900 Mbits / sec. Traffic was garbage from ICMP, TCP SYN, fragmented TCP, and UDP packets. Some servers ceased to be accessible to many parts of the world, but again, all survived. Obviously, for whom it was beneficial to put the World Wide Web in these 3 days, it will remain a mystery of history. But what the traffic looked like in a couple of days ...
February 2007
On February 6, 2007 the attack lasted more than 24 hours and disabled 2 servers:
g.root-servers.net ICANN
 and
and
l.root-servers.net United States Department of Defense

Botnet was used to carry out this attack, approximately the size of ~ 4500-5000 Windows machines. % Of 65 infected machines were in South Korea, 19% in the United States, but the botnet HTTP controller itself in the same place - in Dallas, Texas. Analysts also sniffed out the “Russian trace” - for example, the trace that the botnet was purchased from a Russian seller and was later used for some Russian purpose. Well, okay, about the Russian trace, but here is how the attack looked technically:
* Bots used one DNS request for a victim and 3 threads for a victim.
* Unique but stable sorce port on every thread.
* each thread was with its 1023-octet "grain"
* UDP packets were poured onto port 53 of each victim.
* The source address of the bots has not been changed.
* Each victim thread has been with expire parameters for 24 hours.
To combat the attack, the following rules were recommended:
* 'dst port 53 and udp [10: 2]> 0 and udp [12: 2]! = 1 and udp [14: 2]> 0 ′
* 10: 2 dns flags
* 12: 2 qdcount
* 14: 2 ancount and filter> 300-512 octets - which dumped most of the traffic, even quite legitimate, but helped in the fight against flood.
2 days later, on February 8, Network World magazine made an international statement, where they recalled the US Presidential Decree on a possible bomb strike of a location of a cyber attack source:
If the United States found itself under a major cyberattack aimed at undermining the nation's critical information infrastructure, the Department of Defense is prepared, based on the authority of the President, to launch an actual bombing of an attack source or a cyber counterattack.
One can only hope that from now on no one will disturb the peace of the thirteen Network Whales and no one will have to bomb the enemy’s botnet with uranium earth-to-ground missiles.
Although, time will tell ...
True, the methods of incapacitating the Internet are not entirely clear, given that some Internet service providers have built data centers in anti-nuclear bunkers underground, with a door 40 centimeters, as in Sweden , but only God knows how the military data centers of the Russian Federation or the United States are protected.
So I decided to analyze a bit what we know about attacks on the global network and measures to repel them.

As you know, the Internet is the general son of ARPANET, whose father was the DARPA military project with a budget of $ 3.2 billion. Although Charles Herzfeld was the director of ARPANET 65-67, he did not hint that the Cold War and the fear of Nuclear War with the USSR could serve as the goal of creating the project. But, with speculation by the fact, one might think that ARPANET was just created to centralize the US command and possibly other national security goals at that time, and of course I was sure that there were talks about protecting communications during the Nuclear Attack. That raised the urgent issue of protecting the Internet, at its earliest stages of conception.
By the way, this is what Charles said about this:
The ARPANET was not started to create a Command and Control System that would survive a nuclear attack, as many now claim. To build such a system was, clearly, a major military need, but it was not ARPA’s mission to do this; 30 years have passed ...
April 1997
Seven out of 13 ROOT DNS servers are due to technical problems. He doesn’t especially advertise what kind of problems they’ve got and how they were fixed, but some time before troubleshooting, the remaining 6 DNS servers served the Internet for everyone else. By the way, why is the number of root servers 13? this number quite often appears in US history and has vague symbolism; for example 13 — the first Colony States to break away from the British Lion, 13 stripes on the flag, 13 steps on the Pyramid, 13 branches of an olive tree, 13 stars above the Eagle and 13 arrows on US banknotes.
October 2002 October
21, 2002 beganDOS attack on all 13 ROOT DNS servers - the traffic volume reached 50 to 100 Mbits / sec per server. In total, traffic was about 900 Mbits / sec. Traffic was garbage from ICMP, TCP SYN, fragmented TCP, and UDP packets. Some servers ceased to be accessible to many parts of the world, but again, all survived. Obviously, for whom it was beneficial to put the World Wide Web in these 3 days, it will remain a mystery of history. But what the traffic looked like in a couple of days ...

February 2007
On February 6, 2007 the attack lasted more than 24 hours and disabled 2 servers:
g.root-servers.net ICANN
 and
and l.root-servers.net United States Department of Defense

Botnet was used to carry out this attack, approximately the size of ~ 4500-5000 Windows machines. % Of 65 infected machines were in South Korea, 19% in the United States, but the botnet HTTP controller itself in the same place - in Dallas, Texas. Analysts also sniffed out the “Russian trace” - for example, the trace that the botnet was purchased from a Russian seller and was later used for some Russian purpose. Well, okay, about the Russian trace, but here is how the attack looked technically:
* Bots used one DNS request for a victim and 3 threads for a victim.
* Unique but stable sorce port on every thread.
* each thread was with its 1023-octet "grain"
* UDP packets were poured onto port 53 of each victim.
* The source address of the bots has not been changed.
* Each victim thread has been with expire parameters for 24 hours.
To combat the attack, the following rules were recommended:
* 'dst port 53 and udp [10: 2]> 0 and udp [12: 2]! = 1 and udp [14: 2]> 0 ′
* 10: 2 dns flags
* 12: 2 qdcount
* 14: 2 ancount and filter> 300-512 octets - which dumped most of the traffic, even quite legitimate, but helped in the fight against flood.
2 days later, on February 8, Network World magazine made an international statement, where they recalled the US Presidential Decree on a possible bomb strike of a location of a cyber attack source:
If the United States found itself under a major cyberattack aimed at undermining the nation's critical information infrastructure, the Department of Defense is prepared, based on the authority of the President, to launch an actual bombing of an attack source or a cyber counterattack.
One can only hope that from now on no one will disturb the peace of the thirteen Network Whales and no one will have to bomb the enemy’s botnet with uranium earth-to-ground missiles.
Although, time will tell ...
