The radio navigation systems used by aircraft for a safe landing are unsafe and prone to cracking
- Transfer
The signal by which planes find the runway can be faked using a walkie-talkie for $ 600

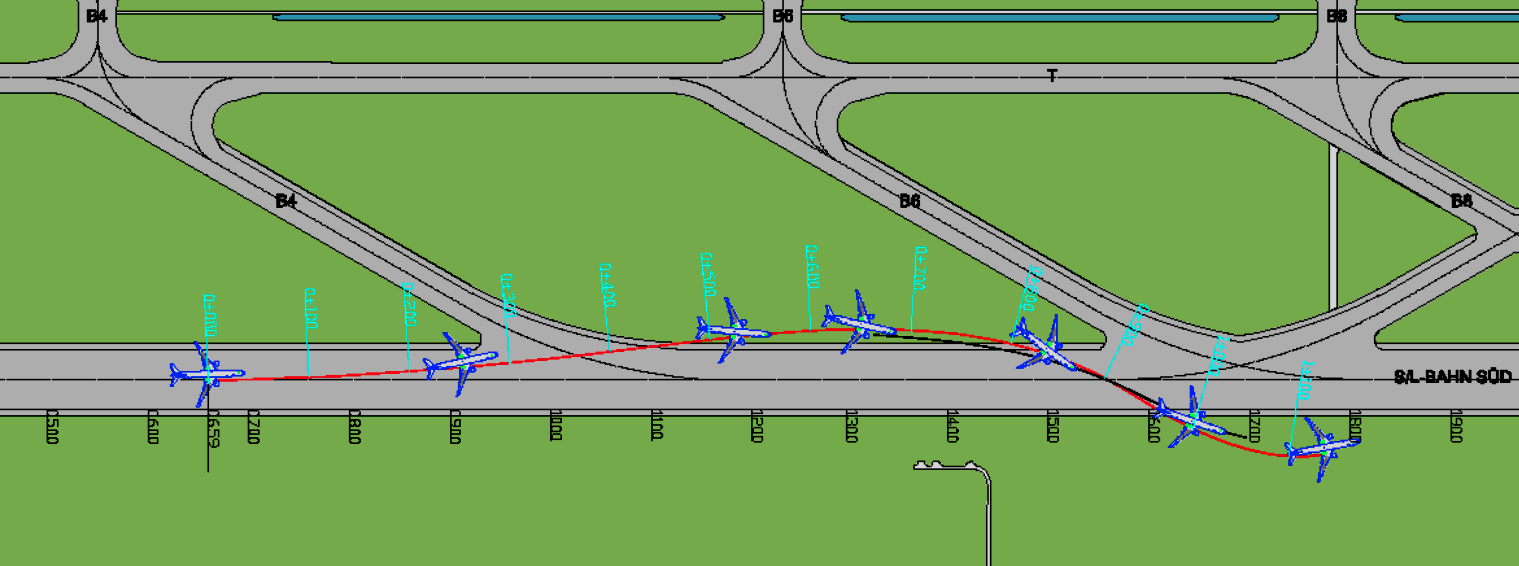
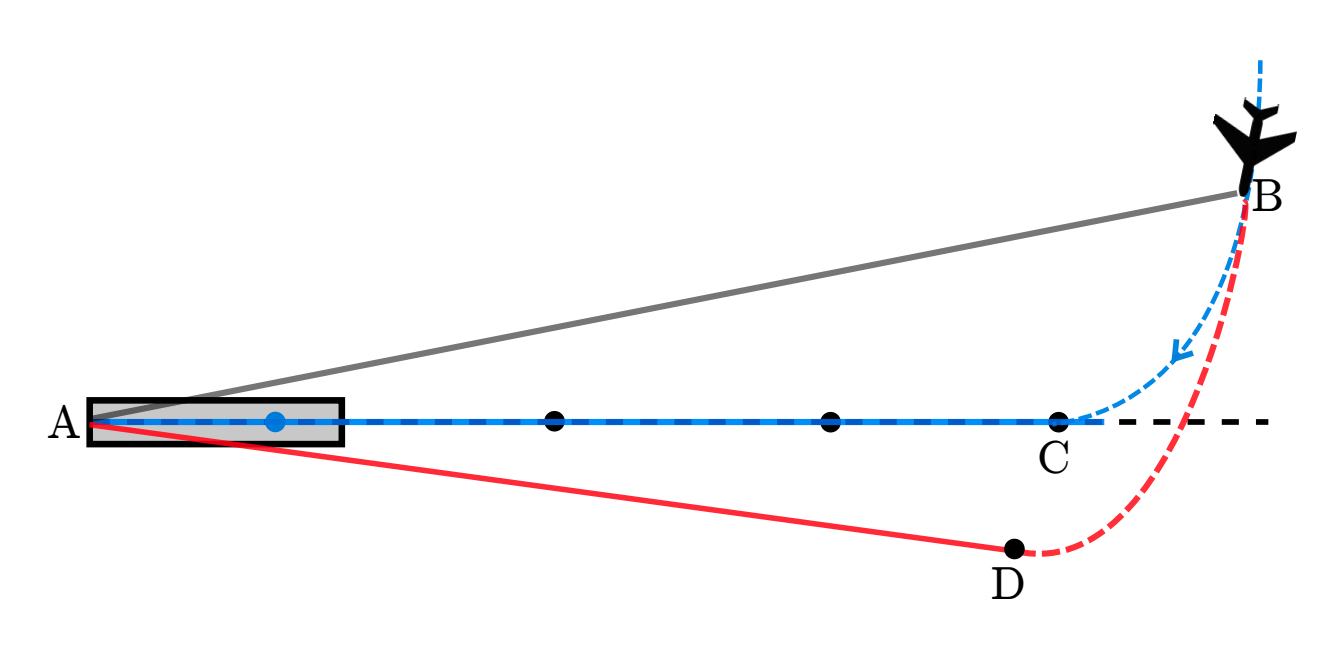
A plane in a demonstration of an attack on the radio, due to fake KGS signals, lands to the right of the landing strip
Almost any aircraft that has flown in the last 50 years - whether it be a single-engine Cessna plane or a giant airliner with 600 seats - used the help of radio stations to safely land at airports. These course-glide path systems, CGS (ILS, instrument landing system), are considered close proximity systems, because, unlike GPS and other navigation systems, they provide vital information in real time about the horizontal orientation of the aircraft relative to the landing strip and vertical angle of descent. In many conditions - especially during landings in fog or in the rain at night - this radio navigation remains the main way to ensure that the plane touches the ground at the beginning of the strip and exactly in the middle.
Like many other technologies created in the past, KGS did not provide protection against hacking. Radio signals are not encrypted, and their authenticity is not confirmed. Pilots simply assume that the sound signals received by their systems at the frequency assigned to the airport are real signals broadcast by the airport operator. For many years, this lack of security bothered almost no one, mainly because the cost and complexity of signal falsification made attacks pointless.
But now, researchers have developed a low-cost hacking method that raises questions about the security of CGS used in almost every civilian airport in the industrial world. Using a $ 600 programmable radio station, researchers can fake airport signals so that the pilot's navigation tools show that the plane is off course. According to the training, the pilot must correct the speed of descent or orientation of the vessel, thereby creating a threat to the accident.
One attack technology is that fake signals indicate that the angle of descent is smaller than it actually is. The forged message contains the so-called the “take down” signal informing the pilot about the need to increase the angle of descent, which may lead to the plane touching the ground before the start of the landing strip.
The video shows a differently tampered signal that could pose a threat to the aircraft landing. The attacker can send a signal informing the pilot that his plane is to the left of the center line of the landing strip, when in fact the plane is exactly in the center. The pilot will react, taking the plane to the right, which is why it will eventually shift to the side.
Researchers at Northeastern University in Boston consulted with a pilot and security expert, and cautiously note that such signal falsification is unlikely to lead to an accident in most cases. Malfunctions in the CSC are a known threat to flight safety, and experienced pilots undergo detailed training on how to respond to them. In clear weather, it will be easy for the pilot to notice that the plane is not aligned with the center line of the strip, and he will be able to leave for the second round.
Another reason for reasonable skepticism is the complexity of the attack. In addition to a programmable radio station, directional antennas and an amplifier are required. All this equipment will be quite difficult to smuggle into the plane if the hacker wants to carry out an attack from the aircraft. If he decides to attack from the ground, it will take a lot of work to level the equipment with the landing strip, without attracting attention. Moreover, airports usually monitor for interference at critical frequencies, which may cause the attack to be stopped shortly after the start.
In 2012, researcher Brad Haines, known as Renderman , uncovered vulnerabilitiesin the AZN-V system (automatic dependent surveillance-broadcasting), which aircraft use to determine their location and transmit data to other aircraft. He summed up the difficulties of a real fake of KGS signals as follows:
If everything converges - location, hidden equipment, bad weather, suitable target, well-motivated, smart and financially capable attacker - what happens? In the worst case scenario, the plane will land on the grass, injuries or deaths are possible, however, the safe development of the aircraft and the quick response teams provide a very low probability of a huge fire with the loss of the entire aircraft. In this case, the landing will be suspended, and the attacker will not be able to repeat this. In the best case, the pilot will notice a discrepancy, get his pants dirty, increase his height, go to the second round, and report that something is wrong with the CSC - the airport will begin an investigation, which means that the attacker will no longer want to stay nearby.
So, if everything converges, then the result will be minimal. Compare this with the ratio of result to investment and the economic effect of the case when one goat with a drone flew around Heathrow Airport for two days for two days. Surely the drone was a more effective and working option than such an attack.
Still, the researchers say that there are risks. Aircraft that do not fall into the glide path — the imaginary line that the plane follows in perfect landing — are much harder to detect even in fine weather. Moreover, some busy airports, in order to avoid delays, tell planes not to rush to leave for the second circle even in conditions of poor visibility. Landing instructions from the US Federal Aviation Administration, which are followed by many US airports, indicate that such a decision should be made at an altitude of only 15 m. Similar instructions apply in Europe. They leave the pilot very little time to safely interrupt the landing if visually the surrounding conditions do not match the data from the CSC.
“Detecting and recovering in the event of failure of any tools during critical landing procedures is one of the most difficult tasks of modern aviation,” the researchers wrote in their work entitled “Wireless attacks on glide path systems of aircraft”, adopted on the 28th USENIX Security Symposium . “Given how much pilots rely on CSG and tools in general, failure and malicious interference can lead to disastrous consequences, especially during autonomous raids and flights.”
What happens to CGS failures
Several touchdowns, which almost led to disaster, demonstrate the danger of failures of KGS. In 2011, a flight of SQ327 Singapore Airlines with 143 passengers and 15 crew members on board suddenly tilted to the left, being 10 meters above the landing strip at Munich Airport in Germany. After landing, the Boeing 777-300 leaned to the left, then turned right, crossed the center line and stopped when the chassis was in the grass to the right of the landing strip.

In the reportabout the incident, published by the German Federal Commission for the Investigation of Incidents with Aircraft, it is written that the plane overshot the landing point at 500 m. Investigators said that one of the perpetrators of the incident was the distortion of the signals of the landing radio beacon by the take-off aircraft. Although no casualties were reported, this event underscored the severity of the failure of the CGS systems. Other incidents involving the failure of the CSC, which almost ended in tragedy, include the New Zealand flight NZ 60 in 2000 and the flight of Ryanair FR3531 in 2013. The video explains what went wrong in the latter case.
Vibhab Sharma has been managing the security company in Silicon Valley worldwide and has been flying small planes since 2006. He also has a license from an amateur communications operator and participates on a voluntary basis in a civilian air patrol, where he underwent training for a lifeguard and radio operator. He controls the aircraft in the X-Plane simulator, demonstrating a signal-swapping attack that causes the aircraft to land to the right of the landing strip.
Sharma told us:
Such an attack on the CGS is realistic, but its effectiveness will depend on a combination of factors, including knowledge of the attacking air navigation systems and conditions on approach. If used appropriately, the attacker will be able to lead the aircraft towards obstacles surrounding the airport, and if this is done in conditions of poor visibility, it will be very difficult for the pilot team to detect deviations and deal with them.
He said the attacks have the potential to threaten both small aircraft and large jet aircraft, but for various reasons. Small planes move at lower speeds. This gives the pilots time to react. Large jet aircraft, on the other hand, have more members on the team who can respond to adverse events, while pilots of such vessels are usually trained more often and more thoroughly.
He said that the most important thing for large and small aircraft would be to assess the environmental conditions, in particular, the weather, during landing.
“Such an attack is likely to be more effective when pilots have to rely more on instruments to carry out a successful landing,” Sharma said. “It can be night landings in conditions of poor visibility, or a combination of poor conditions with a loaded airspace, requiring more workload from pilots, which makes them highly dependent on automation.”
Aanjan Ranganatan, a researcher from Northeastern University who helped develop the attack, told us that there’s almost no reason to rely on GPS help in the event of a CSC failure. Deviations from the landing strip during an effective attack with substitution will be from 10 to 15 meters, since all that will be more, pilots and air traffic controllers will be able to notice. GPS will be able to detect such deviations with great difficulty. The second reason is that replacing GPS signals is very easy.
“I can replace the GPS in parallel with the substitution of the CGS,” said Ranganatan. “The whole question is the degree of motivation of the attacker.”
CGS predecessor
The tests of the CSC began back in 1929 , and the first working system was deployed in 1932 at the German airport Berlin-Tempelhof.
KGS remains one of the most effective landing systems. Other approaches, for example, an omnidirectional azimuthal beacon , a drive beacon, a global positioning system and similar satellite navigation systems, are considered inaccurate because they provide only horizontal or lateral orientation. CGS is considered to be an accurate approach system, since it gives both horizontal and vertical (glide path) orientation. In recent years, inaccurate systems have been used less and less. CGS is increasingly associated with autopilots and auto-landing systems.
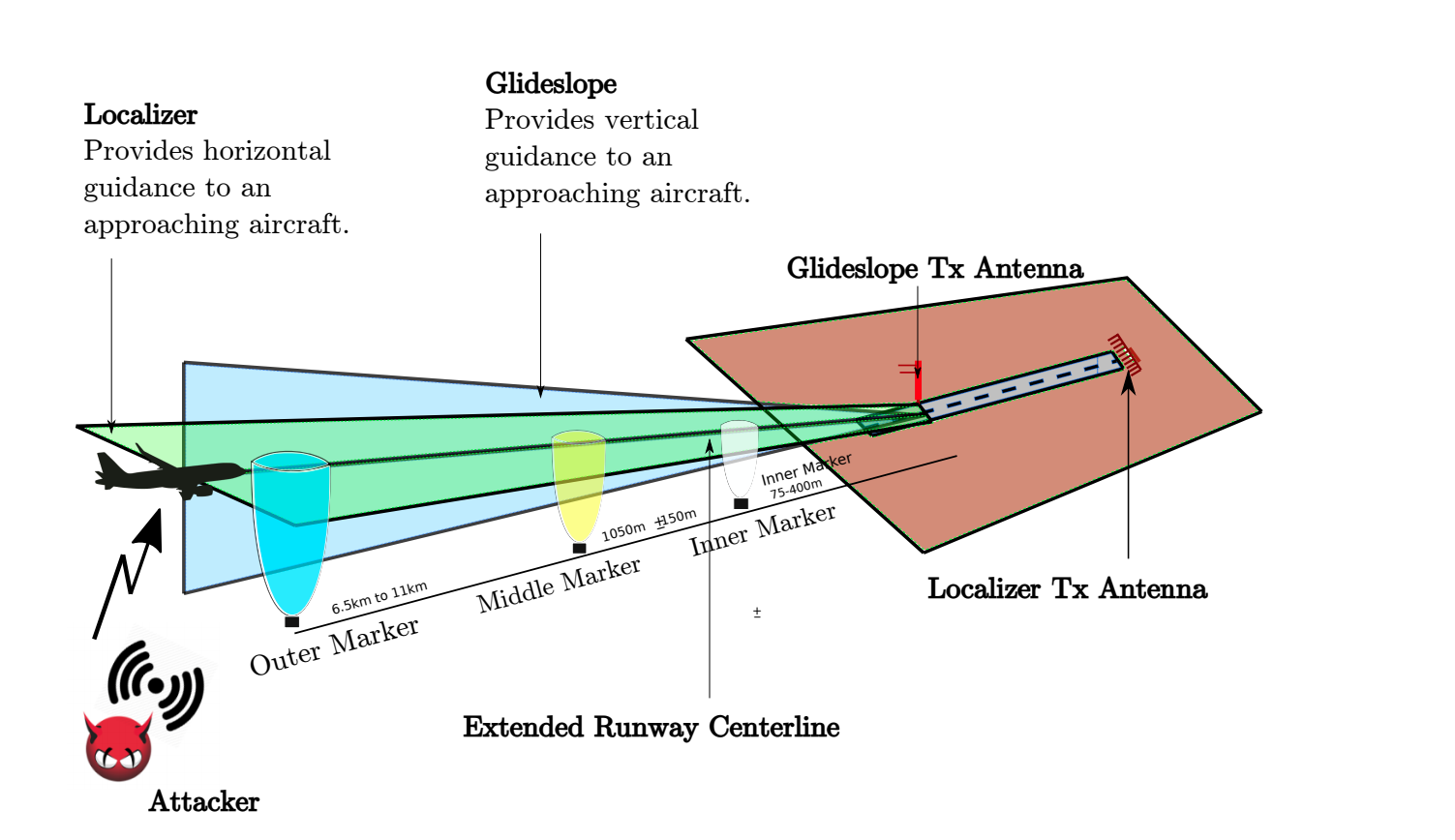
How the CGS works: heading radio beacon [localizer], glide slope [glideslope] and marker beacons [marker beacon]
The CGS has two key components. The directional radio beacon informs the pilot whether the plane is shifted left or right from the center line of the landing strip, and the slope of the glide path says whether the descent angle is too large so that the plane does not miss past the beginning of the strip. The third component is marker beacons. They work as milestones, allowing the pilot to determine the distance to the strip. Over the years, they are increasingly being replaced by GPS and other technologies.
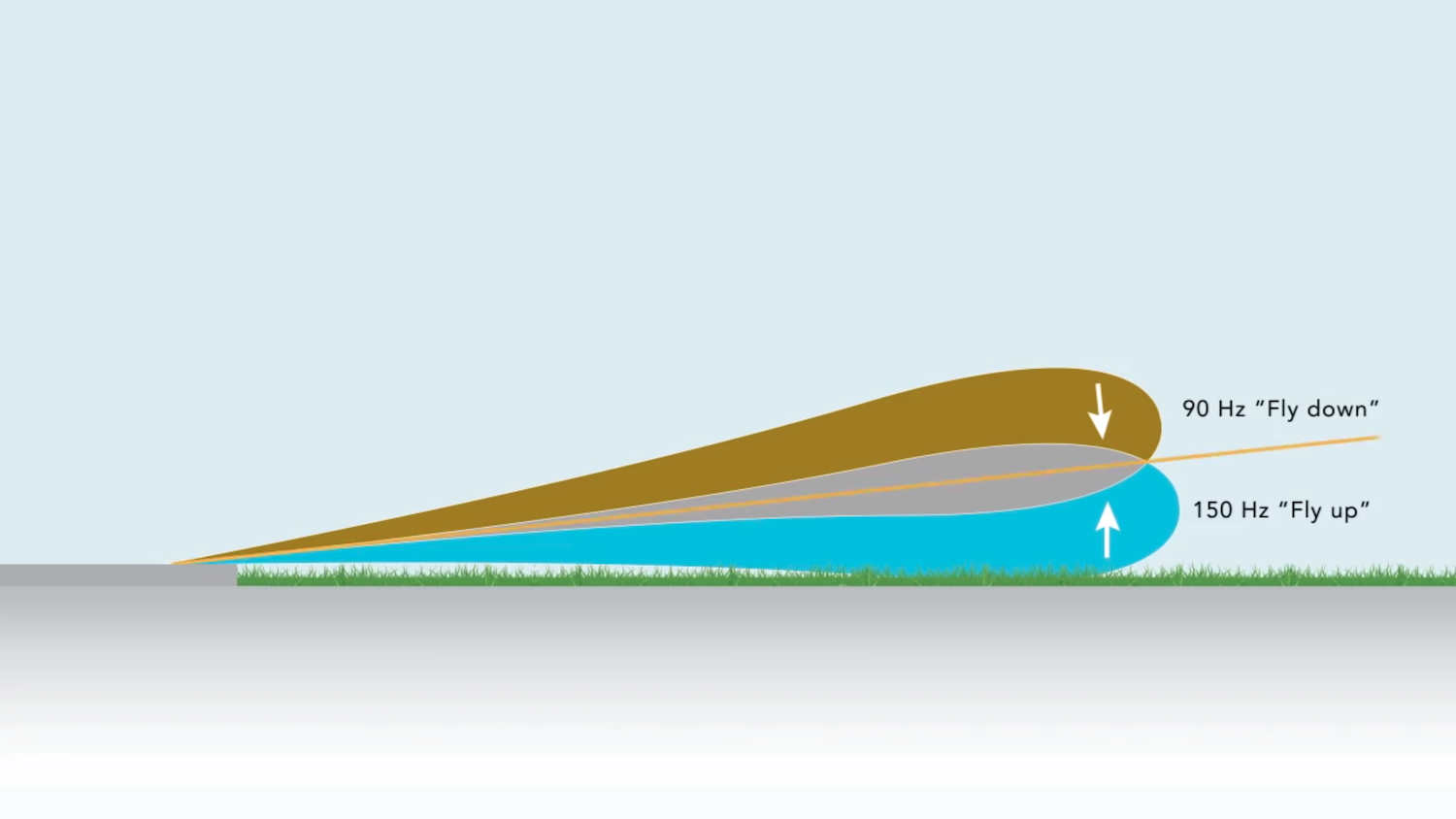
The course landing radio beacon uses two sets of antennas emitting two different in pitch - one at 90 Hz, and the other at 150 Hz - and at a frequency assigned to one of the landing bands. Antenna arrays are located on both sides of the strip, usually after the take-off point, and so that the sounds cancel out when the landing aircraft is located directly above the center line of the strip. The deviation indicator shows a vertical line in the center.
If the plane deviates to the right, the sound at 150 Hz becomes more audible, which is why the deviation indicator pointer moves to the left of the center. If the plane deviates to the left, the sound at 90 Hz becomes more audible, and the pointer moves to the right. The course landing radio beacon, of course, cannot completely replace the visual control of the position of the aircraft, it provides a key and very intuitive means of orientation. Pilots just need to keep the pointer in the center so that the plane is exactly above the center line.

The slope of the glide path works approximately the same, only it shows the angle of descent of the aircraft relative to the beginning of the landing strip. When the angle of the aircraft is too small, the sound at 90 Hz becomes more audible, and the instruments show that the aircraft needs to be lowered. When the descent is too sharp, a signal at 150 Hz indicates that the aircraft needs to be taken higher. When the plane remains at the prescribed glide path angle of about three degrees, the signals cancel each other out. Two glide path antennas are located on the tower at a certain height, determined by the slope angle of the glide path, suitable for a particular airport. The tower is usually located near the touch zone of the strip.
Flawless fake
An attack by researchers from Northeastern University uses commercially available software transmitters. These devices, selling between $ 400- $ 600, transmit signals pretending to be real signals sent by the airport's CSC. An attacker’s transmitter can be located both on board the attacked aircraft and on the ground, at a distance of 5 km from the airport. While the signal of the attackers exceeds the power of the real signal, the CSC receiver will perceive the signal of the attacker, and demonstrate the orientation with respect to the vertical and horizontal flight paths planned by the attacker.

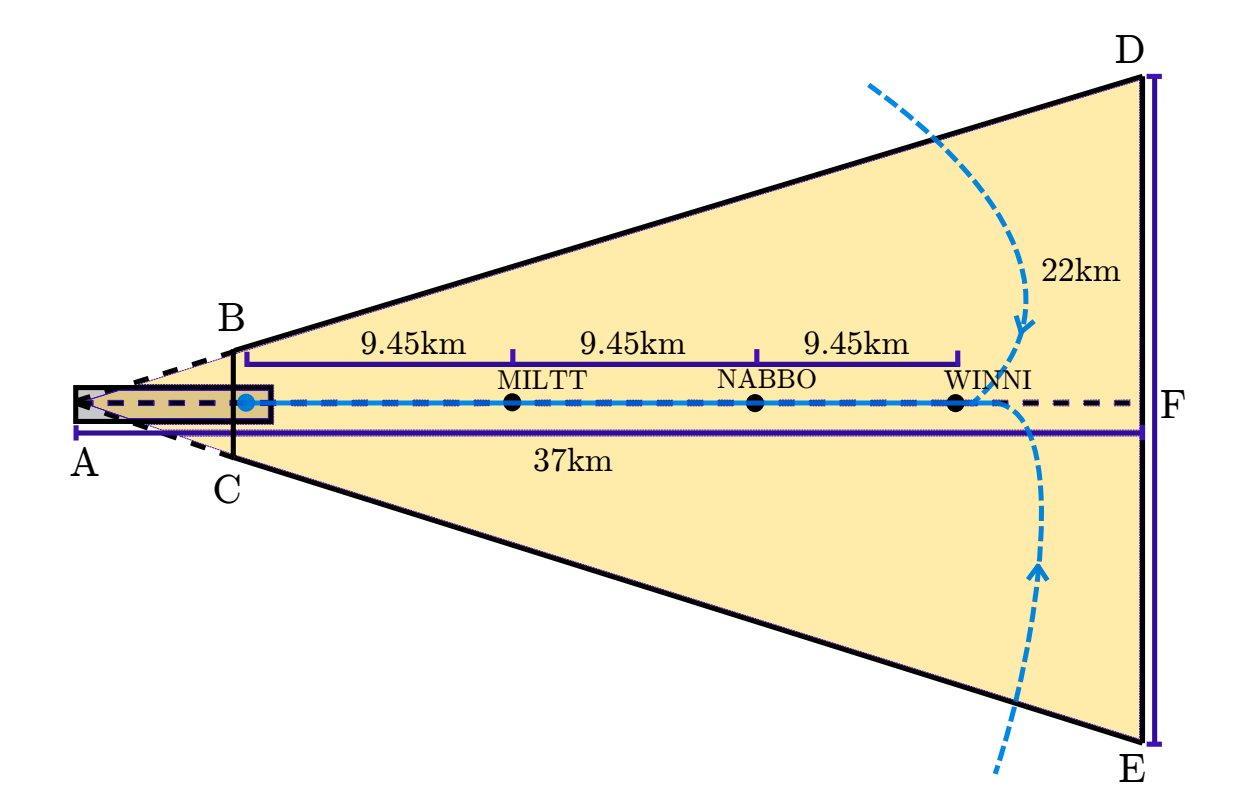
If the substitution is poorly organized, the pilot will see sudden or erratic changes in the readings of the devices, which he will take for a failure of the CSC. To make the fake more difficult to recognize, the attacker can determine the exact location of the aircraft using AZN-V , a system that transmits the aircraft’s GPS location, altitude, ground speed, and other data to ground stations and other ships every second.
Using this information, the attacker can begin to replace the signal when the approaching plane has shifted left or right relative to the landing strip, and send him a signal that the plane is going smoothly. The best time for an attack would be when the plane just passed the waypoint, as shown in the demo video at the beginning of the article.
Then the attacker can apply a real-time signal correction and generation algorithm that will constantly correct the malicious signal to ensure that the offset relative to the correct path will correspond to all movements of the aircraft. Even if the attacker does not have enough skills to make a flawless fake signal, he will be able to confuse the CSC so that the pilot cannot rely on it when landing.
One signal fake option is known as a “shadow attack”. The attacker sends specially prepared signals with a power greater than that of the airport transmitter. For this, an attacker’s transmitter will usually need to send 20 watts of power. Shadowing attacks make it easier to convincingly swap a signal.
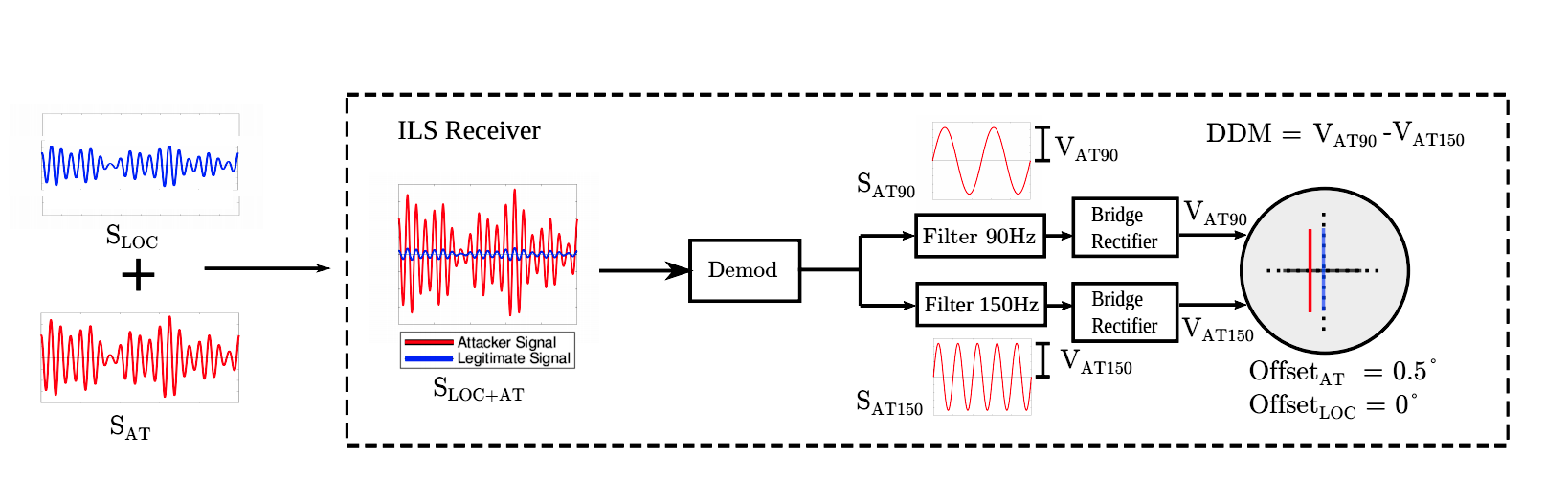
Shadow attack
The second variant of signal substitution is known as a “one-color attack”. Its advantage is that it is possible to send sound of the same frequency with a power less than that of the KGS airport. It has several drawbacks, for example, the attacker needs to know the specifics of the aircraft exactly - for example, the location of its CGS antennas.
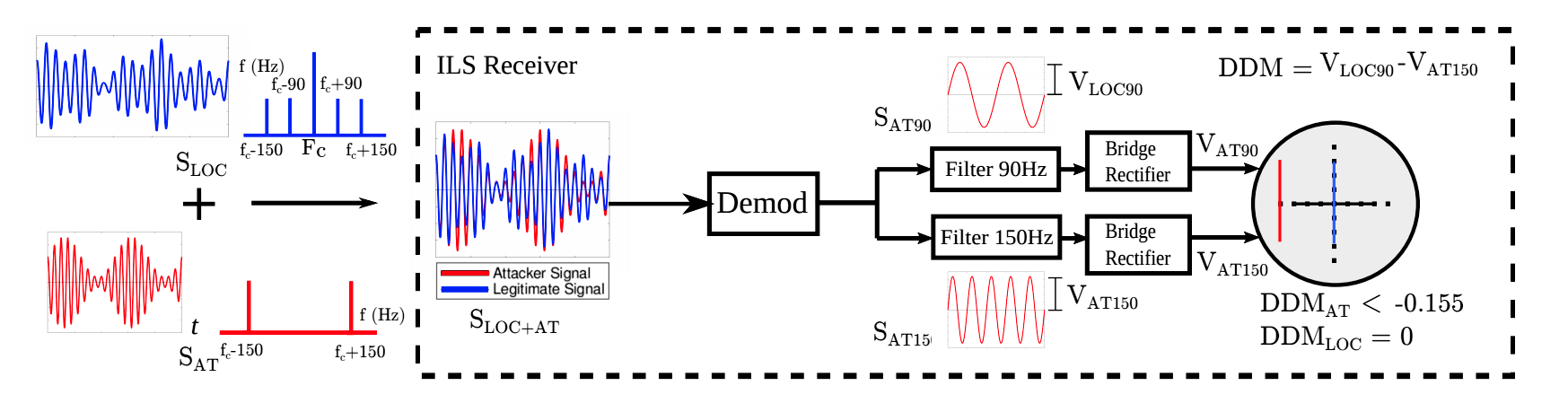
Solid attack
Lack of easy solutions
Researchers say there are no ways to eliminate the threat of spoofing attacks. Alternative navigation technologies - including an omnidirectional azimuthal beacon, a drive beacon, a global positioning system and similar satellite navigation systems - are wireless signals that do not have an authentication mechanism and are therefore susceptible to spoofing attacks. Moreover, information on the horizontal and vertical approach paths can only give CGS and GPS.
In their work, researchers write:
Most security issues faced by technologies such as ADS-B , ACARS and TCAS, can be fixed by implementing cryptography. However, cryptography will not be enough to prevent localized attacks. For example, GPS signal encryption, similar to military navigation technology, can prevent spoofing attacks to a certain extent. Anyway, an attacker will be able to redirect GPS signals with the necessary time delays, and achieve a substitution of location or time. Inspiration can be drawn from existing literature on preventing attacks with GPS spoofing and creating similar systems on the receiver side. An alternative could be the implementation of a large-scale secure localization system based on distance limitation and safe approach confirmation techniques. However, this will require two-way communication, and this option requires further study regarding its scalability,
The U.S. Federal Aviation Administration said they did not have enough information about the demonstration conducted by the researchers to comment.
This attack and the significant amount of research conducted are impressive, but there is no answer to the main question - how likely is it that someone will want to spend effort on realizing such an attack? Other types of vulnerabilities, for example, allowing hackers to remotely install malicious programs on users' computers, or bypass popular encryption systems, are easy to monetize. This is not the case with the substitution attack. Life-threatening attacks on pacemakers and other medical devices fall into the same category.
Although the motivation for such attacks is harder to see, it would be a mistake to discard their possibility. A report published in May by C4ADS, a nonprofit organization covering global conflicts and interstate security, indicates that the Russian Federation has often been involved in large-scale trials of GPS system malfunctions, as a result of which ship navigation systems were wrong in their location for 65 miles or more [ on in fact, the report states that during the opening of the Crimean bridge (that is, not “often”, but only once) the transmitter located on it knocked down the global navigation system m to the bridge, and his work was felt even near Anapa, located 65 km (and not miles) from this place. “And so everything is true” (c) / approx. perev. ].
“The Russian Federation has a relative advantage in using and developing the capabilities of cheating global navigation systems,” the report warns. “However, the low cost, the availability of open sales, and the ease of use of such technologies, gives not only states, but also rebels, terrorists and criminals ample opportunities to destabilize state and non-state networks.”
And although the substitution of CGS seems to be esotericism in 2019, it is unlikely to be so fantastic to assume that in the coming years it will become more familiar, as attack technologies become more understandable, and software-controlled radio transmitters become more common. Attacks on KGS do not have to be carried out in order to cause accidents. They can be carried out to disrupt the operation of airports, since illegal drones led to the closure of Gatwick Airport in London last December, a few days before Christmas, and three weeks later - Heathrow Airport.
“Money is one motivation, and a show of strength is another,” Ranganatan said. - From the point of view of defense, these attacks are very critical. This must be taken care of, because in this world there are enough people who want to demonstrate strength. ”
