Phishing and no chemistry

Because of my work, I often come across various manifestations of network fraud and, of course, phishing resources.
When it comes to phishing sites, the first thing that comes to mind is various schemes designed to steal passwords and other information of interest to cybercriminals. But the vectors for using phishing resources are very diverse. Therefore, the definition of phishing given, say, on Wikipedia, does not fully reveal its essence.
For example, duplicate sites created not to steal data, but to mislead counterparties. Why not phishing? The interest of fraudsters in the creation of such sites has not been falling for 10 years. Here, it is necessary to make a reservation that this is not about sites such as “selling building materials cheaply, money ahead,” but about double sites of real enterprises.
These are:
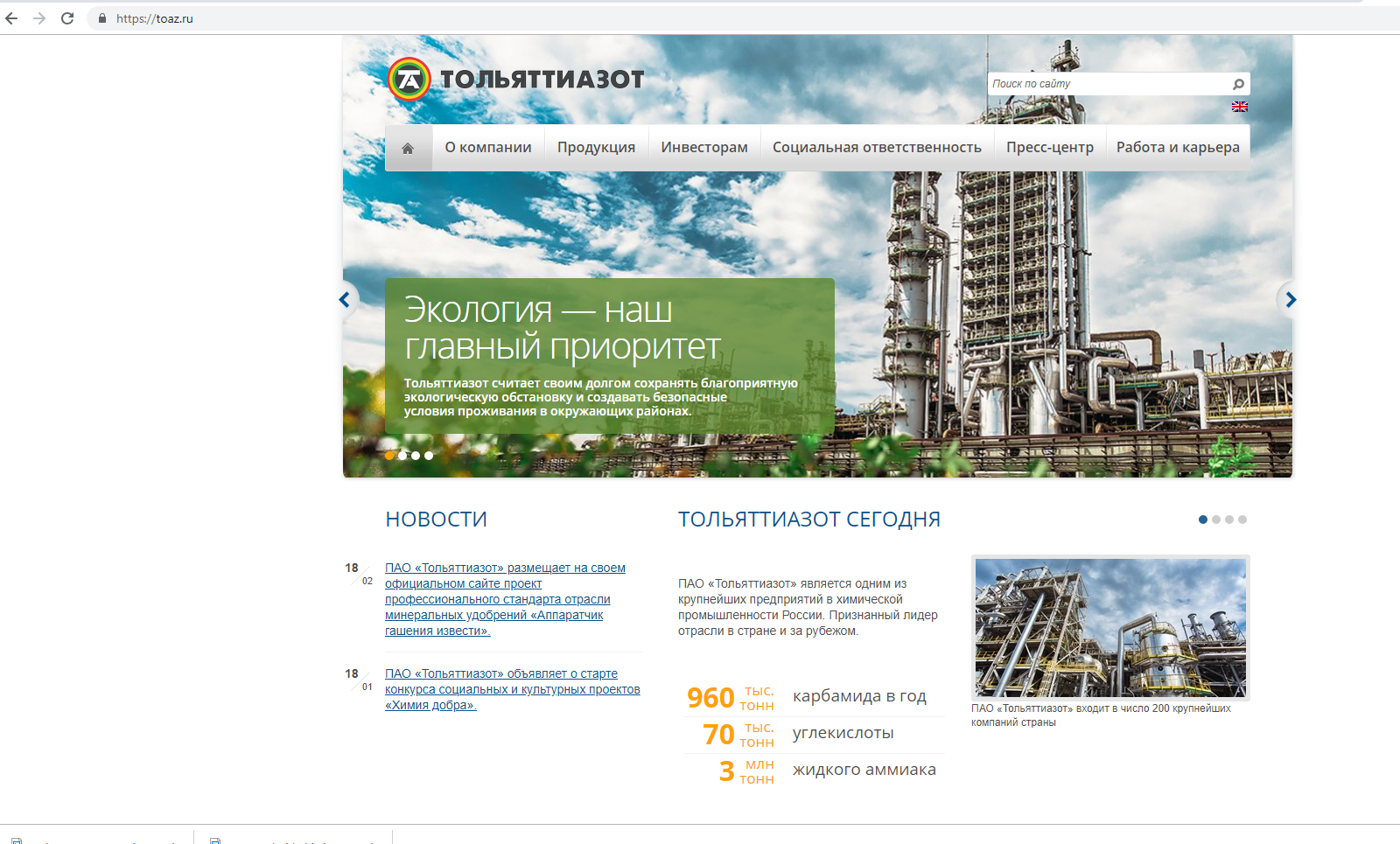
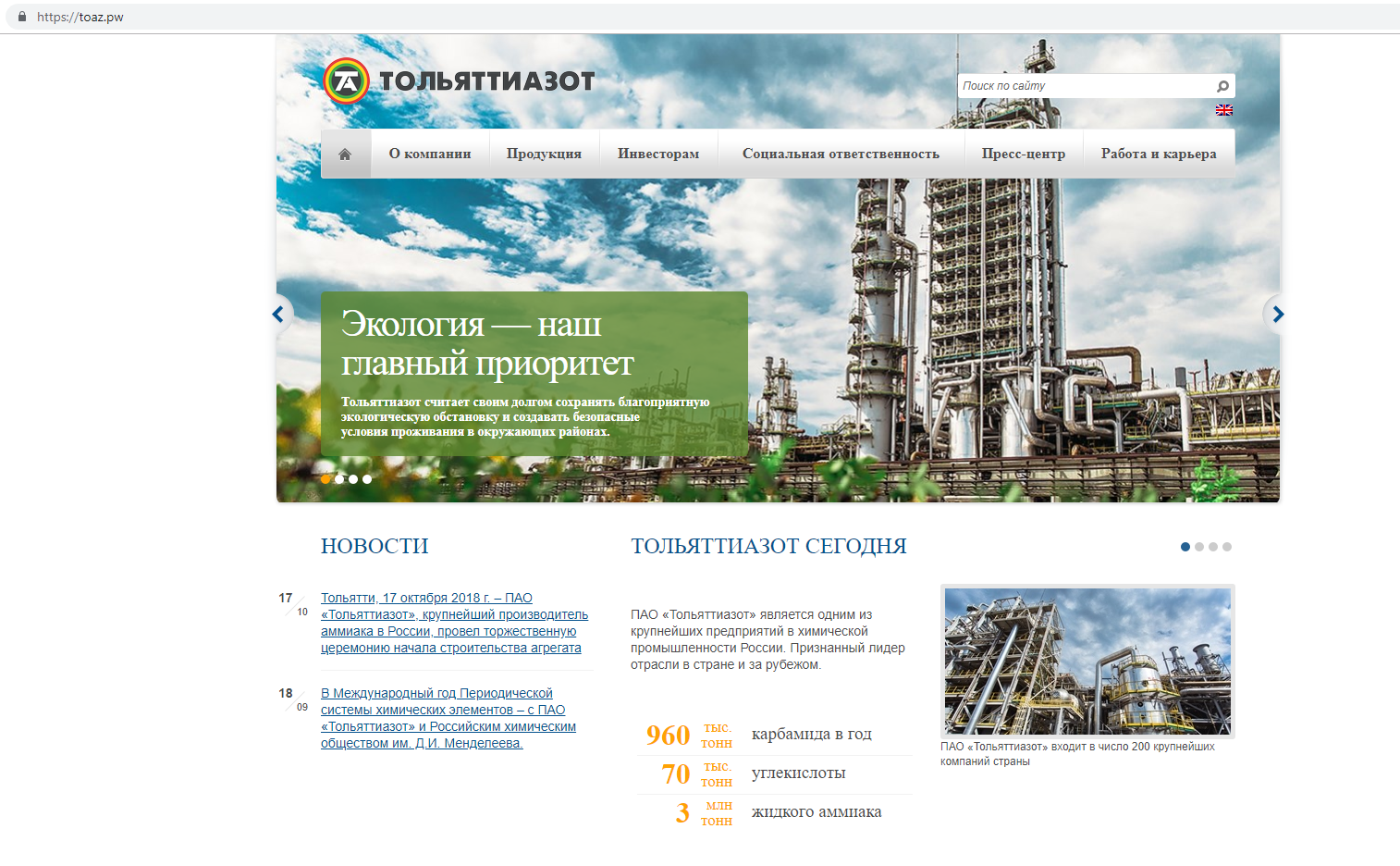
In the first picture, the original site of the chemical enterprise, in the second - its clone. This example was not chosen by chance. Firstly, this clone has already attracted the attention of various researchers, and secondly, it is surprisingly tenacious. The domain name TOAZ.PW was registered in November last year.
Let’s take a closer look at this site and see how this fraudulent scheme works. The first thing that catches your eye is the fonts. Apparently, they were lost somewhere in the process of copying a site with a grabber. But the rest of the resource looks quite authentic except that the news on it has not been updated since October 2018.
All the most interesting begins in the section "Contacts". Phones indicated on the page have no relation to this company. But we will return to phones. They will serve as the main clue.
We look further. Email addresses also differ from those indicated on this resource. Particularly touching in this light is the fraud warning message copied from the company's website. Attackers carefully replaced the “trust line” address with their own, leaving the text virtually unchanged.

The next element is price lists. On the original site they are available in PDF format. In the same format, they migrated to a fake site, while losing real phone numbers and email addresses. It is striking that the scammers did not even bother with the choice of fonts. And so it goes ...

Given that only contact details have undergone changes, we can assume that the double site was created to deceive potential contractors of the enterprise.
In general terms, the cheating scheme looks like this:
- We create a double site of a reputable company
- We send letters to potential clients on behalf of the company
- Attracting even more potential customers
- We receive an advance payment for the supply of products
- ???????
- PROFIT
Money is usually transferred to the accounts of one-day firms, but this is a completely different story, which, however, can be discussed in a separate article.
The fraudulent scheme itself is as old as the world, but still remains quite effective. With one caveat. One double site is not enough. The life span of phishing resources is short-lived (TOAZ.PW has been hanging on the network for six months now - an exception to the rule), which means that fraudsters need to constantly create new sites.
And they are fast. The analysis of Whois data, e-mail addresses and phone numbers allows you to get two more doubles of the desired site without thinking: toaoz.ru and toaoz.com. One of them is already dead (but the web archive remembers everything), while the second seems to have fallen off CSS.
Interestingly, despite the mail addresses of the format ***@toaz.pw, the attackers actually use the Mail.Ru and Yandex mail servers. It is more comfortable.
Digging further. No less interesting resources hang on the same IP with toaoz.com:
- uralechem.com
- min-udo.org
- agrocenter-eurochem.info
The last two at the time of writing are no longer available, but the first - a clone of the Uralchem website is still alive.
A further search allows you to get a dozen more domain names used to create clone sites for chemical industry enterprises.
It would take too long to paint the entire search process, so here is a simplified diagram of the relationships between phishing resources. The diagram does not indicate all resources, in addition, it contains intentionally hidden personal data, as well as phone numbers and names of some sites that are not directly related to the criminal scheme. Some of the illuminated phones pop up in search engines in conjunction with various services for anonymous receipt of SMS confirmations.
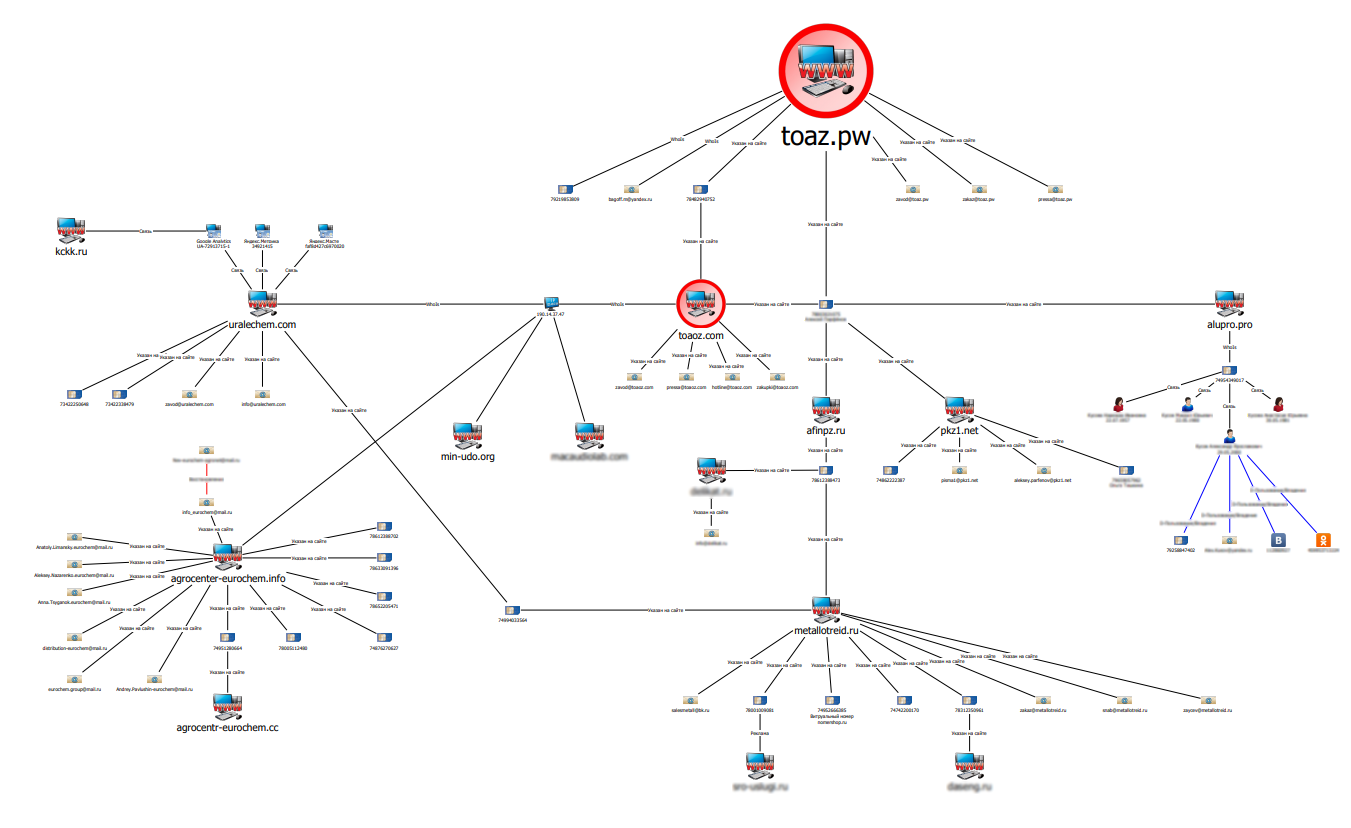
A quick analysis of the resources suggests that this scheme is rooted in fraudsters who created clones of the sites of the Eurochem concern several years ago.
On the network you can find reviews of entrepreneurs who have become victims of such sites. Many of them are quite determined, intending to defend their truth and their money in court. But it’s just that they hardly realize that they will have to sue not with an unscrupulous supplier, but with a one-day company, whose assets tend to zero. In the registers of legal entities one can find many such “LLCs” in respect of which enforcement proceedings are open.
But there’s definitely nothing to take from them. Money has long moved into the pocket of the organizers of this business.
Fraudsters are not limited to Russia. Many phishing sites have English versions, and they actively discuss “scam from Russia” in foreign forums.
Some resources even make lists of organizations that are not worth dealing with. Among them there are especially many companies in the oil and gas industry, which is understandable - the direction is very monetary. In these lists you can also find the addresses of sites that have become the heroes of our today's selection .
The reasons for the popularity of this scheme are many. Unlike fraudsters, profiting from individuals, deceit is legal. individuals have far greater benefits, allowing attackers to receive millions of rubles for several transactions.
In addition, such a fraud is not revealed immediately. Disruption of supply is not such a rare occurrence in business, so scammers try to stretch their time as long as possible, coming up with various explanations for delays. They use this time to cover their tracks and withdraw funds. When the victim finally realizes that she was deceived, the time to investigate the crime “in hot pursuit” is hopelessly lost.
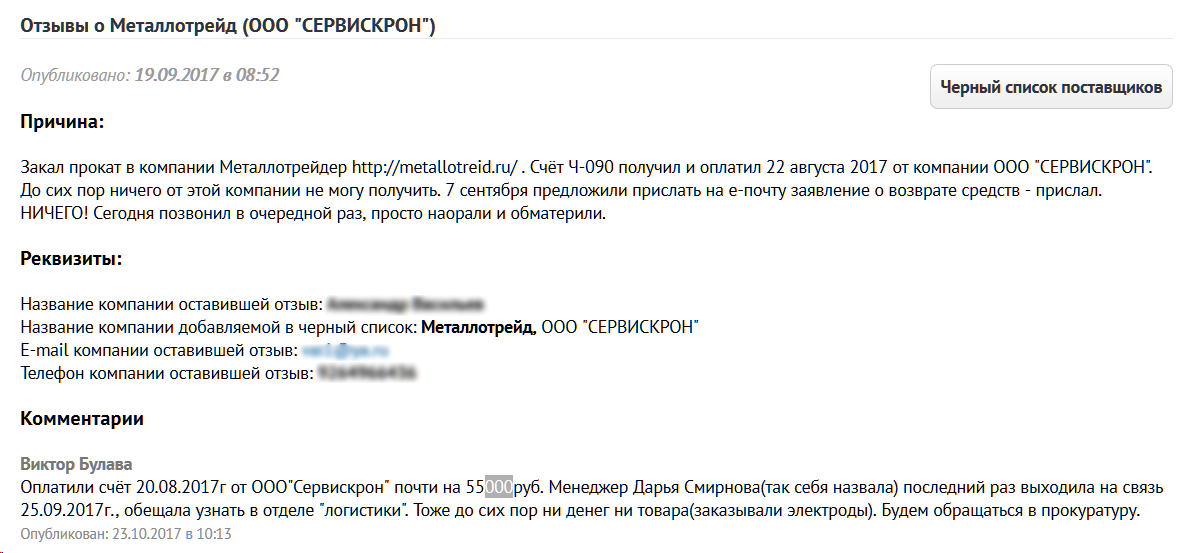
There is another reason for the success of this criminal business. By creating clones of the sites of large enterprises, scammers do not cause them direct damage. To some extent, only their reputation suffers, and even then very indirectly.
Therefore, industrial giants are extremely reluctant to deal with such phishing resources. Third parties are even more difficult to deal with. After all, if a company whose website was copied by cybercriminals can use various legal levers of influence, for example, to demand the cessation of misuse of the brand, then the victims of phishing have no choice but to prove that the site is owned by scammers and used for illegal purposes. And here they are faced with a number of difficulties, because the fact of fraud, or rather intent, still needs to be proved. And any lawyer knows that fraud is one of the most difficult crimes in terms of collecting evidence, especially when it comes to relations between legal entities.
What is left to do? Clients - take a more careful approach to checking counterparties and not transfer money to the account of the next LLC “Vector”. And industrial companies do not ignore the problem, but monitor the appearance of clones of their resources and timely take the necessary measures. Moreover, all the necessary tools for this are available nowadays. The only question is the organization’s desire to take care of the safety of its potential customers.
