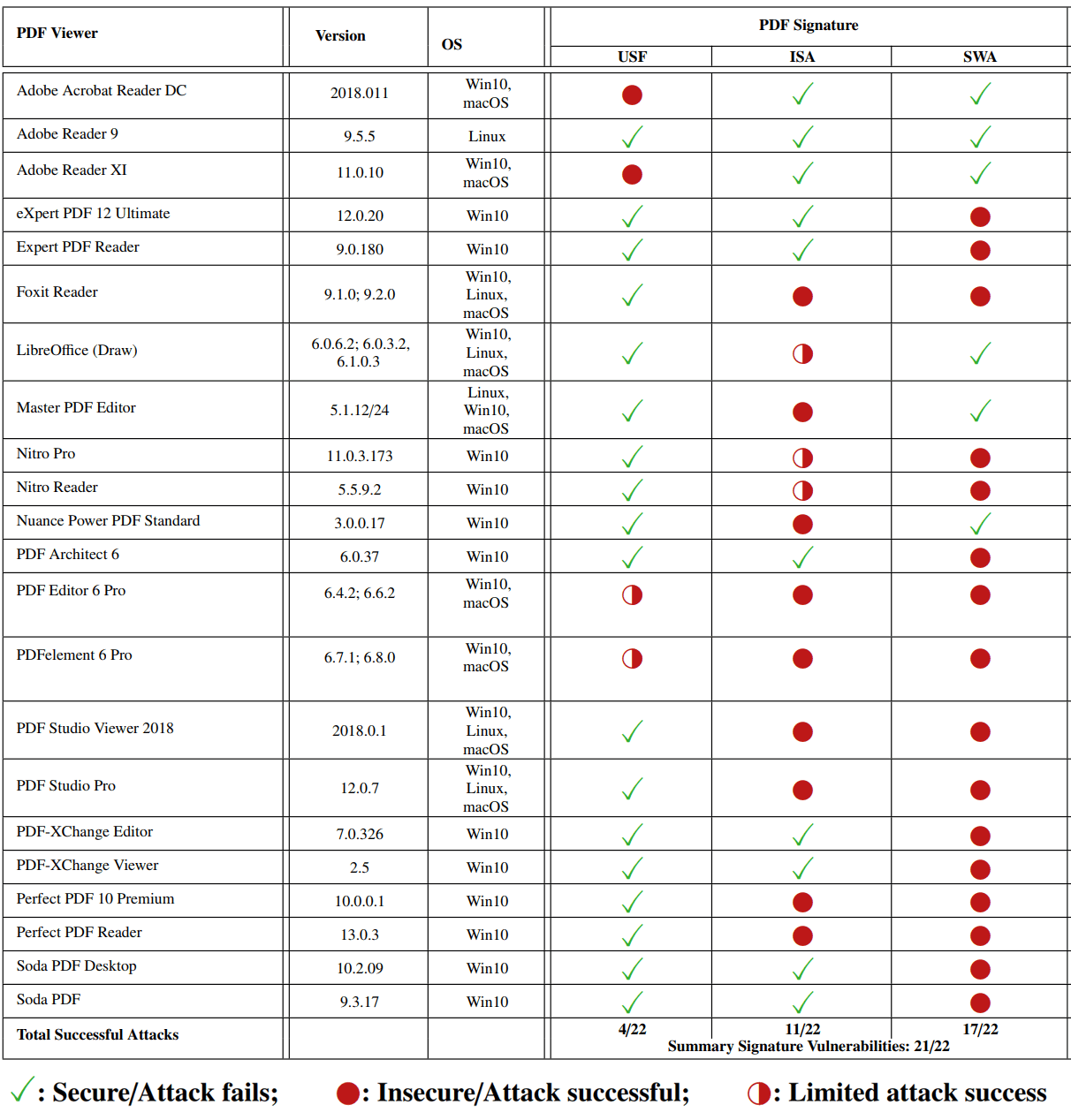
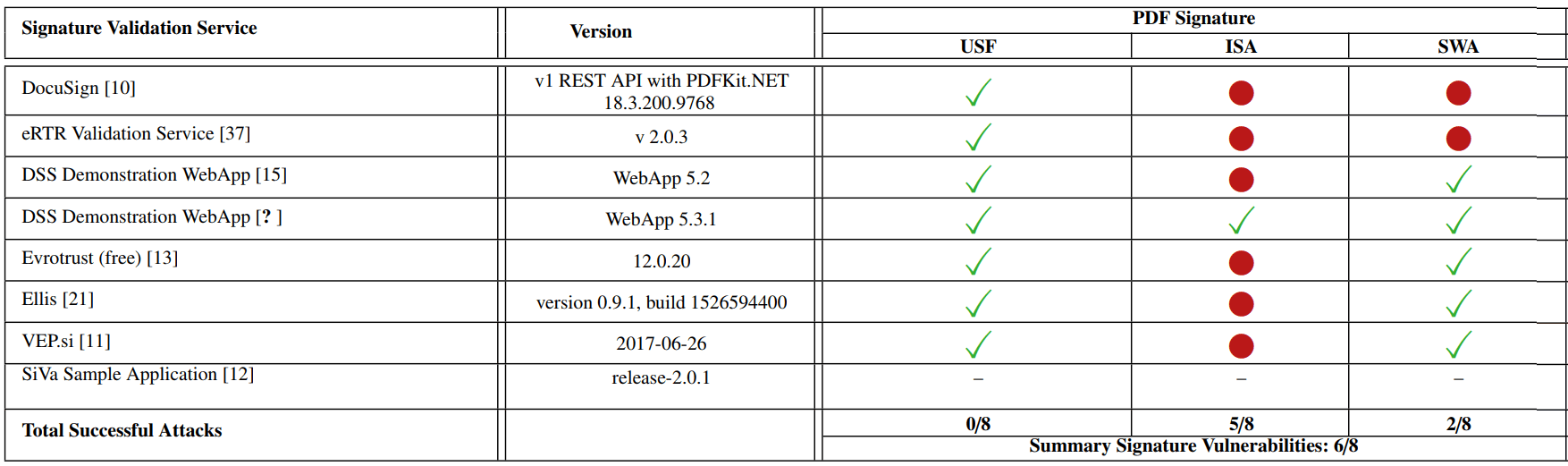
Several ways to fake PDF with digital signature
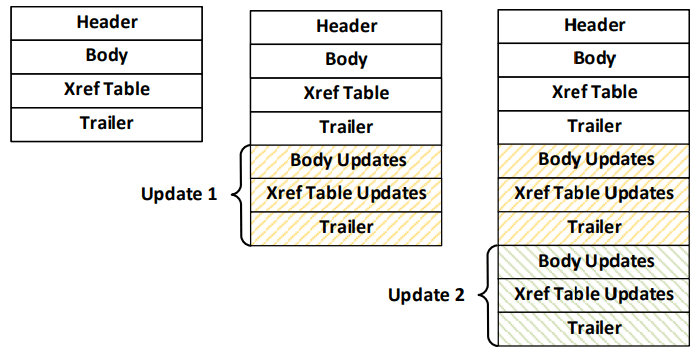
Fig. 1. The incremental save procedure on which PDF digital signatures are based. According to the test results, this is the most effective way to fake documents.
Theoretically, PDF digital signatures reliably authenticate the author of a document. But in practice, PDF processing is usually carried out by proprietary software that does not perform validation correctly. Specialists from the Ruhr University in Bochum (Germany) described several options for falsifying digitally signed PDF documents that work in most PDF viewers and online verification services.
Protection against all attacks is provided only in a single program, and even it works under Linux.
PDF structure
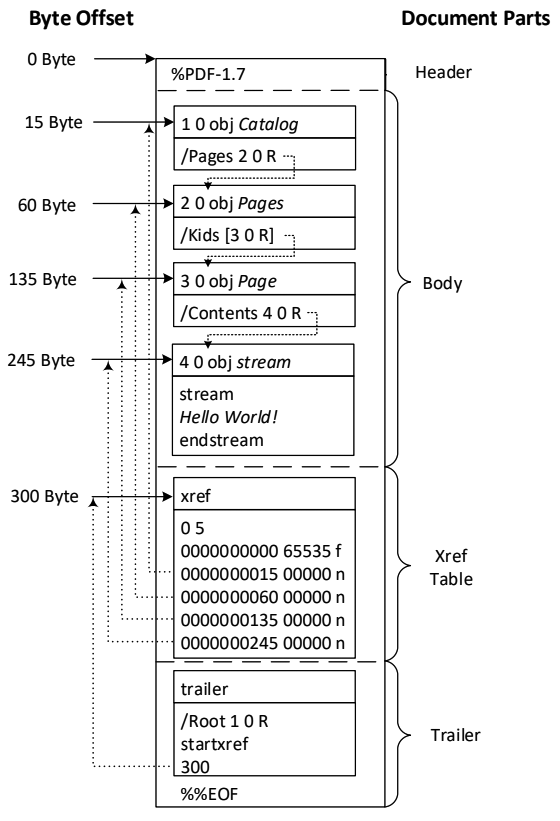
Fig. 2. The structure of the PDF document The structure of the PDF
document is shown in Fig. 2. When incrementally saving changes to the PDF document, new objects are added to the body , as well as a new Xref table with a description of new objects and a new trailer with links to catalog (see Fig. 1). A directory is the root object of a PDF file; it defines the structure of the document and can optionally determine access permissions.
Each object starts with the object number and version number, which increases with each update of the object.
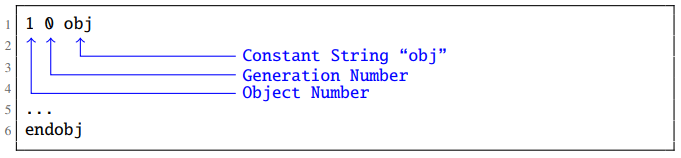
Fig. 2. Structure of the PDF object
Signature Creation
Adding a digital signature to a PDF document relies on an incremental save mechanism (see Figure 1). When adding a signature during incremental saving, the following content is added to the document:
- new Catalog with a new Perms parameter that defines permissions to modify the document; this parameter refers to the Signature object ;
- a Signature (
5 0 obj) object with information about the cryptographic algorithms used to hash and sign the document, with a parameterContentsthat contains the PKCS7 hex-encoded blob - it stores certificates and the value of the signature created using the private key that corresponds to the public key in the certificate. The parameterByteRangedetermines which bytes of the PDF file are used at the input of the hash function to calculate the signature (paira, bandc, d), that is, what part of the file is signed; - A new Xref table with a link to a new object
- new trailer .
In fig. Figure 3 shows a simplified diagram of a digitally signed PDF file.
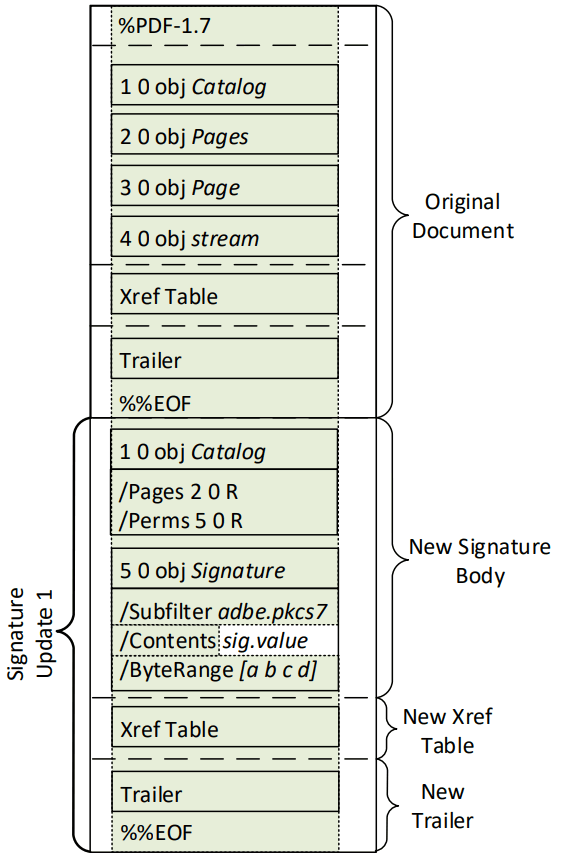
Fig. 3. Simplified layout of a digitally signed PDF file.
According to current specifications, it is recommended that you sign the entire file, except for PKCS7 blob.
Signature verification is carried out by the application in which the PDF document is opened. It immediately extracts the signature from the PDF and uses cryptographic operations to verify its correctness, and then check whether the X.509 certificate, whose keys were used to sign, can be trusted.
Typically, all PDF readers do not trust the keystore built into the operating system. Like the Firefox browser, they distribute their own keystore and usually allow the user to specify a store with trusted certificates. This function allows you to trust only certain certificates, for example, from your own certification authority.
Digital Signature Counterfeiting
Researchers describe three ways to counterfeit content in signed PDFs.
- Universal Signature Forgery (USF);
- Incremental Saving Attack (ISA) attack
- attack on a signature wrapper (Signature Wrapping Attack, SWA).
Universal Signature Fake (USF)
A USF attack disables signature verification in an application that opens a PDF. At the same time, a normal message is sent to the user about the successful validation of the signature. This is done by manipulating the Signature object in the document: either an incorrect record is created inside this document, or the link to the object is deleted from the file. Although the PDF viewer cannot verify the signature is correct, in some cases the program still shows its presence, which meets the goals of the attacker.
Researchers formulated 18 USF attack vectors, eight of which are shown in Fig. 4.
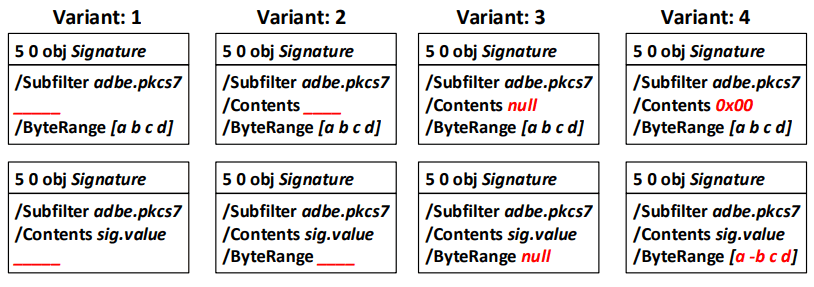
Fig. 4. Eight attack vectors to circumvent digital signature verification.
All these methods work if the PDF viewer does not correctly verify the digital signature.
Incremental Retention Attack (ISA)
This class of attacks consists in redefining the structure and content in an additional section of a document. The idea is that the signature is calculated based on the range of bytes specified in
ByteRange, and the extra section does not fall into this range, as shown in Fig. 5.
Fig. 5. When adding content to the additional section, the digital signature
is not violated. There are several ways to bypass the check for changing a document and block showing the corresponding warning in the PDF document viewer.
Signature Wrapper Attack (SWA)
Finally, the last class of attacks allows you to bypass signature verification without incremental saving, but by moving the signed part of the PDF to the end of the document and reusing the pointer
xrefin the signed Trailer to the modified Xref table. At the same time, to avoid processing the moved part, it can be wrapped in some extraneous object, for example, stream or dictionary .
Fig. 6. Comparison of original and modified PDF documents
Attack Performance
Researchers tested the effectiveness of each type of attack in different programs for viewing PDF. Unable to fool only Adobe Reader 9 under Linux . In all other programs, signature verification is bypassed in one or more ways. The situation with the online PDF digital signature verification services is no better.