Work with cryptographic information protection and hardware key carriers in Linux
- Tutorial

Storing keys on tokens and smart cards provides additional protection against external and internal intruders, including those having a certain level of access to the information system and equipment.
Today I will tell you how we protect encryption keys and electronic signatures in our information systems, and I will do this in a detailed, well-illustrated guide to setting up SUSE Linux Enterprise Server 12 SP3 for working with the Aladdin JaCarta PKI token and CryptoPro CSP KC2 4.0.9944.
There were several reasons for publishing this guide:
Reason 1
The official documentation on Aladdin-RD JaCarta is more adapted for Astra Linux and ALT Linux operating systems, certified by the Ministry of Defense, FSTEC and the FSB as a means of protecting information.
Reason 2
The best instruction on setting up interaction with hardware media in Linux, which was found, was also from wiki.astralinux.ru - Working with CryptoPro CSP
Reason 3
UPD 04/16/2019: In the process of setting up the environment and equipment, it turned out that the carrier that was first available was not JaCarta PKI Nano at all, as expected, but a device operating in SafeNet Authentication Client eToken PRO mode.
UPD 04/16/2019: Once the Bank needed a device that could work in the same infrastructure as eToken PRO (Java). As such a device, the company “ZAO Aladdin RD” offered the JaCarta PRO token, which was selected by the bank. However, at the stage of forming the article and shipping documents, an employee of the company made a mistake. Instead of the JaCarta PRO model, JaCarta PKI was accidentally entered into the article and shipping documents.
UPD 04/16/2019: I thank the company Aladdin R.D. for helping to figure out and establish the truth.
There is no political and hidden meanings in this error, but only an employee’s technical mistake in preparing documents. Token JaCarta PRO is a product of the company Aladdin R.D. The applet performing the functional part was developed by the company “ZAO Aladdin R.D.”
This eToken PRO was for a party released before December 1, 2017.
After this date, Aladdin RD stopped selling eToken PRO (Java) devices.
Running a little ahead, I must say that work with him was configured through the appropriate drivers - SafenetAuthenticationClient-10.0.32-0.x86_64 , which can only be obtained in support of Aladdin R.D. on a separate online application.
In CryptoPro CSP, to work with this token, it was required to install the cprocsp-rdr-emv-64 package | EMV / Gemalto support module .
This token was determined and responded. Using SACTools Utilityfrom the SafenetAuthenticationClient package, you could initialize it. But when working with cryptographic information protection, he behaved extremely strange and unpredictable.
It was shown as follows, on the command:
csptest -keyset -cont '\\.\Aladdin R.D. JaCarta [SCR Interface] (205D325E5842) 00 00\alfa_shark' -check The answer was that everything was fine:
[ErrorCode: 0x00000000]But immediately after trying to read the keys programmatically, the same check began to produce an error:
[ErrorCode: 0x8009001a]According to the list of error codes of the object model of components of Microsoft COM Error Codes (Security and Setup)
NTE_KEYSET_ENTRY_BAD
0x8009001A
Keyset as registered is invalid.“Invalid key set” - the reason for such a message may lie either in the old Gemalto chip, firmware and applet, or in their drivers for the OS that do not support the new ES generation standards and hash functions GOST R 34.10-2012 and GOST R 34.11- 2012.
In this state, the token was blocked. The cryptographic information protection index began to show the irrelevant state of the reader and the key container. Restarting the cprocspractor provider cprocsp service, pcscd token and smart card services and the entire operating system did not help, only reinitialization.
In fairness, it should be noted that SafeNet eToken PRO worked correctly with the GOST R 34.10-2001 keys in Windows 7 and 10.
You could try installingCryptoPro CSP 4.0 CSP 4.0 FCN (Gemalto) , but the goal is to protect our ES and encryption keys with JaCarta family certified FSB and FSTEC products, which support new standards.
The problem was solved by taking the real JaCarta PKI token in the (XL) regular casing.
But a lot of time was spent trying to get Safenet eToken PRO to work. I wanted to draw attention to this and, perhaps, protect someone from this.
Reason 4
Sometimes you yourself need to return to old articles and instructions. This is convenient when the information is placed in an external source. So thanks to Habr for the opportunity.
Setup guide
After installing the JaCarta PKI token in the USB port of the server and starting the system, we verify that the new device is detected and appears in the list:
lsusb
In our case, it is Bus 004 Device 003: ID 24dc: 0101
For diagnostics of readers, you can use the pcsc-tools utility from the security: chipcard project (software.opensuse.org) .
It is launched by the command:
pcsc_scan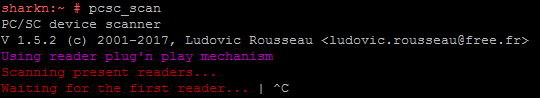
Until all the necessary packages are installed, information about the token will not be displayed.
Installing drivers and software for working with JaCarta PKI
On the Support page of the Aladdin RD website, we download Documentation and software for working only with JaCarta PKI
According to the JaCarta for Linux Implementation Guide, clause 4.2., The first step is to install pcsc-lite , ccid and libusb packages .
For the JaCarta management utility to work, the following components must be installed:We check the availability of these packages and install:
- PC / SC Lite - an intermediate layer for providing access to smart cards according to the PC / SC standard, pcsc-lite package.
- Ccid and libusb libraries for working with USB keys, smart cards and smart card readers.
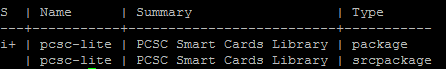
zypper search pcsc-lite
zypper search libusb
zypper install pcsc-lite
zypper search CCID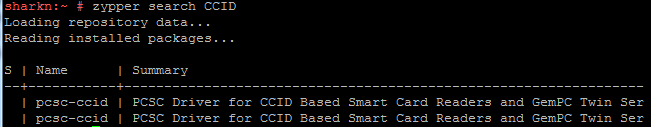
zypper install pcsc-ccid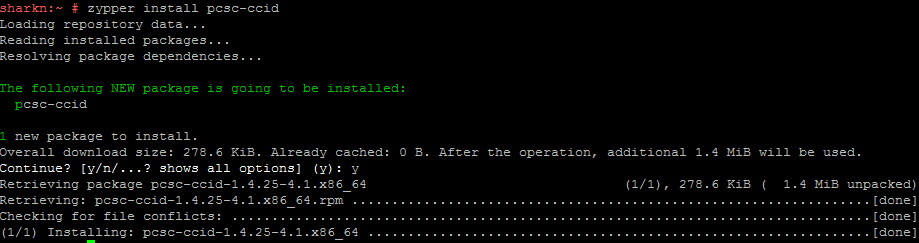
zypper search CCID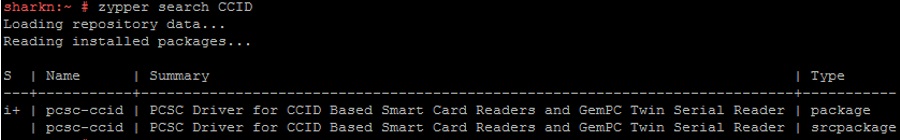
zypper install libusb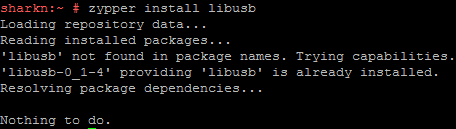
As a result, the pcsc-lite package was updated, CCID was installed, libusb did not require any action.
Using the following two commands, we install the package with drivers and software directly for working with JaCarta PKI: We
zypper install idprotectclientlib-637.03-0.x86_64.rpm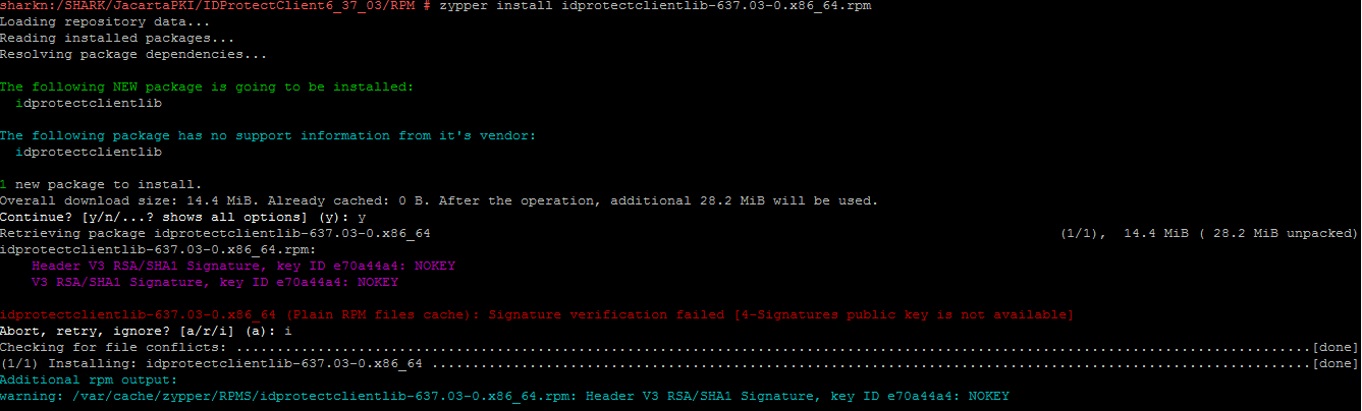
zypper install idprotectclient-637.03-0.x86_64.rpm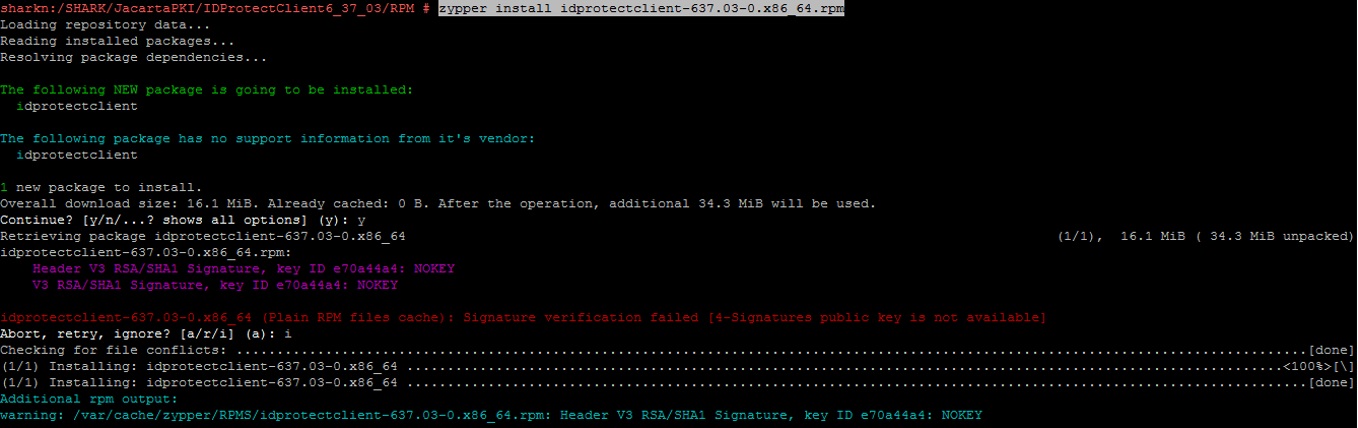
check that the drivers and software for JaCarta PKI are installed:
zypper search idprotectclient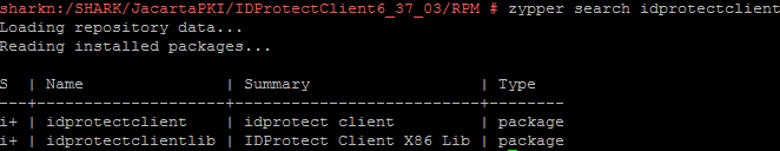
When I tried to get SafeNet eToken PRO to work, I found information that the openct package is preinstalled in SLES - Library for Smart Card Readers may conflict with pcsc-lite - PCSC Smart Cards Library , the installation of which is required by Aladdin R.D.
zypper search openct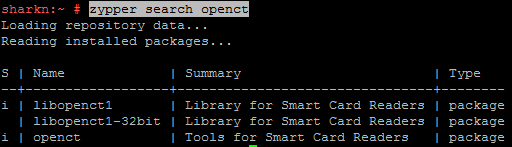
Therefore, we remove the openct package:
rpm -e openctNow all the necessary drivers and software for working with the token are installed.
We perform diagnostics using the pcsc-tools utility and make sure that JaCarta is detected in the operating system:
pcsc_scan
Installing CryptoPro CSP packages
When installing CryptoPro CSP by default, the necessary packages for working with tokens and smart cards are missing.
zypper search cprocsp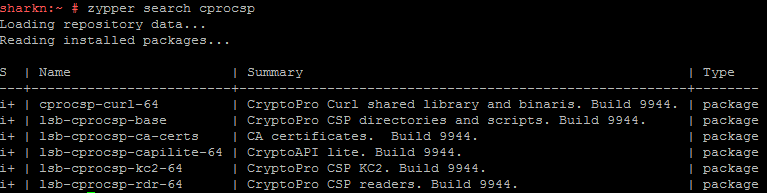
We install the JaCarta components for CryptoPro CSP support component in the CSP.
zypper install cprocsp-rdr-jacarta-64-3.6.408.683-4.x86_64.rpm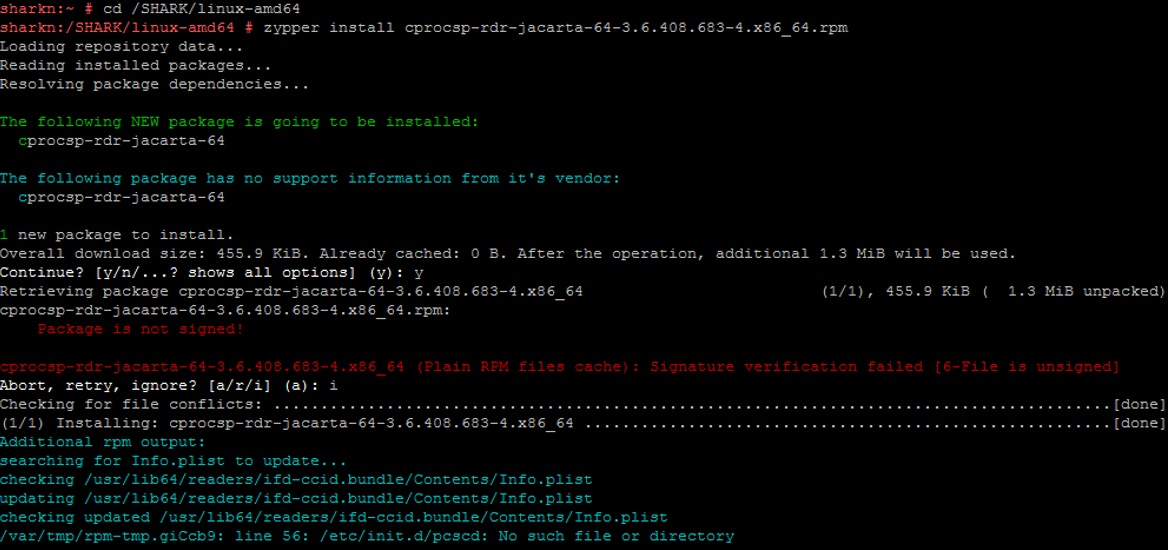
Some components have dependencies. So, for example, if you try to install the SafeNet eToken PRO support package cprocsp-rdr-emv-64-4.0.9944-5.x86_64.rpm - EMV / Gemalto support module , we will get a message about the need to first install the base component of the CSP reader support cprocsp -rdr-pcsc-64-4.0.9944-5.x86_64.rpm - PC / SC components for CryptoPro CSP readers :
zypper install cprocsp-rdr-emv-64-4.0.9944-5.x86_64.rpm
Loading repository data...
Reading installed packages...
Resolving package dependencies...
Problem: nothing provides cprocsp-rdr-pcsc-64 >= 4.0 needed by cprocsp-rdr-emv-64-4.0.9944-5.x86_64
Solution 1: do not install cprocsp-rdr-emv-64-4.0.9944-5.x86_64
Solution 2: break cprocsp-rdr-emv-64-4.0.9944-5.x86_64 by ignoring some of its dependencies
Choose from above solutions by number or cancel [1/2/c] (c): c
Install the basic support packages for readers and key media:
zypper install cprocsp-rdr-pcsc-64-4.0.9944-5.x86_64.rpm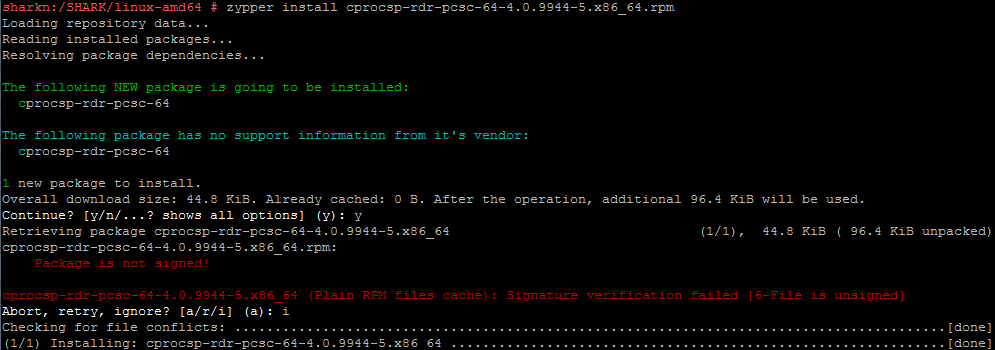
zypper install lsb-cprocsp-pkcs11-64-4.0.9944-5.x86_64.rpmNow you can install modules for working with other types of media and GUI components:
zypper install cprocsp-rdr-emv-64-4.0.9944-5.x86_64.rpm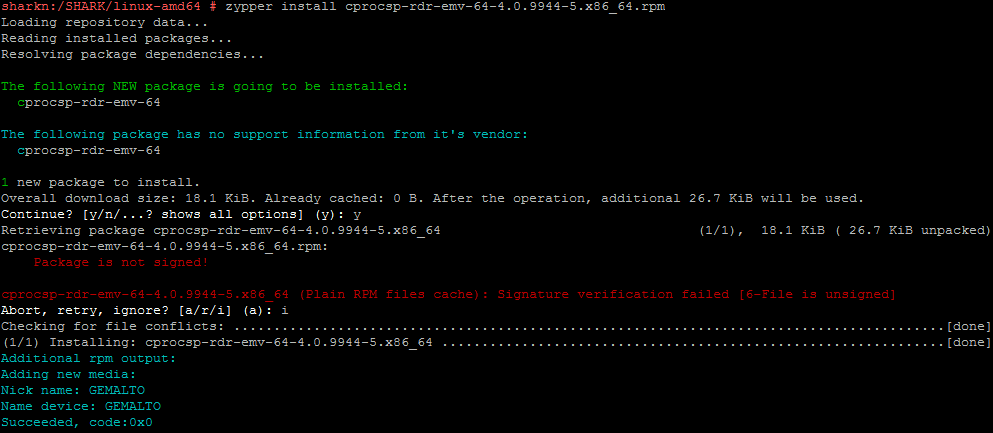
zypper install cprocsp-rdr-novacard-64-4.0.9944-5.x86_64.rpm
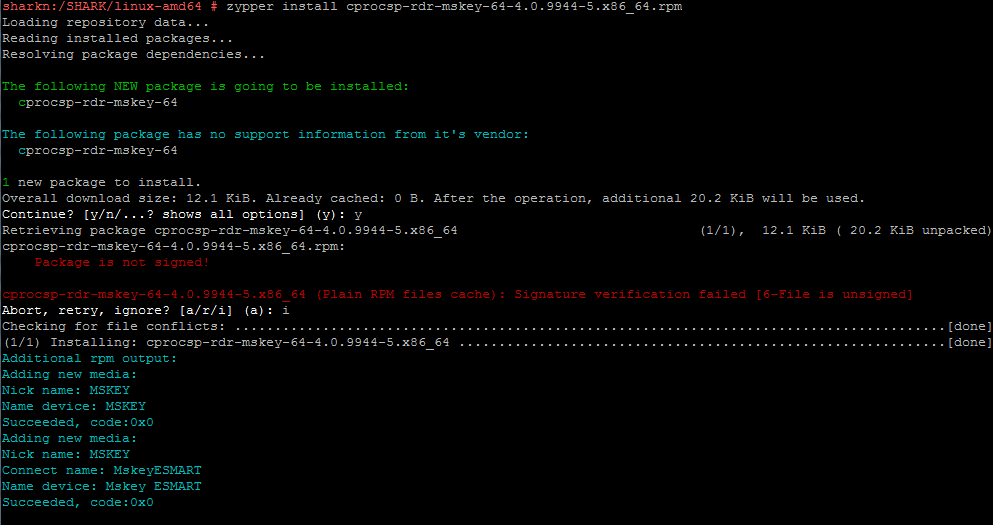
zypper install cprocsp-rdr-mskey-64-4.0.9944-5.x86_64.rpm
zypper install cprocsp-rdr-gui-gtk-64-4.0.9944-5.x86_64.rpm
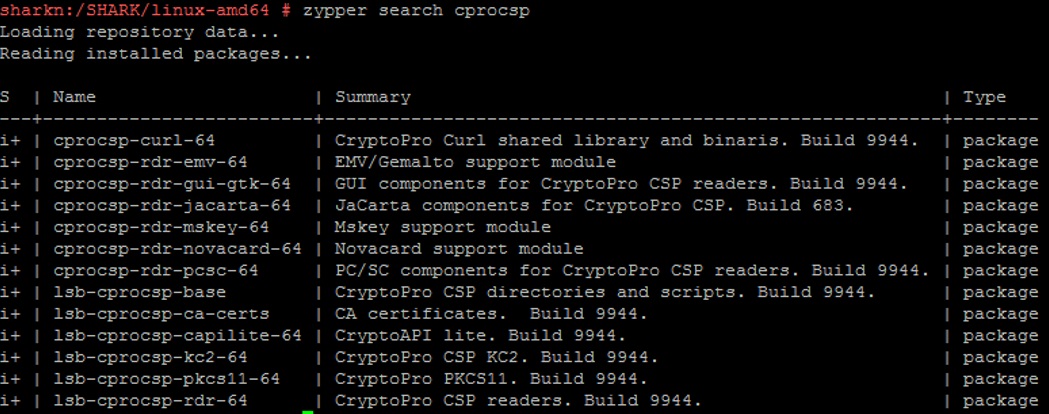
Check the final configuration of CryptoPro CSP:
zypper search cprocsp
Loading repository data...
Reading installed packages...
S | Name | Summary | Type
---+-----------------------------+----------------------------------------------------+--------
i+ | cprocsp-curl-64 | CryptoPro Curl shared library and binaris. Build 9944. | package
i+ | cprocsp-rdr-emv-64 | EMV/Gemalto support module | package
i+ | cprocsp-rdr-gui-gtk-64 | GUI components for CryptoPro CSP readers. Build 9944. | package
i+ | cprocsp-rdr-jacarta-64 | JaCarta components for CryptoPro CSP. Build 683. | package
i+ | cprocsp-rdr-mskey-64 | Mskey support module | package
i+ | cprocsp-rdr-novacard-64 | Novacard support module | package
i+ | cprocsp-rdr-pcsc-64 | PC/SC components for CryptoPro CSP readers. Build 9944.| package
i+ | lsb-cprocsp-base | CryptoPro CSP directories and scripts. Build 9944. | package
i+ | lsb-cprocsp-ca-certs | CA certificates. Build 9944. | package
i+ | lsb-cprocsp-capilite-64 | CryptoAPI lite. Build 9944. | package
i+ | lsb-cprocsp-kc2-64 | CryptoPro CSP KC2. Build 9944. | package
i+ | lsb-cprocsp-pkcs11-64 | CryptoPro PKCS11. Build 9944. | package
i+ | lsb-cprocsp-rdr-64 | CryptoPro CSP readers. Build 9944. | package
To apply the changes, we restart the cryptographic provider service and check its status:
/etc/init.d/cprocsp restart
/etc/init.d/cprocsp status
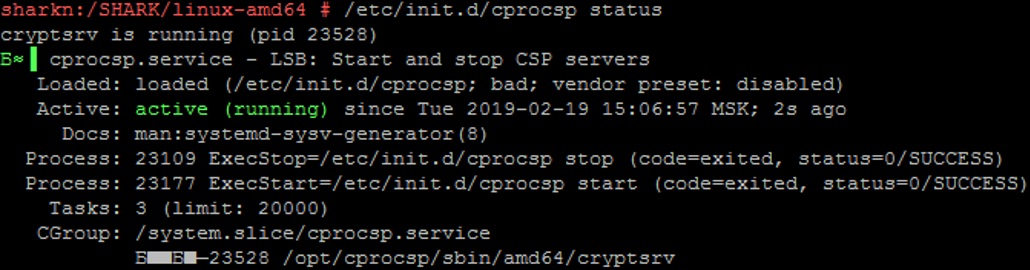
CryptoPro CSP setup and diagnostics
Check if the cryptographic provider sees our token and other available media types with the following commands:
/opt/cprocsp/bin/amd64/csptest -card -enum -v –v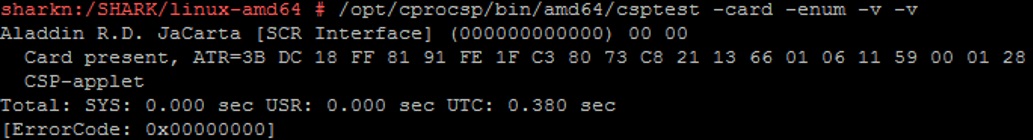
/opt/cprocsp/bin/amd64/csptest -enum -info -type PP_ENUMREADERS | iconv -f cp1251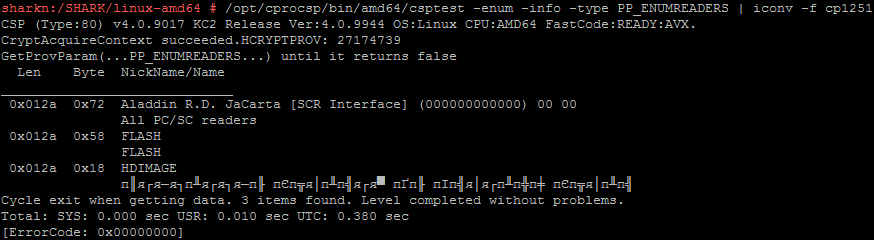
/opt/cprocsp/sbin/amd64/cpconfig -hardware reader -view -f cp1251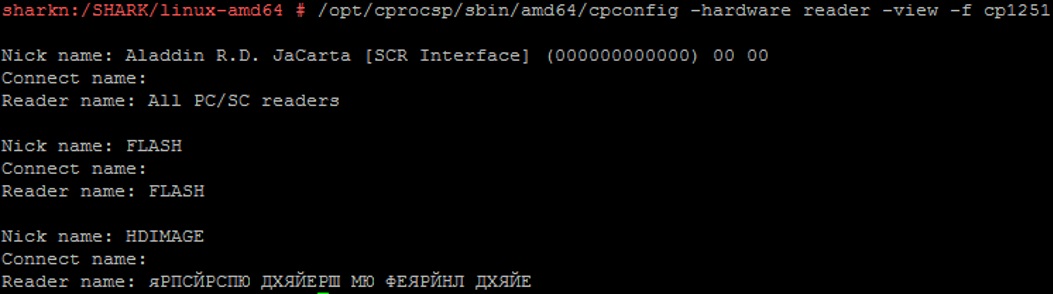
Aladdin RD JaCarta [SCR Interface] (000000000000) 00 00 is our medium.
Following the instructions of CryptoPro CSP for Linux. Configure , perform its registration in the cryptographic provider:
/opt/cprocsp/sbin/amd64/cpconfig -hardware reader -add "Aladdin R.D. JaCarta [SCR Interface] (000000000000) 00 00"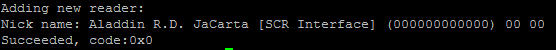
As a result of the execution, the following entry will be added to the /etc/opt/cprocsp/config64.ini configuration file
in the [KeyDevices \ PCSC] section: To fulfill the requirements of the Form, Terms of Use and CryptoPro CSP Security Administrator's Guide:
[KeyDevices\PCSC\"Aladdin R.D. JaCarta [SCR Interface] (000000000000) 00 00"\Default]
The use of CryptoPro CSP CIP version 4.0 with the enhanced key control mode off is not allowed. The inclusion of this mode is described in documents ZHTYA.00087-01 91 02. Security Administrator's Guide.You need to enable enhanced key usage control:
/opt/cprocsp/sbin/amd64/cpconfig -ini '\config\parameters' -add long StrengthenedKeyUsageControl 1Check that the mode is on: We
cat /etc/opt/cprocsp/config64.ini | grep StrengthenedKeyUsageControl
restart the cryptographic provider service:
/etc/init.d/cprocsp restart
/etc/init.d/cprocsp status
After the restart, we check that there are no errors in the provider’s work with key carriers:
/opt/cprocsp/bin/amd64/csptest -keyset –verifycontext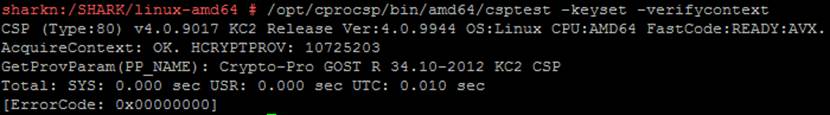
/opt/cprocsp/bin/amd64/csptest -keyset -verifycontext -enum –uniqueCSP (Type:80) v4.0.9017 KC2 Release Ver:4.0.9944 OS:Linux CPU:AMD64 FastCode:REA
AcquireContext: OK. HCRYPTPROV: 16052291
alfa_shark1 |SCARD\JACARTA_4E3900154029304C\CC00\E9F6
OK.
Total: SYS: 0.000 sec USR: 0.000 sec UTC: 4.560 sec
[ErrorCode: 0x00000000]
Work with JaCarta PKI Token
Let's run the Xming (X11 forwarding) program at our station so that we can open and work with the graphical interfaces of the necessary utilities via SSH.

After installing IDProtectClient - software for working with JaCarta PKI, two files appeared on the server in the / usr / share / applications folder :
Athena-IDProtectClient.desktop
Athena-IDProtectManager.desktop
These are shortcuts where you can see the startup options for executables Exec = / usr / bin / SACTools
Run the IDProtectPINTool utility .
Using it, PIN access codes for the token are set and changed.
/usr/bin/IDProtectPINTool
When initializing the token for the first time, a link containingPIN-коды (пароли) ключевых носителей по умолчанию
Программа IDProtect_Manager позволяет просматривать информацию о токене и контейнере с ключами и сертификатом:
/usr/bin/IDProtect_Manager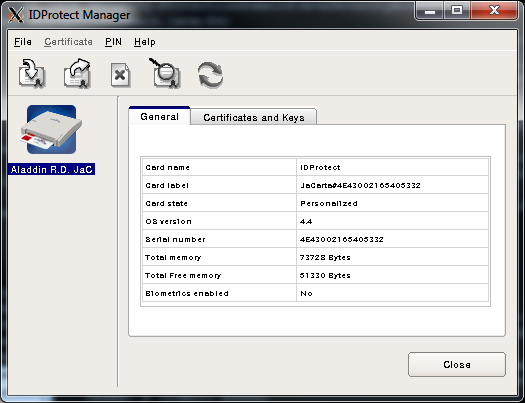
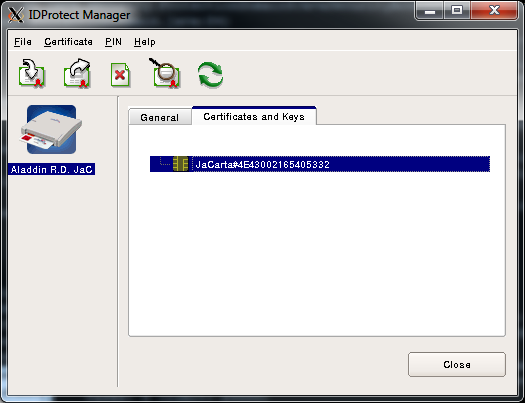
Для доступа к контейнеру с ключами нужно ввести пароль:

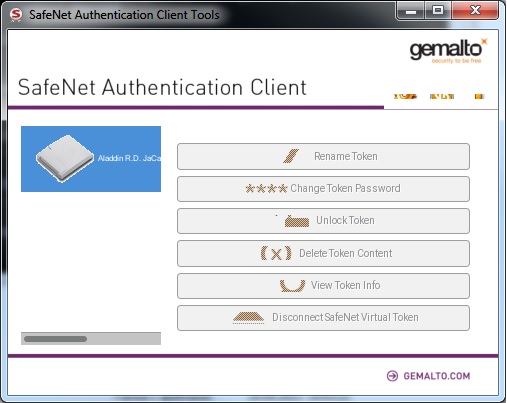
Для работы с SafeNet Authentication Client eToken PRO существуют аналогичные программы — SafeNet Authentication Client Monitor и SafeNet Authentication Client Tools, которые запускаются так:
/usr/bin/SACMonitor
/usr/bin/SACTools
Выполнять операции непосредственно с ключевыми контейнерами удобнее в интерфейсе криптографического провайдера КриптоПро JavaCSP:
/jdk1.8.0_181/jre/bin/java ru.CryptoPro.JCP.ControlPane.MainControlPane
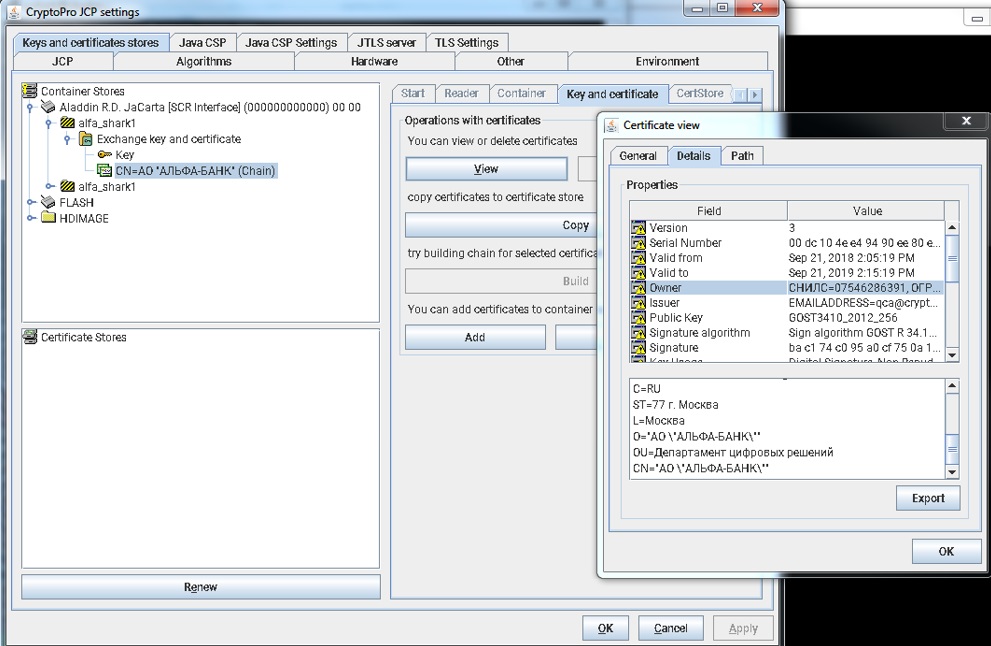
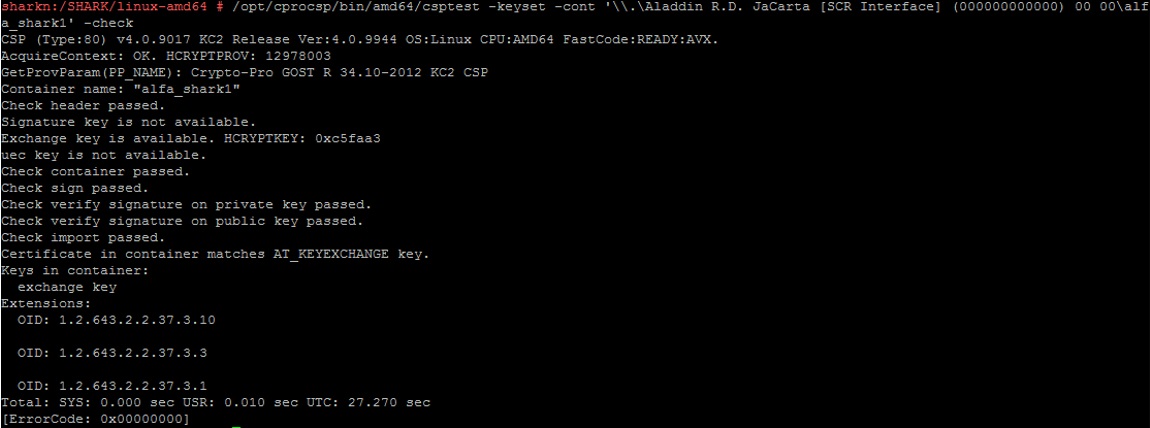
Для отображения информации о содержимом контейнера с ключами можно выполнить команду:
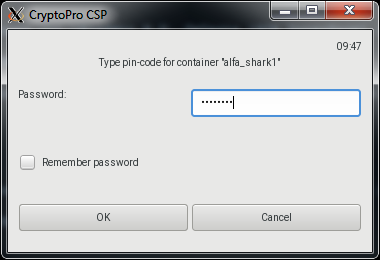
/opt/cprocsp/bin/amd64/csptest -keyset -cont '\\.\Aladdin R.D. JaCarta [SCR Interface] (000000000000) 00 00\alfa_shark1' -infoДля диагностики контейнера используется эта же команда с ключом –check
/opt/cprocsp/bin/amd64/csptest -keyset -cont '\\.\Aladdin R.D. JaCarta [SCR Interface] (000000000000) 00 00\alfa_shark' –checkYou will need to enter the password for the container:
Software Key Retrieval
In general, an example of retrieving a private key and a public key certificate from a container on a token using CryptoPro Java CSP is as follows:
import ru.CryptoPro.JCP.KeyStore.JCPPrivateKeyEntry;
import ru.CryptoPro.JCP.params.JCPProtectionParameter;
KeyStore keyStore = KeyStore.getInstance("Aladdin R.D. JaCarta [SCR Interface] (000000000000) 00 00", "JCSP");
keyStore.load(null, null);
JCPPrivateKeyEntry entry = null;
X509Certificate certificate = null;
PrivateKey privateKey = null;
try {
entry = (JCPPrivateKeyEntry) keyStore.getEntry(keyAlias,
new JCPProtectionParameter(pwd));
certificate = (X509Certificate) entry.getCertificate();
privateKey = entry.getPrivateKey();
} catch (UnrecoverableEntryException | NullPointerException e) {
LOGGER.log(Level.WARNING, PRIVATE_KEY_NOT_FOUND + keyAlias + ExceptionUtils.getFullStackTrace(e));
}
If you act like this:
Key key = keyStore.getKey(keyAlias, pwd);
then the cryptographic provider will try to display a request to enter the password to the container through the console or GUI window.
results
The token key carrier token is installed in the server’s internal USB port.
The server hardware itself is sealed and placed in a room with limited access.
Such measures can increase the level of protection of our information systems from theft and compromise of electronic signature or encryption keys, both remotely over the network and physically.
useful links
- Aladdin-RD JaCarta Documentation
- wiki.astralinux.ru - Work with CryptoPro CSP
- The list of error codes of the object model of components of Microsoft COM Error Codes (Security and Setup)
- CryptoPro CSP 4.0 CSP 4.0 FCN (Gemalto)
- Pcsc-tools reader diagnostic utility from security: chipcard project (software.opensuse.org)
- CryptoPro CSP for Linux. Customization.
- Aladdin-RD default key carrier PINs (passwords)
