Conference DEFCON 20. Capture in 60 seconds: from guest account to Windows domain administrator. Part 2
- Transfer
Conference DEFCON 20. Capture in 60 seconds: from guest account to Windows domain administrator. Part 1 The
good thing is that we can log into the local network by faking DNS. What about social engineering that takes into account user preferences and inclinations? Pentesters know that in IE you can put image file tags, for example, .jpg format, for a UNC network path, and then IE will send it back to Windows and automatically connect to the network folder, trying to get the requested image or something else, for example Javascript iFrame etc So today in IE there is an automatic authentication.
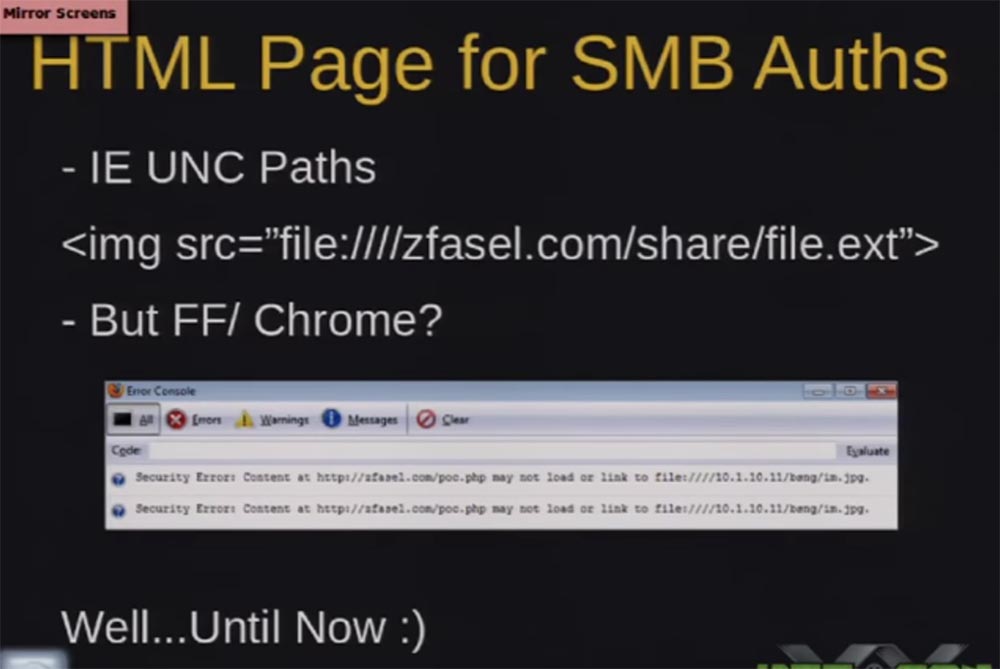
The same can be done in Firefox and Chrome, although people believe that these browsers are more secure. This screenshot shows the Firefox error console, which states that the browser cannot download this image file from the public network, since the security policy prevents the download of files that are not in the context of the browser security. An interesting feature of our tool is that Firefox and Chrome browsers can be made to download files by simply sending HTTP headers to force Content-Type: application / force-download to load and then open these files from the Temp folder or directly from the desktop. Thus, we set the security context of the files and activate automatic authentication in general SMB, so now you can force users to authenticate on your fraudulent server.
But what to do if they do not click “download file” or do not open it from the Temp folder? In this case, you can make sure that users are automatically authenticated simply by viewing the HTML page in the browser. For this, you need to connect plugins to Firefox and Chrome. My attention was drawn to the plugin, QuickTime, which is often set by users by default. I know that there are dozens of different plug-ins, but most of the time you meet people with iTunes on their iPhones and installed QuickTime. I went through the QuickTime feature list and wondered how I could tie it to my fraudulent network server to get people to authenticate by entering their username and password.
We thought a bit and decided that we could insert the playlist into the UNC network path, and then users would automatically authenticate and bypass the local security context. We need to work a little more on the other two plugins, but so far QuickTime has done an excellent job with our task.
Another way to force people to automatically authenticate to our server is through emails. Some people know that in Outlook you can use HTML email, or emails using an HTML template. If we have a shared network resource, then we can insert it into the email, and if the user opens this email, it will automatically connect to this resource and authenticate it.
For our purposes, you can use files in the .docs format. Any document can be used in the same way as an image or HTML file inserted into the UNC, the opening of which will automatically connect to the network share.
Do not forget about the desktop.ini file. This is not very well known, but you can generate this file to install such desktop resources as icons and wallpapers, and place it in a “shared” folder. At the same time, again, the system will automatically connect to receive these icons and “log in” using the current user account.

Likewise, you can change the parameters of the shortcut file with the .lnk extension to automatically connect to the resource.
So, our tool quickly and easily automatically creates these .ini or HTML files.
The last thing I want to talk about is MITM, or the “man in the middle.” You can redirect NTLM authentication requests or embed HTML content into the page, as the tool does not, and thus help it do its job. This is how you can force clients to connect to a fraudulent server in order to implement NTLM Relay. There are other tools that allow you to make NTLM Relay via SMB or HTTP and force users to authenticate for you.
Another great feature of Squirtle is the ability to make it the starting point for creating API requests, where you can use any tool you write to get Type 2 and 3 messages. Type 3 is the last authentication request, you must send an API message to get it Type 2 and get it back. I quickly wrote an API that allows you to use any set of tools you want, you can change the source code and use fraudulent servers to connect and so on.
However, if you are a pentester or are testing users, then you need some interconnections, a reverse interaction. Therefore, our tool includes a set of rules. I have already said that all existing tools send users to the same source, and we must determine who these users are. I wanted to do this in one click so that, as I said, it would be possible to get domain administrator authority in 60 seconds.
I wrote rules in our application based on the fact that users belong to groups, and goals belong to groups of goals.
As soon as we find out that a user belongs to a group and can get access to something during an automatic connection, we don’t need to force him to connect, wait and hope that he will return. We set a simple rule, later I will show it in the user interface that if the user is in group X, a certain module Y is used to perform action Z with respect to the target groups T. In a couple of seconds I will demonstrate how it works.
The rules also include the immediate verification of API requests, the verification of general rules, and repeating this until a timeout occurs. As soon as the time-out comes, you need to answer with a static call and keep the authentication state, not allowing the user to disconnect.
We can use SMB to connect to SMB, HTTP to connect to HTTP, HTTP to connect to SMB, and so on, through NTLM Relaying. The problem is that people practically do not use many other protocols, so I decided to look at protocols such as LDAP and MSSQL.
I’ll talk about LDAP a bit later, but for now I’ll note that MSSQL is a cool thing, because we can get a database, we can access the data, and this is amazing.

Since we are dealing with clients, we want actions to take place automatically right after we connect. Therefore, we listed users and groups using Metasploit, which was presented at the BlackHat conference this year. Thus, as a pentester, I gained access to shared files, was able to execute commands, and seized information about target users and target groups without administrator privileges. However, with all this, I can not connect to domain controllers. The reason is that by default most domain controllers have an SMB signature. For those who are not familiar with SMB signing, I’ll say that this is a security mechanism for the SMB protocol, also called security signatures. It uses the original NTLM hash to sign the session and signs each packet, and if there is no signature, it turns you off. Thus, by default, we cannot apply NTLM Relaying to a domain controller. It made me angry, so I decided to find out how to get to this controller quickly and easily. Let's go back a couple of slides.

It turned out that the LDAP domain controller is enabled by default, which allows the use of NTLM authentication, which is great. But we could not change the password, because, as a rule, changing the password or adding a user requires SSL and SSL is enabled in LDAP if the domain has a CA certificate. What we have done is entered into your tool, that you can change user passwords, exclude and add users, transfer domains, retrieve active user hashes from memory, log in to control the domain and do other cool things. It's great that you can add users to groups without SSL and other things, so as a pentester, you can take and connect other users' accounts, add them to the domain administrators group if you have received administrator privileges, and so on and so forth.
Let's go back to SMB. During my 4-hour flight here from Chicago, I thought of using an SMB SOCKS proxy for our purposes. Anyone who knows, knows that this protocol allows applications to communicate through a firewall that blocks a direct connection using an intermediate server to which both clients can connect. That is, SOCKS-proxy sends the pure data of one client to another and back. Thus, this proxy can replace NTLM packets with relayed data.

Using HTTP, we can link SharePoint servers to internal websites. Some people think that there will be no problem with NTLM because you are on the internal network, but what about external networks? There are also SharePoint servers sometimes, but not too often. I thought that many organizations are open to external access, supports NTLM and allow you to share web services. For those who are not familiar with Exchange Web Services (EWS), I’ll say that they are a kind of HTTP API, which are usually located on the same server as Outlook Web Access webmail. By default, they use the HTTP Negotiate authentication method, which supports NTLM, so we can make an external HTTP relay to the service located in the EWS.
This is worrying, because from the outside you can access the correspondence, contacts, calendar of events and set your own rules for email using HotSpot connection points. You can reach the EWS server via the Internet if they do not have firewall rules for outgoing connections that do not allow connecting to a fraudulent SMB server and automatically get authentication. And all this is possible due to the fact that everyone has a mobile phone connected to the EWS services and synchronized with them.
And now I need a drink, because in this place I wanted to start a demo. So, this slide shows what the graphical user interface of my ZackAttack application looks like, I will scroll the page just below so that you can see the settings for actions, goals, target groups and user groups.

So you can get an idea of its functionality and how it can be powerful. A fraudulent HTTP server, a fraudulent SMB server and a management HTTP server are running right now. Next, the slide shows which groups the users are in.

Here it is shown who connected to the network and when, so that you can trace which users have reconnected.

On the right, system accounts and accounts of existing users are shown in red, from where you can list goals via SMB in one click, receive mail from Exchange Web Services, use the command shell if you are the session administrator, access shared files, access SharePoint, and so on.

As I said before, we can create rules and we can add users to groups by automatic enumeration or by creating groups manually, for example, by creating a group called “moo”.

Something I can not, as I said, the gods do not love me demo. We'll have to go back and fix something in the program.

Sorry guys, but this is just an alpha release, I wrote this code alone in 3 weeks. Now I will add a group called “yar”, now you see that both of these groups appeared below, to which the selected user has been added.

As I said, we can also enumerate various user groups from a domain controller, this is the UserGroups tab, and create rules for automatic authentication using the Attack Rules tab.
Here you can see the users of the newly created Yar group who can be connected to Exchange Web Services for specific purposes of the target groups, and here you can also add any IP address, for example, 10.1.10.250 to the target group.

As soon as someone from the user group receives an authentication request, we automatically connect to the EWS and pull out all the letters from the Inbox, from the Drafts folder, we can easily add another folder, say, the Sent Items folder.

The best thing about this tool is that after authentication, the session is kept open throughout the connection to the fraudulent server and all these actions are performed. Thus, we do not need to re-authenticate to receive incoming emails.
Since we have 30 requests coming from the system, we can first set about 30 rules and then perform a wide variety of actions on this particular connection. As I said, we can repeat all these actions for all users and all the goals of a given connection or for specific purposes.
At the same time, we can generate the payload by clicking on the “Auth Payloads” tab. From here you can create HTML files to determine the user's OS and use one of the 3 methods to force the browser to automatically authenticate.

Here you can create desktop.ini to upload files to shared folders and use the file generator to inject the UNC Path into the xml .doc file, create shortcut .lnk files and archive Zip files, just like automatically create mail XTML files. All this is done as simply as possible using Firesheep and NTLM Relaying.
Finally, through the Results + Logs tab, my tool tracks user hashes, as it did before static authentication, so you can try to crack passwords.

So this was a demonstration of the ZackAttack features. So how do we protect against this? Protection is to limit the attack surface.

Everyone has their own methods of protection against attacks of this kind. People suggest using NTLM version 2. My tool supports this version, but there are no significant differences between version 2 and version 1.
You can install a firewall on outgoing port 445, which will protect you from sending out fraudulent payload that forces automatic authentication. However, this does not protect against penetration through mobile devices.
You can configure group policies to restrict the use of GPO programs in Windows 7 to limit the purpose of NTLM authentication. Everyone claims that the best solution is Kerberos. However, the problem is that the organization will need to switch everything to Kerberos, and this will not work, because there are many things that do not support Kerberos. Another thing is that if you turn on Kerberos, you won’t be able to support NTLM at all, the same goes for signing, because for those you don’t know, you will need to sign each package with the hash of the original password. Signing LDAP, SMB signatures, extended HTTP authentication is all not supported by Cerberus, so people are mistaken in thinking that signatures will solve all problems. If you introduce mandatory signatures, it can disable many things.
Therefore, in defending an organization, you must observe a certain balance. If you are an end user, you usually don’t worry about such things, but if you’re a system administrator for a corporation, the biggest challenge for you will be to stop using NTLM.
Since Windows 8 and Windows 2012 still support NTLM by default, it will take some time to abandon it and switch to using Kerberos, and I hope that my tool will help with this. It will be published on Tuesday, July 31, as soon as I get home, on zfasel.com/tools. It is also available on the DVD of this conference, as well as my slides. If you want to tell me how shitty my performance and my demo were, send emails to dc20@zfasel.com or follow my nickname @zfasel on Twitter.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until spring for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
good thing is that we can log into the local network by faking DNS. What about social engineering that takes into account user preferences and inclinations? Pentesters know that in IE you can put image file tags, for example, .jpg format, for a UNC network path, and then IE will send it back to Windows and automatically connect to the network folder, trying to get the requested image or something else, for example Javascript iFrame etc So today in IE there is an automatic authentication.

The same can be done in Firefox and Chrome, although people believe that these browsers are more secure. This screenshot shows the Firefox error console, which states that the browser cannot download this image file from the public network, since the security policy prevents the download of files that are not in the context of the browser security. An interesting feature of our tool is that Firefox and Chrome browsers can be made to download files by simply sending HTTP headers to force Content-Type: application / force-download to load and then open these files from the Temp folder or directly from the desktop. Thus, we set the security context of the files and activate automatic authentication in general SMB, so now you can force users to authenticate on your fraudulent server.
But what to do if they do not click “download file” or do not open it from the Temp folder? In this case, you can make sure that users are automatically authenticated simply by viewing the HTML page in the browser. For this, you need to connect plugins to Firefox and Chrome. My attention was drawn to the plugin, QuickTime, which is often set by users by default. I know that there are dozens of different plug-ins, but most of the time you meet people with iTunes on their iPhones and installed QuickTime. I went through the QuickTime feature list and wondered how I could tie it to my fraudulent network server to get people to authenticate by entering their username and password.
We thought a bit and decided that we could insert the playlist into the UNC network path, and then users would automatically authenticate and bypass the local security context. We need to work a little more on the other two plugins, but so far QuickTime has done an excellent job with our task.
Another way to force people to automatically authenticate to our server is through emails. Some people know that in Outlook you can use HTML email, or emails using an HTML template. If we have a shared network resource, then we can insert it into the email, and if the user opens this email, it will automatically connect to this resource and authenticate it.
For our purposes, you can use files in the .docs format. Any document can be used in the same way as an image or HTML file inserted into the UNC, the opening of which will automatically connect to the network share.
Do not forget about the desktop.ini file. This is not very well known, but you can generate this file to install such desktop resources as icons and wallpapers, and place it in a “shared” folder. At the same time, again, the system will automatically connect to receive these icons and “log in” using the current user account.

Likewise, you can change the parameters of the shortcut file with the .lnk extension to automatically connect to the resource.
So, our tool quickly and easily automatically creates these .ini or HTML files.
The last thing I want to talk about is MITM, or the “man in the middle.” You can redirect NTLM authentication requests or embed HTML content into the page, as the tool does not, and thus help it do its job. This is how you can force clients to connect to a fraudulent server in order to implement NTLM Relay. There are other tools that allow you to make NTLM Relay via SMB or HTTP and force users to authenticate for you.
Another great feature of Squirtle is the ability to make it the starting point for creating API requests, where you can use any tool you write to get Type 2 and 3 messages. Type 3 is the last authentication request, you must send an API message to get it Type 2 and get it back. I quickly wrote an API that allows you to use any set of tools you want, you can change the source code and use fraudulent servers to connect and so on.
However, if you are a pentester or are testing users, then you need some interconnections, a reverse interaction. Therefore, our tool includes a set of rules. I have already said that all existing tools send users to the same source, and we must determine who these users are. I wanted to do this in one click so that, as I said, it would be possible to get domain administrator authority in 60 seconds.
I wrote rules in our application based on the fact that users belong to groups, and goals belong to groups of goals.
As soon as we find out that a user belongs to a group and can get access to something during an automatic connection, we don’t need to force him to connect, wait and hope that he will return. We set a simple rule, later I will show it in the user interface that if the user is in group X, a certain module Y is used to perform action Z with respect to the target groups T. In a couple of seconds I will demonstrate how it works.
The rules also include the immediate verification of API requests, the verification of general rules, and repeating this until a timeout occurs. As soon as the time-out comes, you need to answer with a static call and keep the authentication state, not allowing the user to disconnect.
We can use SMB to connect to SMB, HTTP to connect to HTTP, HTTP to connect to SMB, and so on, through NTLM Relaying. The problem is that people practically do not use many other protocols, so I decided to look at protocols such as LDAP and MSSQL.
I’ll talk about LDAP a bit later, but for now I’ll note that MSSQL is a cool thing, because we can get a database, we can access the data, and this is amazing.

Since we are dealing with clients, we want actions to take place automatically right after we connect. Therefore, we listed users and groups using Metasploit, which was presented at the BlackHat conference this year. Thus, as a pentester, I gained access to shared files, was able to execute commands, and seized information about target users and target groups without administrator privileges. However, with all this, I can not connect to domain controllers. The reason is that by default most domain controllers have an SMB signature. For those who are not familiar with SMB signing, I’ll say that this is a security mechanism for the SMB protocol, also called security signatures. It uses the original NTLM hash to sign the session and signs each packet, and if there is no signature, it turns you off. Thus, by default, we cannot apply NTLM Relaying to a domain controller. It made me angry, so I decided to find out how to get to this controller quickly and easily. Let's go back a couple of slides.

It turned out that the LDAP domain controller is enabled by default, which allows the use of NTLM authentication, which is great. But we could not change the password, because, as a rule, changing the password or adding a user requires SSL and SSL is enabled in LDAP if the domain has a CA certificate. What we have done is entered into your tool, that you can change user passwords, exclude and add users, transfer domains, retrieve active user hashes from memory, log in to control the domain and do other cool things. It's great that you can add users to groups without SSL and other things, so as a pentester, you can take and connect other users' accounts, add them to the domain administrators group if you have received administrator privileges, and so on and so forth.
Let's go back to SMB. During my 4-hour flight here from Chicago, I thought of using an SMB SOCKS proxy for our purposes. Anyone who knows, knows that this protocol allows applications to communicate through a firewall that blocks a direct connection using an intermediate server to which both clients can connect. That is, SOCKS-proxy sends the pure data of one client to another and back. Thus, this proxy can replace NTLM packets with relayed data.

Using HTTP, we can link SharePoint servers to internal websites. Some people think that there will be no problem with NTLM because you are on the internal network, but what about external networks? There are also SharePoint servers sometimes, but not too often. I thought that many organizations are open to external access, supports NTLM and allow you to share web services. For those who are not familiar with Exchange Web Services (EWS), I’ll say that they are a kind of HTTP API, which are usually located on the same server as Outlook Web Access webmail. By default, they use the HTTP Negotiate authentication method, which supports NTLM, so we can make an external HTTP relay to the service located in the EWS.
This is worrying, because from the outside you can access the correspondence, contacts, calendar of events and set your own rules for email using HotSpot connection points. You can reach the EWS server via the Internet if they do not have firewall rules for outgoing connections that do not allow connecting to a fraudulent SMB server and automatically get authentication. And all this is possible due to the fact that everyone has a mobile phone connected to the EWS services and synchronized with them.
And now I need a drink, because in this place I wanted to start a demo. So, this slide shows what the graphical user interface of my ZackAttack application looks like, I will scroll the page just below so that you can see the settings for actions, goals, target groups and user groups.

So you can get an idea of its functionality and how it can be powerful. A fraudulent HTTP server, a fraudulent SMB server and a management HTTP server are running right now. Next, the slide shows which groups the users are in.

Here it is shown who connected to the network and when, so that you can trace which users have reconnected.

On the right, system accounts and accounts of existing users are shown in red, from where you can list goals via SMB in one click, receive mail from Exchange Web Services, use the command shell if you are the session administrator, access shared files, access SharePoint, and so on.

As I said before, we can create rules and we can add users to groups by automatic enumeration or by creating groups manually, for example, by creating a group called “moo”.

Something I can not, as I said, the gods do not love me demo. We'll have to go back and fix something in the program.

Sorry guys, but this is just an alpha release, I wrote this code alone in 3 weeks. Now I will add a group called “yar”, now you see that both of these groups appeared below, to which the selected user has been added.

As I said, we can also enumerate various user groups from a domain controller, this is the UserGroups tab, and create rules for automatic authentication using the Attack Rules tab.
Here you can see the users of the newly created Yar group who can be connected to Exchange Web Services for specific purposes of the target groups, and here you can also add any IP address, for example, 10.1.10.250 to the target group.

As soon as someone from the user group receives an authentication request, we automatically connect to the EWS and pull out all the letters from the Inbox, from the Drafts folder, we can easily add another folder, say, the Sent Items folder.

The best thing about this tool is that after authentication, the session is kept open throughout the connection to the fraudulent server and all these actions are performed. Thus, we do not need to re-authenticate to receive incoming emails.
Since we have 30 requests coming from the system, we can first set about 30 rules and then perform a wide variety of actions on this particular connection. As I said, we can repeat all these actions for all users and all the goals of a given connection or for specific purposes.
At the same time, we can generate the payload by clicking on the “Auth Payloads” tab. From here you can create HTML files to determine the user's OS and use one of the 3 methods to force the browser to automatically authenticate.

Here you can create desktop.ini to upload files to shared folders and use the file generator to inject the UNC Path into the xml .doc file, create shortcut .lnk files and archive Zip files, just like automatically create mail XTML files. All this is done as simply as possible using Firesheep and NTLM Relaying.
Finally, through the Results + Logs tab, my tool tracks user hashes, as it did before static authentication, so you can try to crack passwords.

So this was a demonstration of the ZackAttack features. So how do we protect against this? Protection is to limit the attack surface.

Everyone has their own methods of protection against attacks of this kind. People suggest using NTLM version 2. My tool supports this version, but there are no significant differences between version 2 and version 1.
You can install a firewall on outgoing port 445, which will protect you from sending out fraudulent payload that forces automatic authentication. However, this does not protect against penetration through mobile devices.
You can configure group policies to restrict the use of GPO programs in Windows 7 to limit the purpose of NTLM authentication. Everyone claims that the best solution is Kerberos. However, the problem is that the organization will need to switch everything to Kerberos, and this will not work, because there are many things that do not support Kerberos. Another thing is that if you turn on Kerberos, you won’t be able to support NTLM at all, the same goes for signing, because for those you don’t know, you will need to sign each package with the hash of the original password. Signing LDAP, SMB signatures, extended HTTP authentication is all not supported by Cerberus, so people are mistaken in thinking that signatures will solve all problems. If you introduce mandatory signatures, it can disable many things.
Therefore, in defending an organization, you must observe a certain balance. If you are an end user, you usually don’t worry about such things, but if you’re a system administrator for a corporation, the biggest challenge for you will be to stop using NTLM.
Since Windows 8 and Windows 2012 still support NTLM by default, it will take some time to abandon it and switch to using Kerberos, and I hope that my tool will help with this. It will be published on Tuesday, July 31, as soon as I get home, on zfasel.com/tools. It is also available on the DVD of this conference, as well as my slides. If you want to tell me how shitty my performance and my demo were, send emails to dc20@zfasel.com or follow my nickname @zfasel on Twitter.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until spring for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
