Hackers claim to have cracked NASA’s security system and gained control of a drone worth $ 222.7 million
Welcome iCover Blog Readers ! AnonSec international hacker team said they were able to crack the security system of the National Aeronautics and Space Administration (NASA). As evidence, hackers published a 276 GB photo-video archive borrowed from the agency’s servers. According to AnonSec, access was also obtained to the control system of the Global Hawk drone flight program, worth $ 222.7 million, after which the latter was sent to the Pacific Ocean.

“OpNasaDrones” - this was the title of the new issue of their own ezin published by hackers on PasteBin. On the pages of AnonSec magazine, she spoke in detail about the motives for the hack and how exactly they were able to once again crack the NASA security system.
“NASA has been hacked many times, most of us won’t even say how much,” hackers write. - Initially, we did not focus on these drones and chemical samples of the upper atmosphere. We didn’t even plan to infiltrate NASA systems; they picked up the Gozi trojan back in 2013" Thus, as noted in the publication by the representative of the international “brigade” AnonSec, which unites hackers from Great Britain, Germany, Japan, Malaysia, Morocco, Indonesia, India, Pakistan, Iraq, Italy, Romania and Latvia, the latter is to the creators of the Trojan, which once infected more than 1 million computers, had no relation. Access to the infected NASA servers from its developer was purchased and became the main entry point, allowing you to move in the right direction.
The next step was to establish the number of such servers on the NASA network that could be hacked and then obtained root-access rights. “You would be surprised to find out how unprofessional government security standards are, the budget allocated for these purposes and the stupid employees entrusted with the control of the computer network are low ...” - notes the author of the publication AnonSec, accompanying his words in a chat with an online journalist a fun “branded” emoticon.

According to AnonSec, NASA server security really left much to be desired: by launching brute force, hackers discovered the first combination of login and root password in 0.32 seconds. At the following stages, they were able to easily get into the internal network of the department, gaining root access, including to network data storages. After intercepting the password of the system administrator, according to hackers, they were able to gain full access to three network-attached storage devices (NAS), which compiled backup copies of aircraft flight logs. The hackers' property also became materials of the John Glenn Research Center, the Space Flight Center. R. Goddard and the Flight Research Center. Dryden. Thus, among the information to which unlimited access was obtained were data,
As hackers describe the goals and mission of this hack: “One of the main goals of our operation is to clarify issues related to NASA's cloud planting, geoengineering and weather management research. You can call it what you want, in fact, it is one and the same. Up to this point, NASA has already conducted a series of tests to study aerosols and their effects on weather and the environment. And we felt that it is worth concentrating efforts in this direction ... ”- AnonSec narrates.
The method of weather correction using silver iodide, in order to provoke precipitation in the clouds, was used by the US military as part of Operation Operation Popeye”During the Vietnam War. Then after sowing clouds in the northern part of the country, which led to heavy rainfall, US units N were able to block the supply of food and ammunition to the fiercely resisting Viet Cong. According to information provided by NASA specialist Erik Conway (Erik Conway), one of the applications of the technology involves “injection of sulfate particles into the upper atmosphere, which, in fact, simulates a large-scale volcanic eruption and creates a barrier to the reflection of sunlight from the planet.”
A survey conducted by NASA experts among the leading climatologists of the planet indirectly identified priorities in the development of this area, but from a slightly different angle: “Just over half - 54% of the 80 international climatologists participating in our survey agreed that the present is so difficult that a backup plan would not be in the way, including the artificial manipulation of the global climate to deal with the effects of anthropogenic greenhouse gas emissions, ”say This article is published in Climate scientists: it's time for 'Plan B' , published in Independent back in January 2009.
“We are sure that many people still don’t even suspect that the research is actually conducted on behalf of the federal government, although it is well known that the CIA finances research that has been ongoing for several years and aimed at studying the effects of climate change on the territory of entire states,” The publication says on behalf of AnonSec.
According to hackers, the U.S. government is actively supporting NASA projects related to atomization of heavy metals to stimulate rain or, conversely, disperse clouds, which is very likely to have a very negative impact on the health of populations of entire regions, the quality and safety of crops. Since plants that are not subject to special treatment under the new conditions are developing with difficulty, farmers are forced to purchase genetically modified “seeds –Terminators” (the term AnonSec), which stimulates the monopoly of producers of GMO seeds in the market. This and other cited arguments explain the motives of AnonSec, citing several reports and patents as confirmation of the development of artificial weather correction programs on the planet by the agency.
Although, according to earlier information, NASA really worked with projects to sow the upper layers of the atmosphere and study the consequences of such a “cultivation,” there is no new evidence that at the time of the hacking, the agency is really working out some kind of a single and coordinated global program and is actively conducting research in this direction by hackers received and not provided.
During the experiment, according to AnonSec, they also managed to gain access to information related to the ambitious projects of Global Hawk drones , worth more than $ 220 million and the mission OIB ( Operation Ice Bridge ).
Despite the impressive flying and technical characteristics (the Global Hawk reconnaissance UAV is capable of spending up to 24 hours in the air), according to AnonSec hackers, the level of protection of confidential data with the drone is worse than ever. Hackers drew attention to the fact that NASA engineers, for most missions, as a rule, download pre-calculated flight plans in .gpx file format to the UAV's on-board computer. Using the information received, the hackers carried out a man-in-the-middle attack, which, they claimed, allowed them to reprogram the Global Hawk flight plan on a new route, sending the drone directly into the Pacific Ocean. With a high degree of probability, the situation would develop according to the scenario proposed by AnonSec and Global Hawk would not go on its next flight with a new mission,
The screenshot below shows a perspective drone flight path along a route adjusted by hackers (according to AnonSec).
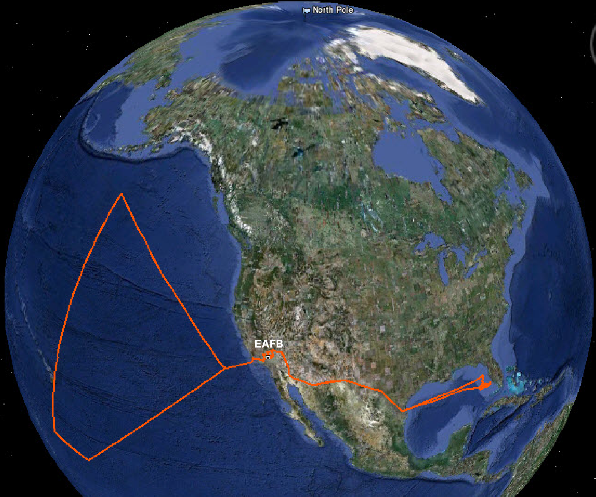
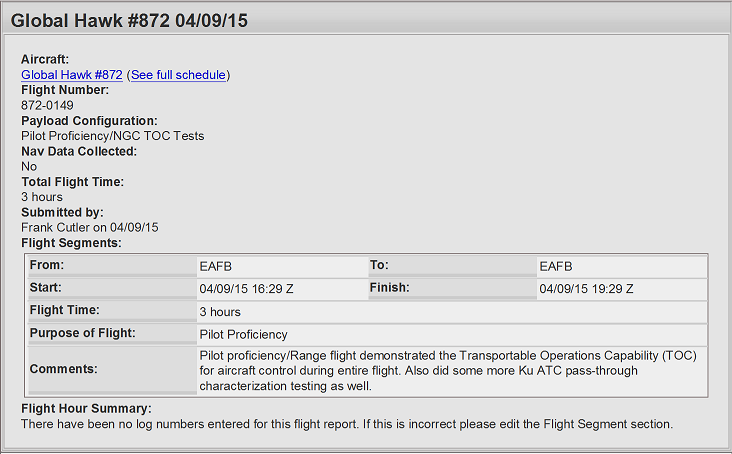
Only after the incident, NASA employees suspected that someone else had control over their networks. Although the described situation occurred in the spring of 2015 (screen shot below), no official comments have been received from the agency for obvious reasons so far.
They refused to publish information about the incident in the publications of Wikileaks and The Guardian, with whom AnonSec contacted. And relatively recently, on January 31, 2016, a fairly comprehensive “report” on the work done by the AnonSec team covering the leak was agreed to be published on the pages of InfoWars. Hackers insist that the information presented in the 276 - gigabyte archive and is now distributed through torrents is genuine. And this, almost 631 videos from UAVs and meteorological radars, 2143 logbooks, real names, email addresses and telephones of 2414 employees of the department. Although there are skeptics who are convinced that the AnonSec raid is no more than a talentedly organized public relations campaign, the aforementioned drone was under the control of the NASA MCC all the time, and all data collected in the archive, including personal data of agency employees, can be easily found in the public domain .

Developing AnonSec: “Shortly after the alleged episode, the vulnerability was fixed. Whether NASA experts prompted the UAV episode to take active action, or is it suspiciously difficult to say the suspiciously high volume of traffic through compiled networks when collecting information about flight logs, ”hackers say. One way or another, attempts to enter the system along the beaten track several days after the episode failed.
So, if we discard the version about artificially increasing the popularity rating of the AnonSec brigade in such a non-standard way, then the huge amount of NASA confidential information was still lost. And, first of all, these are flight magazines with video files, flight routes, aircraft models, mission names, sensor readings and GPS coordinates.
As noted on the InfoWars web page, its staff contacted NASA’s IT Security department, but did not meet with any interest in commenting on the leak in detail. Refused to comment on the appeal of online journalists by phone or e-mail and the FBI. An interesting situation is with the published phone numbers of agency employees, through which InfoWars journalists selectively dialed. And although it was not possible to communicate with any of the subscribers on the other end of the line, the answering machine confirmed the correspondence of the numbers to their owners listed on the AnonSec list, the publication notes.
Source 1
Source 2
Dear readers, we are always happy to meet and wait for you on the pages of our blog. We are ready to continue to share with you the latest news, review materials and other publications, and will try to do our best to make the time spent with us useful for you. And, of course, do not forget to subscribe to our columns . Our other articles and events


“OpNasaDrones” - this was the title of the new issue of their own ezin published by hackers on PasteBin. On the pages of AnonSec magazine, she spoke in detail about the motives for the hack and how exactly they were able to once again crack the NASA security system.
“NASA has been hacked many times, most of us won’t even say how much,” hackers write. - Initially, we did not focus on these drones and chemical samples of the upper atmosphere. We didn’t even plan to infiltrate NASA systems; they picked up the Gozi trojan back in 2013" Thus, as noted in the publication by the representative of the international “brigade” AnonSec, which unites hackers from Great Britain, Germany, Japan, Malaysia, Morocco, Indonesia, India, Pakistan, Iraq, Italy, Romania and Latvia, the latter is to the creators of the Trojan, which once infected more than 1 million computers, had no relation. Access to the infected NASA servers from its developer was purchased and became the main entry point, allowing you to move in the right direction.
The next step was to establish the number of such servers on the NASA network that could be hacked and then obtained root-access rights. “You would be surprised to find out how unprofessional government security standards are, the budget allocated for these purposes and the stupid employees entrusted with the control of the computer network are low ...” - notes the author of the publication AnonSec, accompanying his words in a chat with an online journalist a fun “branded” emoticon.

According to AnonSec, NASA server security really left much to be desired: by launching brute force, hackers discovered the first combination of login and root password in 0.32 seconds. At the following stages, they were able to easily get into the internal network of the department, gaining root access, including to network data storages. After intercepting the password of the system administrator, according to hackers, they were able to gain full access to three network-attached storage devices (NAS), which compiled backup copies of aircraft flight logs. The hackers' property also became materials of the John Glenn Research Center, the Space Flight Center. R. Goddard and the Flight Research Center. Dryden. Thus, among the information to which unlimited access was obtained were data,
Motivation
As hackers describe the goals and mission of this hack: “One of the main goals of our operation is to clarify issues related to NASA's cloud planting, geoengineering and weather management research. You can call it what you want, in fact, it is one and the same. Up to this point, NASA has already conducted a series of tests to study aerosols and their effects on weather and the environment. And we felt that it is worth concentrating efforts in this direction ... ”- AnonSec narrates.
The method of weather correction using silver iodide, in order to provoke precipitation in the clouds, was used by the US military as part of Operation Operation Popeye”During the Vietnam War. Then after sowing clouds in the northern part of the country, which led to heavy rainfall, US units N were able to block the supply of food and ammunition to the fiercely resisting Viet Cong. According to information provided by NASA specialist Erik Conway (Erik Conway), one of the applications of the technology involves “injection of sulfate particles into the upper atmosphere, which, in fact, simulates a large-scale volcanic eruption and creates a barrier to the reflection of sunlight from the planet.”
A survey conducted by NASA experts among the leading climatologists of the planet indirectly identified priorities in the development of this area, but from a slightly different angle: “Just over half - 54% of the 80 international climatologists participating in our survey agreed that the present is so difficult that a backup plan would not be in the way, including the artificial manipulation of the global climate to deal with the effects of anthropogenic greenhouse gas emissions, ”say This article is published in Climate scientists: it's time for 'Plan B' , published in Independent back in January 2009.
“We are sure that many people still don’t even suspect that the research is actually conducted on behalf of the federal government, although it is well known that the CIA finances research that has been ongoing for several years and aimed at studying the effects of climate change on the territory of entire states,” The publication says on behalf of AnonSec.
According to hackers, the U.S. government is actively supporting NASA projects related to atomization of heavy metals to stimulate rain or, conversely, disperse clouds, which is very likely to have a very negative impact on the health of populations of entire regions, the quality and safety of crops. Since plants that are not subject to special treatment under the new conditions are developing with difficulty, farmers are forced to purchase genetically modified “seeds –Terminators” (the term AnonSec), which stimulates the monopoly of producers of GMO seeds in the market. This and other cited arguments explain the motives of AnonSec, citing several reports and patents as confirmation of the development of artificial weather correction programs on the planet by the agency.
Although, according to earlier information, NASA really worked with projects to sow the upper layers of the atmosphere and study the consequences of such a “cultivation,” there is no new evidence that at the time of the hacking, the agency is really working out some kind of a single and coordinated global program and is actively conducting research in this direction by hackers received and not provided.
Global Hawk for $ 222.7 million goes under the control of AnonSec
During the experiment, according to AnonSec, they also managed to gain access to information related to the ambitious projects of Global Hawk drones , worth more than $ 220 million and the mission OIB ( Operation Ice Bridge ).
Despite the impressive flying and technical characteristics (the Global Hawk reconnaissance UAV is capable of spending up to 24 hours in the air), according to AnonSec hackers, the level of protection of confidential data with the drone is worse than ever. Hackers drew attention to the fact that NASA engineers, for most missions, as a rule, download pre-calculated flight plans in .gpx file format to the UAV's on-board computer. Using the information received, the hackers carried out a man-in-the-middle attack, which, they claimed, allowed them to reprogram the Global Hawk flight plan on a new route, sending the drone directly into the Pacific Ocean. With a high degree of probability, the situation would develop according to the scenario proposed by AnonSec and Global Hawk would not go on its next flight with a new mission,
The screenshot below shows a perspective drone flight path along a route adjusted by hackers (according to AnonSec).

Only after the incident, NASA employees suspected that someone else had control over their networks. Although the described situation occurred in the spring of 2015 (screen shot below), no official comments have been received from the agency for obvious reasons so far.

They refused to publish information about the incident in the publications of Wikileaks and The Guardian, with whom AnonSec contacted. And relatively recently, on January 31, 2016, a fairly comprehensive “report” on the work done by the AnonSec team covering the leak was agreed to be published on the pages of InfoWars. Hackers insist that the information presented in the 276 - gigabyte archive and is now distributed through torrents is genuine. And this, almost 631 videos from UAVs and meteorological radars, 2143 logbooks, real names, email addresses and telephones of 2414 employees of the department. Although there are skeptics who are convinced that the AnonSec raid is no more than a talentedly organized public relations campaign, the aforementioned drone was under the control of the NASA MCC all the time, and all data collected in the archive, including personal data of agency employees, can be easily found in the public domain .


Developing AnonSec: “Shortly after the alleged episode, the vulnerability was fixed. Whether NASA experts prompted the UAV episode to take active action, or is it suspiciously difficult to say the suspiciously high volume of traffic through compiled networks when collecting information about flight logs, ”hackers say. One way or another, attempts to enter the system along the beaten track several days after the episode failed.

So, if we discard the version about artificially increasing the popularity rating of the AnonSec brigade in such a non-standard way, then the huge amount of NASA confidential information was still lost. And, first of all, these are flight magazines with video files, flight routes, aircraft models, mission names, sensor readings and GPS coordinates.
As noted on the InfoWars web page, its staff contacted NASA’s IT Security department, but did not meet with any interest in commenting on the leak in detail. Refused to comment on the appeal of online journalists by phone or e-mail and the FBI. An interesting situation is with the published phone numbers of agency employees, through which InfoWars journalists selectively dialed. And although it was not possible to communicate with any of the subscribers on the other end of the line, the answering machine confirmed the correspondence of the numbers to their owners listed on the AnonSec list, the publication notes.
Source 1
Source 2
Dear readers, we are always happy to meet and wait for you on the pages of our blog. We are ready to continue to share with you the latest news, review materials and other publications, and will try to do our best to make the time spent with us useful for you. And, of course, do not forget to subscribe to our columns . Our other articles and events

