Viruses, statistics and a bit of everything
Everyone “knows” who actually writes viruses, but do you know what the average life time of one virus is, what users do by installing an antivirus, and why do antivirus companies rarely talk about penetration in the news?
Interesting? We ask for a cut!
Let's start with the time of life. We will not repeat the news that in some organization or company they found a virus that went unnoticed ... for years. This happens, but usually such cases are associated with targeted attacks, when the implementation occurs in a small number of organizations. The usual malware attack is aimed at a large number of individuals or companies and it is only logical that sooner or later someone will pay attention to the new trojan. The reaction time of antiviruses (without a cloud) is approximately two hours, respectively, a rather high probability that a malicious file will be destroyed on infected computers in two to three hours.
Unfortunately for users, malware development lends itself to automation and attackers can issue malicious programs faster than antivirus updates:
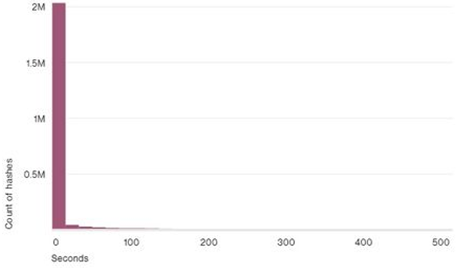
Source
More than 99% of malware samples (hashes) “live” (detected in the wild) 58 seconds or less!
How many malware are released per day by cybercriminals? Nobody knows the exact number, in particular because it is impossible to guarantee that all malware created on the same day that day will be caught. Up to a million samples come in for analysis per day. Of course, there are fewer signatures, but also a lot :

This is without android, adware, tool and other signatures.
And now about the sad. It is logical that such a speed of release of malicious programs, plus the use of non-detection tools by attackers (repacking, obfuscation, elimination of known signatures, etc.) lead to the fact that whatever antivirus is, but to catch 100% of malicious programs at the time of penetration into the network, including unknown he cannot. If anyone thinks that this is the saddest thing, then he is wrong. There are two sadnesses. The first is that regulators indicate in their documents that the antivirus protection is exclusively antivirus (and even does not even use heuristics ), and the second is that information security experts, following the regulators, believe (the result of surveys at conferences) that a good antivirus can Detect all malware at the time of penetration into the network.
Conclusions:
Since we mentioned updates, let's talk about them.
But this is after the epidemics of Wanna Cry and Nepeta, which probably the most lazy media did not write about!
Well, these are companies, but how do users behave? Microsoft responds to this. Thanks to her system of collecting information about users, she now also knows how antivirus users behave. Open Microsoft Security Intelligence Report Volume 22:

Yellow - installed and turned off antivirus. Impressive, huh? And green is installed, but not updated.
And by the way, the number of computers without antivirus in the latest versions of Windows does not mean that the situation is better there, they just have Windows Defender enabled by default - which users may not know about.
About the same statistics gives the CureIt utility! - At least 60 percent of computers are not protected. Add to this the lack of updates and default passwords, and we should not be surprised at the ransomware ransomware, as there are few victims.
But back to updates.drweb.com. Which type of trojan do you think is the most popular? Cryptographers (Trojan.Encoder)? Miners (Trojan.BtcMine)?
Loaders:

What do they do? Example
Modern malware is a complex of many parts. Loaders are the first to arrive at the machines, analyze the situation, download the “payload”, clean the logs and remove themselves. As a result, the researchers get the entire malicious complex except the bootloader, as a result of which the infection method (vulnerability in the system) remains unknown and the infection can happen again.
Conclusion. Take care of the logs, they are the key to a successful analysis of the IT incident.
What time do the attacks occur? Legends say that real attackers work at night. Is it so?


The source is
funny, but the intensity of the attacks completely coincides with the maximum activity of company employees - coming to work, time before lunch and time at the end of the working day. The fourth peak - attacks at night can be caused by the fact that at this time the probability of detecting an attack and reacting to it by the company’s security service is much lower.
By the way, another figure from the link already given . About three days
elapse between the publication of the vulnerability and the start of the attacks. The conclusion is that it is dangerous to postpone security updates for a longer period.
I hope it was interesting, if you have any questions, I will be grateful.
Interesting? We ask for a cut!
Let's start with the time of life. We will not repeat the news that in some organization or company they found a virus that went unnoticed ... for years. This happens, but usually such cases are associated with targeted attacks, when the implementation occurs in a small number of organizations. The usual malware attack is aimed at a large number of individuals or companies and it is only logical that sooner or later someone will pay attention to the new trojan. The reaction time of antiviruses (without a cloud) is approximately two hours, respectively, a rather high probability that a malicious file will be destroyed on infected computers in two to three hours.
Unfortunately for users, malware development lends itself to automation and attackers can issue malicious programs faster than antivirus updates:

Source
More than 99% of malware samples (hashes) “live” (detected in the wild) 58 seconds or less!
How many malware are released per day by cybercriminals? Nobody knows the exact number, in particular because it is impossible to guarantee that all malware created on the same day that day will be caught. Up to a million samples come in for analysis per day. Of course, there are fewer signatures, but also a lot :

This is without android, adware, tool and other signatures.
And now about the sad. It is logical that such a speed of release of malicious programs, plus the use of non-detection tools by attackers (repacking, obfuscation, elimination of known signatures, etc.) lead to the fact that whatever antivirus is, but to catch 100% of malicious programs at the time of penetration into the network, including unknown he cannot. If anyone thinks that this is the saddest thing, then he is wrong. There are two sadnesses. The first is that regulators indicate in their documents that the antivirus protection is exclusively antivirus (and even does not even use heuristics ), and the second is that information security experts, following the regulators, believe (the result of surveys at conferences) that a good antivirus can Detect all malware at the time of penetration into the network.
Conclusions:
- Despite the widespread use by virus writers of services such as VirusTotal, the traditional heuristic does not lose ground. So one of the two Russian antiviruses detected Wanna Cry right away with heuristics.
- A behavioral or preventive malware detection mechanism in antivirus software is required. Unfortunately, the majority of users believe that prevention in antivirus software is superfluous and purchase products without it. A typical example is the results of voting for components that should be in the antivirus
- Cloud mechanisms have the advantage that rules updates are laid out on them immediately and the antivirus can instantly apply them. According to rumors, the second Russian antivirus also detected Wanna Cry, but the cloud affected companies in which the cloud was disabled or not allowed at all.
- Antivirus is not a wizard and cannot detect 100% of malicious files. Therefore, to protect against the penetration of malicious programs, you need to install updates and restrict rights.
Since we mentioned updates, let's talk about them.
A report from Fortinet Corporation showed that in the second quarter of 2017, 90% of organizations recorded exploits for vulnerabilities that were more than three years old. Researchers also noted that 10 years after fixing defects, 60% of companies were still subjected to corresponding attacks.
But this is after the epidemics of Wanna Cry and Nepeta, which probably the most lazy media did not write about!
Well, these are companies, but how do users behave? Microsoft responds to this. Thanks to her system of collecting information about users, she now also knows how antivirus users behave. Open Microsoft Security Intelligence Report Volume 22:

Yellow - installed and turned off antivirus. Impressive, huh? And green is installed, but not updated.
And by the way, the number of computers without antivirus in the latest versions of Windows does not mean that the situation is better there, they just have Windows Defender enabled by default - which users may not know about.
About the same statistics gives the CureIt utility! - At least 60 percent of computers are not protected. Add to this the lack of updates and default passwords, and we should not be surprised at the ransomware ransomware, as there are few victims.
But back to updates.drweb.com. Which type of trojan do you think is the most popular? Cryptographers (Trojan.Encoder)? Miners (Trojan.BtcMine)?
Loaders:

What do they do? Example
The Trojan Trojan.DownLoader23.60762 contacts the management server to receive commands, including the following:
- run the file from a temporary folder on the disk of the infected computer;
- integrate into a working process;
- download the specified file;
- run the specified executable file;
- save and transfer to attackers the SQLite database used by Google Chrome;
- delete cookies;
- reboot the operating system;
- turn off computer.
Modern malware is a complex of many parts. Loaders are the first to arrive at the machines, analyze the situation, download the “payload”, clean the logs and remove themselves. As a result, the researchers get the entire malicious complex except the bootloader, as a result of which the infection method (vulnerability in the system) remains unknown and the infection can happen again.
Conclusion. Take care of the logs, they are the key to a successful analysis of the IT incident.
What time do the attacks occur? Legends say that real attackers work at night. Is it so?


The source is
funny, but the intensity of the attacks completely coincides with the maximum activity of company employees - coming to work, time before lunch and time at the end of the working day. The fourth peak - attacks at night can be caused by the fact that at this time the probability of detecting an attack and reacting to it by the company’s security service is much lower.
By the way, another figure from the link already given . About three days
elapse between the publication of the vulnerability and the start of the attacks. The conclusion is that it is dangerous to postpone security updates for a longer period.
I hope it was interesting, if you have any questions, I will be grateful.
