SecaaS as a type of cloud services and other standards of the GOST project "Information Security Using Cloud Technologies"

In the previous article “Everything is according to GOST. Information protection when using virtualization technologies ” , we mentioned the developed GOST project“ Information protection when using cloud technologies ”. Despite the fact that it has been without approval for more than a year, we can focus on it as a source of information on the direction of regulators' activities in the field of cloud technologies. The project is also valuable in a systematic list of terms, threats and protection measures for cloud services.
Let's start in order, as indicated in the draft, GOST establishes requirements for the protection of information processed using cloud technologies. Therefore, I propose to go to the terms and understand what is understood in the project as cloud technologies and other terms that are found in this document. It is worth noting in advance that some of the standards in this document are highly controversial and at times contradict established business practice.
Terms
Of course, in this article we will not consider the entire list of terms and definitions, they can be found in detail in the project itself, we will single out the main and most interesting ones.
So, according to the version of the Project, which in turn refers to a number of standards, namely GOST R ISO / IEC 27000, GOST R ISO / IEC 27001, GOST R 50922, GOST R 53114, the following definition of cloud computing is given.
Cloud computing : a model for providing users, upon request, with ubiquitous and convenient network access to a pool of computer resources distributed between them (for example, processor time (processing power), storage space, computer network bandwidth, network services, programs, etc.) allocated and provided with a minimum amount of management actions and minimal interaction with the service provider.The Project also defines cloud services: a service consisting in the provision of cloud resources to its consumers. But here the types of services under consideration are more interesting. The following main types of services are highlighted in the Project:
- BPaaS - Business process as a service - business process as a service;
- CaaS - Communications as a service - communication as a service;
- DaaS - Data as a service - data storage as a service;
- HaaS - Hardware as a service - hardware as a service;
- IaaS - Information as a service - infrastructure as a service;
- NaaS - Network as a service - connection as a service;
- PaaS - Platform as a service - platform as a service;
- SaaS - Software as a service - software as a service;
- SDPaaS - Service delivery platform as a service - cloud development environment as a service;
- SecaaS - Security as a service - security as a service;
- TraaaS - Transparency as a service - transparency as a service;
- WaaS - Workplace as a service - workstation as a service.
As you can see, the Project includes a fairly large number of cloud services, including some rather rare services, such as TraaaS (transparency).
Why are they on a par with those familiar in the industry and summarizing IaaS, Paas and SaaS? Why is DaaS not a Desktop as a Service , but a cloud storage? How can the consumer guess that TraaaS (transparency as a service) provides an opportunity to recover information lost during the transition to cloud computing? In our opinion, such standards are far from reaching consensus in the professional community.
In addition, various models of cloud hosting are considered, although their definitions are also quite controversial and not entirely consistent with the same standards on the basis of which the Project data was developed. Nevertheless, we list the models under consideration:
- private cloud (supplier and consumer - one organization);
- public cloud (supplier and consumer are different organizations);
- public cloud (consumer - a specific community from different organizations with common goals);
- hybrid cloud (combined two or more types of clouds).
The cloud infrastructure itself is considered as a composition of hierarchically interconnected groups of hardware and software implementing the five inherent properties of the cloud computing model. There is an important note for understanding, and the application even has a picture, I will give it below.
- Cloud infrastructure includes both physical and abstract layers.
- At the physical level (equipment level) is the hardware of the perimeter of the cloud infrastructure - the hardware used to implement cloud technologies.
- Among the abstract levels are distinguished: the level of orchestration, the level of management and the level of virtualization.
At the level of orchestration, there are tools for processing requests from consumers of cloud services and reports of means for the centralized distribution of cloud resources about their spending.
At the management level, there are facilities for the centralized distribution of cloud resources among cloud service consumers based on requests from the orchestration level.
At the virtualization level, hypervisors and the objects generated by them are located. The level of virtualization is absent in the cloud infrastructure if virtualization technologies are not used for its implementation.
4. Cloud infrastructure is built in compliance with the following hierarchy of levels:
- the top level is the level of orchestration;
- under the level of orchestration is the control level;
- under the control level - virtualization level (in case of using virtualization technology);
- the bottom is the physical level (equipment level).
5. Five inherent properties of cloud computing are implemented using tools located at different levels of the cloud infrastructure:
- self-service at the request of consumers, prompt response, ubiquitous access and measurability are implemented at the level of orchestration;
- combining computer resources into a single pool - at the management level.
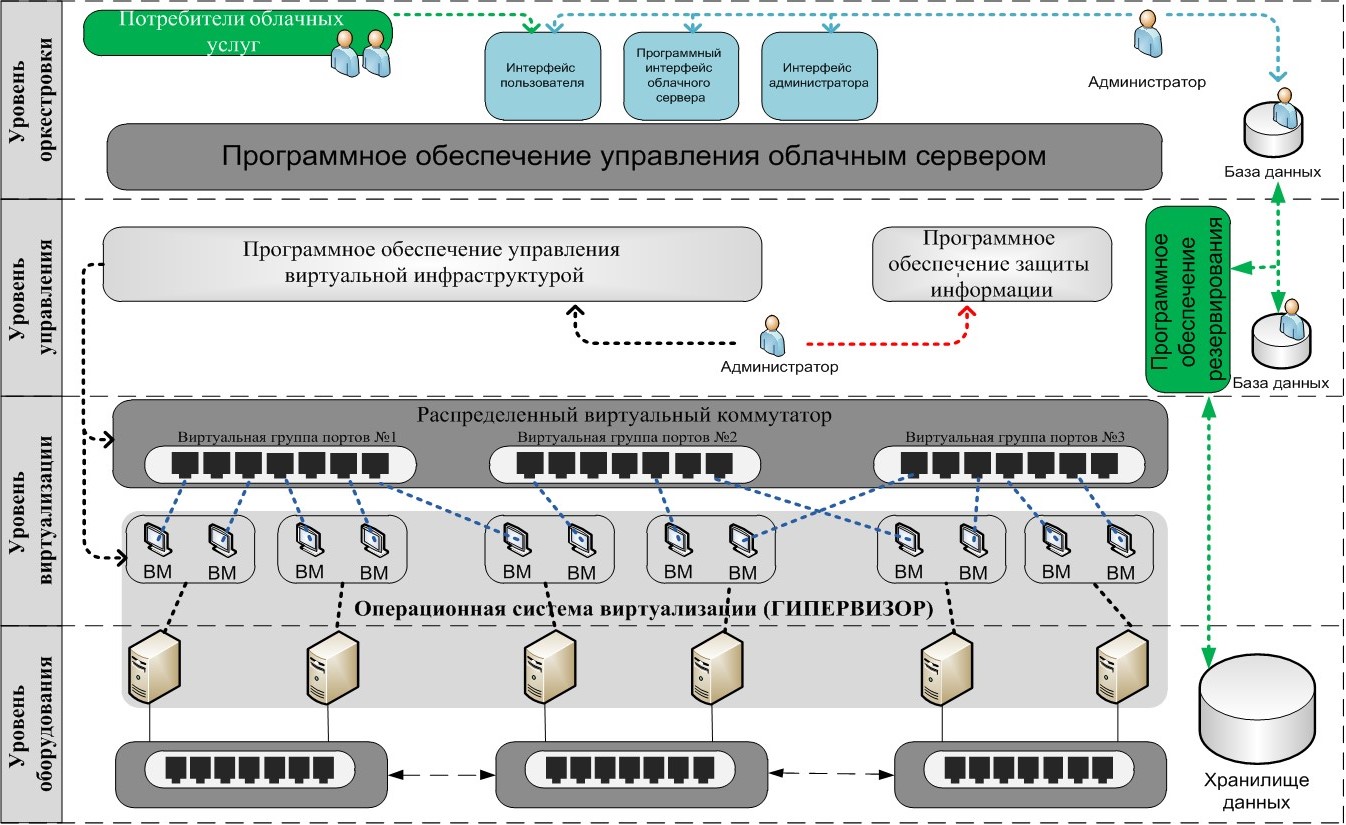
Infrastructure of a typical information system built using cloud technologies (larger image by reference ).
Threats
In the draft GOST, all threats are divided into two large sections:
- threats to consumers of cloud services;
- threats to cloud providers.
Threats are similar for all parties to the interaction, but it should be noted that the number of threats to suppliers has been allocated much more. As I see it, some of the threats, although classified as threats to suppliers, also pose a threat to consumers. So, the assignment of threats to a particular group is very conditional.
Threats to consumers of cloud services are identified as follows:
- threat of uncertainty of liability;
- threat of loss of control;
- threat of loss of confidence;
- threat of being tied to a cloud service provider;
- the threat of unprotected access by consumers of cloud services;
- threat of lack of information / cloud management;
- threat of data loss and leakage.
Threats to cloud providers:
- threat of uncertainty in the distribution of responsibility;
- threat of inconsistent security policies;
- the threat of continuous modernization;
- the threat of suspension of services due to technical failures;
- the threat of the inability to migrate virtual machine images due to incompatibility of hardware and software;
- threat of licensing policies;
- threat of conflict of jurisdictions of various countries;
- the threat of poor infrastructure transfer to the cloud;
- threat of insecure administration of cloud services;
- threat to the public availability of infrastructure;
- threat of using virtualization technologies;
- threat to cloud server availability;
- threat of unfair performance of obligations by cloud service providers;
- threat of abuse by cloud service providers;
- the threat of abuse by consumers of cloud services.
Also, all threats are summarized in a summary plate, in which threats are divided not only for suppliers and consumers, but also depending on the provided cloud service.
A generalized diagram of the dependence of the presence of threats on the provided cloud services
Threats | Cloud service | |||||||||||||||||
H | S | B | D | I | S | C | P | N | S | T | W | |||||||
Security Threats for Cloud Consumers | ||||||||||||||||||
Threat of liability uncertainty | + | + | + | + | + |
| + | + | + | + | + | + | ||||||
Threat of loss of control | + | + | + | + | + | + |
| + |
| + |
| + | ||||||
The threat of loss of confidence | + | + | + | + | + | + | + | + | + | + |
| + | ||||||
Cloud Service Provider Threat | + | + | + | + | + | + |
| + | + | + |
| + | ||||||
The threat of unprotected access by consumers of cloud services | + | + | + | + | + |
| + | + | + | + |
| + | ||||||
Threat of Lack of Information / Cloud Management | + | + | + | + | + | + | + | + | + | + | + | + | ||||||
Threat of data loss and leakage |
| + | + | + |
|
|
|
|
| + | + | + | ||||||
Security Threats for Cloud Service Providers | ||||||||||||||||||
The threat of uncertainty in the distribution of responsibility | + | + | + | + | + | + | + | + | + | + | + | + | ||||||
Threat to inconsistent security policies | + | + | + | + | + | + |
| + | + | + | + | + | ||||||
The threat of continuous modernization | + | + | + | + | + | + |
| + | + | + |
| + | ||||||
The threat of suspension of services due to technical failures | + | + | + | + | + | + | + | + | + | + | + | + | ||||||
Threat of inability to migrate VM images due to hardware and software incompatibility | + |
| + | + | + |
|
| + |
| + |
| + | ||||||
Threat to licensing policies |
| + | + | + | + | + |
| + |
| + | + | + | ||||||
Threat of conflict of jurisdictions of different countries | + | + | + | + | + | + | + | + | + | + | + | + | ||||||
The threat of poor infrastructure transfer to the cloud |
|
|
|
|
|
|
|
|
|
| + |
| ||||||
Threat of insecure administration of cloud services | + | + | + | + | + | + | + | + | + | + | + | + | ||||||
Infrastructure Access Threat | + |
| + | + | + | + | + | + |
| + |
| + | ||||||
The threat of virtualization technology | + | + | + |
| + |
|
| + |
| + |
| + | ||||||
Cloud server availability threat |
|
|
| + | + | + |
| + |
| + |
|
| ||||||
The threat of malpractice by cloud service providers |
| + | + | + |
| + | + | + | + | + | + | + | ||||||
Threat of Abuse by Cloud Service Providers | + | + | + | + | + | + | + | + | + | + | + | + | ||||||
Cloud Abuse Threats | + |
|
|
| + |
|
| + |
|
|
| + | ||||||
Protection requirements
The sixth section of the GOST project is fully devoted to the requirements for the protection of information in the provision of cloud services, depending on the type of service. As an example, we list the measures for a service (IaaS), because the measures are generally identical and it is not practical to list them for each of the services under this article.
Ensuring the security of information in the provision of infrastructure as a service requires particular attention to the protection of hardware and virtual data processing devices, as well as communication channels. The following measures should be aimed at this:
- measures for identification and authentication of access subjects and access objects;
- measures to control the access of access subjects to access objects;
- measures to limit the software environment;
- measures to protect machine storage media;
- measures to remove residual information;
- меры по регистрации событий безопасности;
- меры по криптографической защите хранимой и передаваемой информации;
- меры по антивирусной защите;
- меры по обнаружению (предотвращению) вторжений;
- меры по контролю (анализу) защищённости информации;
- меры по обеспечению целостности ПО ИС и информации;
- меры по обеспечению доступности информации;
- меры по защите облачного сервера, его средств и систем связи и передачи данных;
- меры по межсетевому экранированию;
- меры по централизованному управлению.
В заключение
Looking at our previous article “Information Security Using Virtualization Technologies”, you can see that most of the requirements are identical, since the cloud infrastructure is implemented through virtualization technology. All the more surprising is the fact that if we compare the GOST for the protection of virtualization and the GOST project for the protection of clouds, you can see the difference in the conceptual apparatus and the terms used . Given that when using cloud technologies with a high degree of probability it is necessary to apply both documents, this can introduce some confusion.
Draft standard is under developmentfor about five years, amendments have been made to it, and when we see the approved edition, it is not clear. Nevertheless, now it can be used as a source of information when planning a secure cloud infrastructure. Also, do not forget about the standards that are given in the draft GOST and with which it was developed.
PS Here you can download our White Paper on Federal Law No. 152 .
This is a book that was published in order to help eliminate confusion regarding the processing of personal data and clearly describe the process of bringing personal information IP in accordance with Russian law.
