Miners replace cryptographers
At Solar JSOC, we continuously collect data on events and incidents of information security in customer infrastructures. Based on this information, we do an analysis every six months that demonstrates how attacks on Russian organizations are changing. Today we have collected for you the most interesting trends of the second half of 2017.

So, for starters, a bit of general statistics, and then we will consider threats and attack vectors in more detail.
In total, in the second half of 2017, the flow of IS events amounted to about 8.243 billion (6.156 billion in the first half of the year). Of these, about 1,270 per day (231,623 in half a year) are events with suspected incident that needed to be considered by an analytical engineer.
Approximately every sixthThe incident was classified as critical. In our terminology, critical events include incidents that potentially lead to financial losses worth more than 1 million rubles, compromise of confidential information or stop critical business systems.
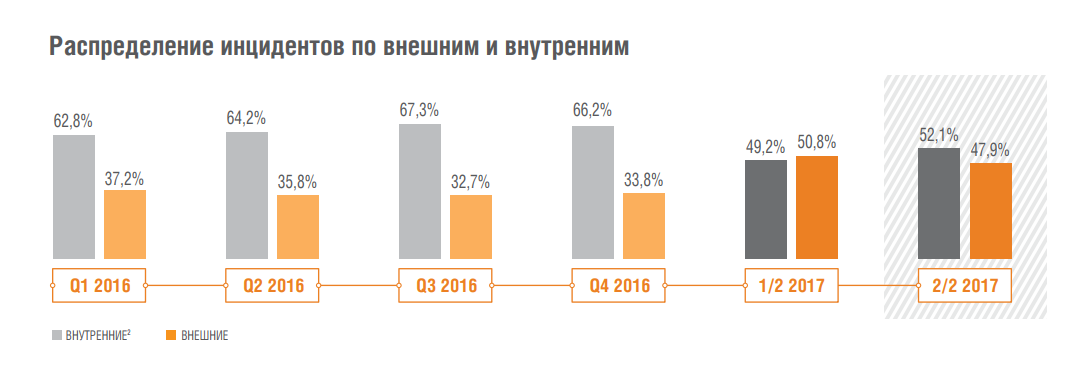
This time we compared the performance of all key metrics over 4 years, and in some places it gave interesting results. For example, it turned out that every year the share of critical incidents is steadily growing. If in the first half of 2015 this indicator was 8.1%, then in the second half of 2017 it was already 15.5% (with an increase in the number of customers).
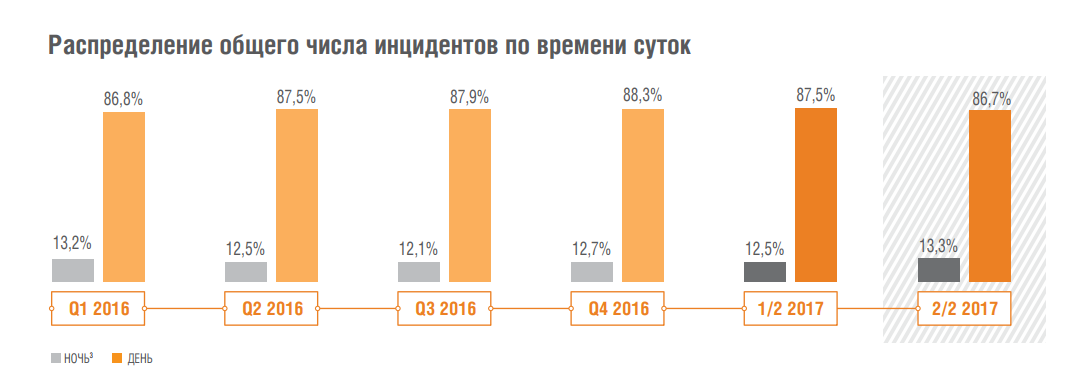
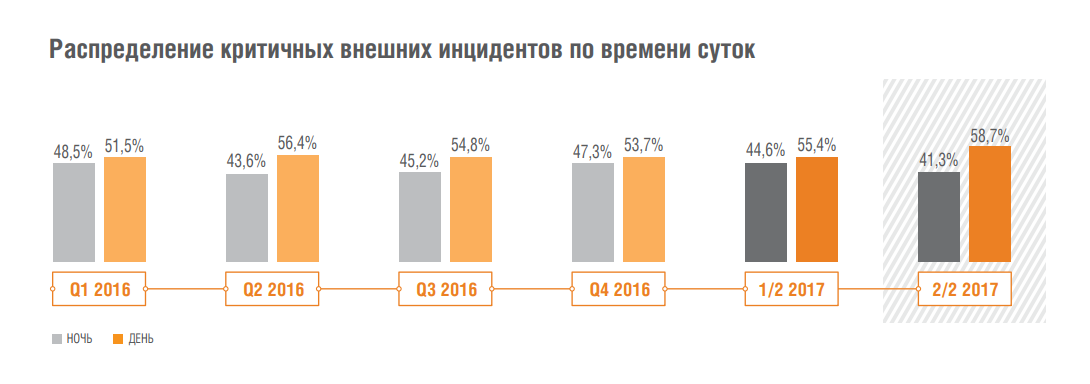
Most of the incidents (86.7%) occurred during the day, however, if we talk about critical external incidents, then in 58.7% of cases they occurred at night. This is the highest rate in the last four years.
This phenomenon is understandable: with a high probability the night incident is not immediately detected, and cybercriminals will have more time to fix themselves in the infrastructure or even to penetrate into the target segments, which allow to monetize the attack.
Separately, we consider the incidents that make up the Kill Chain - a chain of sequential cybercriminal actions aimed at hacking infrastructure and compromising key company resources. The classic and most common Kill Chain scheme looks like this:

It would seem that ordinary users are constantly told about the threats emanating from the Web. However, social engineering is still amazingly effective. In the second half of 2017, in 65% of cases, it was it that was used to penetrate the company's infrastructure. Moreover, in the first half of the year, this figure was 54%. Users opened malicious attachments and clicked on phishing links, thereby downloading malware that served the purpose of cybercriminals.
Speaking of malware, we can note that the number of infections with cryptographic viruses has decreased by about a third compared to the first half of 2017. But their place was quickly taken by miner viruses.
It is curious that in relation to mining software, a certain industry specificity is traced. So, in banks, they are most often found on workstations that have been infected through mail or infected sites and, as a rule, as part of malware packages.
Outside the financial sector, the situation is different: on average, in every third organization we record incidents when miners on the server hardware of the company are installed directly by IT department employees.
In general, external attackers most often attack the organization’s web applications (32.3%), in 22.8% they resort to brute-force and compromise the credentials of external client services, in another 22.1% of cases they try to introduce malware into the organization BY.

Incidents related to the actions of internal attackers were distributed as follows: confidential data leakage - 48.2%, internal account compromise - 22.6%, violation of Internet access policies - 8.2%. Note that leaks are almost half of all internal incidents. Apparently, the desire to increase its value in the eyes of other potential employers is often irresistible.
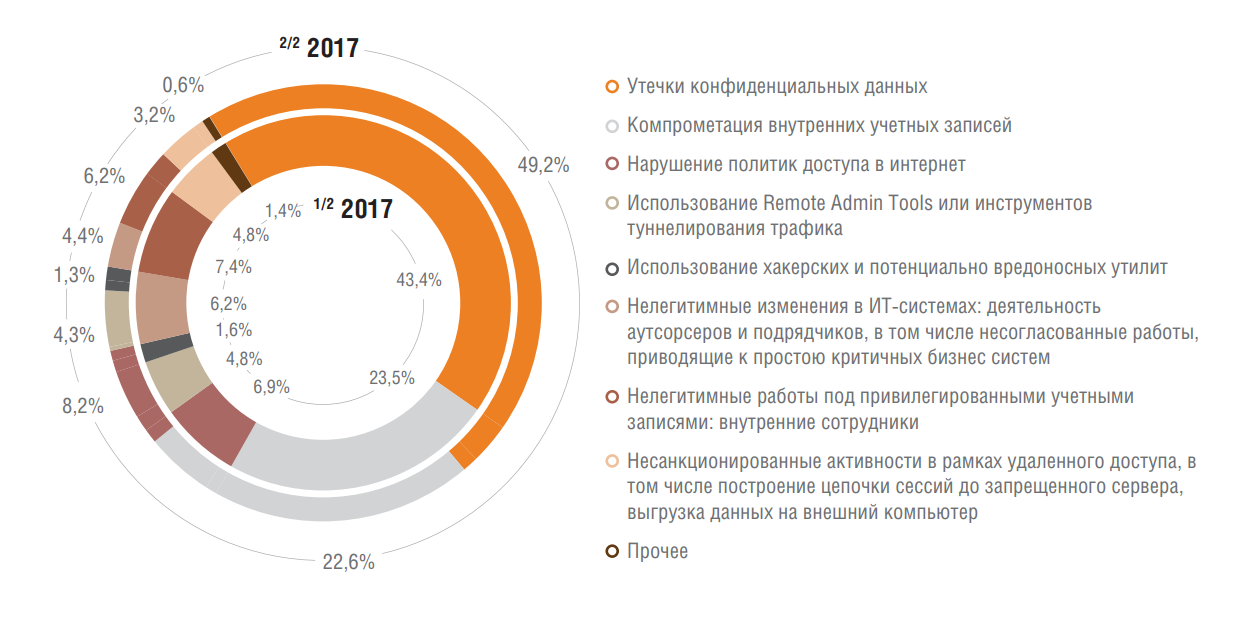
In the second half of 2017, the number of incidents caused by IT administrators of the companies increased significantly (from 25.6% to 31.3%). This includes leaks of confidential information and non-compliance with information security policies by the IT department. It can be assumed that such numbers are associated with poor control over these employees (or the ability of IT professionals to circumvent technical security measures).

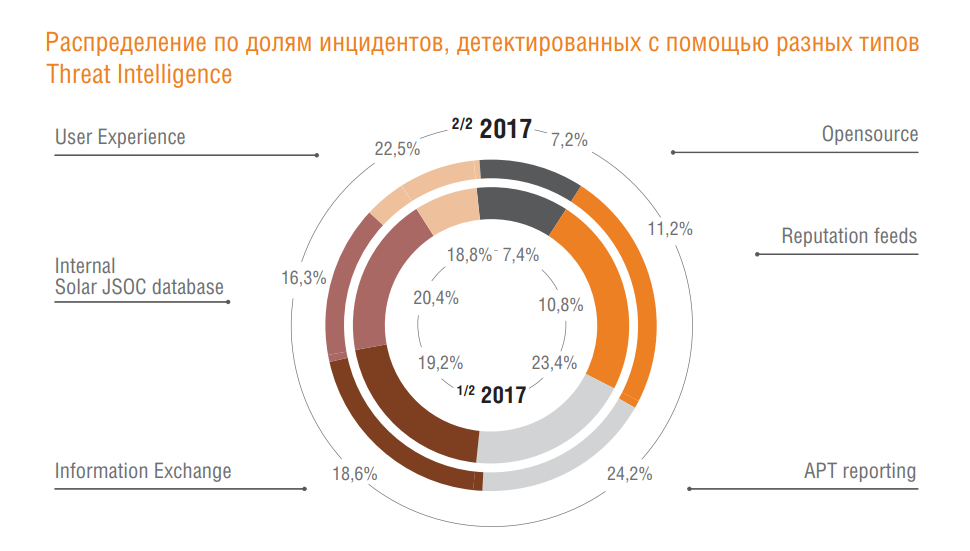
In addition, some time ago we talked about how to properly build the process of using external sources of threat data. Here are the types of Threat Intelligence we use ourselves:
And here are some of them that were most useful in the second half of 2017:

So, for starters, a bit of general statistics, and then we will consider threats and attack vectors in more detail.
In total, in the second half of 2017, the flow of IS events amounted to about 8.243 billion (6.156 billion in the first half of the year). Of these, about 1,270 per day (231,623 in half a year) are events with suspected incident that needed to be considered by an analytical engineer.
Approximately every sixthThe incident was classified as critical. In our terminology, critical events include incidents that potentially lead to financial losses worth more than 1 million rubles, compromise of confidential information or stop critical business systems.
This time we compared the performance of all key metrics over 4 years, and in some places it gave interesting results. For example, it turned out that every year the share of critical incidents is steadily growing. If in the first half of 2015 this indicator was 8.1%, then in the second half of 2017 it was already 15.5% (with an increase in the number of customers).
The number of attacks on companies since 2014 increased by an average of 26%.

Most of the incidents (86.7%) occurred during the day, however, if we talk about critical external incidents, then in 58.7% of cases they occurred at night. This is the highest rate in the last four years.


This phenomenon is understandable: with a high probability the night incident is not immediately detected, and cybercriminals will have more time to fix themselves in the infrastructure or even to penetrate into the target segments, which allow to monetize the attack.
Kill chain
Separately, we consider the incidents that make up the Kill Chain - a chain of sequential cybercriminal actions aimed at hacking infrastructure and compromising key company resources. The classic and most common Kill Chain scheme looks like this:

It would seem that ordinary users are constantly told about the threats emanating from the Web. However, social engineering is still amazingly effective. In the second half of 2017, in 65% of cases, it was it that was used to penetrate the company's infrastructure. Moreover, in the first half of the year, this figure was 54%. Users opened malicious attachments and clicked on phishing links, thereby downloading malware that served the purpose of cybercriminals.
Speaking of malware, we can note that the number of infections with cryptographic viruses has decreased by about a third compared to the first half of 2017. But their place was quickly taken by miner viruses.
It is curious that in relation to mining software, a certain industry specificity is traced. So, in banks, they are most often found on workstations that have been infected through mail or infected sites and, as a rule, as part of malware packages.
Outside the financial sector, the situation is different: on average, in every third organization we record incidents when miners on the server hardware of the company are installed directly by IT department employees.
In general, external attackers most often attack the organization’s web applications (32.3%), in 22.8% they resort to brute-force and compromise the credentials of external client services, in another 22.1% of cases they try to introduce malware into the organization BY.

Incidents related to the actions of internal attackers were distributed as follows: confidential data leakage - 48.2%, internal account compromise - 22.6%, violation of Internet access policies - 8.2%. Note that leaks are almost half of all internal incidents. Apparently, the desire to increase its value in the eyes of other potential employers is often irresistible.

In the second half of 2017, the number of incidents caused by IT administrators of the companies increased significantly (from 25.6% to 31.3%). This includes leaks of confidential information and non-compliance with information security policies by the IT department. It can be assumed that such numbers are associated with poor control over these employees (or the ability of IT professionals to circumvent technical security measures).

In addition, some time ago we talked about how to properly build the process of using external sources of threat data. Here are the types of Threat Intelligence we use ourselves:
- Opensource - open databases of malware indicators, management servers and phishing links. As a rule, in the context of detection using SIEM platforms, only network indicators are relevant.
- Reputation feeds - Paid subscriptions to reputation lists of malware, management servers, and phishing links. As a rule, in the context of detection using SIEM platforms, only network indicators are relevant.
- APT / IOC reporting - paid subscriptions to detailed descriptions of 0day malware, including, among other things, a description of vulnerabilities used and host indicators of malware.
- Information Exchange - information obtained through information exchanges with state, departmental and foreign incident response centers (CERT).
- Internal Solar JSOC database - indicators obtained as a result of Solar JSOC's own research or incident investigations.
- User experience - information obtained directly from customer users (successful counteraction to social engineering, detection of phishing mailings, etc.).
And here are some of them that were most useful in the second half of 2017:

