Bitcoin Software Wallets and Security

Let's talk a bit about cryptocurrency wallets. By “cryptocurrency,” I will primarily mean Bitcoin. In other cryptocurrencies, the situation is similar and if you are interested in the details, then you can dig yourself.
Despite the ongoing hype around cryptocurrencies and blockchain as technology, in my opinion, very few people talk about the security of these solutions. Everyone concentrates on the various advantages that blockchain technology provides, discuss mining and jumps in cryptocurrency rates, while security is critical, especially when it comes to money or distributed property registries. All information for the article is taken from open sources, such as https://bitcoin.org , https://en.bitcoin.it/wiki ,https://bitcointalk.org , https://github.com and others.
Below is a shallow overview of cryptocurrency wallets and their security. The more I plunged into this topic when writing an article, the more I was surprised that so few hacks and withdrawals of funds from users of the same Bitcoin took place in the world. But first things first.
What is a cryptocurrency wallet?
Let's deal with a little terminology. Cryptocurrency wallets mean at the same time:
- a set of keys for accessing money;
- Programs that manage these keys and allow you to conduct transactions on the cryptocurrency network.
In order not to get confused when we talk about a set of keys, I will use the term “private key”. Although we all understand that there is also an open one in the key pair, as well as the fact that there can be several pairs themselves.
We will talk about the wallet precisely as a means of managing, storing and conducting transactions. Without a wallet, you cannot receive, save or spend your bitcoins or funds in another cryptocurrency. Wallet - your personal interface to the cryptocurrency network, similar to a bank account for fiat currency.
In fact, the security of storing your funds in cryptocurrency very much depends on the wallet you use. And the security of the wallet itself is largely based on the security of private key transactions.
All wallets are divided into “hot” and “cold”. “Hot” is a cryptocurrency wallet, funds from which can be spent at any time. A "cold" wallet works in exactly the opposite way. It is not intended for the regular sending of cryptocurrencies, but nonetheless, funds for it can be received at any time. The simplest “cold” wallet is a piece of paper on which the private key to your wallet is written.
A Bitcoin Hot Wallet is an application, website, or device that manages your private keys. The most popular are, of course, applications, both mobile and desktop, as well as websites. Let's dwell on each of these types in a little more detail and see what threats the use of this or that wallet is fraught with.
Since there are so many wallets, I decided to study only those that are presented on the site https://bitcoin.org/ . The following are presented as software wallets for a personal computer:

Wallets Requirements
The first thing we pay attention to is the recommendations of the bitcoin.org website regarding the security of using a particular wallet. When downloading, you will be shown 6 requirements and information about which requirements are met by each of these wallets and which are not. Most of these requirements are directly or indirectly related to information security, and therefore to the security of your funds.
These are the requirements, as well as the levels of compliance with these requirements.
Control over your money
- Full control. No one will be able to freeze your account or lose your money. However, you must remember that the responsibility for security and backing up your private key lies entirely with you.
- Joint control. A wallet requires that each transaction be authorized by both you and a third party. Usually, you can regain full control of your funds using the initial backup or pre-signed transaction sent by email.
- Hosting Control A wallet gives you access to your funds. However, it stores an encrypted copy of your private key. So your funds can be stolen if you do not use a strong password or if the service is compromised.
- Money is controlled by a third party. This means that you must trust this service, and hope that it does not lose your funds as a result of the incident on its side. At the moment, most online wallets do not insure deposits like a bank, and many services in the past had security problems.
Once again, I note that this information is not hidden, but is available to everyone. Even the Russian translation is, although not entirely correct in some places.
So, I don’t know about you, but I don’t like the last two levels of control at all. The story of a strong password sounds generally very bad. And the point here is not even that users have big problems with creating, entering and remembering really strong passwords, but that key loggers have not gone away.
And to be completely realistic, it is unlikely that anyone reads these warnings. And even if he reads, by no means everyone understands how many security problems there are.
Transaction Check
- Complete. A wallet is a full node that checks the validity and conducts operations on the network. When checking payments, trust in a third party is not required. Valuable nodes provide the highest level of security and are important for network security. However, they require more disk space (over 145 GB), bandwidth and more time for initial synchronization.
- Simplified or decentralized. The wallet uses a random server from the server list. This means that you must trust these servers when checking payments. This is not as safe as using a wallet, which is a complete node.
- Centralized. The wallet relies on a centralized server by default. So, you must 100% trust this third party in matters of concealment or falsification of payments.
The use of full nodes by all network participants, in my opinion, is simultaneously one of the pillars and, at the same time, one of the main disadvantages of blockchain technology. Since the number of transactions in both relative and absolute values is constantly growing, the size of the wallet itself will also constantly grow. And few people want to store several TB of data for a couple of transactions per day.
Alternative solutions have obvious security concerns. The list of servers, in the case of a decentralized check, must be well protected. And then, as if the next virus did not leave only one infected server in this list.
And I don’t even want to talk about absolute trust in a third party.
By the way, supporters of cryptocurrencies love in this case to pay attention to the fact that the banking system is structured in a similar way. It certainly is. But banks are regulated by numerous standards, and if a new problem / vulnerability arises, then your funds will be protected by insurance. Therefore, cryptocurrency services still have room to grow.
Transparency
- Full transparency. The wallet source codes are open, and the assembly procedure is fixed. Any developer in the world can audit the code and make sure that the executable code does not hide any secrets.
- Basic transparency. The developers have published the source code of the wallet. Any developer in the world can audit the code. However, you must trust the developers when installing or updating your wallet software.
- Remote application. The wallet is loaded from a remote service. So, when you use the wallet, you must trust the developers in matters of theft or loss of your funds as a result of the incident. Using an extension for a browser or mobile application can reduce these risks.
Source codes are generally a sore point. Since this topic is very close to the Habr audience, let's dwell on it in more detail.
Most of all I like the phrase “Any developer in the world can audit the code." Yeah, well. Firstly, the developer must have a good knowledge of the specific programming language in which the particular wallet is written. And this immediately cuts off a large chunk from "any developer in the world."
Secondly, not every developer is at the same time an information security specialist or has experience writing secure code. I will give a banal example:
memset(password, 0, sizeof(password))Open articles from PVS-studio developers and remember what mistakes developers sometimes make. And even those developers who are well versed in security issues (for example, A boring article about checking OpenSSL ).
Therefore, a very limited number of developers can do a full audit of all wallet code. Most of which already have a bunch of interesting tasks, in addition to this audit. Even if one of them is interested in this task, then it will be executed only for a specific commit in git. This means that evaluating code security at a particular point in time is not easy.
What did the guys from the Bitcoin website mean by the fixed assembly procedure could not be precisely understood. There are problems with the assembly. For example, how to understand that the assembly or update you received is built from the correct source code. Let's be realistic - there will be one unit to collect a wallet from source codes. The best thing you can do is check the hash from a freshly downloaded installer with the hash listed on the official website. And he hopes that the site was not compromised and the correct hash lies there, and also trust the developers and collectors of the wallet, as well as the site administrators.
In order to completely finish off the question about the source codes, I decided to take a look at the source codes of Bitcoin Core, which, according to all the indicators that have already been described and those described below, occupies a leading position. For code examples and conclusions that I have drawn by looking briefly at the source, see below.
Transparency Bonus
There is another interesting aspect that I discovered quite by accident. Let's say you decide to use a Bitcoin Armory wallet that modestly positions itself as a BEST BITCOIN WALLET. In the description you will find - “Armory is the most secure and full featured solution available for users and institutions to generate and store Bitcoin private keys”. Having scored the name of the wallet on Google, you will find that the wallet has 2 sites. The first https://www.bitcoinarmory.com is commercial with beautiful words in the top of the list. The second https://btcarmory.com is more technical, a link from https://bitcoin.org/ will lead you to it .
So, on the technical site, on the main page in the news, you will find a warning:
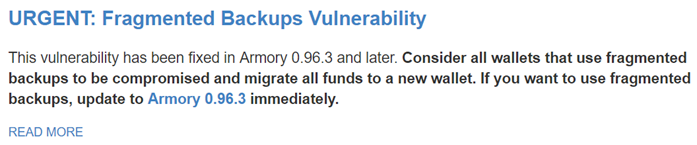
A commercial site doesn’t write such nonsense =) You don’t have to worry about such stupid reasons.
Environmental safety
- Two-factor authentication. Wallet can be downloaded in an insecure environment. However, the service requires two-factor authentication. So, to steal your funds you need access to multiple devices or accounts.
- Safe environment. The wallet runs on a mobile device, where applications are usually isolated. This provides good malware protection, although mobile devices are more likely to get lost or be stolen. Mobile device encryption and wallet backup can reduce this risk.
- Vulnerable environment. The wallet can be downloaded to computers that are potentially vulnerable to malware. If you increase the security of your computer using a complex password, transfer most of your funds to offline storage or activate two-factor authentication, then your bitcoins will be more difficult to steal.
I like the terms in which these requirements are described. It looks like the developers decided to give you a hint right away that your funds will be stolen for sure. The only question is how much effort and time it will require =)
Let us also dwell here in a little more detail.
The use of strong two-factor authentication can really help solve many problems with information security.
The key word here is “reliable.” And also correctly implemented. And with this, everything is not always good. For example, blockchain.info will offer you good old SMS as a second factor. Nobody is interested in the same NIST recommendations in Special Publication 800-63B:
- [Out of band verification] using SMS is deprecated, and will no longer be allowed in future releases of this guidance.
We will talk more about the correct two-factor authentication in the next article, in which we will take a closer look at hardware wallets for cryptocurrencies.
We will not dwell on the security of computers and mobile devices. It is enough to read any of the reports from Kaspersky Lab or other serious players in the security market to draw conclusions on your own.
The following two points are not directly related to the security of storage of your funds. Therefore, I will not dwell on them in detail, but I will bring them here to complete the picture.
Confidentiality
- Superior. A wallet makes it difficult to keep track of your balances and payments by rotating the addresses used. You should use a new bitcoin address every time you request a payment. When receiving or sending payments, the wallet does not transfer information about them to other network nodes. The wallet allows you to configure and use Tor as a proxy in order to prevent attackers or Internet providers from associating your payments with your IP address.
- Basic. A wallet makes it difficult to keep track of your balances and payments by rotating the addresses used. You should use a new bitcoin address every time you request a payment. The wallet uses central servers that can bind your payments together and remember your IP address. The wallet allows you to configure and use Tor as a proxy in order to prevent attackers or Internet providers from associating your payments with your IP address.
- Weak A wallet allows anyone to keep track of your balance and payments, because it reuses the same addresses. Discloses limited information to other participants. Other hosts can remember your IP address and subsequently link all the payments you received or sent. Tor is not supported.
Even if you use cryptocurrency completely legally (although what is legal with respect to cryptocurrency is a big question), then additional privacy will not hurt you. And no one wants to disclose their balance and expenses. Your KO.
Commission
- Full control over the commission. The wallet will allow you to change the commission after sending funds using RBF or CPFP. This wallet also gives recommendations on the commission, depending on the current state of the network to conduct the transaction on time and without overpayments.
- Dynamic commissions. The wallet gives recommendations on the commission depending on the current state of the network, which you can override. This means that the wallet will help you in choosing the appropriate commission for conducting the transaction on time without overpayment, but at the same time gives you complete control for setting the commission if you want.
- Static commissions. The wallet does not give any offers on the commission, given the current state of the network. This means that your transactions may take longer if you select too low a commission or you can pay too high a commission.
To summarize
All the requirements sound very reasonable. Moreover, this list could be further expanded to increase security.
Having carefully studied all these requirements, you want to find a wallet that would satisfy them to the maximum. And here comes the fun part. At https://bitcoin.org there is not a single wallet that would satisfy all the requirements.
In the best case, you can choose Bitcoin Core or Bitcoin Knots, for which there will be such a picture:

Or you will use Electrum, for which such a picture:
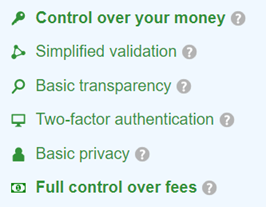
Using green creates a false impression of full satisfaction. Full compliance - bold green. This design was clearly chosen intentionally, which means that the creators of the portal decided to slightly manipulate a regular user. This is not good.
This could have been finished. I think everyone has already imagined how securely private keys are stored in cryptocurrency wallets. But we on Habré.

Work with private keys on the example of Bitcoin Core
Let's go a little further and see how the storage and work with private keys takes place using the example of software clients. As we already found out, malware can gain access to the private keys of your wallet. The question is how easy or hard it really is.
First, let's see how Bitcoin Core does it. This process is well described in the wiki of Bitcoin itself. As you saw in the screenshot above, this client is marked as one of the most advanced and satisfying most requirements.
The private keys of your wallet are stored along with other information in the wallet.dat file in the “bitkeys” format. This file maybe encrypted, but may not be =) By default, of course, nothing is encrypted. You are a competent user and you will find the right button. Only private key information is encrypted using the AES-256-CBC algorithm . Moreover, the so-called master key is used as an encryption key - a random number. In this case, the master key itself is encrypted on the key obtained from the passphrase using SHA-512 and the OpenSSL function EVP_BytesToKey. The number of rounds of encryption is determined by the speed of the computer at which the initial encryption takes place.
After that, your wallet is used by the client as usual. This condition is called “locked”. If at some point, you need to access the wallet’s private keys, then you need to enter the passphrase in the client’s GUI or use the command
walletpassphrase in RPC. In this case, the private keys will be decrypted and the wallet will go into the “unlocked” state. In the first case, he will be in this state exactly as much as necessary for the implementation of a particular operation. In the second case, the time after which the wallet will return to the locked state is determined by the second parameter in the RPC request! The code looks like this:
int64_t nSleepTime = request.params[1].get_int64();
pwallet->nRelockTime = GetTime() + nSleepTime;
RPCRunLater(strprintf("lockwallet(%s)", pwallet->GetName()), boost::bind(LockWallet, pwallet), nSleepTime);It looks very cute. A regular wallet user is unlikely to start a server at home, unless it misses a file. But the attacker ...
With the GUI and storing the same passphrase in memory, everything is also not very simple. The guys implemented a special class for storing such data - SecureString. Implemented, in general, not bad, a rake using memset successfully bypassed. But they keep it in memory longer than it should.
For example, our GUI does this (slightly corrected for clarity, it is interesting to look at askpassphrasedialog.cpp: 154):
case Unlock:
if(!model->setWalletLocked(false, passphrase))
{
QMessageBox::critical(this, tr("Wallet unlock failed"),
tr("The passphrase entered for the wallet decryption was incorrect."));
}
else
{
QDialog::accept(); // Success
}
break;
}
return;At the beginning we will do accept (), and only then our oldpass will go out of scope and cleanup will happen. It is clear that a more secure code will turn out not as beautiful as a less secure one. But are we kind of working with money here?
In my opinion, this perfectly confirms my fear about the open source of the wallet. Open source is not equal to security.
PS
I will try to anticipate the first comments and immediately answer them:
- Yes, you can draw up a certain set of rules for using a crypto wallet, which will significantly increase the level of security of your funds. Ease of use will certainly suffer greatly.
- Yes, there are customers who are significantly safer than others. The problem is that the rest also exist and are recommended by the official site.
The purpose of the article is to draw the attention of the community to problems that need to be addressed, and not to set someone up against new technologies.
I have nothing against cryptocurrencies or blockchain technology. On the contrary, I am for it with all my hands (this is my personal opinion, which in no way is the official position of the company whose blog the article is posted on). But since we are starting to work with new technology, we must do it technically competently and not forget about information security.
