Malefactors learned to bypass two-factor authentication of Yahoo Mail and Gmail
Recently, information security specialists from the company Cerfta Lab have published the results of a study of a number of hacking user accounts for Yahoo Mail and Gmail. As it turned out, the two-factor authentication technology used by these services has several disadvantages that allow attackers to act.
The authors of the investigation believe that the hacks were carried out by order of the Iranian government. The goal of the whole campaign was information of hacked accounts. The attack was carried out using an e-mail with a hidden image and a script.
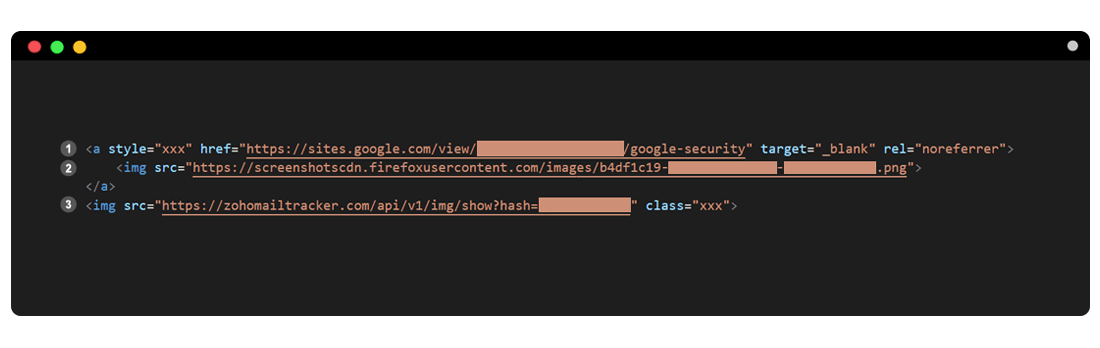
The letter itself was a message about allegedly detected suspicious activity in the user account of the mentioned mail services. These e-mails were sent from addresses like mailservices @ gmail [.] Com, noreply.customermails@gmail [.] Com, customer] email-delivery [.] Info. Therefore, for not very advanced users, these messages were not suspicious.
On the contrary, many sought to click on the button “protect account”, which threw the user to the fake login page of the mail service. When the user entered his data, the attackers used it almost in real time to access the real account. A user who has enabled two-factor authentication received an SMS with a one-time password on the phone, the attackers somehow got the opportunity to log into the account. They learned to bypass Google Authenticator protection.
The researchers drew up a diagram of the used domains and servers that are associated with them.
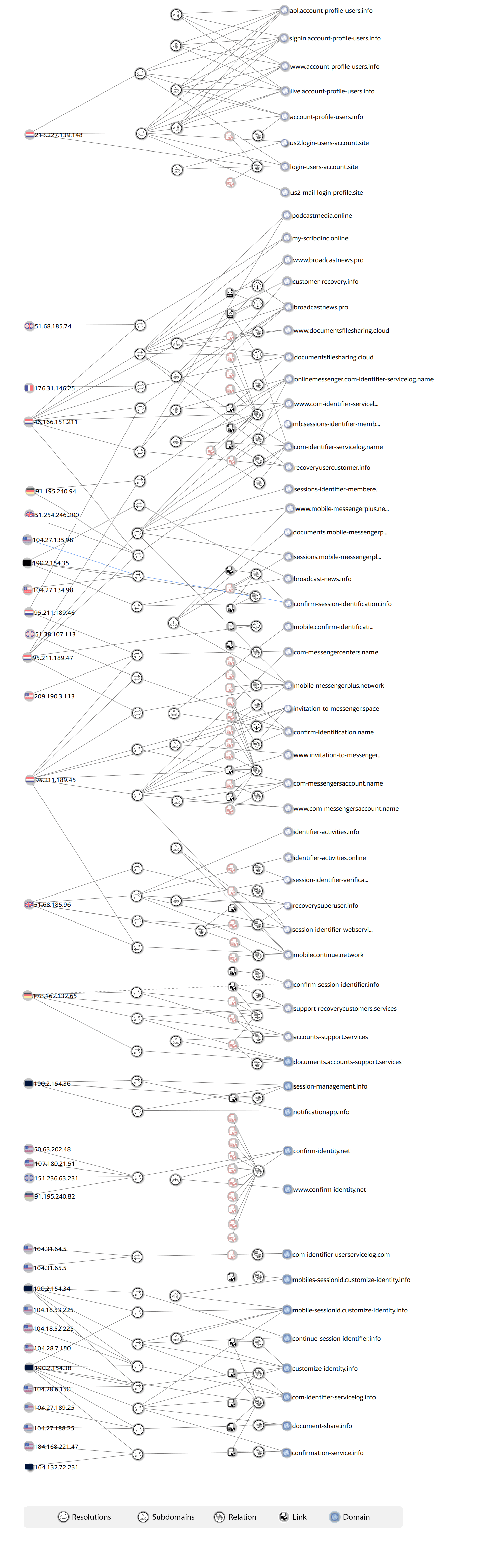
The attackers used a VPN system and a proxy in order to hide their location. But the researchers managed to restore the original IP range from which the attack was carried out. These were Iranian addresses. In addition, similar working methods have been used and are being used by the Charming Kitten hacker group, which is associated with the Iranian government.
The victims, which the attackers were hunting, were, first of all, journalists, politicians, all sorts of social activists from many countries of the world.
It is clear that the main way to protect against attacks of this kind is simply not to open a suspicious e-mail. Unfortunately, this method does not always work, because many people do not see anything suspicious in a letter compiled supposedly by Google or Yahoo. Situations can be helped by the use of hardware keys (for example, YubiKey), which allow authentication by connecting a USB device to the port.
Google conducted a study, the results of which unequivocally indicate that USB keys are much more reliable than smartphones or other systems that can be used for two-factor authentication.
Information security specialists also recommend not to use two-factor authentication with sending SMS as one of the security components.
