Targeted attacks on Polish banks: technical analysis
On the Polish cybersecurity portal ZaufanaTrzeciaStrona.pl, the news about successful attacks on Polish banks appeared recently (the English version is here ). The incident was described as "serious." Data confirmed by Symantec and BAE Systems . Institutions from Mexico and Uruguay joined the list of victims, as well as other targets around the world.
These attacks have a lot of interesting things, from targets and infection vectors to the characteristics of malicious executable files. If the first two aspects have already been studied, then the malicious code has not been investigated in detail. In this post we will conduct a technical analysis of the malware.
Distribution channel
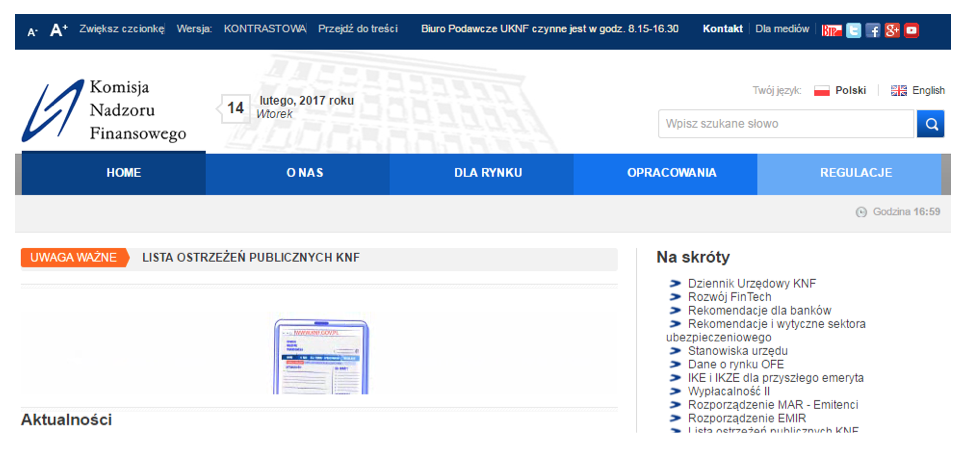
According to ZaufanaTrzeciaStrona.pl, hackers carried out a series of attacks such as the watering hole - infecting sites that potential victims visit. A compromised site redirects the user to an infected exploit page. In Poland, the starting point was the official website of the Financial Supervisory Commission (Komisji Nadzoru Finansowego).
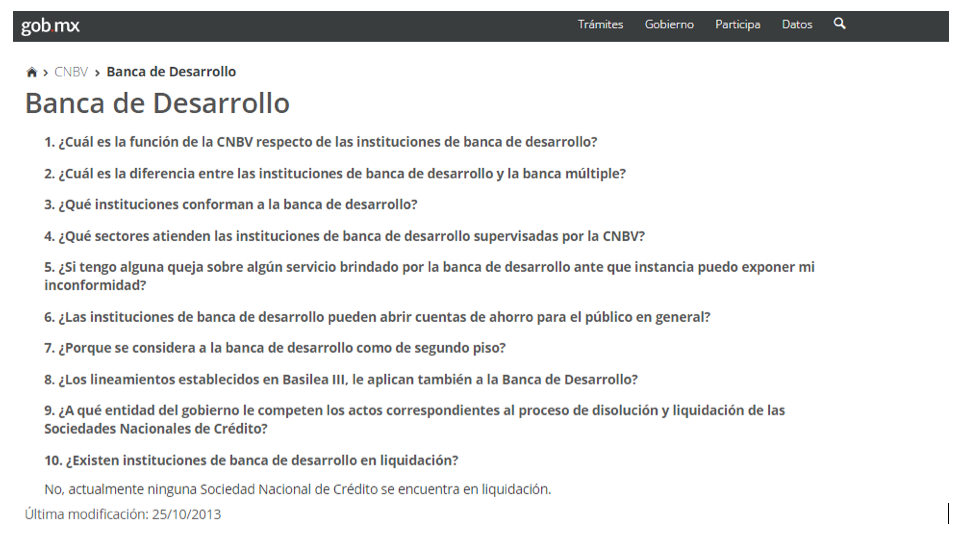
According to our data, in Mexico the website of a similar agency (National Commission for the Banking System and Securities - Comisión Nacional Bancaria y de Valores) was used for the same purpose. Unfortunately, this information has not yet been confirmed by web tracking services or by the institution itself. However, we assume that the redirect was from this site:
Stage 1: Injection
If the exploit kit successfully delivered the trojan, a malicious load is executed on the victim’s computer - a 64-bit console application. Unlike the injection described by BAE Systems, the program expects one of three arguments: -l, -e, or –a (section 2 in the figure below).
While the -l option has the same meaning, the remaining two are necessary for unpacking the resources of the next step (section 4) and for autostarting one of them as a service (section 5):

In section 5, the injection tries to change the configuration of the system service in order to install the bootloader as a service. The configuration is intended to be automatically launched by the service management manager during system startup. This requires administrator rights.
At the first stage of the attack, the threat does not hide itself as carefully as at the subsequent ones. It even contains a lengthy statement providing information on the execution status (in this case, on the extraction of encrypted resources; however, there is no debugging information, including the names of the original functions).
Injection uses dynamic loading of the API instead of the Windows functions in the import table (more on this in the Novetta Operation Blockbuster report on the Lazarus hacker group, page 34). Section 3 in the image above demonstrates the shell of this function, which starts one system library after another.
It seems that hackers designate the second stage as the “bootloader”, and the third, containing the main functionality of the malware, as the “module”. The bootloader is decrypted, while the module is removed and installed unchanged. For the purpose of disguising, files borrow the creation time from the shlwapi.dll system.
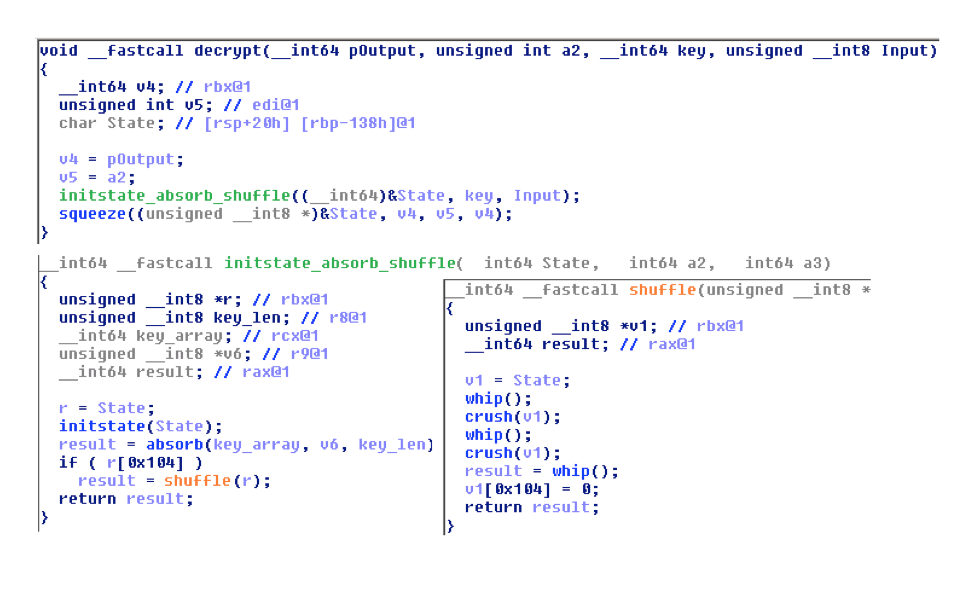
An interesting feature of the encryption algorithm is the relatively new Spritz stream cipher , reminiscent of RC4. The Spritz implementation in the C and Python programming languages is already available, it corresponds to the following unpacked code from the injection:
Stage 2: Loader
The threat hides the presence in the infected system. The bootloader is protected by the Enigma Protector paid utility, the module is stored encrypted. As we expected, hackers use an unregistered copy of the 64-bit Enigma v1.31 - it would be strange to expect a qualified author to make an elementary mistake and jeopardize his identity using an officially registered copy. (On the contrary, the use of hacked or pirated software, if available, is not unusual.) Hackers planning to build a botnet usually do not use commercial archivers, since some anti-virus vendors identify them by their virus signature. Therefore, this limits the potential size of the botnet. But in the case of a targeted attack, there are advantages to using such protection.
It seems that only 64-bit versions of Windows are at risk. The impression is erroneous, as 32-bit malware modifications were also found on computers in the affected facilities. Despite the similar structure, the 32-bit version is not just 64-bit compilation, it is slightly different: the injection and bootloader stages are combined into one stage, classical RC4 encryption is used instead of Spritz, the module of this stage is stored in the system registry and not in the file system . The version of the Enigma tread used is 3.7 with a single development license, it is clearly used to protect the binary code on January 11, 2017.
Stage 3: Module
The third and final stage is a relatively large module (about 730 Kb), which contains the main functions of the malware: interaction with the C&C server and receiving commands from operators (hackers). The module integrates itself into all current sessions in a compromised Windows system.
The upper line shows the different parts of the binary code: sections of the code are highlighted in blue, data sections are gray-yellow. Blue (as opposed to dark blue) is a code that is statistically linked to existing libraries. In addition to the usual C runtime, we found a link to the open source cross-platform file transfer library libcurl (version 7.47.1, release date February 8, 2016), as well as code snippets for OpenSSL and XUnzip projects. The color effect in the line is not automatically generated, in this case we had to explicitly mark the parts that we consider to be related by the library code, and we imported all the function names. Dark blue sections are code written by attackers.
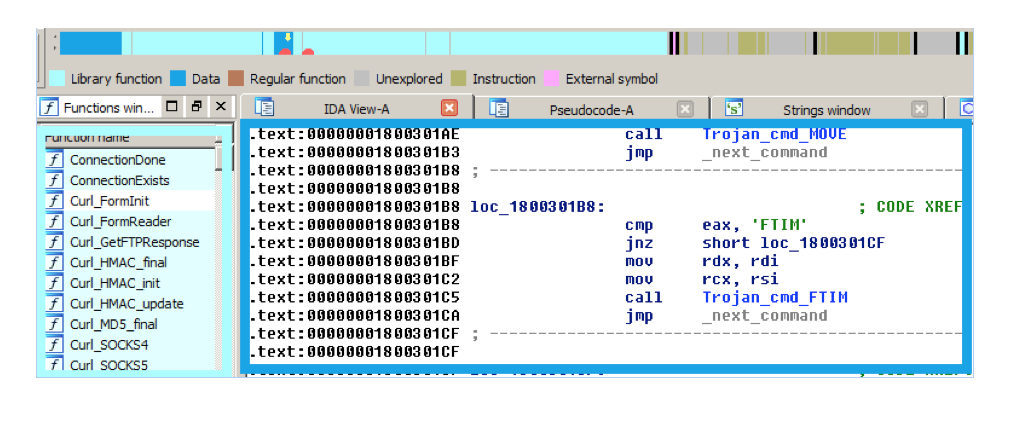
Only one URL is encoded in the module. Data exchange is encrypted. We did not record any interaction, since the remote server did not respond during the analysis. The module supports enough commands to classify it as a remote access trojan. The set of commands is as follows: “SLEP”, “HIBN”, “DRIV”, “DIR”, “DIRP”, “CHDR”, “RUN”, “RUNX”, “DEL”, “WIPE”, “MOVE”, “FTIM ”,“ NEWF ”,“ DOWN ”,“ ZDWN ”,“ UPLD ”,“ PVEW ”,“ PKIL ”,“ CMDL ”,“ DIE ”,“ GCFG ”,“ SCFG ”,“ TCON ”,“ PEEX ”, “PEIN”. The purpose of most commands is obvious: SLEP - go to standby mode, PKIL - kill the process, UPLD - stealth data output, DOWN - download, DEL - delete the file, etc. It is possible that the original libcurl functions were adapted to hacker tasks. However, libcurl is a large-scale project with hundreds of participants, tens of thousands of lines of code and hundreds of versions.
Lazarus-like toolkit
Researchers at BAE Systems describe a 32-bit injection protected by Enigma as follows: “After unpacking, the software resets a version of a known malware resembling part of the toolkit of the Lazarus hacker group.” This is confirmed by Symantec experts: “Some lines of code are similar to the malware of the Lazarus cybergroup.” The connection is confirmed by the Novetta report, in particular, the already mentioned dynamic loading of the API. Based on this evidence, we characterized the key properties of malicious attacking tools as follows:
Our data shows the recent in-the-wild activity of various programs like Lazarus. However, in order to provide a clear picture of the incident, it takes time to gather additional information.
A strange discovery
In the course of the study, we discovered an interesting example of this family of malware. This is the fdsvc.exe console application, which expects four parameters (we check with the list of characteristics - 2), which is executed in stages (1). Moreover, the application decodes the next step using RC4 with a 32-bit key (4). Two properties from the list above (3 and 5) are missing. On the other hand, the tool embeds a payload in all running Windows sessions. The payload is statistically related to libcurl v7.49.1.
Another interesting feature is the hacker teams at the final stage. Teams are used "in Russian" - written in transliteration from the Cyrillic alphabet, but not very similar to the work of a Russian-speaking author.
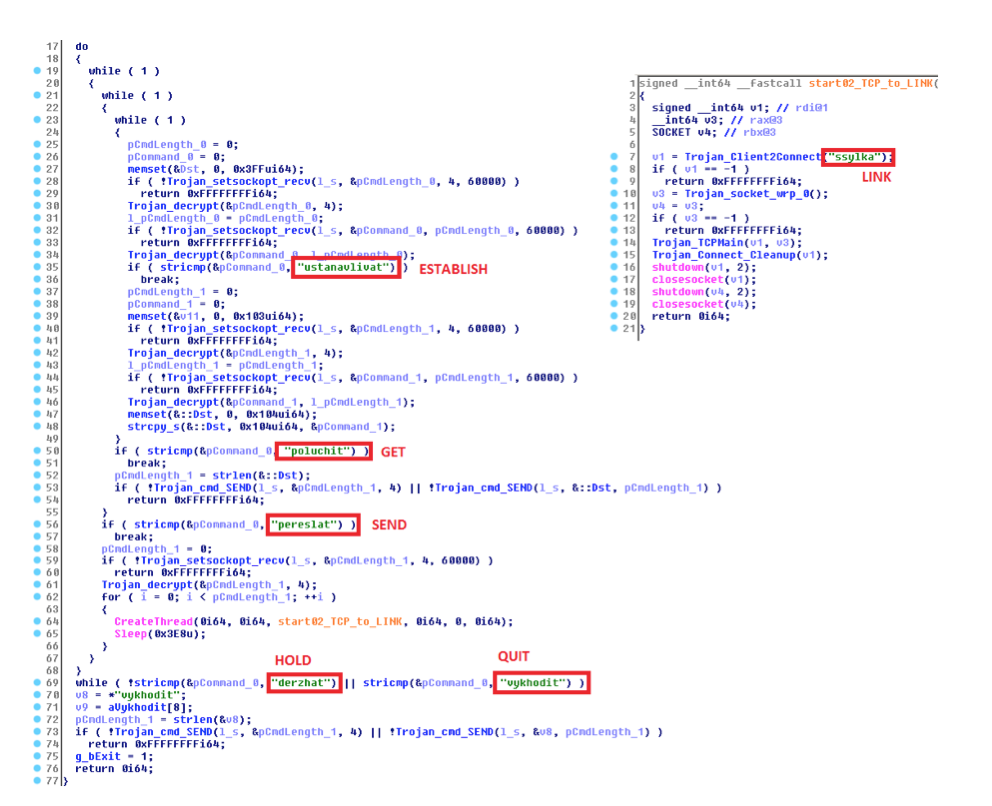
This sample once again recalls the importance of caution in determining the language of the attackers. Such "bait" in broken Russian may well be a dramatization. Without going into details of a philological nature, we can recall that the authors of malware most often use numbers to indicate commands or reduction in Latin letters. A team of 12 letters is at least impractical.
Conclusion
Considering the samples, we dare to assume that this is not a reuse of the code that existed long before the attacks on Polish banks, and not a forgotten or stopped project. Moreover, over the course of many weeks we have observed the appearance of malware resembling “our” samples.
The hackers behind the incident are highly qualified, so information security specialists at financial institutions are not recommended to relax. Here, by the way, it is necessary to recall the 50% discount when switching to ESET antivirus products from solutions of other manufacturers - for more details, click here .
Table of samples and indicators
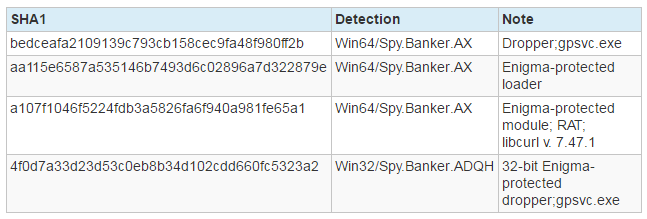
Samples used in attacks:
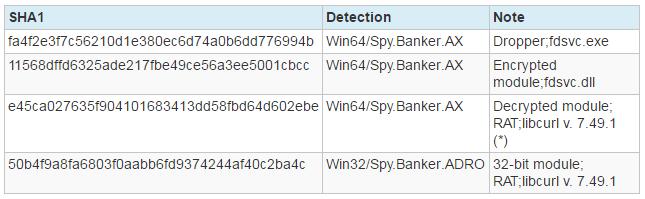
Malicious software with transliterated code:

These attacks have a lot of interesting things, from targets and infection vectors to the characteristics of malicious executable files. If the first two aspects have already been studied, then the malicious code has not been investigated in detail. In this post we will conduct a technical analysis of the malware.
Distribution channel
According to ZaufanaTrzeciaStrona.pl, hackers carried out a series of attacks such as the watering hole - infecting sites that potential victims visit. A compromised site redirects the user to an infected exploit page. In Poland, the starting point was the official website of the Financial Supervisory Commission (Komisji Nadzoru Finansowego).
According to our data, in Mexico the website of a similar agency (National Commission for the Banking System and Securities - Comisión Nacional Bancaria y de Valores) was used for the same purpose. Unfortunately, this information has not yet been confirmed by web tracking services or by the institution itself. However, we assume that the redirect was from this site:

Stage 1: Injection
If the exploit kit successfully delivered the trojan, a malicious load is executed on the victim’s computer - a 64-bit console application. Unlike the injection described by BAE Systems, the program expects one of three arguments: -l, -e, or –a (section 2 in the figure below).
While the -l option has the same meaning, the remaining two are necessary for unpacking the resources of the next step (section 4) and for autostarting one of them as a service (section 5):

In section 5, the injection tries to change the configuration of the system service in order to install the bootloader as a service. The configuration is intended to be automatically launched by the service management manager during system startup. This requires administrator rights.
At the first stage of the attack, the threat does not hide itself as carefully as at the subsequent ones. It even contains a lengthy statement providing information on the execution status (in this case, on the extraction of encrypted resources; however, there is no debugging information, including the names of the original functions).
Injection uses dynamic loading of the API instead of the Windows functions in the import table (more on this in the Novetta Operation Blockbuster report on the Lazarus hacker group, page 34). Section 3 in the image above demonstrates the shell of this function, which starts one system library after another.
It seems that hackers designate the second stage as the “bootloader”, and the third, containing the main functionality of the malware, as the “module”. The bootloader is decrypted, while the module is removed and installed unchanged. For the purpose of disguising, files borrow the creation time from the shlwapi.dll system.
An interesting feature of the encryption algorithm is the relatively new Spritz stream cipher , reminiscent of RC4. The Spritz implementation in the C and Python programming languages is already available, it corresponds to the following unpacked code from the injection:

Stage 2: Loader
The threat hides the presence in the infected system. The bootloader is protected by the Enigma Protector paid utility, the module is stored encrypted. As we expected, hackers use an unregistered copy of the 64-bit Enigma v1.31 - it would be strange to expect a qualified author to make an elementary mistake and jeopardize his identity using an officially registered copy. (On the contrary, the use of hacked or pirated software, if available, is not unusual.) Hackers planning to build a botnet usually do not use commercial archivers, since some anti-virus vendors identify them by their virus signature. Therefore, this limits the potential size of the botnet. But in the case of a targeted attack, there are advantages to using such protection.
It seems that only 64-bit versions of Windows are at risk. The impression is erroneous, as 32-bit malware modifications were also found on computers in the affected facilities. Despite the similar structure, the 32-bit version is not just 64-bit compilation, it is slightly different: the injection and bootloader stages are combined into one stage, classical RC4 encryption is used instead of Spritz, the module of this stage is stored in the system registry and not in the file system . The version of the Enigma tread used is 3.7 with a single development license, it is clearly used to protect the binary code on January 11, 2017.
Stage 3: Module
The third and final stage is a relatively large module (about 730 Kb), which contains the main functions of the malware: interaction with the C&C server and receiving commands from operators (hackers). The module integrates itself into all current sessions in a compromised Windows system.
The upper line shows the different parts of the binary code: sections of the code are highlighted in blue, data sections are gray-yellow. Blue (as opposed to dark blue) is a code that is statistically linked to existing libraries. In addition to the usual C runtime, we found a link to the open source cross-platform file transfer library libcurl (version 7.47.1, release date February 8, 2016), as well as code snippets for OpenSSL and XUnzip projects. The color effect in the line is not automatically generated, in this case we had to explicitly mark the parts that we consider to be related by the library code, and we imported all the function names. Dark blue sections are code written by attackers.

Only one URL is encoded in the module. Data exchange is encrypted. We did not record any interaction, since the remote server did not respond during the analysis. The module supports enough commands to classify it as a remote access trojan. The set of commands is as follows: “SLEP”, “HIBN”, “DRIV”, “DIR”, “DIRP”, “CHDR”, “RUN”, “RUNX”, “DEL”, “WIPE”, “MOVE”, “FTIM ”,“ NEWF ”,“ DOWN ”,“ ZDWN ”,“ UPLD ”,“ PVEW ”,“ PKIL ”,“ CMDL ”,“ DIE ”,“ GCFG ”,“ SCFG ”,“ TCON ”,“ PEEX ”, “PEIN”. The purpose of most commands is obvious: SLEP - go to standby mode, PKIL - kill the process, UPLD - stealth data output, DOWN - download, DEL - delete the file, etc. It is possible that the original libcurl functions were adapted to hacker tasks. However, libcurl is a large-scale project with hundreds of participants, tens of thousands of lines of code and hundreds of versions.
Lazarus-like toolkit
Researchers at BAE Systems describe a 32-bit injection protected by Enigma as follows: “After unpacking, the software resets a version of a known malware resembling part of the toolkit of the Lazarus hacker group.” This is confirmed by Symantec experts: “Some lines of code are similar to the malware of the Lazarus cybergroup.” The connection is confirmed by the Novetta report, in particular, the already mentioned dynamic loading of the API. Based on this evidence, we characterized the key properties of malicious attacking tools as follows:
- Multistage malware that is cascaded.
- The initial stage is a console application that expects at least one parameter.
- WINAPI boots automatically.
- An RC4 stream cipher or other similar long-key algorithm that is used for decryption in the next step.
- The next step (s) are DLLs that are loaded as a service with the SERVICE_AUTO_START startup type (administrator rights are required).
Our data shows the recent in-the-wild activity of various programs like Lazarus. However, in order to provide a clear picture of the incident, it takes time to gather additional information.
A strange discovery
In the course of the study, we discovered an interesting example of this family of malware. This is the fdsvc.exe console application, which expects four parameters (we check with the list of characteristics - 2), which is executed in stages (1). Moreover, the application decodes the next step using RC4 with a 32-bit key (4). Two properties from the list above (3 and 5) are missing. On the other hand, the tool embeds a payload in all running Windows sessions. The payload is statistically related to libcurl v7.49.1.
Another interesting feature is the hacker teams at the final stage. Teams are used "in Russian" - written in transliteration from the Cyrillic alphabet, but not very similar to the work of a Russian-speaking author.

This sample once again recalls the importance of caution in determining the language of the attackers. Such "bait" in broken Russian may well be a dramatization. Without going into details of a philological nature, we can recall that the authors of malware most often use numbers to indicate commands or reduction in Latin letters. A team of 12 letters is at least impractical.
Conclusion
Considering the samples, we dare to assume that this is not a reuse of the code that existed long before the attacks on Polish banks, and not a forgotten or stopped project. Moreover, over the course of many weeks we have observed the appearance of malware resembling “our” samples.
The hackers behind the incident are highly qualified, so information security specialists at financial institutions are not recommended to relax. Here, by the way, it is necessary to recall the 50% discount when switching to ESET antivirus products from solutions of other manufacturers - for more details, click here .
Table of samples and indicators
Samples used in attacks:

Malicious software with transliterated code:

